2023-5-11 08:0:0 Author: www.trustwave.com(查看原文) 阅读量:13 收藏
In the first part of this series, we looked at some common issues when a Chief Information Security Officer (CISO) is communicating with the Board. At the heart of many of these issues is how the CISO and upper management view security.
As one CISO recently told me, "It's a catch-22 situation: If the business leaders don't consider this to be a business problem, they are unlikely to listen to people they don't consider to be business leaders telling them it is."
So, how do we put it in terms the C-Suite will understand? We must demonstrate cost savings, protect the organization's reputation, improve resilience, and create a common language CISOs and technical personnel can use when communicating with executives so they understand the risk correctly.
Every organization faces risks – events or situations which inhibit it from reaching its goals. These risks can range from taking a chance on manufacturing a new product or building a facility in areas prone to floods. Such enterprise risks are recognized and managed by the senior leadership, and this means security risks must fall under the same umbrella. However, as all CISOs know, security is an area that touches every part of the business and, therefore, deals with risks affecting highly-focused processes to wide-ranging activities; the danger here is that security risks can be challenging to quantify in easy-to-understand language and, as such, can overshadow or more commonly, be overshadowed, by other threats.
Use Business Terminology to Explain Cyber Risk
That's the first part of the problem: documenting the cyber hazards in business terms, the C-Suite can understand and digest. The easiest and most direct way to handle this task is to bring the discussion back to dollars. It is a topic leadership understands and does not want impacted in a negative manger.
The unfortunate fact is the C-Suite may not understand the damaging impact of a cyberattack if it is not explained properly. For example, when discussing a cyber hazard like a data breach, caused by any type of attack, a CISO should take care to explain it to the C-Suite or Board in business terms such as idle/downtime for the entire organization until the network is back up. If the security officer says, “breach to the database,” then the Board should hear, “the need to protect my customers account information in order to maintain goodwill and keep my customers safe and coming back.”
While this should get their attention, given how a cyber incident can unfold, it might not be the ultimate outcome or risk and the narrative needs continue. At this point the CISO can hammer home to the Board or C-Suite the potential for damage by citing a few pertinent figures.
The financial damage a cyberattack can inflict is gathered and disseminated each year by the FBI in its Internet Crime Report. For 2022, the report recorded $459.3 million in losses due to data breaches and another $34 million lost due to ransomware.
The FBI noted the ransomware number is likely understated as it only includes ransoms paid and does not take into account lost business. Additionally, the figures only included reported incidents with it being likely many aren’t known about outside the impacted organization. Phishing attacks resulted in another $52 million in losses, with the highest losses generated by business email compromise attacks at $2.7 billion.
Data Driven Risk Management
The second issue is to ensure the CISO correctly states the level of risk. Only then will it be possible to assess these risks against the organization's risk appetite. The risk appetite is simply how much of a risk you're willing to accept to conduct business.
In the previous example we noted that explaining the financial impact a cyber incident can have on an organization is one way to grab an executive’s attention in a manner they will understand.
Another method is using data.
Organizations that make effective risk management decisions do not do so in a vacuum, but base their conclusions on the best information available at the moment.
One general business tool to use that is fairly well understood is a risk matrix. Here various potential problems, such as a ransomware attack, an insider threat, or database compromise can be plotted based on their likelihood.
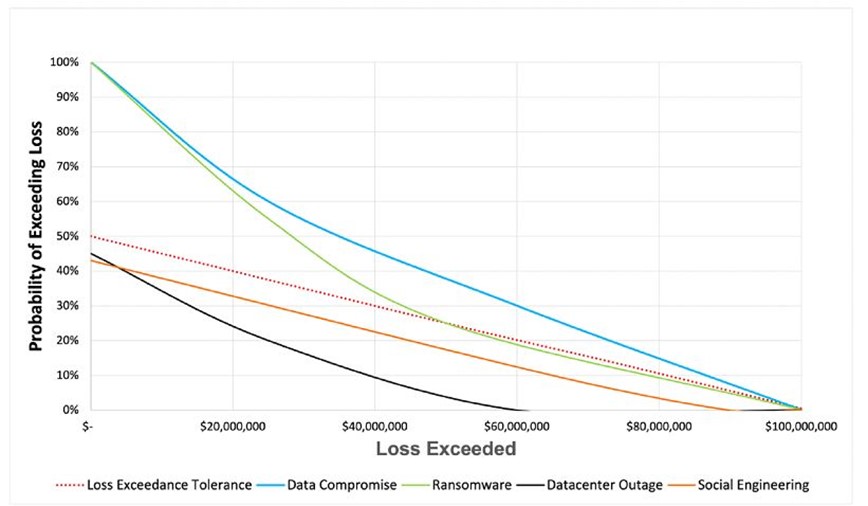
The next step is to move the data from the matrix to a Loss Exceedance Curve. Here a potential loss number can be determined if an incident takes place. Using information pulled from trusted industry sources, such as the FBI IC3 report or the Verizon Data Breach Report, a CISO can visualize the cost of an attack and balance it against how much the organization is willing to spend to defer that risk.
Source: ISACA - The Elephant in the Risk Governance Room
Reducing Risk
At first glance, this may seem counter-intuitive; why would you accept reducing risk instead of removing it entirely? But when you consider the implications of risk elimination, it becomes more apparent. Traditionally, there are five methods to reduce risk:
- Transfer the Risk – This means someone else is responsible, such as a cyber insurance company or a supplier. It's not ideal as, apart from cost implications, it doesn't stop the threat from materializing, it only means somebody else deals with the consequences, which can be days or weeks later.
- Mitigate the Risk (otherwise known as loss prevention and reduction) – When your organization deploys technical and procedural controls. Mitigation is often the primary method of risk reduction, but also the one that requires the most ongoing time and resources to implement and manage effectively.
- Share the Risk – Where two or more entities reduce costs or resources by combining their need. This method combines the two methods above but has the added complexity of who takes responsibility for the operation and response to any active threat.
- Avoid the Risk – In effect, when the operation or process potentially can lead to the risk is not carried out. This result can limit the business's effectiveness and profitability. For example, just imagine if you avoid the risk of your website being defaced by just not having a website. The consequence would be a loss of marketing, sales, and communication ability.
- Accept the Risk – have you judged the potential outcome to be either unlikely to occur, to be manageable and recoverable without affecting the business unduly, or the risk cannot be reduced without causing major upset to the way the organization operates?
Setting Realistic Goals
Setting a realistic risk appetite is a task for the entire C-Suite. Each member is likely to have their own thoughts and inputs, so it's important to correctly identify and communicate the level of risk. Therefore, the C-Suite members will need to reach a consensus, and the CISO can provide guidance and direction in this activity.
Once this team reaches agreement, the CISO can use a combination of the items listed above to balance costs, manage overheads and effectiveness while keeping everything below the agreed-upon risk appetite level, complying with relevant legislation and regulatory requirements, and constantly monitoring the threat landscape and adjusting the response.
Breaking New Ground
Security and cyber risk are relatively recent phenomenon, yet to be fully recognized or comprehended by all as yet. However, that's not necessarily the C-Suite's fault, as these people generally have to juggle cybersecurity with many other issues. To help management properly understand the concept of risk, the security leader must have the verbal tools to educate and drive understanding and acceptance of the real-world risks each organization faces. This education will ensure the protection and resilience of the business is the primary objective of a cohesive risk management approach.
如有侵权请联系:admin#unsafe.sh

