一例APP绕过root检测解密
最近在分析一款app时遇见了root检测,数据包加密,花了时间简单研究了一下,记录下学习的过程。 打开app发现提示检测到设备为root设备,闪退。能看到提示,推测应该是java层的检测。 拖进 2022-9-9 17:2:11 Author: 雷石安全实验室(查看原文) 阅读量:53 收藏
最近在分析一款app时遇见了root检测,数据包加密,花了时间简单研究了一下,记录下学习的过程。 打开app发现提示检测到设备为root设备,闪退。能看到提示,推测应该是java层的检测。 拖进 2022-9-9 17:2:11 Author: 雷石安全实验室(查看原文) 阅读量:53 收藏
最近在分析一款app时遇见了root检测,数据包加密,花了时间简单研究了一下,记录下学习的过程。
打开app发现提示检测到设备为root设备,闪退。能看到提示,推测应该是java层的检测。
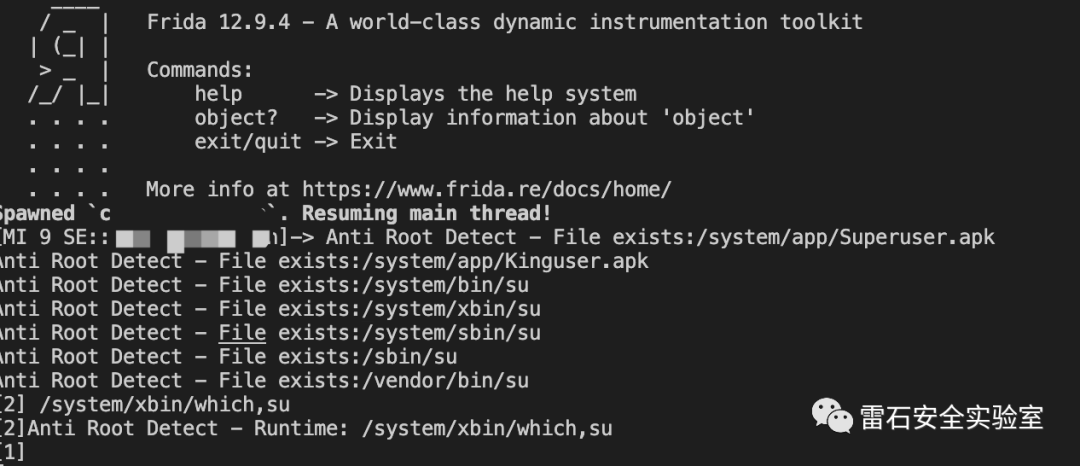
拖进jadx发现是加固的。
java层常见root检测大多是通过检测系统文件:一些路径下的su文件,一些root的app相关文件。
"/data/local/bin/su","/data/local/su","/data/local/xbin/su","/dev/com.koushikdutta.superuser.daemon/","/sbin/su","/system/app/Superuser.apk","/system/bin/failsafe/su","/system/bin/su","/su/bin/su","/system/etc/init.d/99SuperSUDaemon","/system/sd/xbin/su","/system/xbin/busybox","/system/xbin/daemonsu","/system/xbin/su","/system/sbin/su","/vendor/bin/su","/cache/su","/data/su","/dev/su","/system/bin/.ext/su","/system/usr/we-need-root/su","/system/app/Kinguser.apk","/data/adb/magisk","/sbin/.magisk","/cache/.disable_magisk","/dev/.magisk.unblock","/cache/magisk.log","/data/adb/magisk.img","/data/adb/magisk.db","/data/adb/magisk_simple","/init.magisk.rc","/system/xbin/ku.sud"
检测一些root的app如magisk等。
"com.noshufou.android.su","com.noshufou.android.su.elite","eu.chainfire.supersu","com.koushikdutta.superuser","com.thirdparty.superuser","com.yellowes.su","com.koushikdutta.rommanager","com.koushikdutta.rommanager.license","com.dimonvideo.luckypatcher","com.chelpus.lackypatch","com.ramdroid.appquarantine","com.ramdroid.appquarantinepro","com.topjohnwu.magisk","com.kingroot.kinguser","com.kingo.root","com.smedialink.oneclickroot","com.zhiqupk.root.global","com.alephzain.framaroot","com.android.vending.billing.InAppBillingService.COIN","com.android.vending.billing.InAppBillingService.LUCK","com.chelpus.luckypatcher","com.blackmartalpha","org.blackmart.market","com.allinone.free","com.repodroid.app","org.creeplays.hack","com.baseappfull.fwd","com.zmapp","com.dv.marketmod.installer","org.mobilism.android","com.android.wp.net.log","com.android.camera.update","cc.madkite.freedom","com.solohsu.android.edxp.manager","org.meowcat.edxposed.manager","com.xmodgame","com.cih.game_cih","com.charles.lpoqasert","catch_.me_.if_.you_.can_"
frida -U -f com.xxxx.xxxx -l anti_root.js --no-pause此时不再闪退。
挂上代理进行测试抓包,发现存在参数加密。
还是需要脱壳进行分析。 这里已经绕过了root检测,没有frida检测,直接上frida-dexdump就行。
frida-dexdump -FU分析后定位到类:com.xxxx.xxxx.utils.http.DESHelp直接hook就行。
只是hook加解密还是用很多不方便的地方,有时候需要去主动调用对应的加解密函数。
这里可以用brida,或者是httpdecrypt等工具。
这里提供一个通过python frida交互,使用rpc来完成主动调用。
调用也很简单,只是代码写死在了js脚本中,所用使用rpc.exports开启RPC调用接口,后面使用python来调用。
function htddecrypt(param,key){var result;Java.perform(function () {var hclass = Java.use("com.xxxx.xxxx.utils.http.DESHelp");var hexarry = hclass.parseHexStr2Byte(param);param = byteToString(hexarry);console.log("[*] Hooking ...");result = hclass.decrypt(param, key);//console.log(result);});return result;}function htdencrypt(param,key){var result;var encJava.perform(function () {var hclass = Java.use("com.xxxx.xxxx.utils.http.DESHelp");console.log(param);enc = hclass.encrypt(param, key);//console.log(result);var hexarry = stringToByte(enc);result = hclass.parseByte2HexStr(hexarry);});return result;}rpc.exports = {rpcfunc: htdencrypt,rpcfunc1: htddecrypt}
通过python中代码:
session = frida.get_usb_device().attach("com.xxxx.xxxx")script = frida_rpc(session)param = str(sys.argv[2])ret = script.exports.rpcfunc(param,"CCCk+H%b6.MMMMkoKKK")print(ret)
还是一个简单的例子,现在常规的app大体思路都是这样,只能碰到问题花时间研究去解决,不能迷信通杀方案。
往期回顾
Log4j2漏洞复现&原理&补丁绕过
一个文件上传漏洞靶场
商务咨询:
0571-87031601
商务邮箱:
联系地址:
浙江省杭州市市民街98号尊宝大厦金尊3301
文章来源: http://mp.weixin.qq.com/s?__biz=MzI5MDE0MjQ1NQ==&mid=2247516249&idx=1&sn=9960c67513d78c7012f7c4feda3839b9&chksm=ec26a1c1db5128d7daceaab4dd17ffa3f19e800389b3104e423b1004fe08f280c075068bcf43#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh