Quick Start GuideDownload PacuChange to Pacu's DirectoryInstallationStart PacuS 2018-09-07 22:55:27 Author: github.com(查看原文) 阅读量:266 收藏
1. Download Pacu
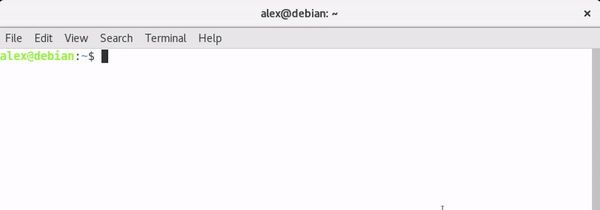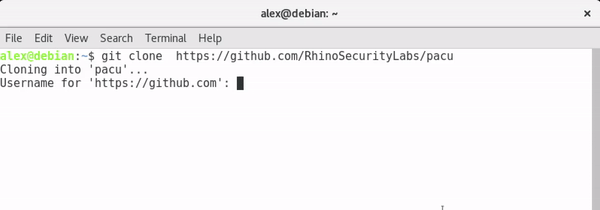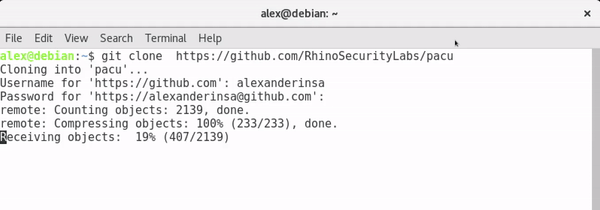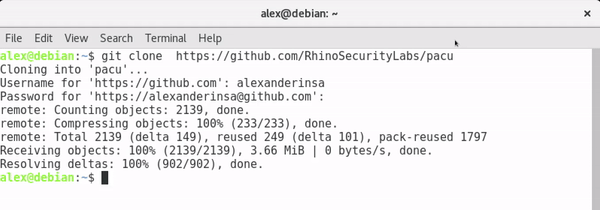
Pacu can be downloaded either through downloading Pacu as a zip file and extracting it to a directory of your choice, or by using Git and cloing the repository. This guide will use Git to download Pacu.
Git Install:
2. Enter Pacu Directory
3. Installation
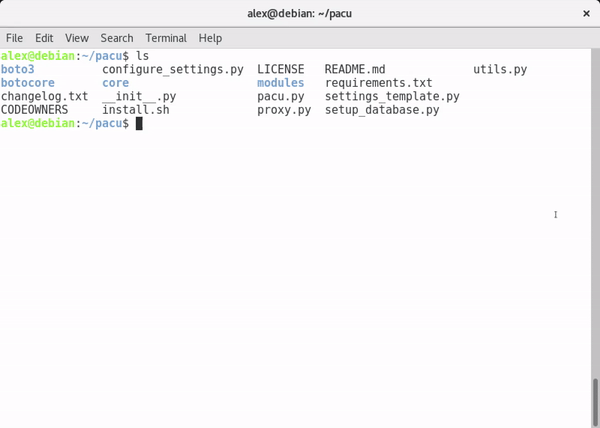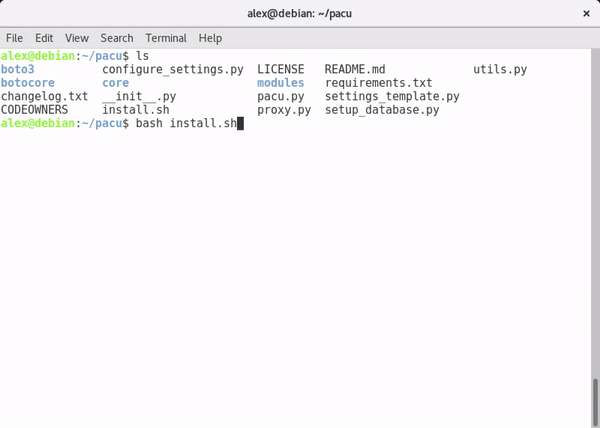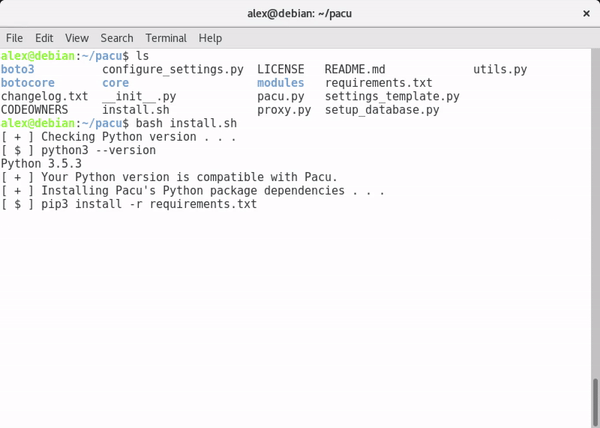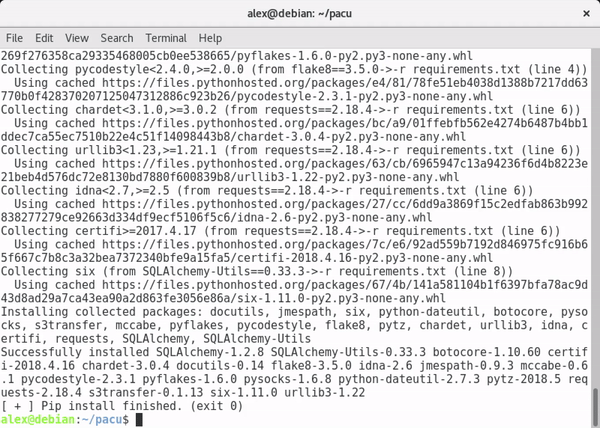
Type bash install.sh to install Pacu. If you do not meet the requirements to run Pacu, you will be notified.
4. Start Pacu
Enter python3 pacu.py to launch Pacu.
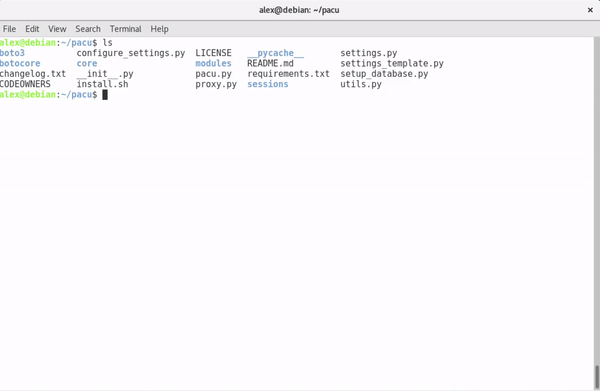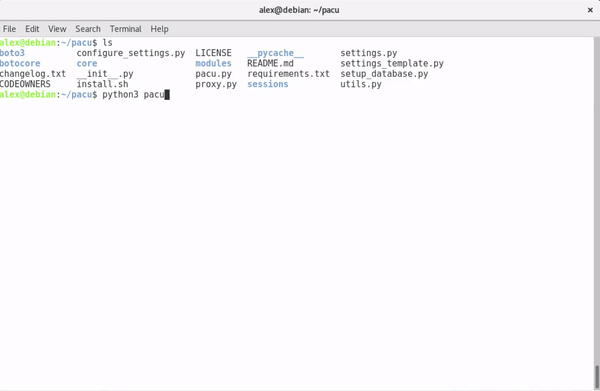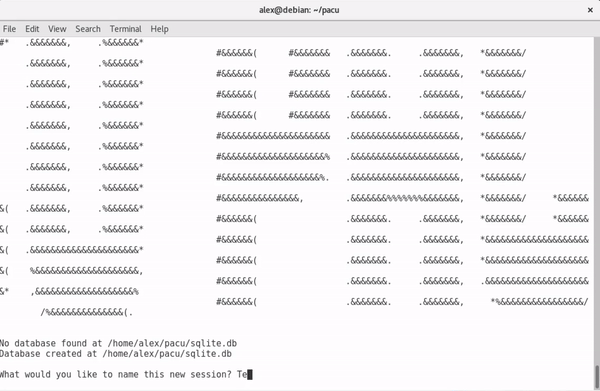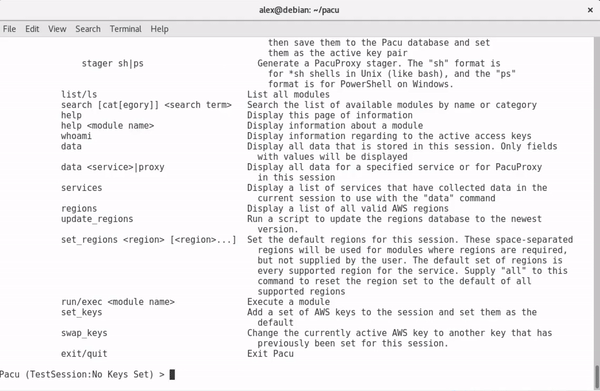
The first time launch Pacu will go through these steps:
-
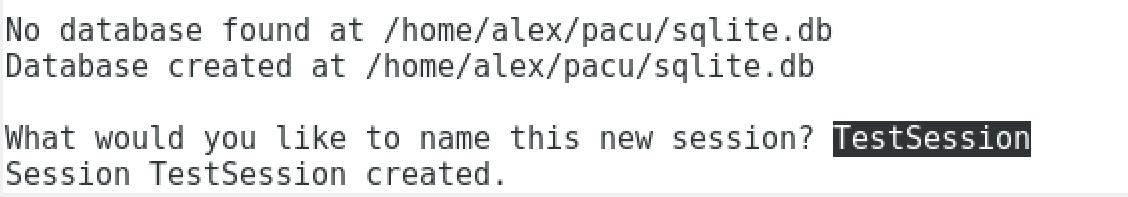
Creation of database. This is done automatically, no user input required.
-
Enter in a session alias to store captured data and command logs.
- We will use TestSession for the purposes of this guide.
5. Set AWS Keys
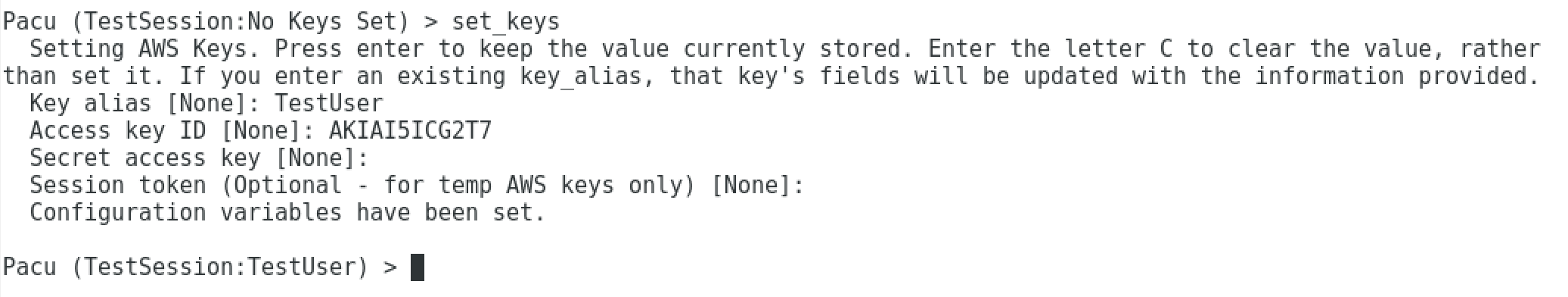
This step will set an AWS keypair to test against. If you do not know how to create AWS keys, click here
-
Key alias - Used internally within Pacu and is associated with a AWS key pair. Has no bearing on AWS permissions.
-
Access Key - Generated from an AWS User
-
Secret Key - Secret key associated with access key. Omitted in image.
-
(Optional) Session Key serves as a temporary access key to access AWS services.
6. Running Modules
-
List of modules can be brought up with 'ls'

-
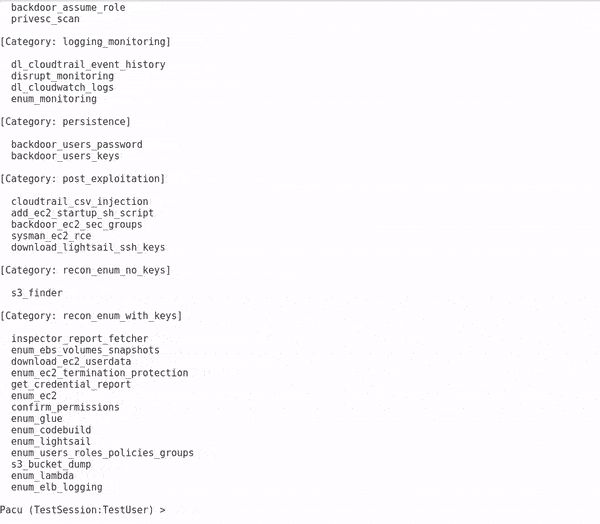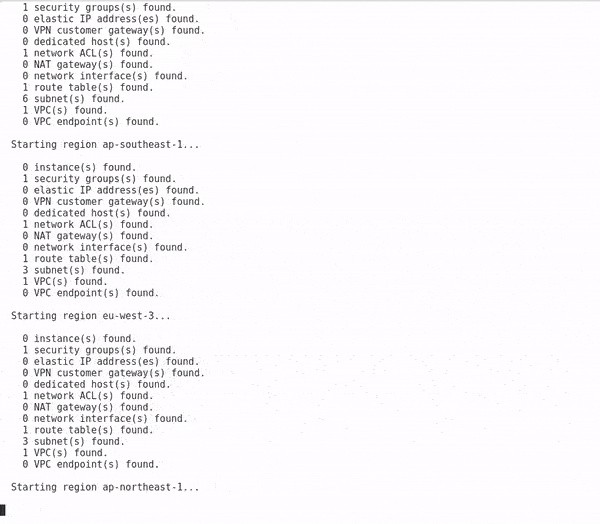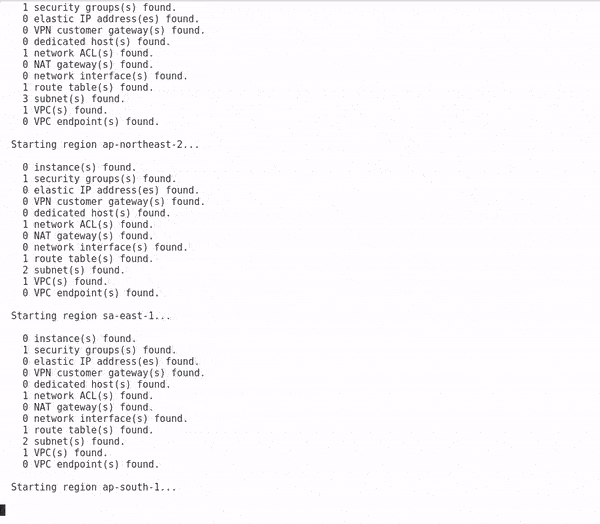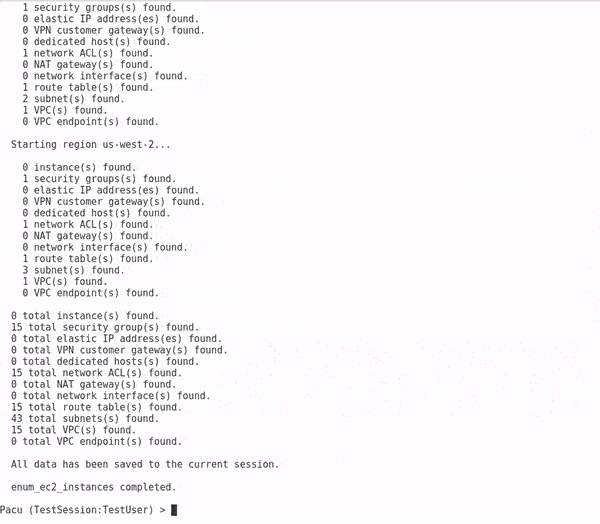
Running enum_ec2
A module can be executed in the format
run <module_name> [--keyword-arguments]This guide uses a set of created AWS keys and permissions created during the following guide to enumerate networking and instance data for the given account for all regions automatically.
1. Go to IAM User Dashboard
Sign into your AWS account and go to the following page :
https://console.aws.amazon.com/iam/home?region=us-east-1#/users
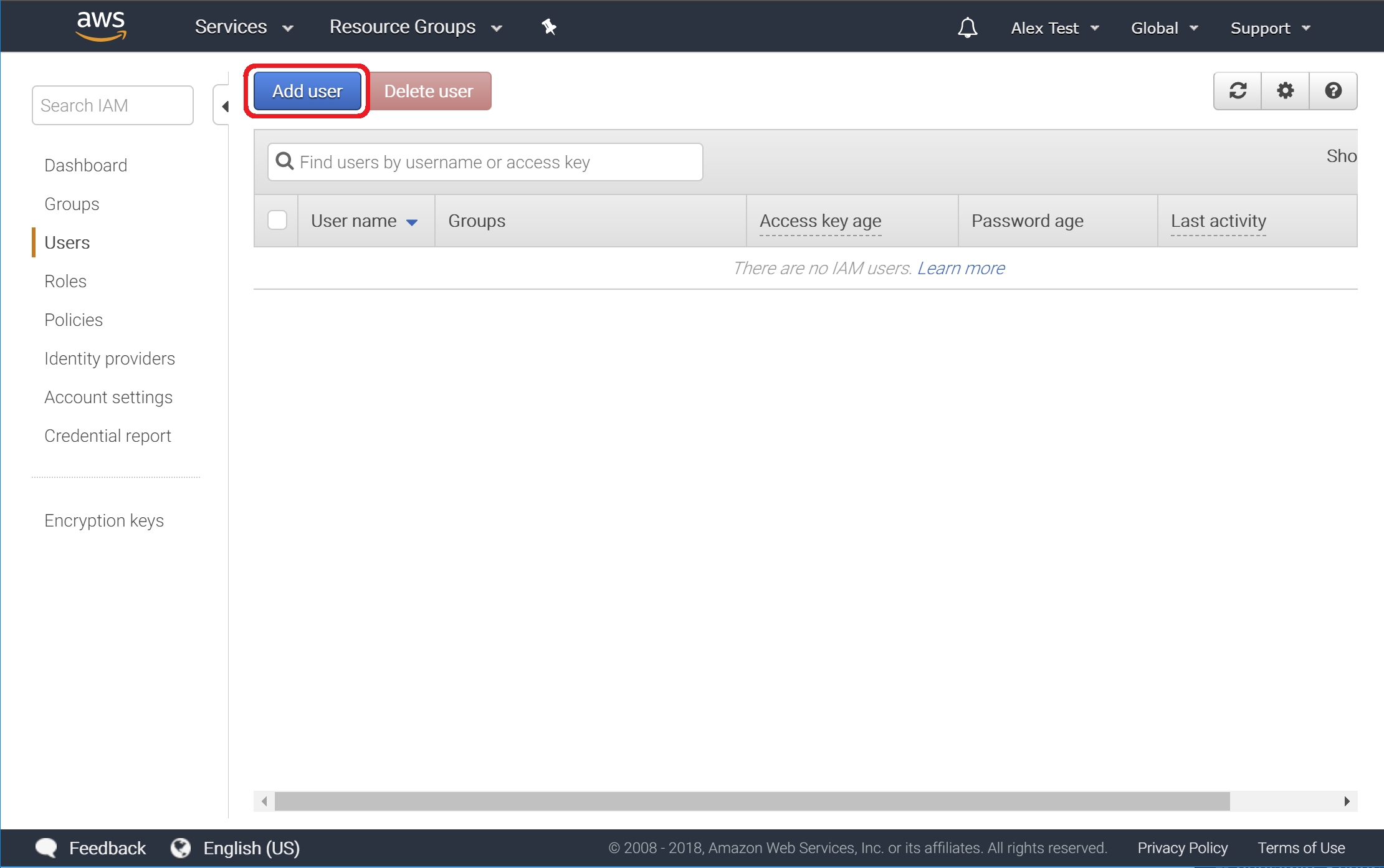
2. Click "Add user" Button
3. Enter "User name" and "Access type"
The 'User name' is what will be used to reference a particular user's access in AWS. An important step here is to allow Programmatic access to generate a key-pair that will be used to programmatically access AWS services.
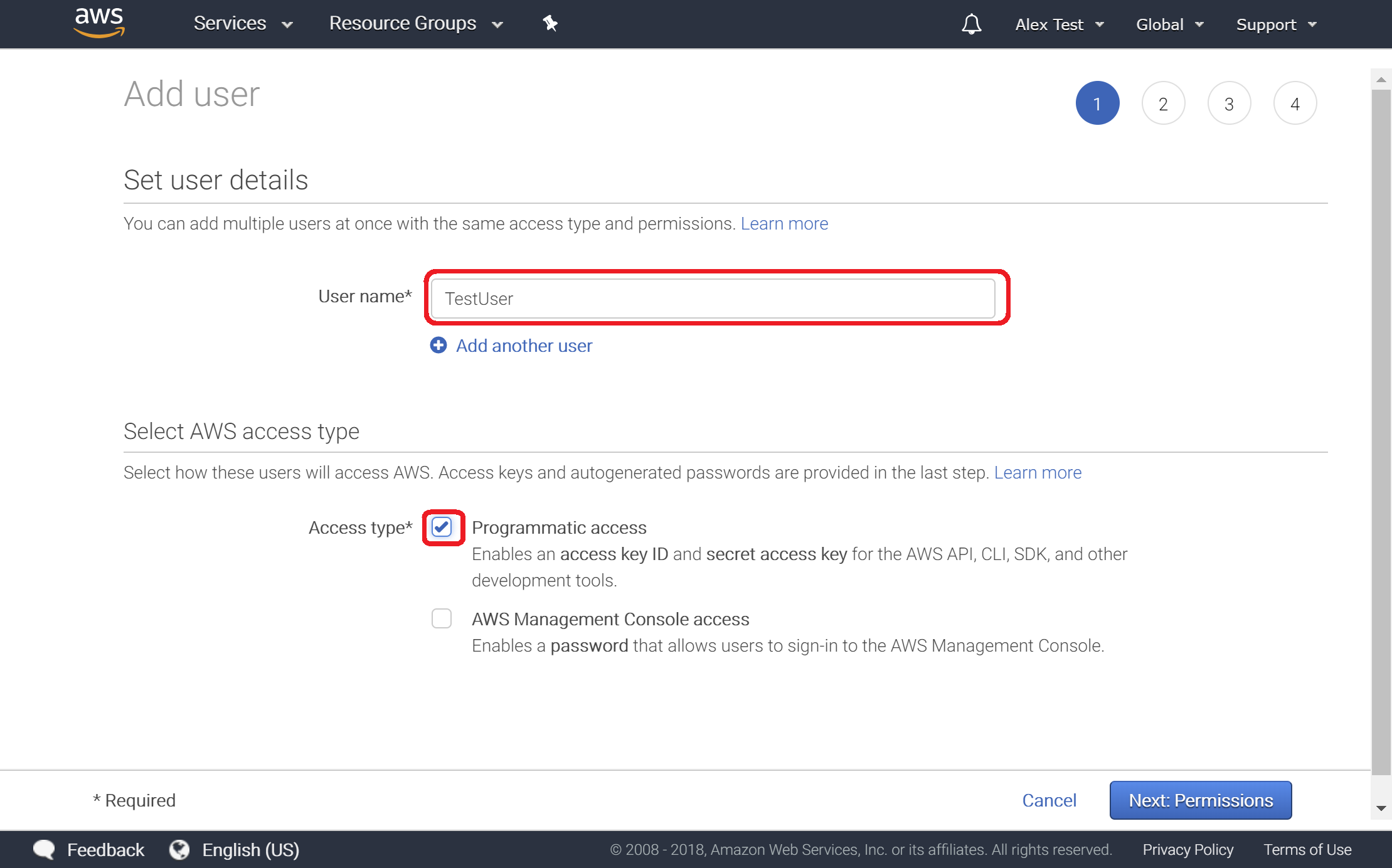
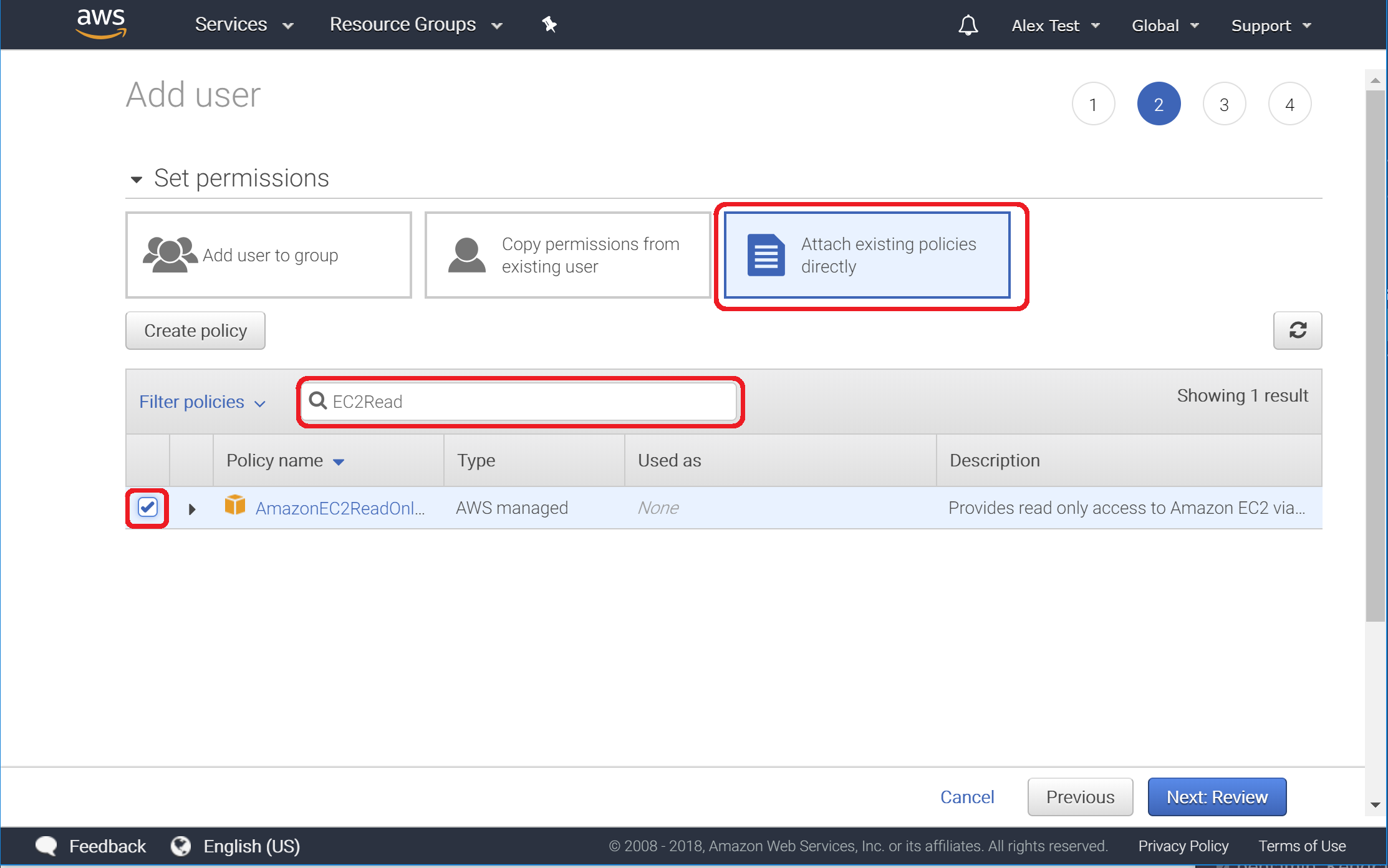
4. Set Permissions
For this guide we will attach a policy directly to our created User.
Enter "EC2Read" to filter out existing, default Policies and check the box next to AmazonEC2ReadOnly
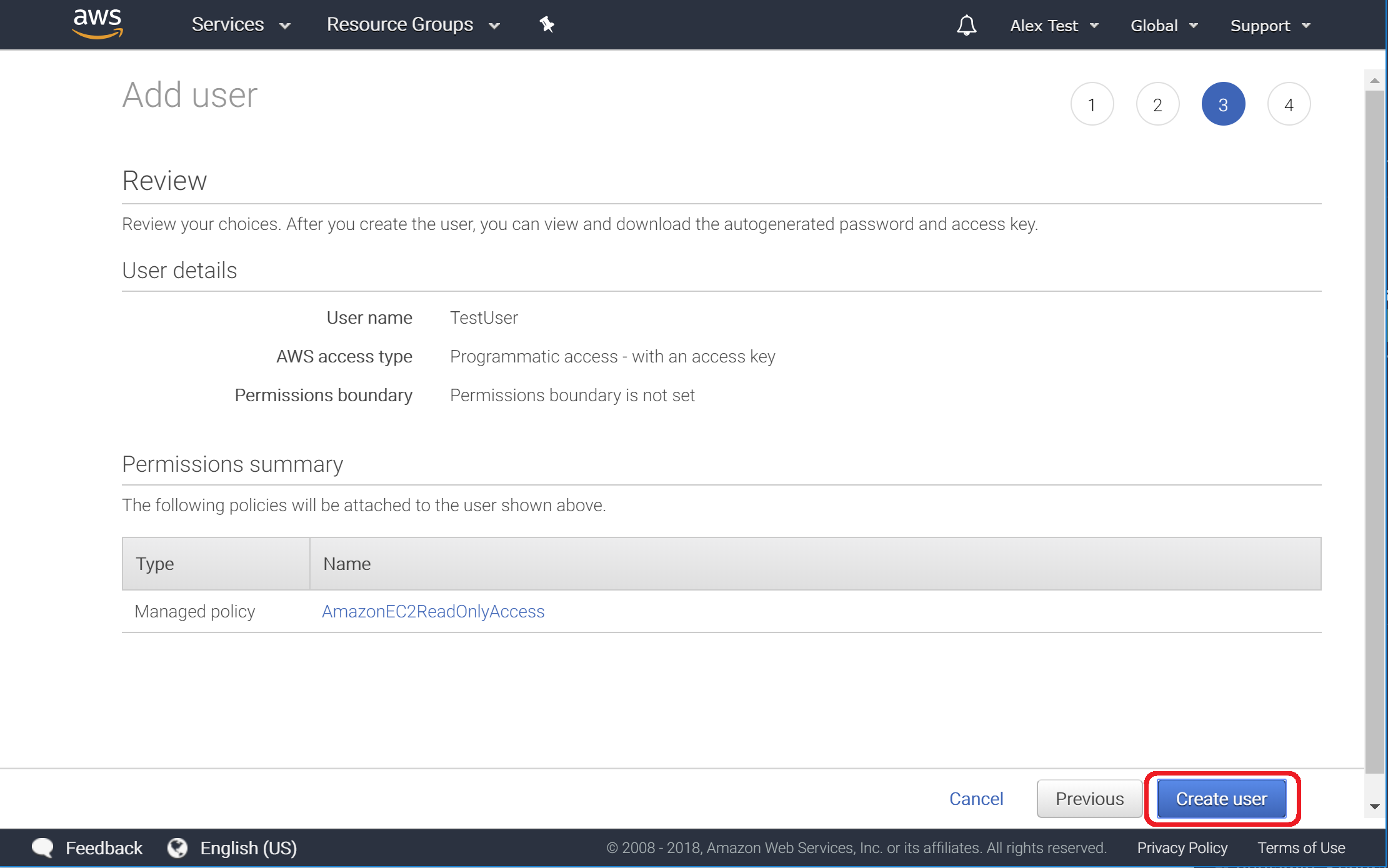
5. Review User Creation
Ensure that your page looks similar to the following image.
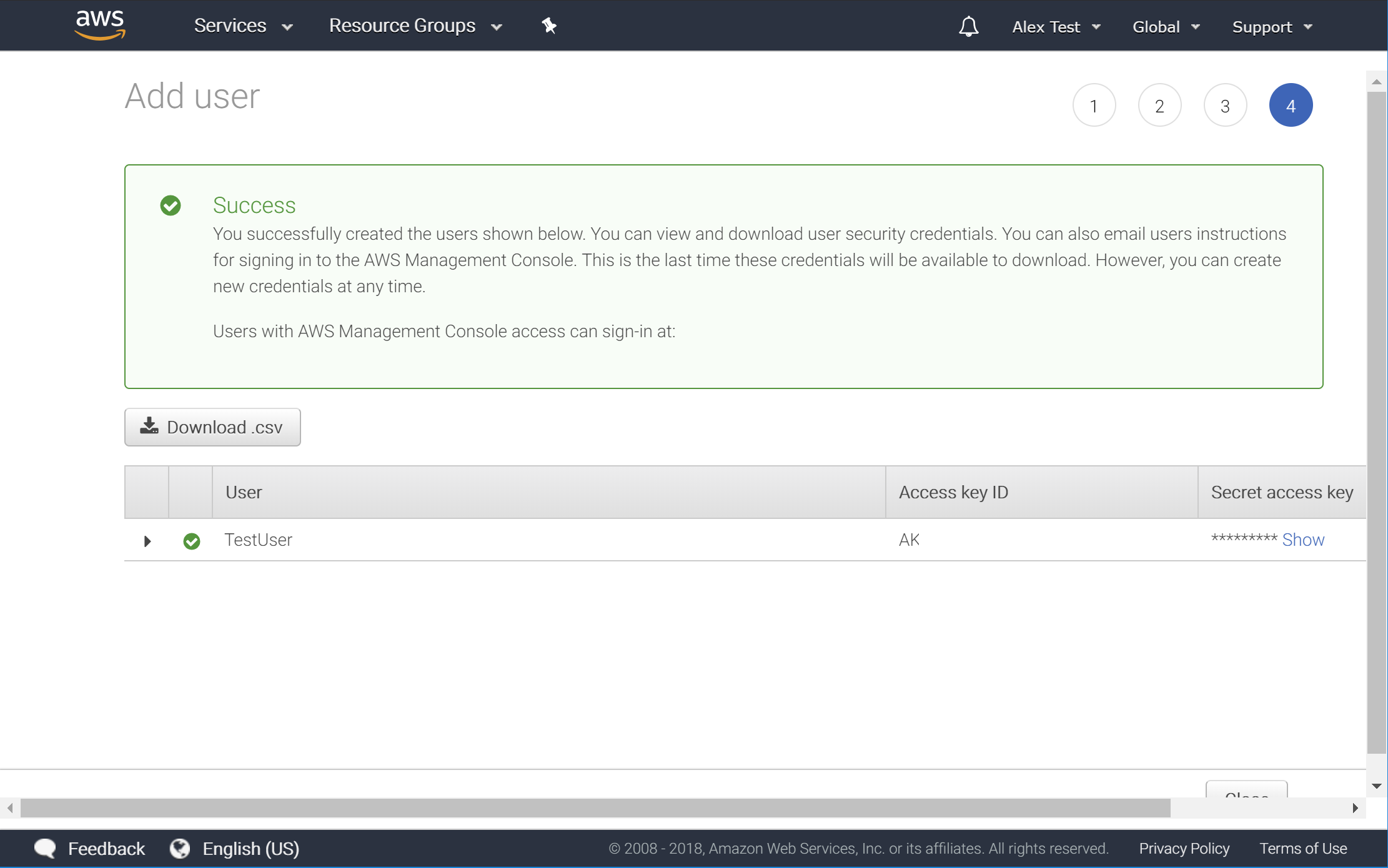
6. Confirm User Creation
Disrupt GuardDuty and CloudTrail monitoring with disrupt_monitoring and then inject a malicious formula into CloudTrail event history with cloudtrail_csv_injection.
Run enum_ec2 to get data on EC2 instances, then run backdoor_ec2_sec_groups to gain access to hosted services that were otherwise blocked.
Run download_lightsail_ssh_keys and use the default SSH key pair to try to connect to any existing instances.
Escalate to administrator with privesc_scan and then establish backdoor persistence with backdoor_users_keys and backdoor_users_password.
如有侵权请联系:admin#unsafe.sh