
read file error: read notes: is a directory 2023-1-23 22:0:56 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:39 收藏
This post is also available in: 日本語 (Japanese)
Executive Summary
This blog presents the answers for our January 2023 Unit 42 Wireshark quiz. The information is ideal for security professionals who investigate suspicious network activity, but everyone is welcome to review. To get the most benefit, readers should understand basic network traffic concepts and be familiar with Wireshark.
If you’d like to view the version without answers, please see the standalone quiz post.
| Related Unit 42 Topics | AgentTesla, OriginLogger, pcap, Wireshark, Wireshark Tutorial |
Table of Contents
Background, Requirements and Quiz Material
Quiz Questions
Quiz Answers
Pcap Analysis
Conclusion
Additional Resources
Background, Requirements and Quiz Material
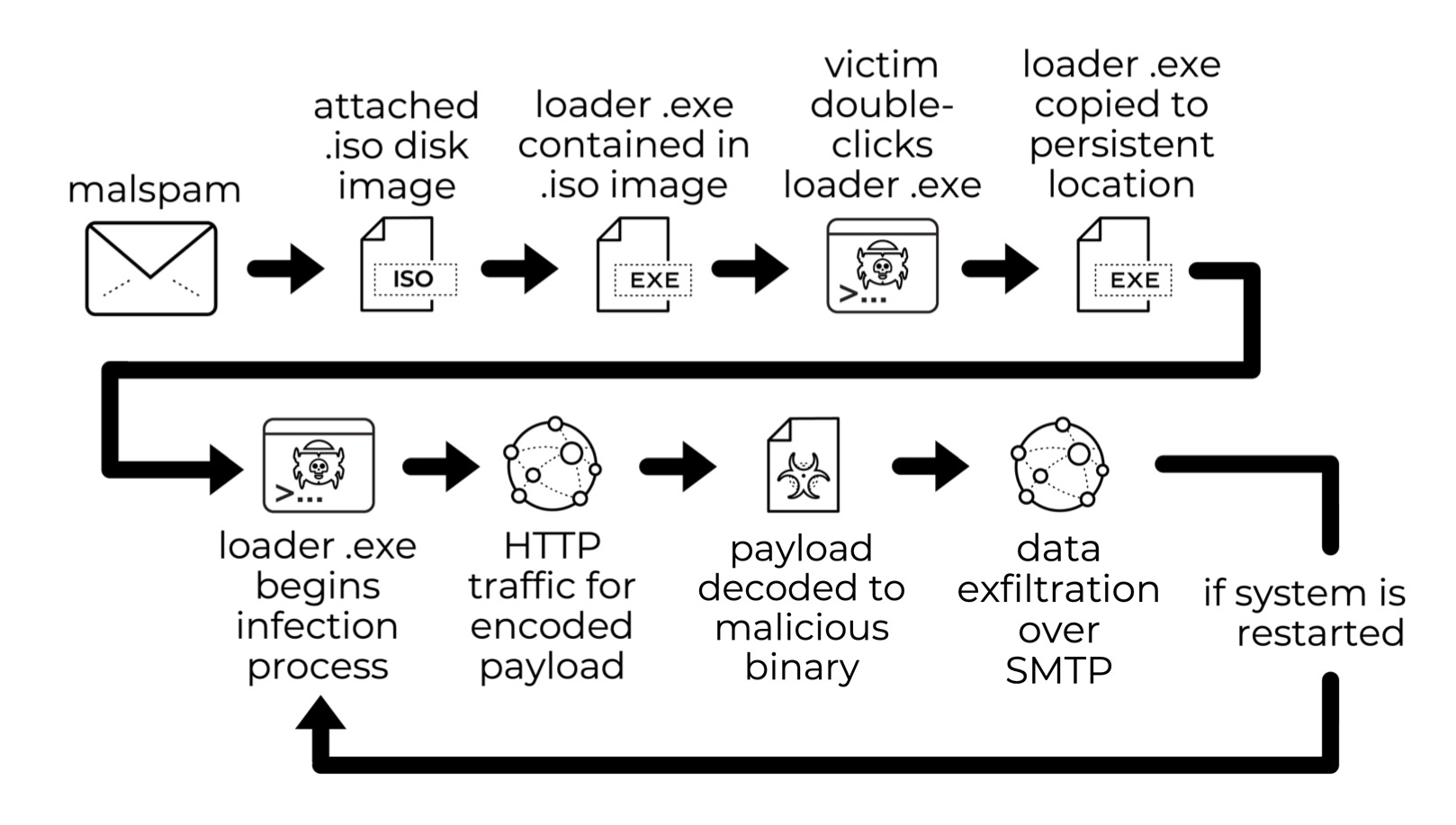
This quiz is based on a Palo Alto Networks Unit 42 tweet about Agent Tesla-style activity from a possible OriginLogger infection that was found Thursday, Jan. 5, 2023. Figure 1 provides a chain of events from the infection.
Our investigation for this month’s quiz requires Wireshark. This blog utilizes a recent version of Wireshark, and we recommend Wireshark version 3.x. We also use the Thunderbird email client to review an email extracted from the packet capture (pcap).
Participants should have some basic knowledge of network traffic fundamentals. We also recommend readers customize their Wireshark display to better analyze web traffic. A list of tutorials and videos is available. As always, we recommend using Wireshark in a non-Windows environment like BSD, Linux or macOS when analyzing malicious Windows-based traffic.
To obtain the pcap, visit our Github repository. Download the ZIP archive and extract the pcap. Use infected as the password to unlock the ZIP archive.
Quiz Questions
The Unit 42 Wireshark quiz for January 2023 has the following questions:
- When did the malicious traffic start in UTC?
- What is the victim’s IP address?
- What is the victim’s MAC address?
- What is the victim’s Windows host name?
- What is the victim’s Windows user account name?
- How much RAM does the victim’s host have?
- What type of CPU is used by the victim’s host?
- What is the public IP address of the victim’s host?
- What type of account login data was stolen by the malware?
Quiz Answers
The answers for our January 2023 Unit 42 Wireshark quiz are:
- The malicious traffic started 2023-01-05 at 22:51 UTC
- Victim’s IP address: 192.168.1[.]27
- Victim’s MAC address: bc:ea:fa:22:74:fb
- Victim’s Windows host name: DESKTOP-WIN11PC
- Victim’s Windows user account name: windows11user
- Amount of victim’s RAM on victim’s host: 32 MB
- Victim’s CPU: Intel(R) Core(TM) i5-13600K
- Victim’s public IP address: 173.66.46[.]112
- Type of stolen account data: email and web accounts
Pcap Analysis
Our analysis assumes you have customized Wireshark according to our tutorials or workshop videos.
Analyzing the pcap requires a basic knowledge of network traffic. You should understand that a router acts as a gateway between public-facing IP addresses and hosts within an internal network.
Participants should recognize internal, non-routable IPv4 addresses. We commonly find one of three classes for non-routable internal IPv4 addresses behind an internet router:
- Class A: 10.0.0[.]0/8 (10.0.0[.]0 through 10.255.255[.]255)
- Class B: 172.16.0[.]0/12 (172.16.0[.]0 through 172.31.255[.]255)
- Class C: 192.168.0[.]0/16 (192.168.0[.]0 through 192.168.255[.]255)
In most pcaps, the victim’s IP address is from the internal network. For this month’s pcap, our victim is using a Class C non-routable IP address in the 192.168.0[.]0/16 range.
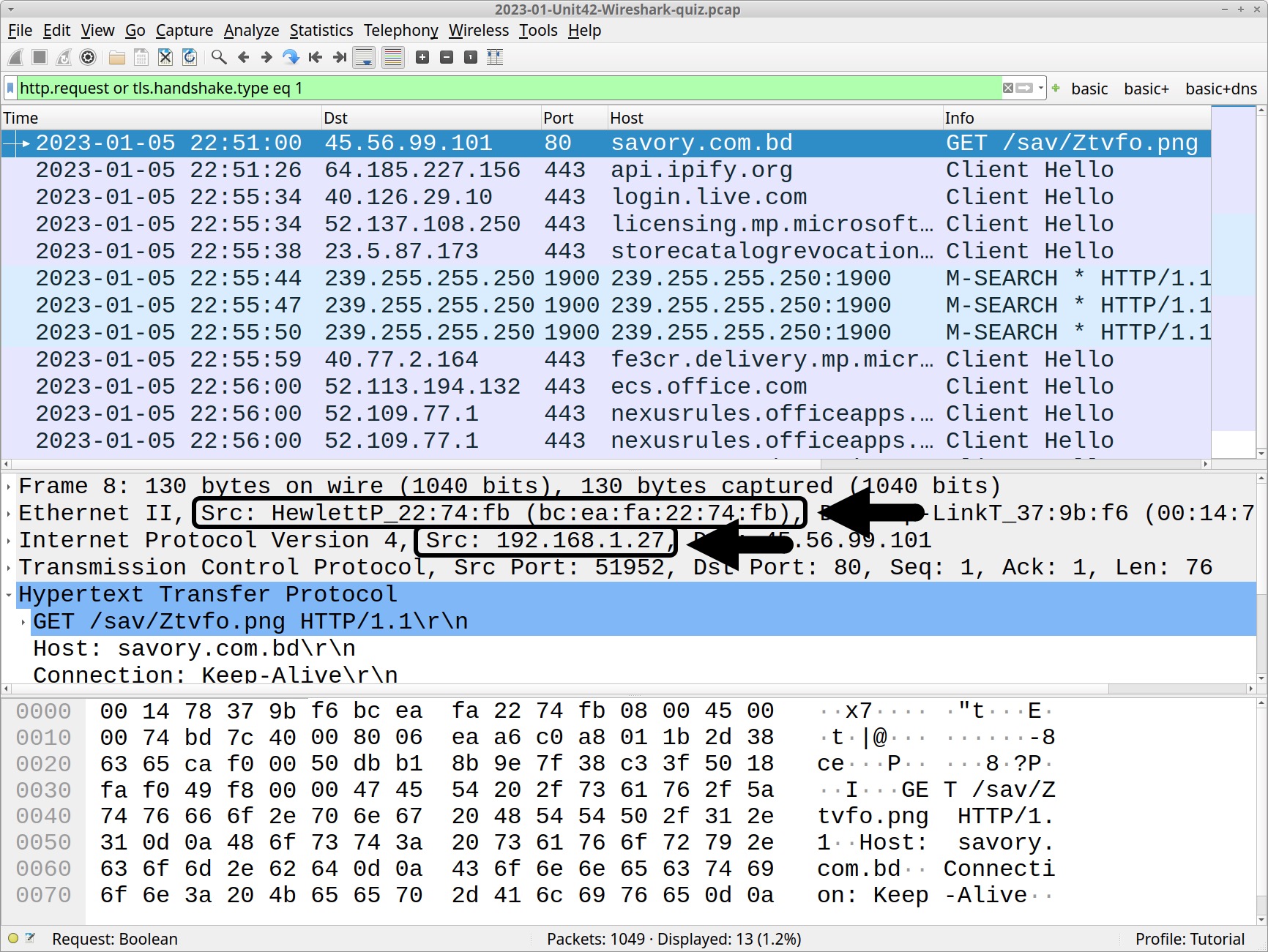
How do we find the victim’s IP address? Use the basic web filter provided in our Wireshark tutorials, or type the following in your Wireshark filter bar:
http.request or tls.handshake.type eq 1
In the frame details panel for any frame listed in the column display, the source IP address should be 192.168.1[.]27. The frame details also provide a MAC address that corresponds to 192.168.1[.]27 as shown below in Figure 2.
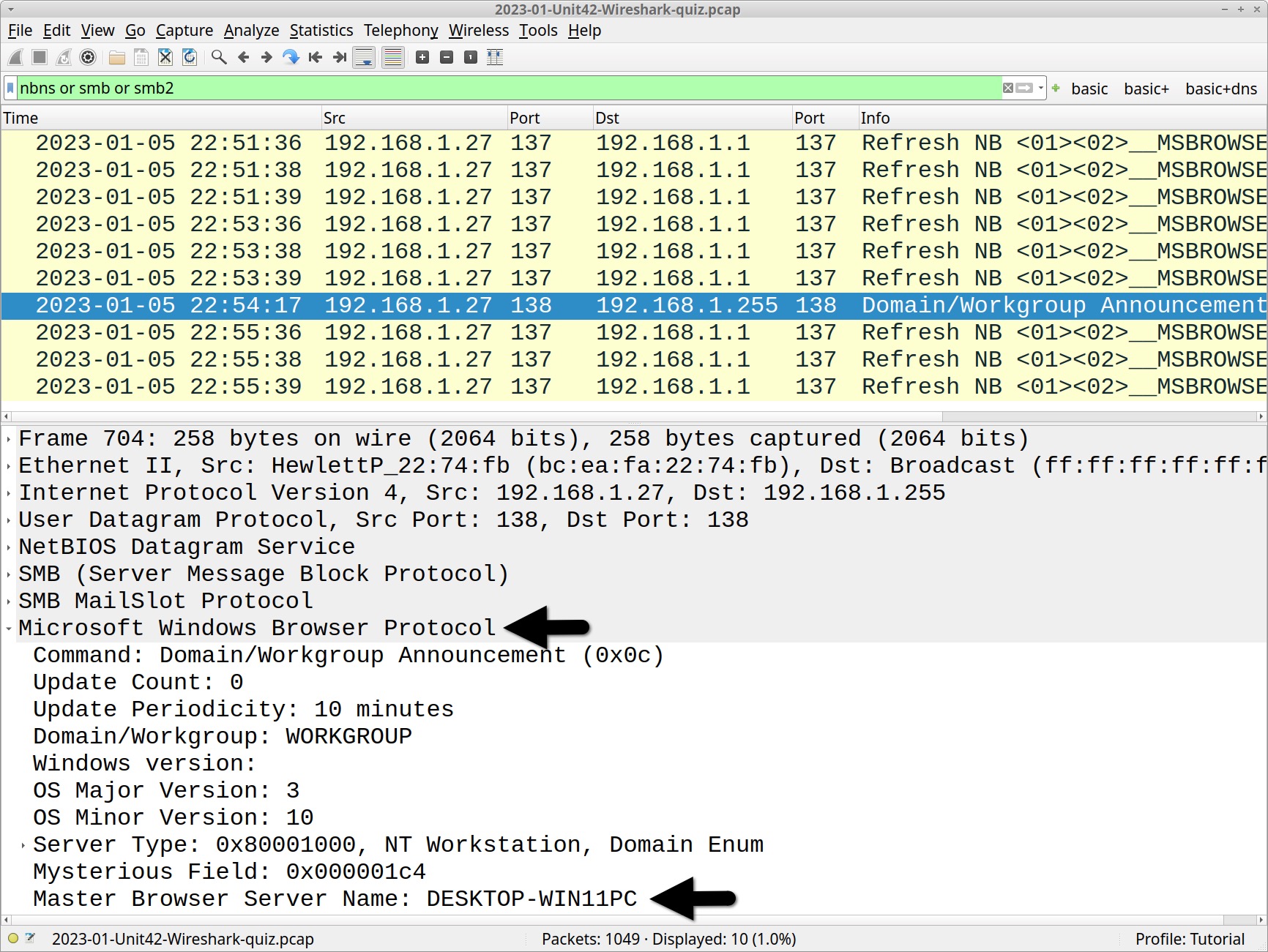
In some pcap files, NBNS or SMB traffic provides a victim’s Windows host name. Use the following filter in Wireshark:
nbns or smb or smb2
The default host name for a Windows 10 and Windows 11 computer is a 15 character string. The name starts with DESKTOP- and is followed by an alpha-numeric string of seven additional ASCII characters. In Figure 3, we find DESKTOP-WIN11PC in the frame details from one of the frames in the column display.
Please note that threat actors often abuse legitimate products and operating system features for malicious purposes. This does not necessarily imply a flaw or malicious quality to the legitimate software being abused.
The remaining information for this quiz is from stolen data in the unencrypted SMTP traffic. Type smtp in your Wireshark filter. The results reveal several frames as shown below in Figure 4.
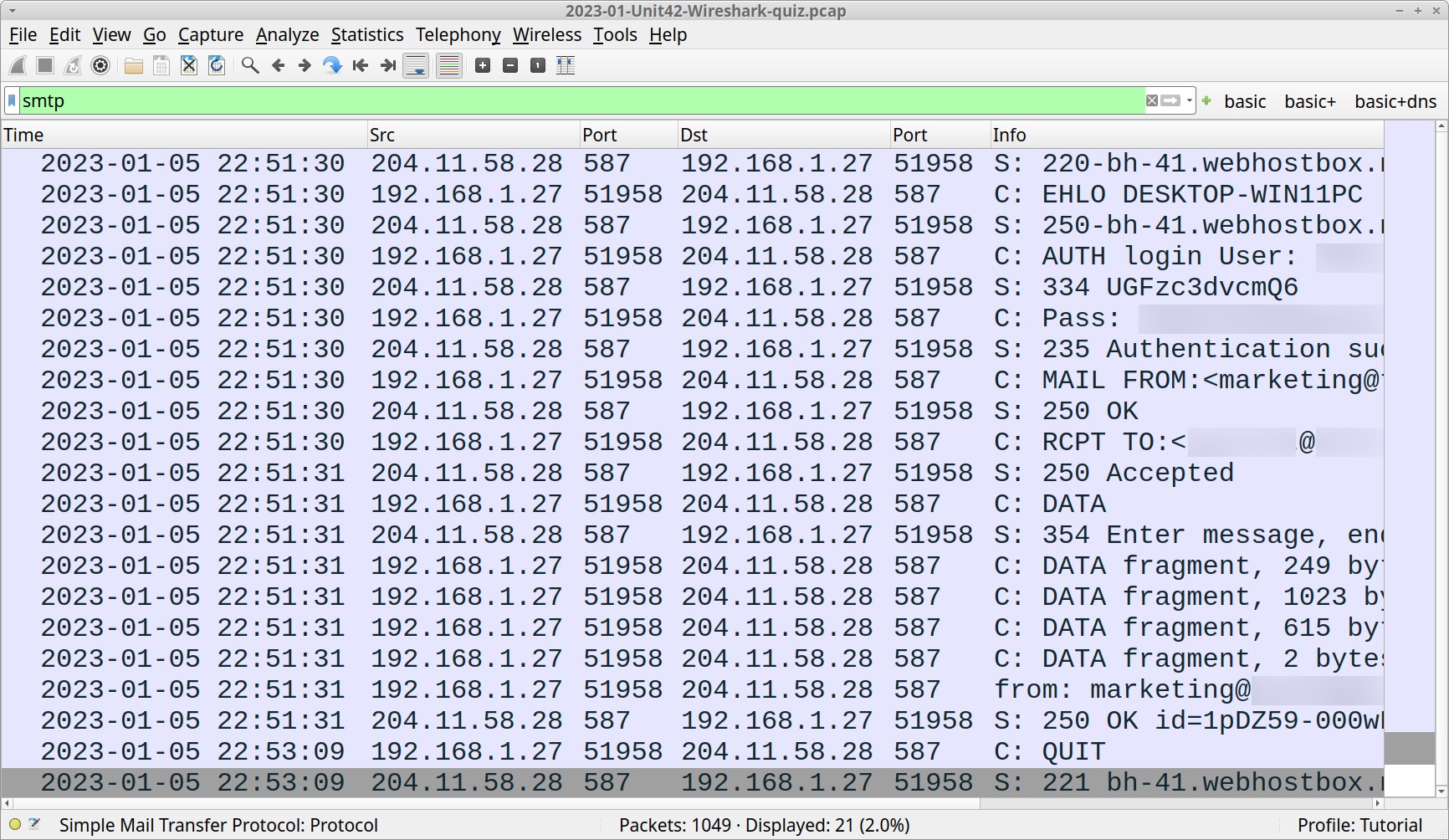
These frames represent a single TCP stream of traffic. Follow the TCP stream to review the associated email as shown in Figures 5 and 6.
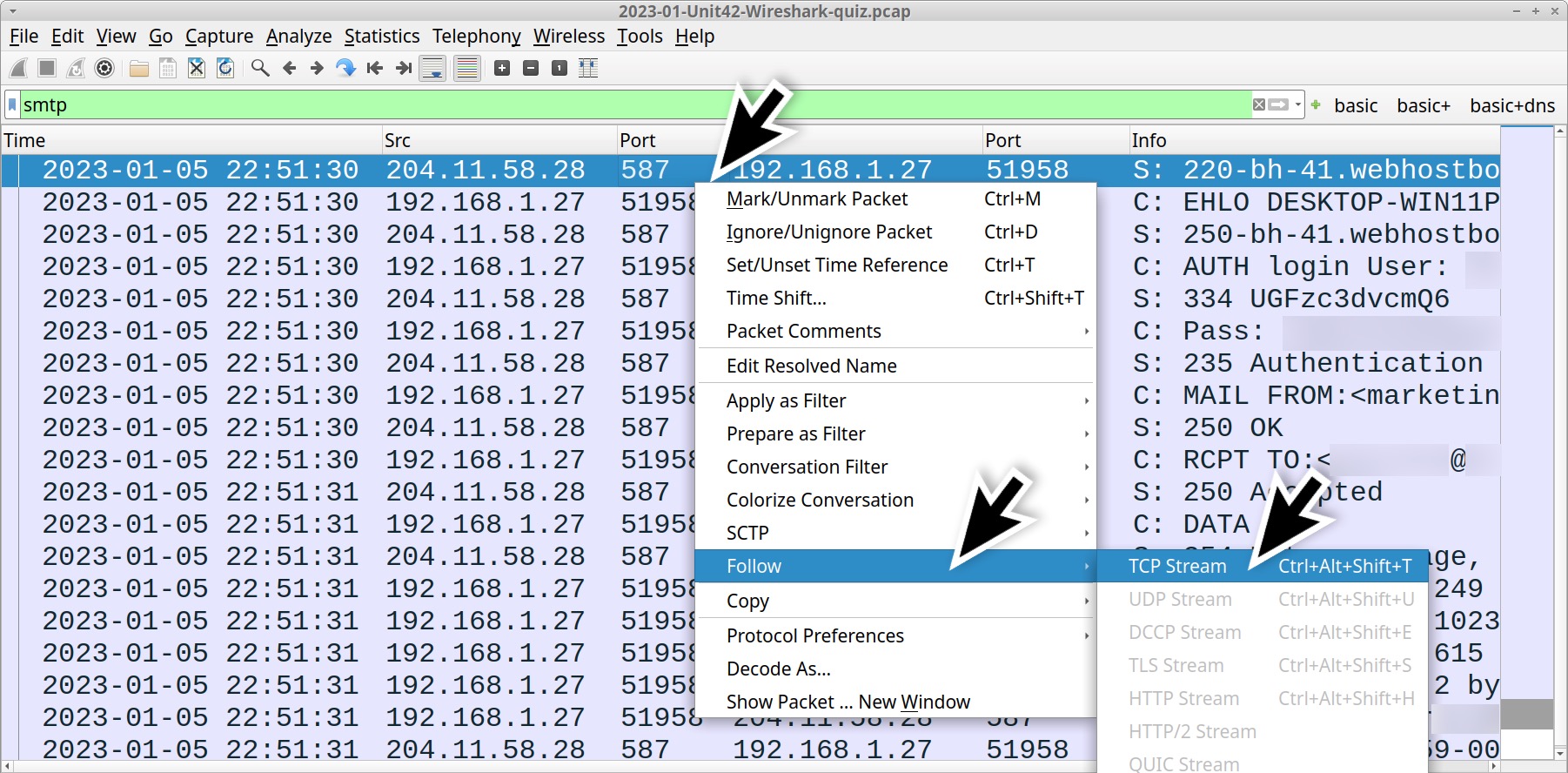
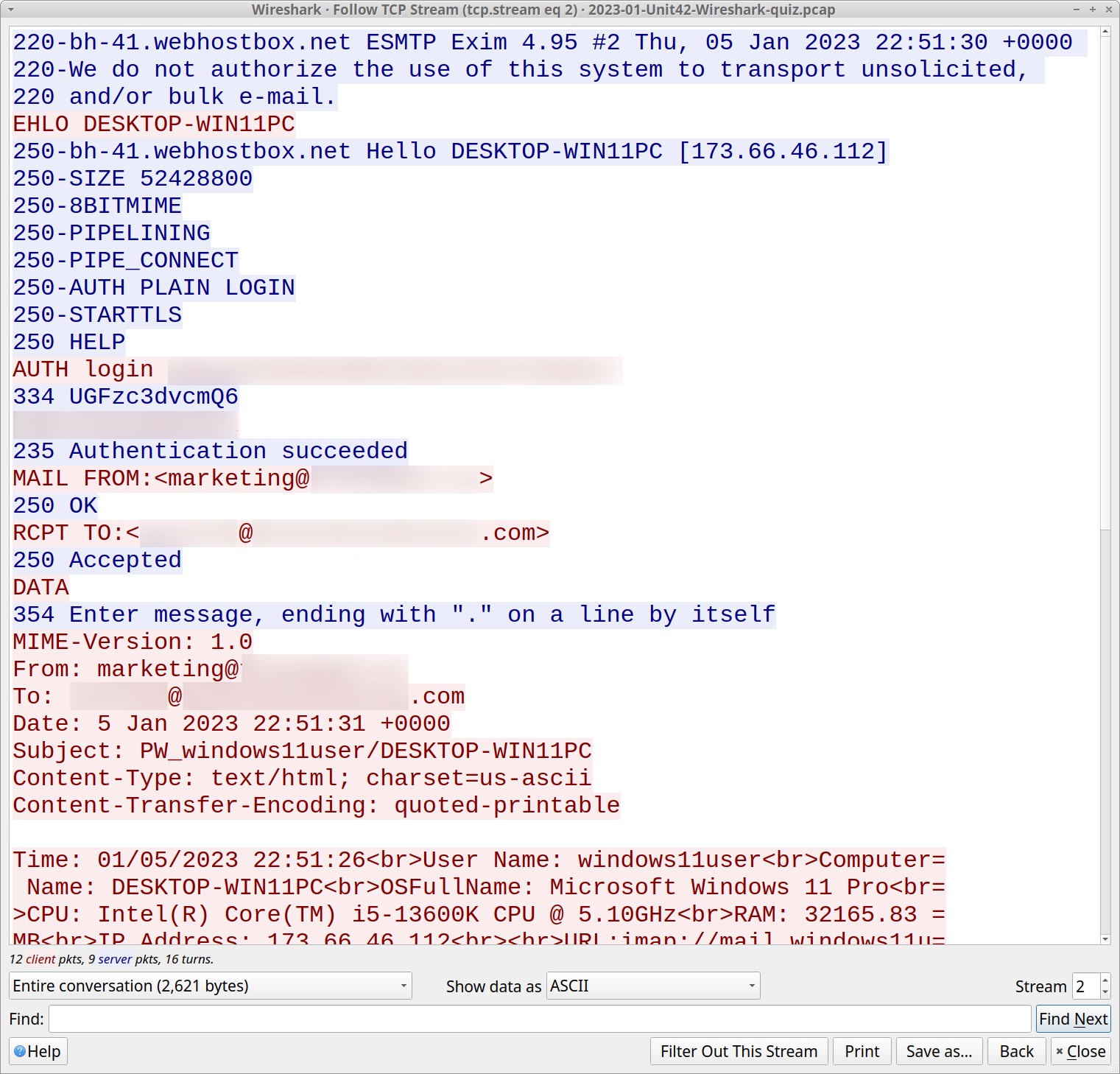
Figure 6 shows the infected Windows host using one email address to relay stolen data to another address. The recipient address collects similar data from other hosts infected by the same malware. The message text has HTML tags, and it is somewhat cumbersome to read.
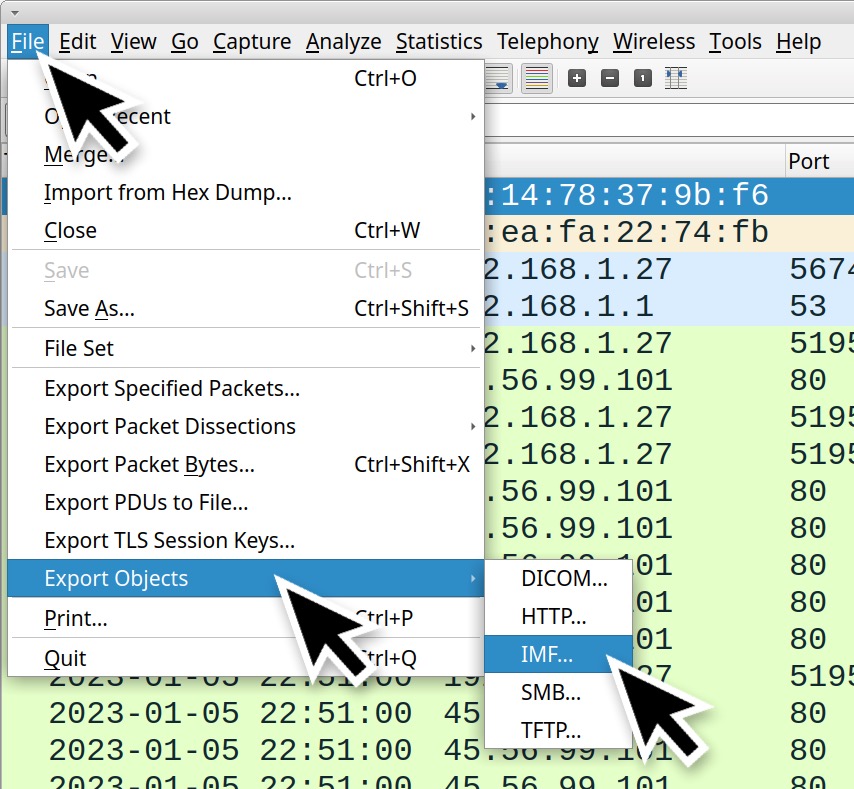
To more easily view this stolen data, export the email from our pcap, then open the exported file in a Thunderbird email client. Use the following menu chain in Wireshark:
File → Export Objects → IMF
Actions to export the email from the pcap in Wireshark should look similar to Figures 7 and 8.
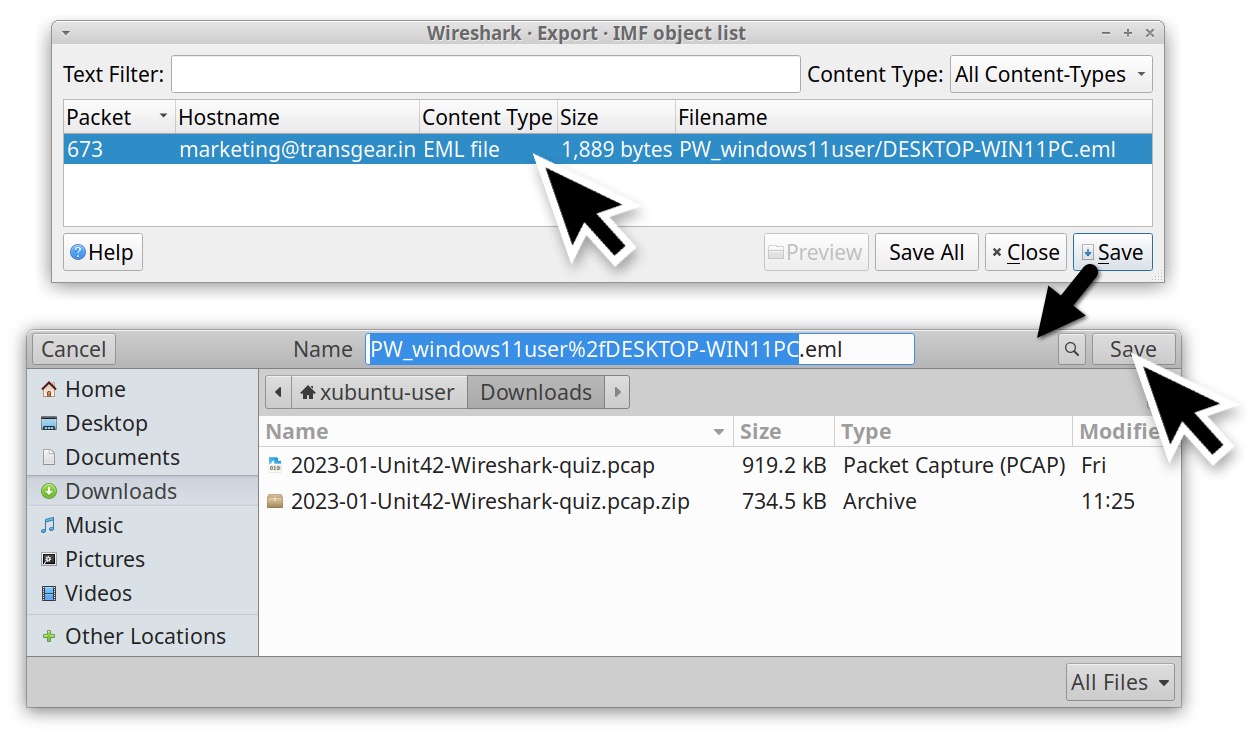
Once the email has been saved, open the file in Thunderbird to see the content. Figure 9 shows the exported message viewed in Thunderbird.
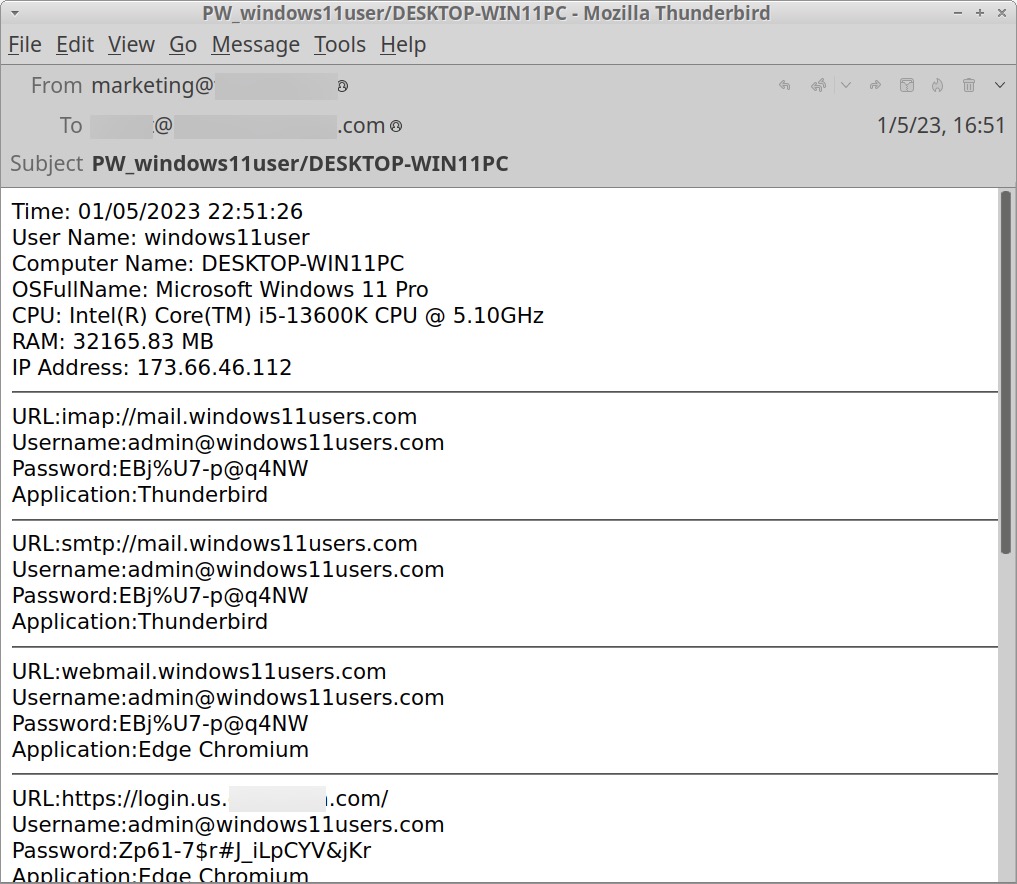
The email contains information about the infected Windows host, including account credentials saved by the victim’s email client (Thunderbird) and web browser (Microsoft Edge). Stolen data includes information such as the operating system, Windows user account name, CPU, amount of RAM and public IP address of the infected host.
Of note, none of these are legitimate login credentials. Before running the malware, we populated the host with fake login data. However, the traffic illustrates the type of data stolen by Agent Tesla variants like OriginLogger.
Conclusion
This blog provides answers to our Unit 42 Wireshark quiz for January 2023. We reviewed traffic from the pcap to answer characteristics of the infected Windows host, and we discovered what type of data this malware steals.
Many organizations lack access to full packet capture in their IT environment. As a result, many security professionals lack experience in reviewing network traffic. Training material like this Wireshark quiz can help. Pcap analysis is a useful skill that helps us better understand malicious activity.
You can also find the original post, without answers, for this month’s Unit 42 Wireshark quiz.
Palo Alto Networks customers receive protections from Agent Tesla variants like OriginLogger through Cortex XDR and our Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention.
If you think you may have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Additional Resources
Wireshark Tutorial: Wireshark Workshop Videos Now Available – Unit 42, Palo Alto Networks
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh