
read file error: read notes: is a directory 2023-2-24 22:0:3 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:54 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
Welcome to the February 2023 Unit 42 Wireshark quiz. This blog presents a packet capture (pcap) of malicious activity and asks participants to write an incident report. A separate Unit 42 blog post will present the answers: an example of an incident report and detailed explanations for the report content.
These quizzes are designed for security professionals who investigate suspicious network activity, but anyone can participate. To get the most benefit, readers should understand basic network traffic concepts and be somewhat familiar with Wireshark.
The material provides experience reviewing real-world traffic from a live setting. This month’s Wireshark quiz uses a pcap of infection activity from an Active Directory (AD) environment.
Table of Contents
Scenario
Requirements
Quiz Material
Incident Report Format
Conclusion
Additional Resources
Scenario
The pcap for this month’s Wireshark quiz is from an AD environment, and it contains real-world traffic from a simulated enterprise setting. Details of the local area network (LAN) from the pcap follow.
- LAN segment range: 10.0.0[.]0/24 (10.0.0[.]0 through 10.0.0[.]255)
- Domain: work4us[.]org
- Domain Controller IP address: 10.0.0[.]6
- Domain Controller host name: WORK4US-DC
- LAN segment gateway: 10.0.0[.]1
- Land segment broadcast address: 10.0.0[.]255
Requirements
This quiz requires Wireshark to review pcap files. However, Wireshark’s default settings are not optimized for web-based traffic commonly generated by malware. Therefore, we encourage participants in this quiz to customize Wireshark after installing it. To help, Unit 42 has published a series of tutorials and videos that include customizing Wireshark.
We recommend using a 3.x or later version of Wireshark, since it has more features, capabilities and bug fixes over previous Wireshark versions.
Furthermore, we recommend using a non-Windows environment like BSD, Linux or macOS to analyze malicious traffic. Malware traffic could contain malicious code targeting Microsoft Windows. This presents a risk of infection if participants use a Windows computer to analyze the pcap.
Quiz Material
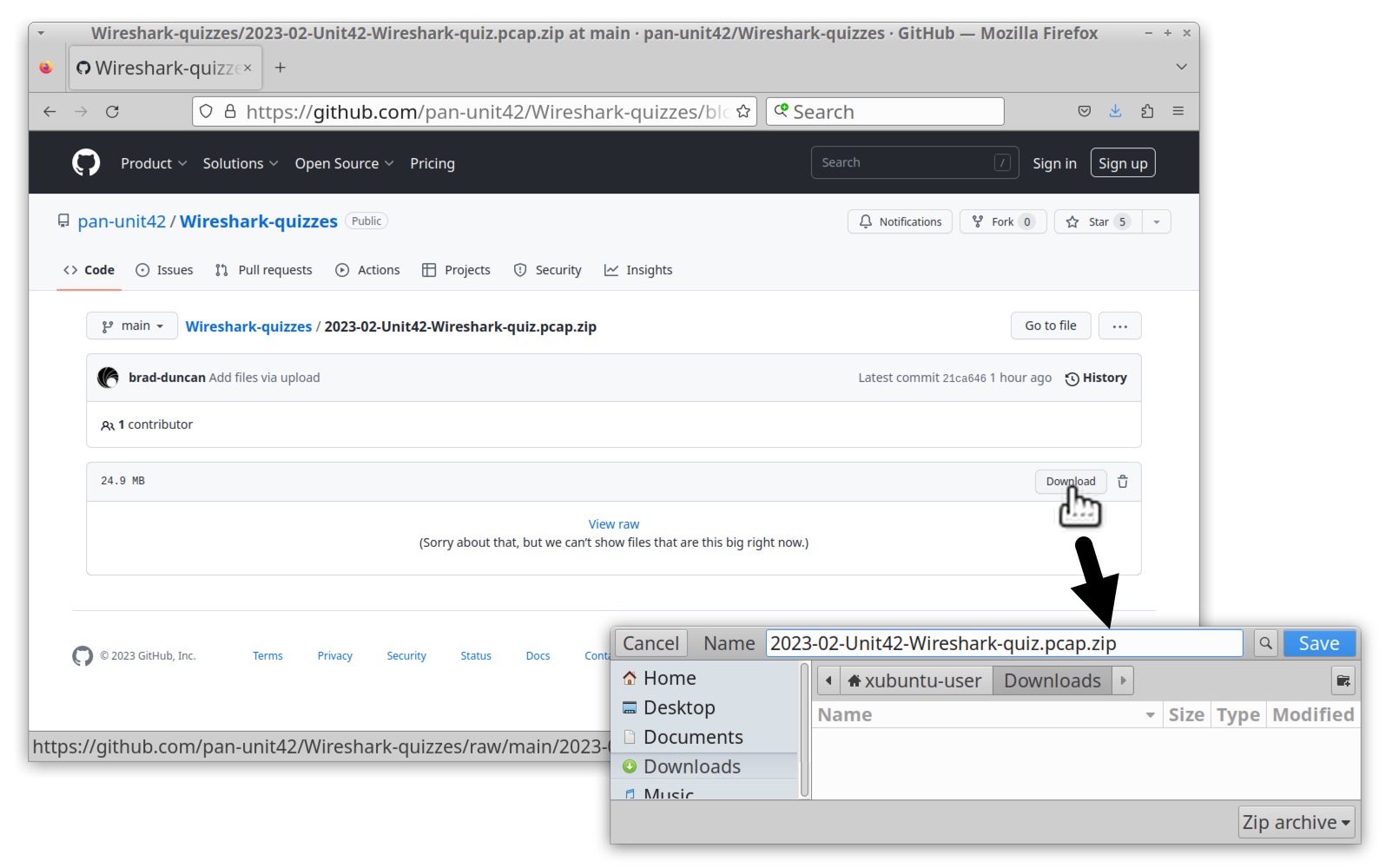
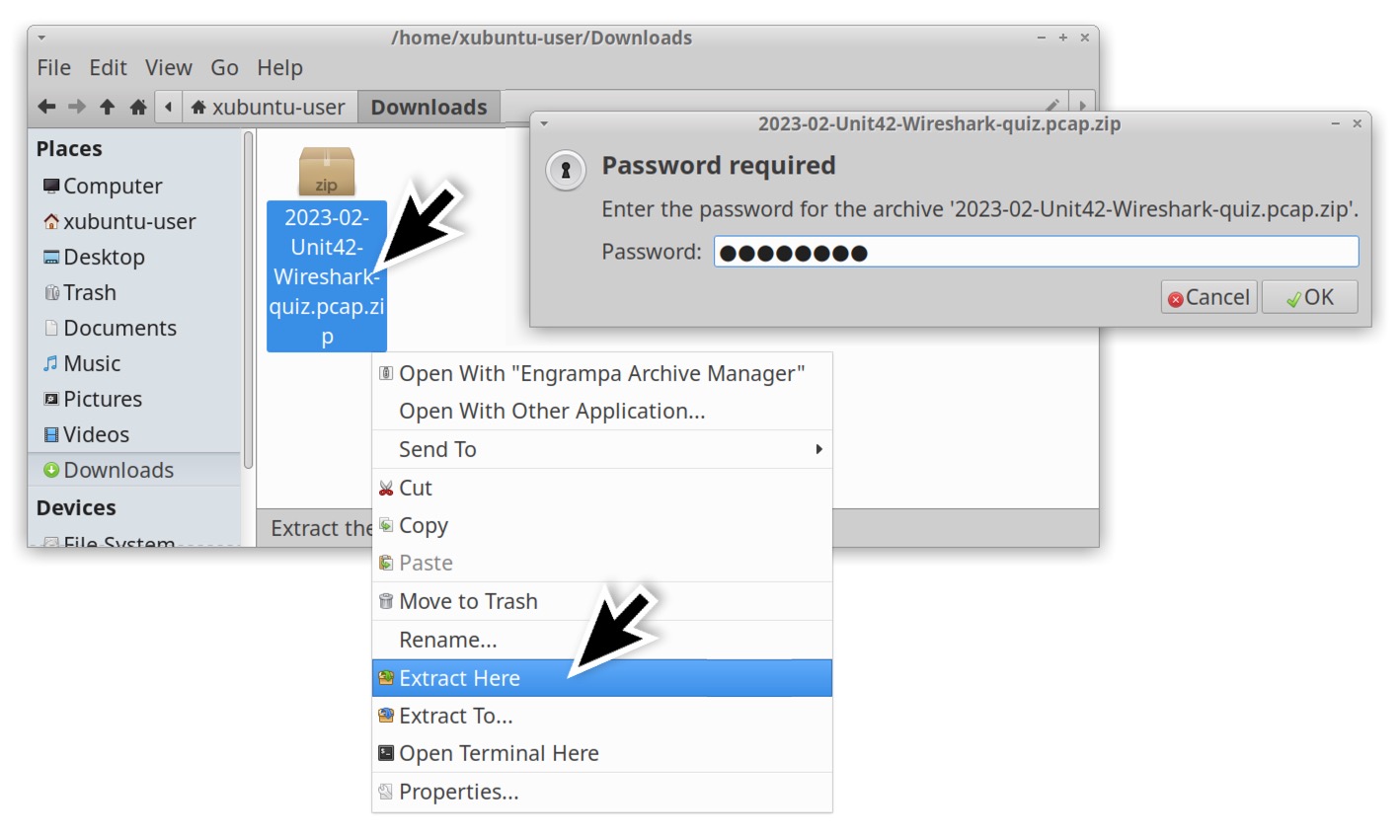
To obtain the pcap for this month’s quiz, visit our GitHub repository. Download the ZIP archive and extract the pcap as shown below in Figures 1 and 2. Use infected as the password to unlock the ZIP archive.
Incident Report Format
In this scenario, quiz participants provide an incident report to document the infection. Depending on your workplace requirements, incident report formats vary. For this month’s Unit 42 Wireshark quiz, we recommend a generic format applicable to many situations. Our recommended incident report format contains the following three sections:
- Executive summary
- Victim details
- Indicators of compromise (IoCs)
The executive summary is a paragraph describing the incident. This should give the reader a clear idea of what happened. The executive summary states the type of malicious activity and any corrective actions taken. An example follows.
On 2023-02-01 at 12:53 UTC, a Windows computer used by John Doe was infected with unknown, Windows-based malware. Security confiscated the infected host at 13:15 UTC, then help desk personnel wiped and re-imaged it. John Doe changed his login password and was instructed to change any other passwords used on the infected computer.
Most of the summary lists corrective actions. But our quizzes focus on analysis of the event, so we only require the first sentence.
On [date] at [time in UTC], a Windows computer used by [victim’s name] was infected with [name of malware, if known].
The victim details section contains the following information:
- Victim’s IP address
- Victim’s MAC address
- Victim’s Windows host name
- Victim’s Windows user account name
In the AD environments used for our Wireshark quizzes, all Windows user account names are formatted as firstname.lastname. For example, the user account for someone named John Doe would be john.doe.
Finally, the IoCs section consists of IP addresses, port numbers, domain names and URLs associated with the infection. Include file information if any malicious binaries from an infection can be exported from the pcap, like SHA256 hash and file size.
Conclusion
When network traffic is available, pcap analysis of an infection provides valuable insight on the activity. This insight helps security personnel identify the victim and determine the time of infection. Data from a pcap might also provide indicators that help identify the malware.
Reviewing traffic from real-world infections can help members of the security community secure their networks and better protect our digital way of life. Incident reports help investigators organize their findings in a more easily digestible format. Security professionals who write incident reports are better able to recognize similar activity. A well-written report helps other people within the organization take appropriate steps to prevent the incident from happening again.
The answers to this month’s Unit 42 Wireshark quiz will be published in a separate blog post on Monday, Feb. 27.
Palo Alto Networks customers receive protections from Qakbot and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services, including WildFire and Advanced Threat Prevention.
If you think you may have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Additional Resources
- Wireshark Tutorial: Wireshark Workshop Videos Now Available - Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, January 2023 - Unit 42, Palo Alto Networks
- Answers to January 2023 Unit 42 Wireshark Quiz - Unit 42, Palo Alto Networks
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh