US pharmacy giant PharMerica has notified over 5.8 million people about a security incident in which it says personal information and medical information may have been obtained by cybercriminals. The Data Breach Notification lists the total number of persons affected as 5,815,591.
An investigation was started after PharMerica noticed suspicious activity on its network. The investigation showed that an unauthorized party accessed PharMerica computer systems on March 12-13, 2023, and that this party may have had access to certain personal information. The incident was noticed on March 14, and a week later PharMerica identified that the personal information accessed included names, dates of birth, Social Security numbers, medication lists and health insurance information.
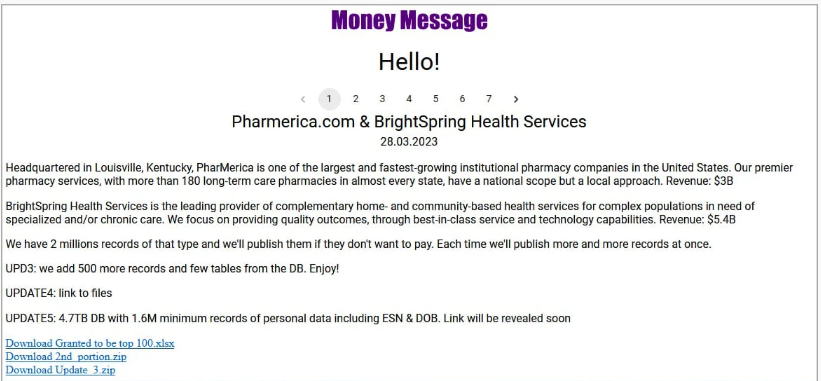
Ransomware group Money Message has claimed responsibility for the attack. The gang claims that they encrypted almost the entire PharMerica infrastructure, and has published parts of the stolen data to their leak site.

Image courtesy of BleepingComputer
Money Message is a new ransomware which targets both Windows and Linux systems. As we mentioned in our May ransomware review, Taiwanese PC parts maker MSI also fell victim to Money Message.
On its website PharMerica says:
“At this point, PharMerica is not aware of any fraud or identity theft to any individual as a result of this incident, but is nonetheless notifying potentially affected individuals to provide them with more information and resources. The notice will include information on steps individuals can take to protect themselves against potential fraud or identity theft. PharMerica has arranged for complimentary identity protection and credit monitoring services for potentially affected individuals.”
An extra point of concern is that a relative large part of the people affected by the breach have passed away, which makes it unlikely that relatives will regularly monitor their credit reports, making any cybercrime related to the stolen data even more difficult to detect and stop.
What to do if you've been caught in a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor's advice. Every breach is different, so check with the vendor to find out what's happened, and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don't use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims, and verify any contacts using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you've isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.