
read file error: read notes: is a directory 2023-1-20 22:0:39 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:51 收藏
This post is also available in: 日本語 (Japanese)
Executive Summary
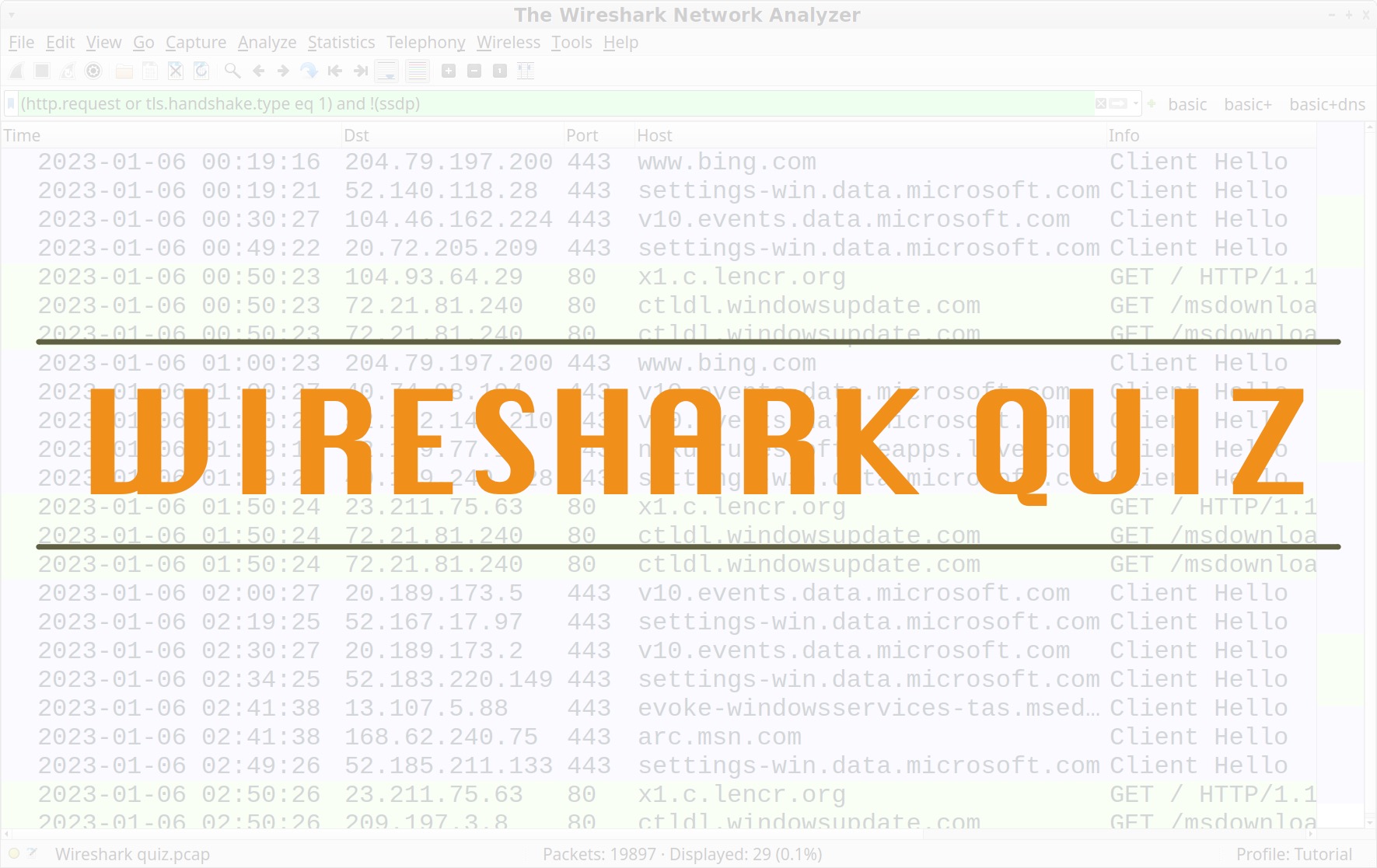
Welcome to the January 2023 Unit 42 Wireshark quiz. This blog presents a packet capture (pcap) of malicious activity and asks questions based on information derived from the network traffic. A separate Unit 42 blog post will present the answers with detailed explanations.
These quizzes are designed for security professionals who investigate suspicious network activity, but anyone can participate. To get the most benefit, readers should understand basic network traffic concepts and be somewhat familiar with Wireshark.
The material provides experience reviewing real-world traffic from a live environment.
| Related Unit 42 Topics | AgentTesla, OriginLogger, pcap, Wireshark, Wireshark Tutorial |
Table of Contents
Background
Requirements
Quiz Material
Quiz Questions
Conclusion
Additional Resources
Background
Earlier this month, Palo Alto Networks Unit 42 tweeted about Agent Tesla-style activity from a possible OriginLogger infection that was found Thursday, Jan. 5, 2023. The original tweet contains our initial analysis. You can also find further information on the associated malware binary.
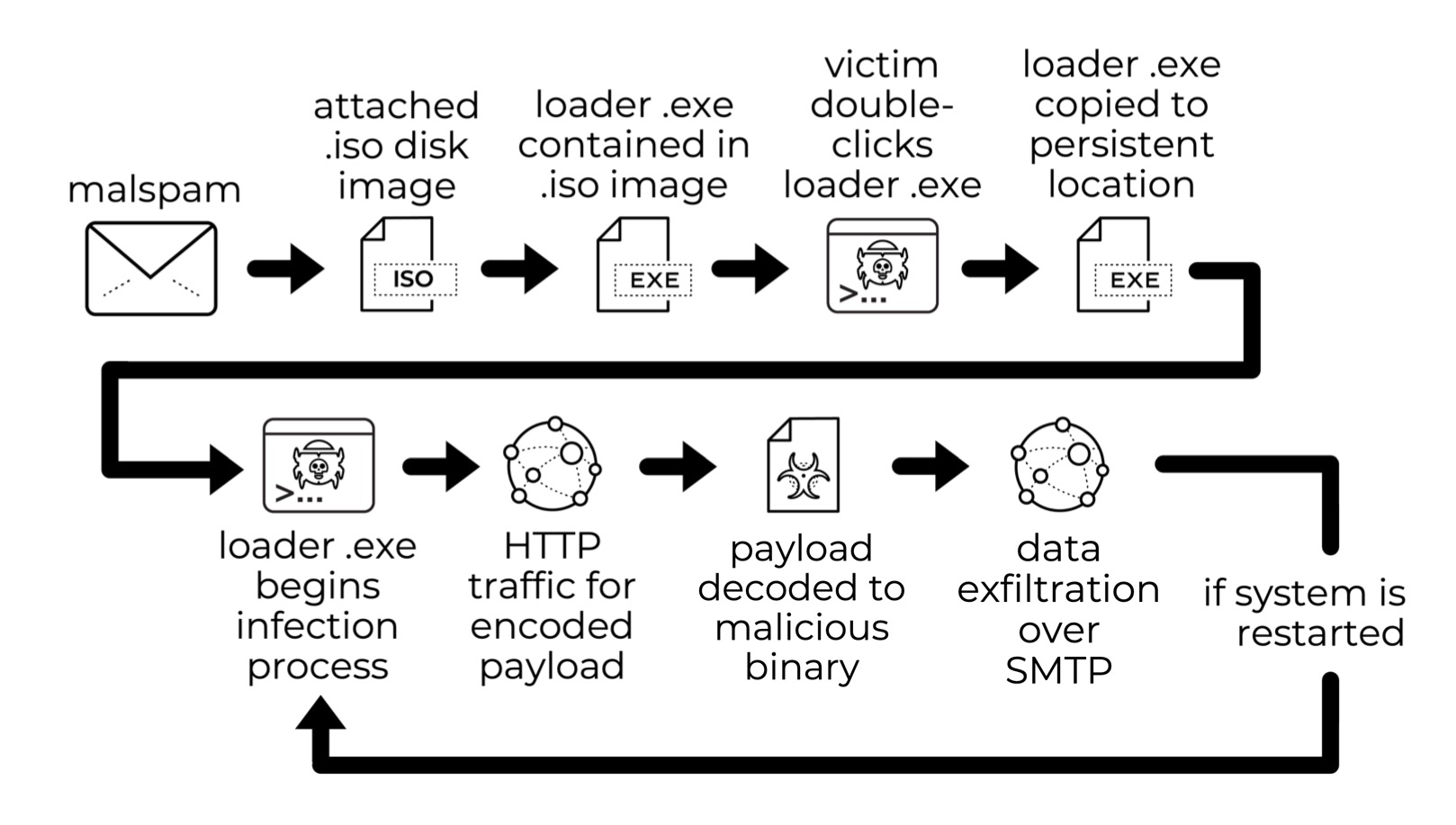
For this month’s exercise, we generated a pcap of network traffic from this malware sample. Post-infection activity contains unencrypted SMTP traffic with data stolen from the infected computer.
Requirements
Our analysis requires Wireshark, a well-known tool used to review pcaps. However, its default settings are not optimized for web-based malware traffic. Therefore, we encourage people to customize Wireshark after installing it. To help, Unit 42 has published a series of tutorials and videos that include customizing Wireshark.
We recommend using the latest 3.x version of Wireshark, since it has more features, capabilities and bug fixes over previous Wireshark versions.
Furthermore, we recommend using a non-Windows environment like BSD, Linux or macOS to analyze malicious traffic. The pcap for this quiz contains HTTP traffic of an obfuscated binary. If decoded, this binary becomes a malicious DLL file, as previously noted in the indicators for this infection posted on Github. The decoded malware presents a risk of infection when using a Windows computer.
Quiz Material
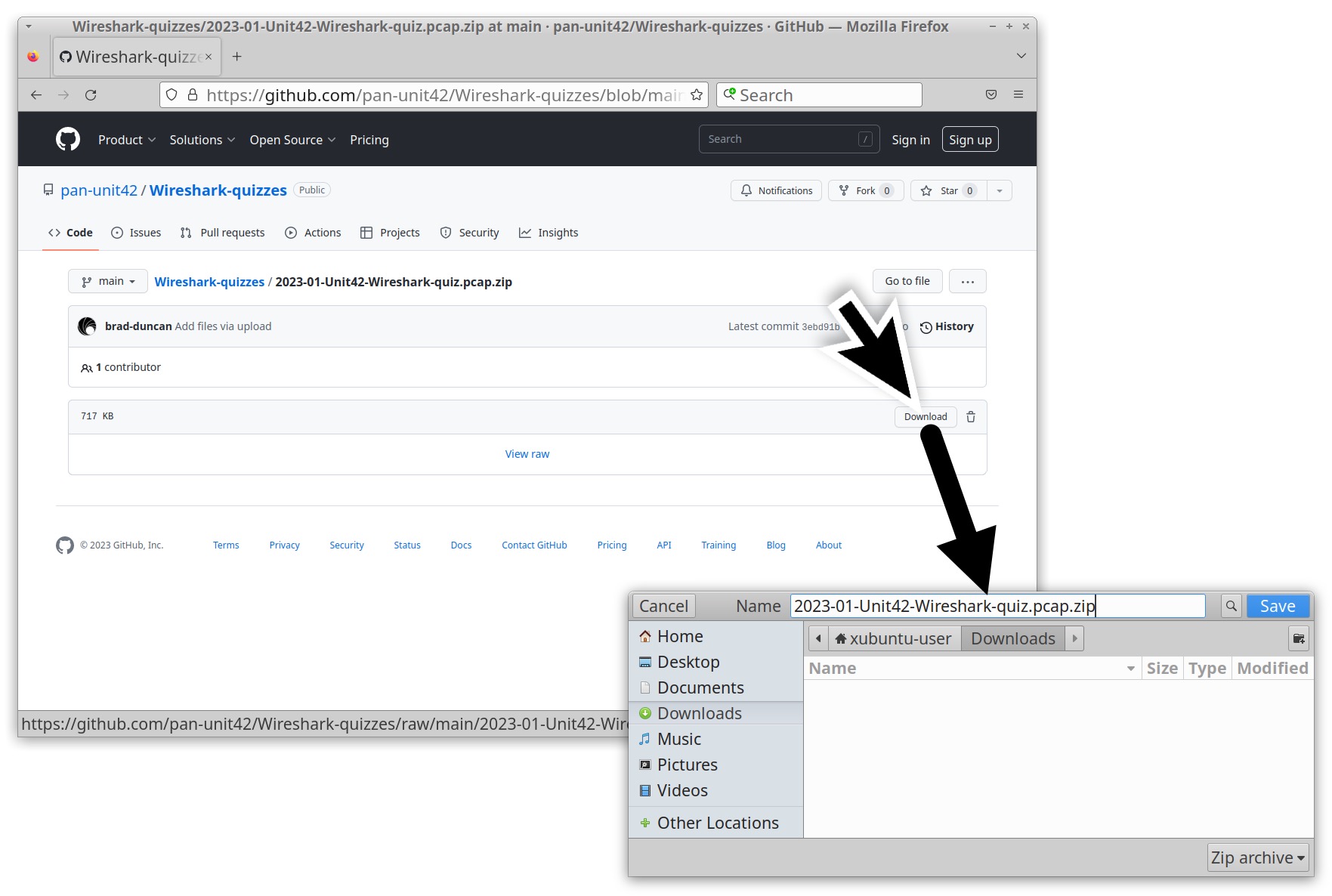
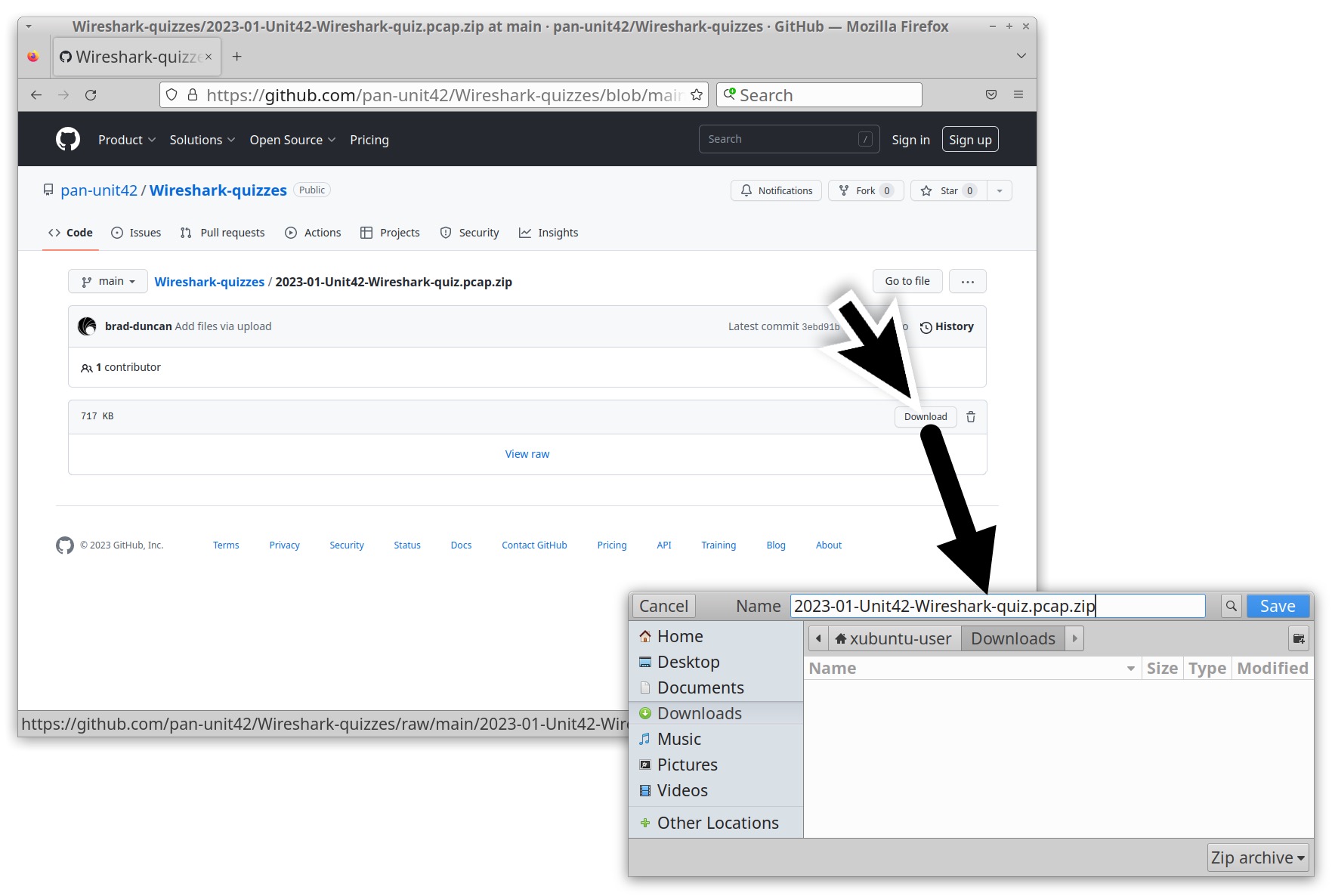
To obtain the pcap for this month’s quiz, visit our Github repository. Download the ZIP archive and extract the pcap as shown below in Figures 2 and 3. Use infected as the password to unlock the ZIP archive.
Quiz Questions
When did this activity first occur? Format your answer as Universal Coordinated Time (UTC). When sharing threat intelligence, UTC ensures recipients understand the exact time regardless of time zone.
Can you identify the infected host? For a Windows computer, the basic identifiers are the following:
- Victim’s IP address
- Victim’s MAC address
- Victim’s Windows host name
- Victim’s WIndows user account name
This month, our infected host is a stand-alone Windows client. In addition to Windows system traffic, the pcap also contains unencrypted SMTP traffic generated by the malware. This traffic contains additional information, so we can determine all four of the above identifiers.
The SMTP traffic includes various login credentials from the infected host. Of note, this traffic does not contain legitimate credentials. We populated the host with fake login data before we ran the malware. Despite the fake data, this traffic provides a better understanding of data stolen by Agent Tesla variants like OriginLogger.
Review the pcap and answer the following questions for this month’s Unit 42 Wireshark quiz:
- When did the malicious traffic start in UTC?
- What is the victim’s IP address?
- What is the victim’s MAC address?
- What is the victim’s Windows host name?
- What is the victim’s Windows user account name?
- How much RAM does the victim’s host have?
- What type of CPU is used by the victim’s host?
- What is the public IP address of the victim’s host?
- What type of account login data was stolen by the malware?
Conclusion
Palo Alto Networks encourages members of the security community to develop their skills, so we can all better protect our digital way of life. This month’s Wireshark quiz can help participants accomplish that goal.
The answers to this month’s Unit 42 Wireshark quiz will be published in a separate blog post on Monday, Jan. 23.
Palo Alto Networks customers receive protections from Agent Tesla variants like OriginLogger through Cortex XDR and our Next-Generation Firewall with cloud-delivered security services including WildFire and Advanced Threat Prevention.
If you think you may have been compromised or have an urgent matter, contact the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Additional Resources
Wireshark Tutorial: Wireshark Workshop Videos Now Available – Unit 42, Palo Alto Networks
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh