Author: Knownsec 404 Team中文版:https://paper.seebug.org/2057/1. AbstractIn the process of 2023-3-29 16:44:0 Author: paper.seebug.org(查看原文) 阅读量:19 收藏
Author: Knownsec 404 Team
中文版:https://paper.seebug.org/2057/
1. Abstract
In the process of using Jupyter Notebook and JupyterLab, some users lack security awareness and do not enable the authentication function, so that any user can directly access their own Jupyter server and view the code and documents on their server.
We use the ZoomEye cyberspace search engine to find those Jupyter servers on the Internet that do not enable authentication through specific search keywords. The leaked code and documents on these servers, if exploited by criminals, may cause data leakage and asset loss.
We recommend that all Jupyter users follow the official security recommendations when starting the Jupyter service, and set it to log in through token or password.
2. Overview
ZoomEye [1] is a cyberspace search engine. Through the global deployment of detection nodes, it conducts uninterrupted in-depth detection of global Internet exposed assets, builds Internet security basic situation mapping maps, and provides comprehensive asset basic data for security research.
Jupyter Notebook [2] is a program that opens in the form of a web page. You can directly write and run code on the web page, and the running result of the code will also be displayed directly under the code block. If you need to write an instruction document during the programming process, you can write it directly on the same page, which is convenient for explanation [3]. It is one of the most familiar and commonly used tool for data scientists.
JupyterLab [4] is an interactive development environment, which is the next generation of Jupyter Notebook. You can use it to write Notebook, operate terminal, edit MarkDown text, open interactive mode, view csv files and pictures, etc. It can be said that JupyterLab is a more mainstream development environment for developers in the next stage [5].
In this article, we describe how to use ZoomEye to find Jupyter servers without identity verification enabled, and access their code and documentation through a web browser.
3. Installation and startup of Jupyter
3.1 Jupyter Notebook
In this chapter, we introduce how to install, startup normally, startup Jupyter Notebook without authentication, and the effect of the corresponding web browsing access.
For the installation method of Jupyter Notebook, refer to its official website [6]. You only need to enter a sentence command on the command line, which is simple and convenient.
pip install notebookThe normal way to startup Jupyter Notebook is to enter a one-sentence command. By default, a web service is opened on port 8888 of localhost, and a token value for user authentication is generated.
jupyter notebook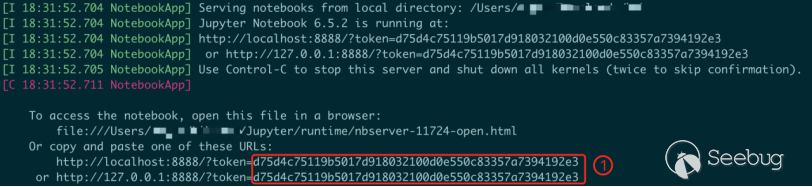
At this point, when you enter http://localhost:8888 in your web browser to access Jupyter Notebook, the page will prompt you to enter a password or token.
We enter the token value obtained when the command line is started on the page to pass the authentication and use the product functions of Jupyter Notebook.
Some users need to access their Jupyter Notebook service through the Internet, and in order to avoid the trouble of entering a password or token, they will use the following command to expose the Jupyter Notebook service to the Internet IP without enabling authentication.
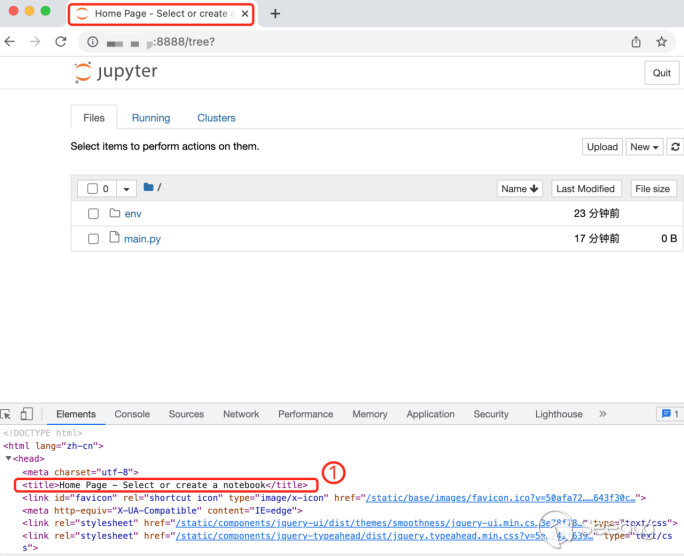
jupyter notebook --ip="*" --NotebookApp.token="" --NotebookApp.password=""At this time, any user who knows the Internet IP of the Jupyter Notebook service can enter "http://*.*.*.*:8888" in the web browser to access the Jupyter Notebook service without authentication. Review the code and files on the server. Note that in this case, the title of the page reads: "Home Page - Select or create a notebook".
3.2 JupyterLab
In this chapter, we introduce how to install, startup JupyterLab normally, startup JupyterLab without authentication, and the effect of the corresponding web browsing access.
For the installation method of JupyterLab, refer to its official website [7]. You only need to enter a sentence command on the command line, which is simple and convenient.
pip install jupyterlabThe normal way to startup JupyterLab is to enter a command. By default, a web service is opened on port 8888 of localhost, and a token value for user authentication is generated.
jupyter-lab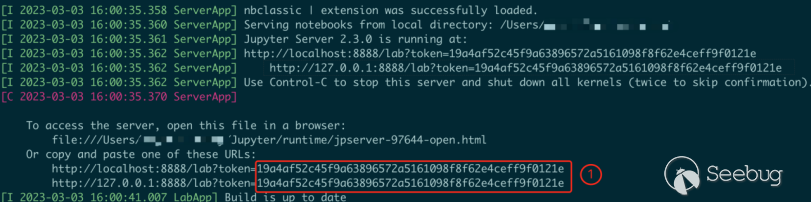
At this point, when you enter http://localhost:8888 in the web browser to access Jupyter Lab, the page will prompt you to enter a password or token.
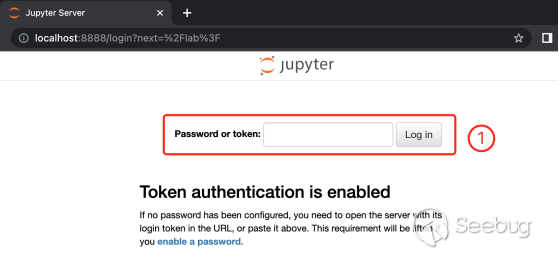
We enter the token value obtained when the command line is started on the page to pass the authentication and use the product functions of JupyterLab.
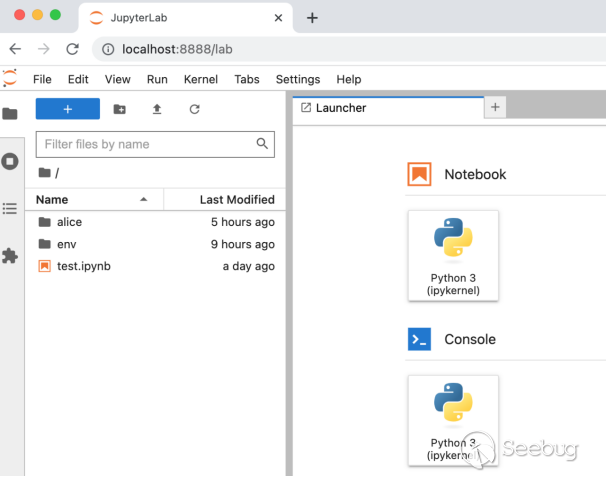
Some users need to access their JupyterLab service through the Internet, and in order to avoid the trouble of entering a password or token, they will expose the JupyterLab service to the Internet IP through the following command, and do not enable authentication.
jupyter-lab --ip="*" --NotebookApp.token="" --NotebookApp.password=""At this time, any user who knows the Internet IP of the JupyterLab service can enter "http://...:8888" in the web browser to access the JupyterLab service without authentication, and can directly view the server code and documentation on. Note that the content of the page title in this case is: "JupyterLab".
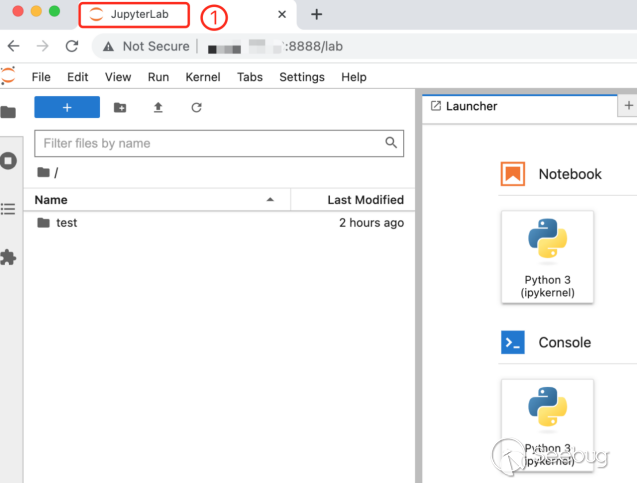
4. Find Jupyter servers without identity verification enabled
As mentioned in the previous section, the title content of the Jupyter Notebook service without authentication is "Home Page - Select or create a notebook", and the title content of the JupyterLab service without authentication is "JupyterLab".
We used the following keywords to search on ZoomEye, and found the Jupyter Notebook server IP address and port that can be directly viewed and used without authentication, with a total of 1180 results.
title:"Home Page - Select or create a notebook"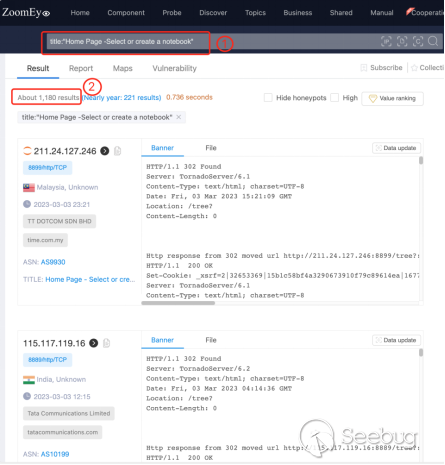
② Get 1180 results
We used the following keywords to search on ZoomEye, and found the JupyterLab server IP address and port that can be directly viewed and used without authentication, with a total of 1597 results.
title:"JupyterLab"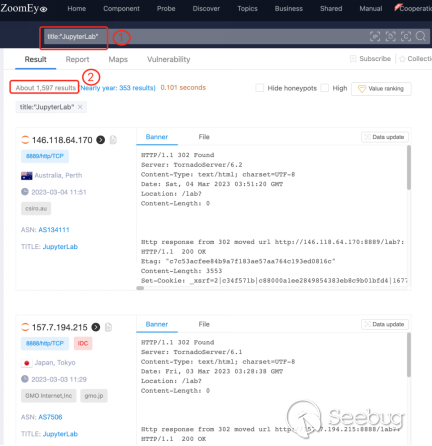
② Get 1597 results
5. Hazards of Jupyter Serving without identity verification enabled
When the user builds the Jupyter service, the identity verification is not enabled. Although it is convenient for daily use and does not need to enter a password; If sensitive information such as name/password, API key/secret is used by criminals, it may cause data leakage and asset loss.
Example 1:
As shown in the figure below, the code in the Jupyter server leaked: the key and secret of the user API of the bitFlyer cryptocurrency exchange, the username and password of the Gmail mailbox.
Criminals can use the key and secret of the bitFlyer cryptocurrency exchange API to create transactions and cancel transactions on the exchange, which may cause asset losses; use the username and password of Gmail mailboxes to log in to Gmail mailboxes, which may cause privacy Data leakage.
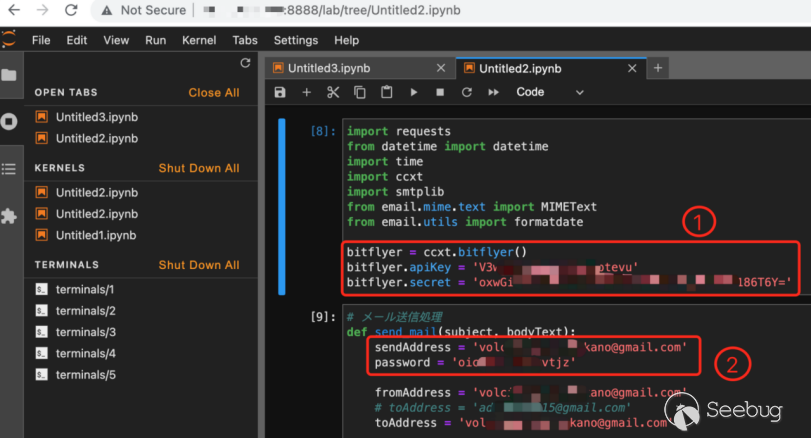
② Leaked Gmail username and password
Example 2:
As shown in the figure below, the code in the Jupyter server leaked: the ACCESS KEY ID and SECRET ACCESS KEY of the Amazon AWS account.
Criminals can use the ACCESS KEY ID and SECRET ACCESS KEY of the Amazon AWS account to obtain the account permissions of Amazon AWS, upload files to Amazon S3 cloud storage space, and even create new cloud servers on Amazon AWS.
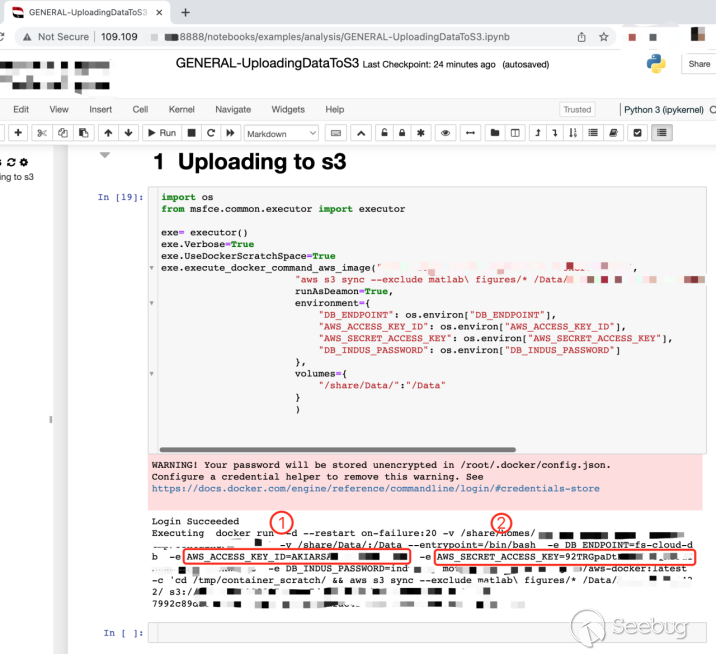
② Leaked SECRET ACCESS KEY of Amazon AWS account
6. Conclusion
When using Jupyter, try not to expose its web services on the Internet, but open them for use in the local area network to avoid being accessed by unrelated people.
If there is a need to expose Jupyter's web services to the Internet, you must set up a token or password login instead of disabling authentication for convenience. For specific operations, please refer to Jupyter's official security advice blog: Please don't disable authentication in Jupyter servers [8].
7. Reference
[1] ZoomEye cyberspace search engine
https://www.zoomeye.org
[2] Jupyter Notebook
https://jupyter.org
[3] Jupyter Notebook introduction, installation and usage tutorial
https://zhuanlan.zhihu.com/p/33105153
[4] JupyterLab
https://jupyter.org
[5] Introduction to JupyterLab and common operations
https://support.huaweicloud.com/engineers-modelarts/modelarts_23_0209.html
[6] Installation method of Jupyter Notebook
https://jupyter.org/install
[7] Istallation method of JupyterLab
https://jupyter.org/install
[8] Please don’t disable authentication in Jupyter servers
https://blog.jupyter.org/please-dont-disable-authentication-in-jupyter-servers-dd197206e7f6
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2058/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/2058/
如有侵权请联系:admin#unsafe.sh