2022-5-30 17:8:34 Author: blog.avast.com(查看原文) 阅读量:26 收藏
This year's DBIR offers practical advice on improving your security posture and tips for making yourself much less of a target.
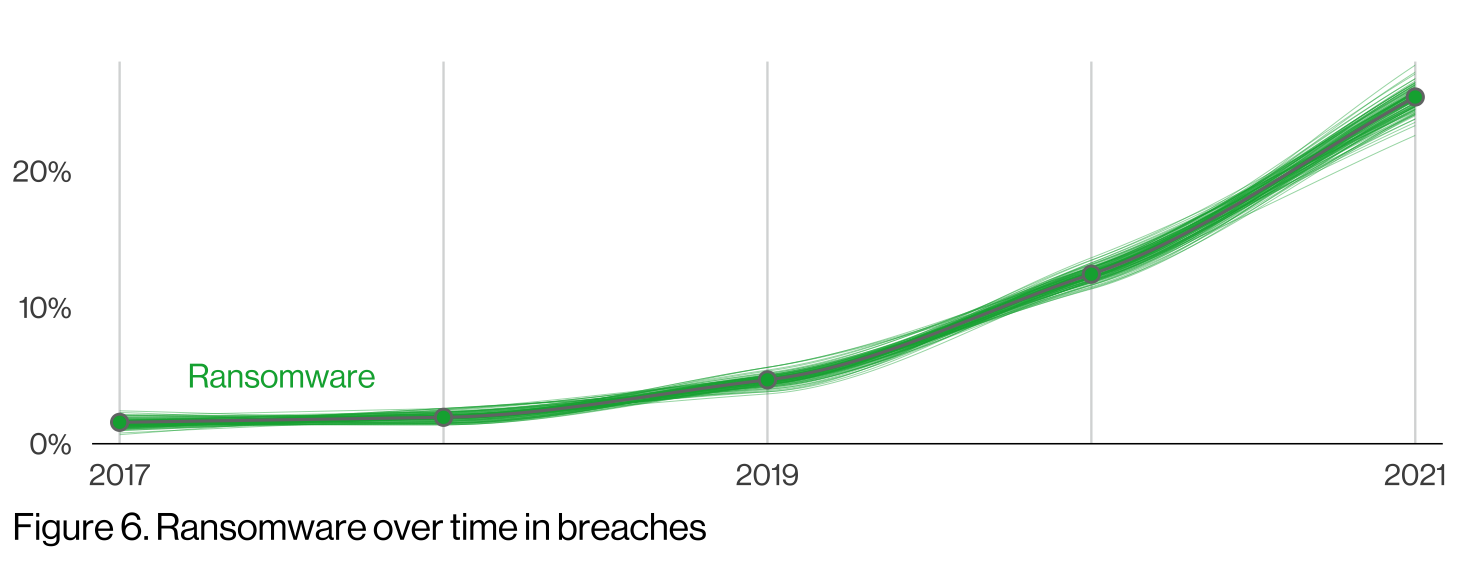
It’s time for the annual Verizon Data Breach Investigation Report (DBIR), a compendium of cybersecurity and malware trends that offers some of the best analyses in our field. It examines more than 5,000 data breaches collected from 80 partners from around the world. If you'd like to explore the report from previous years, we’ve also written up summaries of the 2021 and 2020 reports. If the events of last year could be summed up with one attack, it would be the SolarWinds breach and how it had so many wide-ranging consequences. Overall, supply chain attacks were responsible for 62% of system intrusion incidents this past year, illustrating just how interconnected we have become to run our businesses and operate our computing networks. One notable consequence is the big rise in system intrusions as a proportion of attacks, which is shown in the following graph. Nevertheless, the topic of ransomware remains at the front and center of this year’s report. In the past year, this particular threat has doubled its frequency to account for a total of a quarter of all breaches, as is shown in the chart below. Certainly, the pandemic has been good for ransom actors. Image credit: GitHub However, even with this huge corpus of breaches, the number presented may still be on the low side. The U.S. Senate Committee on Homeland Security & Governmental Affairs revealed that the numbers provided to them by the FBI and other organizations might be drastically underestimating the real number of ransomware victims and the amounts paid out during attacks. Its report is also worth reviewing and contains several recommendations that the federal government should take to improve overall posture and response to these attacks. Another challenging aspect of ransomware is its effect across all sizes of targets. The DBIR specifically examined thousands of incidents involving the smallest businesses that have less than 10 employees. There were 130 incidents with data leaks, using both ransomware and stolen credential attacks. While this is a small proportion, it is still troubling. When describing how to monitor devices for suspicious activity, the report offers the following comparison: “Think of your computer like a car – if it suddenly won’t start, runs slower or makes a weird noise, it’s time to have an expert take a look.” The trick is knowing when these telltale signs appear that aren’t as obvious as what we expect from our cars. The report offers additional suggestions, such as tips to make yourself much less of a target. The authors write, “Use antivirus to remove bots; implement patching, filtering and asset management to prevent exposed vulnerabilities; and standardize two-factor authentication and password managers to minimize credential exposure.” This year's DBIR offers some positive notes on three fronts: We’re patching more and we’re patching faster. Next, we are generally getting better at detecting attacks in a timely manner. Image credit: GitHub Finally, we are also getting better at detecting and reporting phishing, as is visualized in the below graph showing the increase in people who didn’t click on phishing lures: Image credit: GitHub “The question is can your organization both act on the 12.5% that reported phishing lures and find the 2.9% of the targets who clicked on them?”, the report authors ask. Further reading:
Image credit: GitHubPractical advice on improving your security posture
What's the good news?
How to spot email scams
Stay protected against scams and online fraud
如有侵权请联系:admin#unsafe.sh