
read file error: read notes: is a directory 2023-3-24 21:0:30 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:40 收藏

Executive Summary
The Palo Alto Networks Unit 42 Twitter handle tweeted Monday, March 6, 2023, about Gozi (ISFB/Ursnif) malware targeting Italy. Also known as ISFB or Ursnif, Gozi malware or its variants have been part of our cyberthreat landscape for the past several years. Gozi generates distinct traffic patterns during post-infection activity.
This month's Unit 42 Wireshark quiz presents real-world traffic from a Gozi infection in an Active Directory (AD) environment. Participants are asked questions based on the network activity. A separate Unit 42 blog post will provide the answers.
Participants will review a packet capture (pcap) from the infection to answer our quiz questions. While designed for security professionals who focus on suspicious network activity, anyone can participate. Participants should understand basic network traffic concepts and be familiar with Wireshark to get the most benefit.
Palo Alto Networks customers receive protections from Gozi and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services, including WildFire and Advanced Threat Prevention.
| Related Unit 42 Topics | Gozi, ISFB, pcap, Ursnif, Wireshark, Wireshark Tutorial |
Table of Contents
Scenario
Requirements
Quiz Material
Questions
Conclusion
Additional Resources
Scenario
A threat hunt revealed the same activity seen from the Unit 42 tweet in your organization Tuesday, March 7, 2023, at approximately 02:07 UTC.
Details of the local area network (LAN) for this month’s exercise follow.
- LAN segment range: 172.16.1[.]0/24 (172.16.1[.]1 through 172.16.1[.]255)
- Domain: pcapworkshop[.]net
- Domain Controller IP address: 172.16.1[.]16
- Domain Controller host name: PCAPWORKSHOP-DC
- LAN segment gateway: 172.16.1[.]1
- Land segment broadcast address: 172.16.1[.]255
Your Security Operations Center (SOC) provides a pcap, and you are tasked to determine who was infected. You should also find any notable differences between indicators from this month’s exercise pcap and indicators from this Gozi activity previously reported by Unit 42.
Requirements
This quiz requires Wireshark to review pcap files. However, Wireshark’s default settings are not optimized for web-based traffic commonly generated by malware. Therefore, we encourage participants in this quiz to customize Wireshark after installing it. To help, Unit 42 has published a series of tutorials and videos that include customizing Wireshark.
We recommend using a 3.x or later version of Wireshark, since it has more features, capabilities and bug fixes over previous Wireshark versions.
Furthermore, we recommend using a non-Windows environment like BSD, Linux or macOS to analyze malicious traffic. Malware traffic could contain malicious code targeting Microsoft Windows. This presents a risk of infection if participants use a Windows computer to analyze the pcap.
Quiz Material
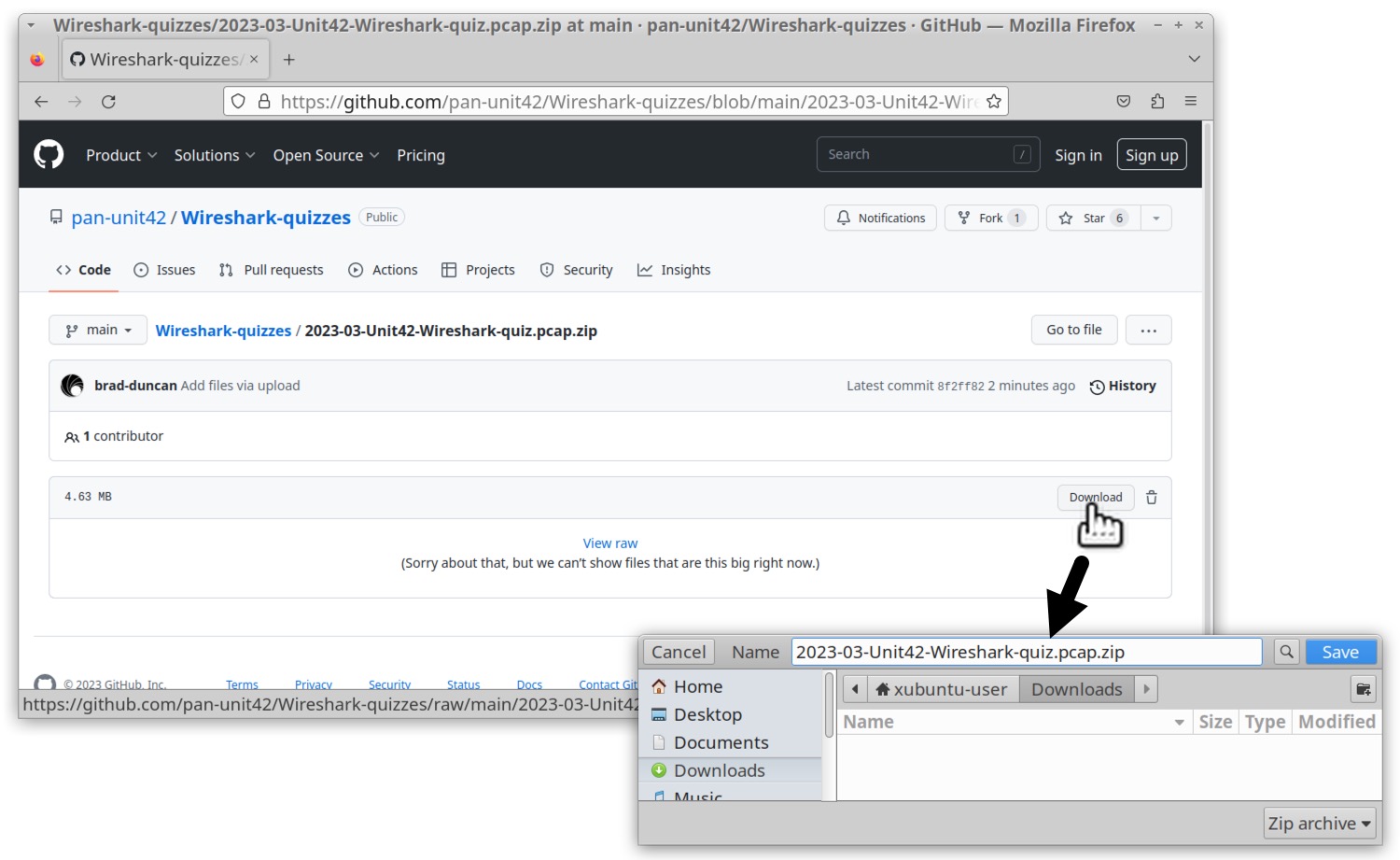
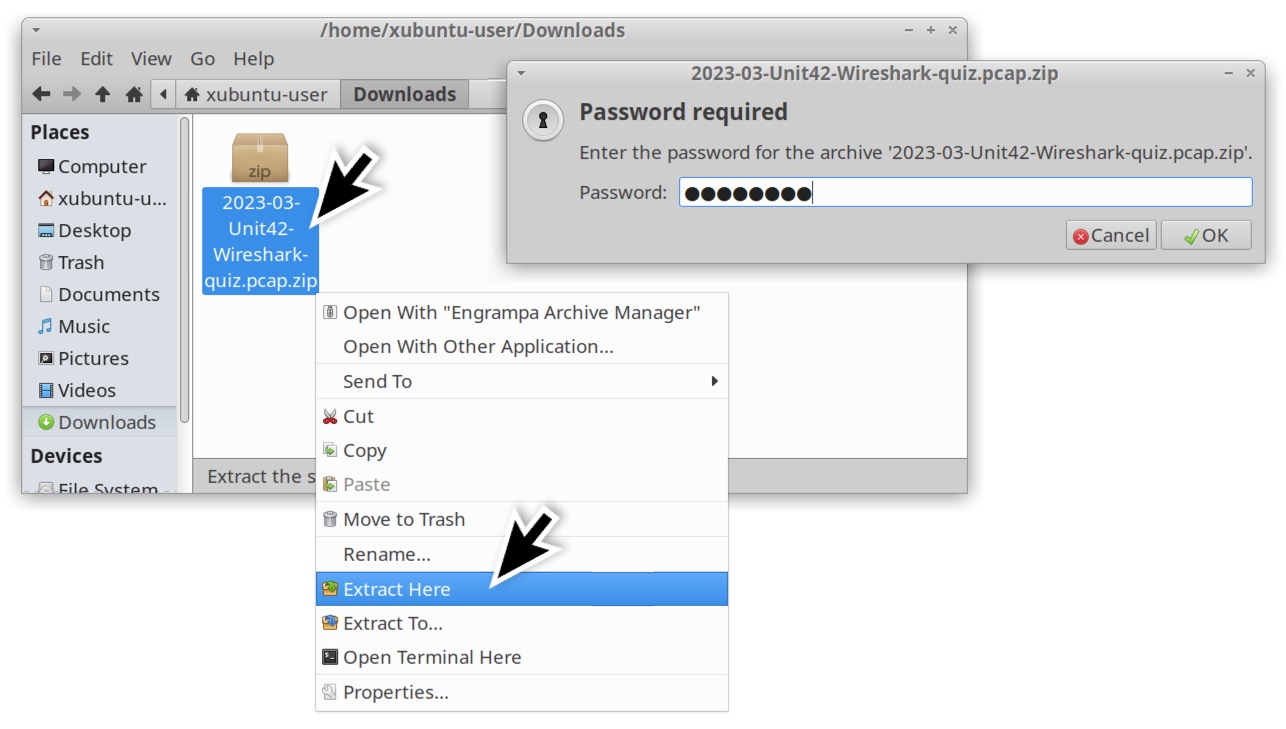
To obtain the pcap for this month’s quiz, visit our GitHub repository. Download the ZIP archive and extract the pcap as shown below in Figures 1 and 2. Use infected as the password to unlock the ZIP archive.
Questions
For this month’s Wireshark Quiz, answer the following questions:
- What is the IP address, host name and Windows user account name for the infected Windows client?
- What is the URL and SHA-256 hash of the ZIP archive downloaded by the infected Windows host?
- Can you find any notable differences between indicators from this Gozi infection and indicators from Gozi on March 6, 2023, reported by Unit 42?
Conclusion
Palo Alto Networks encourages the security community to continue developing our skills, so we can better protect ourselves against criminals and other cyberthreats. This month’s Wireshark quiz can help participants better detect Gozi, one of many different malware families in our current threat landscape.
The answers to this month’s Unit 42 Wireshark quiz will be published in a separate blog post on Monday, March 27.
Palo Alto Networks customers receive protections from Gozi and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services, including WildFire and Advanced Threat Prevention.
If you think you may have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Additional Resources
- Wireshark Tutorial: Wireshark Workshop Videos Now Available - Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, January 2023 - Unit 42, Palo Alto Networks
- Answers to January 2023 Unit 42 Wireshark Quiz - Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, February 2023 - Unit 42, Palo Alto Networks
- Answers to February 2023 Unit 42 Wireshark Quiz - Unit 42, Palo Alto Networks
- Unit 42 GitHub post - Indicators for Gozi (ISFB/Ursnif) from malspam targeting Italy
- Unit 42 tweet, March 9, 2023 - Malspam targeting Italy leads to Gozi (ISFB/Ursnif)
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh