
read file error: read notes: is a directory 2023-7-29 07:0:54 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:95 收藏

Executive Summary
On July 18, 2023, Citrix published a security bulletin for vulnerabilities affecting their NetScaler ADC and NetScaler Gateway products. When these appliances are configured as a gateway or authentication server and managed by a customer (i.e., not Citrix-managed) they can be vulnerable to remote code execution initiated by an attacker. Vulnerabilities on Citrix-managed servers have already been mitigated.
Citrix states that they have observed attacks targeting CVE-2023-3519 against appliances that haven’t been patched. The Cybersecurity and Infrastructure Security Agency (CISA) has also released an advisory detailing an attack using this vulnerability.
Palo Alto Networks customers receive protections from and mitigations for CVE-2023-3519 in the following ways:
- Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks.
- Cortex Xpanse customers can identify external-facing instances of the application through the “Insecure Citrix Application Delivery Controller” attack surface rule.
Palo Alto Networks also recommends patching against these vulnerabilities, including CVE-2023-3519, with the software update provided by Citrix.
| Vulnerabilities Discussed | CVE-2023-3519, CVE-2023-3466, CVE-2023-3467 |
Table of Contents
Details of the Vulnerability
Current Scope of the Attack
Interim Guidance
Conclusion
Palo Alto Networks Product Protections for CVE-2023-3519
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Cortex Xpanse
Indicators of Compromise
References
Details of the Vulnerabilities
CVE-2023-3519 is a remote code execution (RCE) vulnerability with a CVSS severity score of 9.8 that was disclosed on July 18, 2023. This vulnerability affects older installations of NetScaler ADC (an application delivery controller firmware for securing network traffic) as well as NetScaler Gateway, which is an access gateway that provides VPN and single sign-on (SSO) capabilities for remote end users of network assets.
Additional vulnerabilities covered in this security bulletin affecting NetScaler users include CVE-2023-3466 and CVE-2023-3467. According to Citrix, CVE-2023-3466 is a reflected Cross-Site Scripting (XSS) vulnerability that requires a victim to visit an attacker-controlled link via web browser while the virtual NetScaler appliance is on the same network with connectivity to the NetScaler IP (NSIP).
CVE 2023-3467 is a privilege escalation vulnerability that requires attackers to have unauthenticated access to the NSIP or subnet IP (SNIP) with management interface access, and allows for potential privilege elevation to root administrator access. CVE-2023-3466 and CVE-2023-3467 have severity scores of 8.3 and 8 respectively.
According to Citrix, these three vulnerabilities affect the following versions of Citrix NetScaler ADC and NetScaler Gateway:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC and NetScaler Gateway version 12.1 (EOL)
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
CISA also reports that the appliance requires configuration as a gateway or authentication, authorization and auditing (AAA) server for exploitation. These updates from Citrix patch for all three of the aforementioned vulnerabilities.
Current Scope of the Attack
CISA has reported at least one attack in which a threat actor had exploited this vulnerability as a zero-day exploit, to gain access to a critical infrastructure organization’s NetScaler appliance. For this incident, the threat actor leveraged CVE-2023-3519 to drop a PHP webshell on the targeted appliance.
The threat actor then used the dropped web shell to enumerate and exfiltrate Active Directory data. The threat actor also attempted further discovery activities but failed because the exploited NetScaler appliance was in a segmented environment.
Interim Guidance
Citrix has released a patch for this vulnerability and recommends that all customer managed appliances update as soon as possible. Additionally, CISA released an advisory article with an accompanying document containing information on detection methods, incident response tips, mitigations, and validating security controls for securing your organization against this vulnerability and others like it.
The CISA detection methods include information such as the following:
- Instructions for modifying specific parameters regarding your NetScaler appliance installation
- Specific commands for checking logs that may contain abnormalities
- Guidance on reviewing various network logs that could indicate anomalous Application Delivery Controller (ADC) activity
Their incident response guidance depicts basic steps to quarantine and reimage affected hosts, while provisioning account credentials and reviewing system and network artifacts such as processes, services, and logs.
In terms of mitigations, CISA provides the following recommendations for organizations:
- Install the relevant updated version of NetScaler ADC and NetScaler Gateway as soon as possible.
- Follow cybersecurity best practices in your production and enterprise environments, including mandating phishing-resistant multifactor authentication (MFA) for all staff and for all services.
Additional best practices can be found by referring to CISA’s Cross-Sector Cybersecurity Performance Goals.
Conclusion
Based on the amount of publicly available information, Palo Alto Networks highly recommends following CISA’s guidance on mitigations for protecting your organization against CVE-2023-3519, CVE-2023-3466 and CVE-2023-3467. These mitigations include applying vendor-provided patches as well as executing their described detection and mitigation methods in your network environment.
Palo Alto Networks and Unit 42 will continue to monitor the situation for updated information including release of proof-of-concept code or evidence of more widespread exploitation.
Palo Alto Networks customers are protected by our products, as listed below. We will update this threat brief as more relevant information becomes available.
Palo Alto Networks Product Protections for CVE-2023-3519
Palo Alto Networks customers can leverage a variety of product protections and updates to identify and defend against this threat.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Next-Generation Firewalls and Prisma Access With Advanced Threat Prevention
Next-Generation Firewall with the Advanced Threat Prevention security subscription can help block the attacks via the following Threat Prevention signature: 94145.
Cortex Xpanse
Cortex Xpanse customers can identify external facing instances of the application through the “Insecure Citrix Application Delivery Controller” attack surface rule. The rule is available to all customers with a default state of “On.”
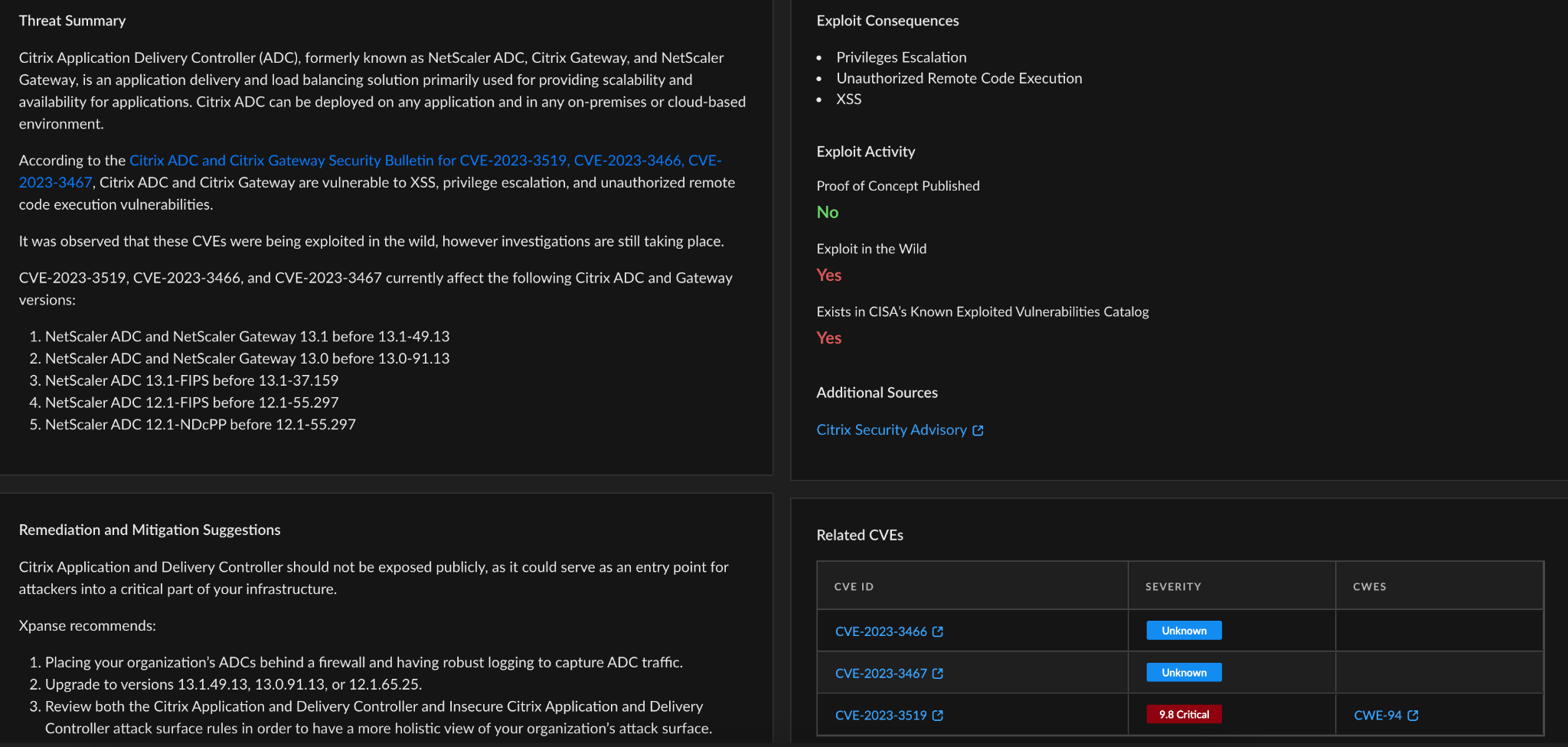
Within Cortex Xpanse’s Threat Response Center, organizations can also find curated threat intel summaries, exploit consequences, previous exploit activity, and links to other sources for additional information. This allows you to see how risk is distributed across your organization and build a remediation plan based on the guidance provided. Cortex Xpanse identifies service owners automatically, so organizations can easily assign a ticket to the right person.
Indicators of Compromise
SHA-256 Hash
- 293fe23849cffb460e8d28691c640a5292fd4649b0f94a019b45cc586be83fd9
IP Addresses
- 216.41.162[.]172
- 216.51.171[.]17
References
- New Critical Citrix ADC and Gateway Flaw Exploited as Zero-Day – Bleeping Computer
- Citrix ADC and Citrix Gateway Security Bulletin for CVE-2023-3519, CVE-2023-3466, CVE-2023-3467 – Citrix Support Knowledge Center
- Threat Actors Exploiting Citrix CVE-2023-3519 to Implant Webshells – CISA
- Threat Actors Exploiting Citrix CVE-2023-3519 to Implant Webshells – CISA (PDF)
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh