A few days ago we wrote about two vulnerabilities found in PaperCut application servers. As we noted, exploitation was fairly simple so there was some urgency to install the patches. My esteemed colleague Chris Boyd literally wrote:
“Arbitrary code can be deployed, or even ransomware if that’s part of the attacker’s toolkit.”
As it turns out, there are already two flavors of ransomware preying on those that haven’t updated yet.
A Cl0p affiliate, branded as DEV-0950 by Microsoft has already incorporated the PaperCut exploits into its attacks. This affiliate has also been known to use the GoAnywhere zero-day that basically brought Cl0p back from the dead last month.
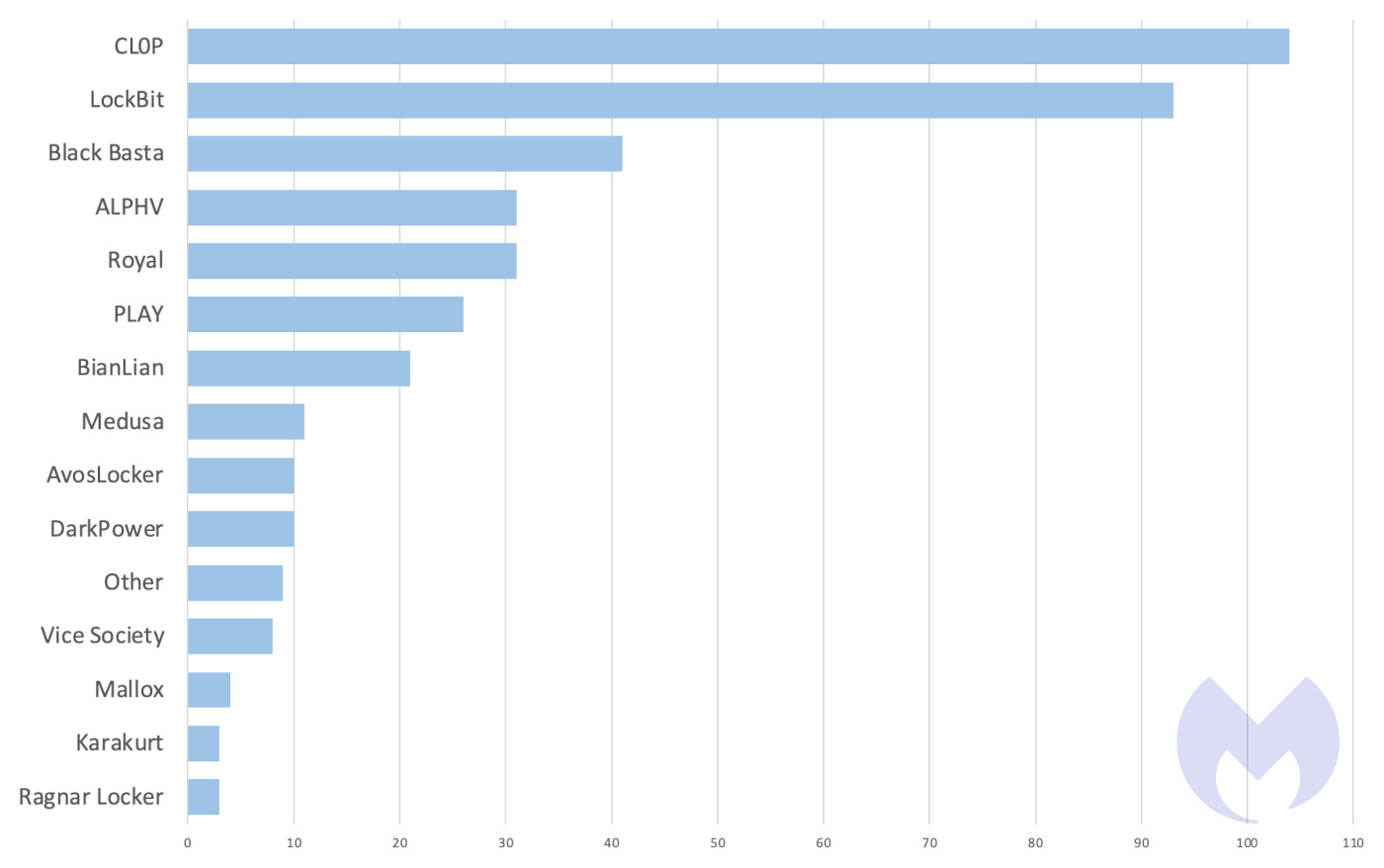
In a surprising turn of events for the ransomware landscape, Cl0p emerged as the most used ransomware in March 2023, coming out of nowhere to dethrone the usual frontrunner, LockBit.

But don’t rule the habitual frontrunner LockBit out just yet. Microsoft Threat Intelligence said in a tweet that it's "monitoring other attacks also exploiting these vulnerabilities, including intrusions leading to Lockbit deployment.”
PaperCut is printing management software that works by intercepting print jobs as they pass into a print queue. It’s used by large companies, state organizations, and education institutes because it is compatible with all major printer brands and platforms. This makes a vulnerability, especially one that is as easy to exploit, a virtual goldmine for ransomware peddlers, and puts a bullseye on anyone that is running an unpatched server.
Both the underlying vulnerabilities have been addressed with patches. If you update your PaperCut application servers, you are no longer at risk. From the Updating FAQ:
- Please follow your usual upgrade procedure. Additional links on the ‘Check for updates’ page (accessed through the Admin interface > About > Version info > Check for updates) will allow customers to download fixes for previous major versions which are still supported (e.g. 20.1.7 and 21.2.11) as well as the current version available.
- If you are using PaperCut MF, we highly recommend following your regular upgrade process. Your PaperCut partner or reseller information can also be found on the ‘About’ tab in the PaperCut admin interface.
If you’re unable to upgrade, PaperCut advises the following:
- Block all inbound traffic from external IPs to the web management port (port 9191 and 9192 by default)
- Block all traffic inbound to the web management portal on the firewall to the server. Note: this will prevent lateral movement from internal hosts but management of the PaperCut service can only be performed on that asset.
- Apply “Allow list” restrictions under Options > Advanced > Security > Allowed site server IP addresses. Set this to only allow the IP addresses of verified Site Servers on your network. Note this only addresses ZDI-CAN-19226 / PO-1219.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you've isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.