2022-10-28 08:0:0 Author: blog.didierstevens.com(查看原文) 阅读量:17 收藏
The Making Of: qa-squeaky-toys.docm
Filed under: Hacking — Didier Stevens @ 0:00
qa-squeaky-toys.docm is a challenge I made for CSCBE 2022.
It’s a Word document with VBA code. But the VBA code has been “cleaned” by an anti-virus.
I was inspired by a real maldoc cleaned by a real anti-virus: “Maldoc Cleaned by Anti-Virus“.
Here is how I made this challenge.
I created a .docm file with the following vba code:

I extracted the vbaProject.bin file from the OOXML file (.docm).
First, I removed all the compiled VBA code from stream 3. -s 3c selects the compiled code stored in VBA stream 3.

I open a copy of vbaProject.bin with a binary editor, and search for the bytes of the compiled code. And I set them all to 0x00.
Then at position 0x40 inside that stream, I write this ASCII test: “Cleaned by your favorite anti-virus!”.
Next I will shorten the compressed VBA source code. This is the compressed VBA source code (selected with 3v):

Value F4B0 is a little-endian integer: 0xB0F4. B are some flags, F4 is the length of the chunk of compressed VBA code. F4 hexadecimal is 244 decimal. I shorten this by 206 bytes. Thus I replace F4 with 26 (with a binary editor).
The result is that now, only the first line is readable, followed by some gibberish:

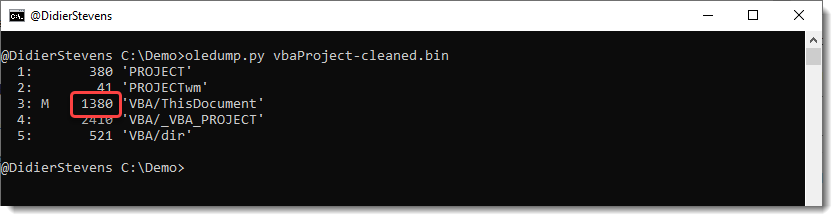
And to get rid of the gibberisch, I also shorten the length of the stream. It is 1380 bytes long:

That’s 64 05 00 00 (representation for a 32-bit little-endian unsigned integer).
I subtract 204, thus 1380 – 204 = 1176. Or 98 04 00 00. I use again the binary editor to make this change.
Result:

How did I find the values to subtract? Educated guessing and trial and error. Why 2 different subtractions? Because that was also the case in the original sample that inspired me.
No comments yet.
如有侵权请联系:admin#unsafe.sh