2022-7-18 02:17:17 Author: infosecwriteups.com(查看原文) 阅读量:50 收藏
A tale of ‘Site-wide Account Takeover’
Before we start with the technical part of the vulnerability i.e. covered below, I want you to brief about the application which was the target.
It is called an ‘Unified Access’ portal for employees that provides access to IT based applications through a single platform. The ESS application is sold by IBM and could also be integrated with SAP running Lotus Domino server.
During an on-going a Red team engagement I came across this web application and wanted to explore the post authentication functionalities of the application, hence I started collecting all relevant information that could lead to post authentication functionalities.
Having no idea about the login details format which is to be passed in the login fields, I randomly created a list of all default usernames and password but the failed to reuse the same.
We later started collecting a list of all email address and clear text password from the available data breaches and performed brute-force over the same. Luckily one combination of email address and password worked. We later started to explore all post authentication modules, as it was a single-sign on application we had a lot of modules to explore. While exploring the application I had came across multiple common web application vulnerabilities, out of which two of them proved helpful to chain the attack:
- Post-authentication: Discovered an endpoint that provided Emails, Employee ID, Employee details, etc. Created a crawler and collected the same.

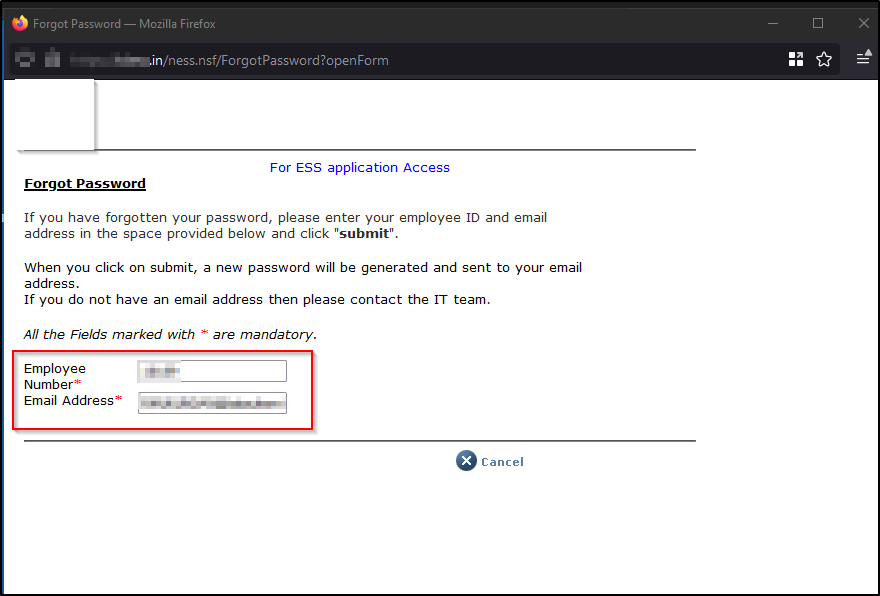
2. Pre-authentication: Discovered an endpoint to reset password of an employee, where a valid email address and employee ID is required.

Having knowledge of the emails and employee ID, we decided to understand the flow of a password reset functionality. I entered a valid employee ID and instead of entering a valid registered corporate email address I decided to enter my email address and hit enter. BOOM !!!


The application provided me with a new password to login. Similarly, I created a brute force list and for test purpose I successfully reset passwords of 500+ accounts.

This application is being used by at least 200+ companies across the world. The vulnerability is reported to the company on which I was performing red team assessment, the company decided to take down the portal and in future they are going to migrate the same to another application. The same has been reported to the parent company i.e. SAP and their partner IBM.
如有侵权请联系:admin#unsafe.sh