
read file error: read notes: is a directory 2023-5-15 21:0:16 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:32 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Within Unit 42 Threat Intelligence, we are often asked, “How does Unit 42 define and track actor activity?” To answer this question, we’ll give you a glimpse into our day-to-day activities, specifically focusing on how Unit 42 Threat Intelligence tracks behavior-based activity clusters.
The convention that Unit 42 Threat Intelligence uses for naming formal threat actor groups has been discussed in a previous blog. In this post, we’ll step back to give you a broader view, covering how the Unit 42 team builds and tracks activity clusters, and then associates this behavior with temporary threat actor groups. We’ll also discuss how we decide when to enact our formal actor naming and definition processes.
| Related Unit 42 Topics | APT, nomenclature, threat actors, threat intelligence |
Table of Contents
Activity Clusters
Temporary Actor Groups
Final Thoughts
Threat Tracking Overview
Defining a cluster of activity or a temporary actor group is a complex and often ambiguous process that typically takes a lot of time, effort and coordination. Formal actor naming begins when our team analyzes artifacts and TTPs from a single intrusion. It then evolves when we build and track additional activity into what we call an activity cluster.
Activity clusters consist of observed threat actor behavior that we have identified and use as a basis for tracking. These behaviors are clustered into groups of tactics, techniques and procedures (TTPs). We continually review and push these TTPs through our analysis process such that the clusters grow over time, potentially becoming a temporary threat actor group.
To achieve Unit 42’s mission of protecting the digital world against cyberattacks, we need to consistently track and monitor activity clusters and temporary threat actor groups.
Activity Clusters
An activity cluster is a grouping of related threat activity that includes observable artifacts like adversary tools, infrastructure or trade craft. The intention of defining an activity cluster is to build out a corpus of knowledge on a cluster of activity over time before “graduating” that cluster to a temporarily tracked threat group.
These clusters start with data collected in a single incident or investigation, and they grow by piecing together additional data from other incidents and collection sources. While running investigations, Unit 42 researchers often discover new artifacts associated with their investigations that can grow, merge or break off clusters of activity.
The Unit 42 team defines activity clusters based on our hypothesis of the actor’s motivation, where it is possible to establish. We name clusters using the following shorthand notation:
- CL - short for cluster
- CRI - short for criminal motivation
- STA - short for state-backed motivation
- MIX - short for mixed motivation
- UNK - short for unknown motivation
Using this shorthand, Unit 42 names clusters of activity as follows:
CL-{CRI | STA | MIX | UNK} - ####
The number assigned to the activity cluster is in consecutive order, incrementing by one from the previously classified activity cluster.
Let’s examine how this looks with an example.
Unit 42 researchers are often involved in the research of multiple incidents targeting medical facilities throughout the United States. While working on each of the incidents, we find that the different adversary tools, infrastructure and trade craft are sometimes related. This helps us form an activity cluster.
We will often find the adversary exploiting the same vulnerabilities to gain initial access, applying the same lateral movement and exfiltration tactics, and using the same infrastructure for command and control (C2) across varying medical organizations. However, in many cases, we might not know the motivation of the adversary. Based on this, Unit 42 could track this as an activity cluster named CL-UNK-0042.
Now that we’ve examined some of the core tenants of tracking activity clusters, let’s examine the next step of our definition process: creating temporary actor groups.
Temporary Actor Groups
The concept of creating temporary actor groups is a way for the Unit 42 team to graduate activity clusters to a more solidified categorization. This graduation means the researcher feels confident that a single actor is participating in the threat activity.
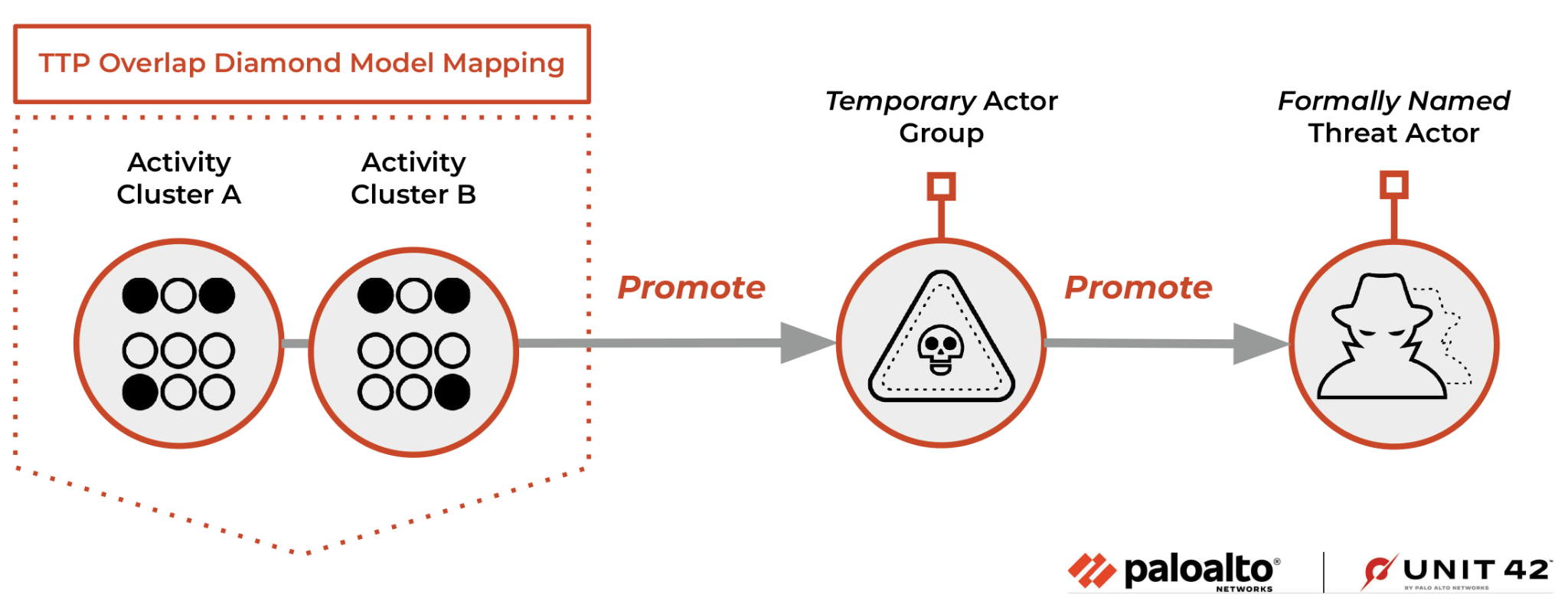
It is important to note that within Unit 42 Threat Intelligence, we prevent direct migration of activity clusters to formally named actor groups. The activity clusters must first go through graduation to a temporary threat actor group.
This graduation is done after establishing several correlation points over time and across activity clusters, and after mapping those overlaps to the Diamond Model of Intrusion Analysis. This model focuses on core features of intrusions such as adversary, capability, victim and infrastructure, which Unit 42 researchers leverage and examine to correlate related clusters of activity.
For temporary actor groups, we opted to keep the same naming convention, with the addition of TGR, which is short for “threat group.”
We name temporary group names as follows:
TGR-{CRI | STA | MIX | UNK} - ####
Like the numbering for activity clusters, the number assigned at the end of the name for a threat group is in consecutive order, incrementing by one from the previously classified threat group.
Let’s look at an example of how we name a temporary actor group using our defined convention, continuing with tracking CL-UNK-0042. Further tracking and analysis revealed shared usage of phishing and C2 infrastructure in addition to overlaps with another activity cluster: CL-STA-0073.
During tracking, researchers also determined that threat actors were sharing tooling and malware throughout both clusters of activity, some of which were custom created. Based on these and previous investigative findings, Unit 42 could now start tracking clusters CL-STA-0042 and CL-STA-0073 as TGR-STA-0051.
Consistent tracking and analysis over time of TGR-STA-0051 could ultimately lead to a formal Unit 42 threat actor name, after we establish higher confidence in the relationship between the temporary group and the formal group.
Final Thoughts
In this blog, we wanted to give a glimpse into a day in the life of a researcher who’s identifying, defining and tracking activity clusters and temporary threat actor groups. We hope this insight provides clarity into how some of the more nebulous aspects of threat research are performed. You can now be better informed about the meaning of these two groupings, as Unit 42 starts to leverage activity clusters and temporary actor groups in our forthcoming publications.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh