Here are the steps to follow to protect yourself from scam email attacks
One would think that scammy emails are a thing of the past and that users are digitally educated in this day and age, a fact which enables them to tell which email is a scam and which one isn't. And while this may be partially true, email scams — and scams in general — have become more sophisticated, making the task of recognizing them that much harder: The numbers above come from FBI reports and refer to the losses people and businesses suffered in 2019. As we know, this number increased vastly in 2020, as "It was a year of fake news and scams, deceiving users while taking advantage of the pandemic," according to Avast Security Evangelist Luis Corrons. Email scams, generally speaking, are emails that intend to damage a person or a company in some way. Their objective could be to trick recipients out of large sums of money or obtain important credentials like bank emails and passwords. Of course, a scammer may also want to target other data, like email lists, social security numbers, even personal information like home addresses and phone numbers. Usually, scammers implement tricks that will trigger a person's worry or make them an offer they can't refuse — perhaps an investment opportunity or an outstanding deal for expensive products at a very low price. Recognizing emails that are not a part of some elaborate scam is not easy for most users. Especially since some of the things one would think scammers wouldn't do, are a matter of speculation rather than certainty. However, the email address, wording, and grammar used is not a matter of speculation. More specifically: (Source) This is not a legitimate email address, which means that it's improbable for this email to be valid. In this case, a good rule of thumb would be to understand the type of action that could have led to this email having been sent. Generally speaking, scammers are here to entice for a quick buck and rarely — if ever — are in it for the long game. Which means that elements like personalization are not something they use in most cases. Another thing scammers won't use would be subtlety. On the contrary, they'll use words like "URGENT", "EXCLUSIVE" and so on. Of course, setting a time limit is common practice with many email marketing campaigns. As a matter of fact, most email marketing tools offer elements like countdown timers that can spice up your email marketing campaigns. However, there's a difference between this: (Source) And this: (Source) Wording like "Urgent action required", or "Your account is at risk" won't sit well with your recipients. This is textbook scammer language, especially if it's highly generic and impersonal. Marketers, unlike scammers, use techniques that minimize — almost eliminate — suspicion and allow users to understand that they're talking to an actual brand, with triggered emails and personalized and honest content that makes sense to the user first and foremost. Before we dive into the different types of email scams and how to spot them and protect your account, let's point out what goes into an attempt at scammy behavior. Scammers will: But let's get a little more specific. The most common digital scam is email phishing. Phishing emails are designed to urge people into biting into a scam, by giving away financial data, passwords to protected websites, or other sensitive information. The reason why phishing is so successful is because it's modeled after human behavior. The scammer uses techniques that can manipulate a person's way of thinking, leading them to believe that there's an urgent situation at hand that requires them to act quickly. This sense of imminent danger pushes users into making online payments or giving up important data. Spam emails are not inherently dangerous, but they could be. They are intended for a large number of recipients, mainly for commercial purposes, and more often than not, they lack personalization and segmentation. The reason why they could be dangerous is the fact that the brand or person messaging the recipient hasn't built an email list organically. On the contrary, your data could have very well been mined or sold at a hefty price, much like the content of the email list overall. Email scams, as mentioned before, are designed to trick recipients into disclosing information that could harm them in a multitude of ways. From causing physical and emotional damage up to identity theft or creating false claims at illegal activity, email scams can be positively harmful to a person's well-being. Spoofing scams have the ability to create an email address almost identical to that of a well-known brand users would most likely interact with, as well as email content that includes the logos and colors of said brand. These addresses could look legitimate at first glance, like "@venrno.com" instead of Venmo and so on. Usually, those emails contain a link that could lead to the user downloading malware or disclosing personal information that could lead to users losing a good chunk of their assets. Malware is a type of software designed to obtain data like passwords by gaining access to a computer. This access allows scammers to monitor, alter, and ultimately steal sensitive data. Usually, users receive an email with suspicious links or attachments through a suspicious sender address. This email urges users to download the attachment or click on the link as a part of a standard operating procedure that could solve a possible "threatening" problem. The most surefire way for users to protect themselves from scam email attacks is to educate themselves and truly realize what goes into a scam. Until then, here are the steps to follow. Using backups and two-factor authentication could save user data and educate users on what to expect at the same time. Backup software can keep information secure in the sense that the user won't suddenly see their computer wiped out of all their data, even if the computer suffers great damage. On the other hand, two-factor authentication will send a message to the user when it comes to suspicious log-in activity or password change. By asking the user to verify and authenticate the action, two-factor authentication ensures that the activity is driven by a user action. A computer's operating system (OS) needs to always be up to date. Some scam methods can override the security provided by an older version of your OS. This is especially true considering that an OS can be the object of frequent attacks, largely through older versions of internet browsers as well as scam emails. The same holds true for an up-to-date version of the antivirus software. Updated antivirus software can protect computers from newer versions of malware. As mentioned above, the first level of protection, and the most important one, is understanding what an email scam is and what its tell-tale signs are. Apart from verifying the sender's email address and pointing out inconsistencies between addresses and domain names, users should note that spam emails usually have subtle mistakes. These mistakes are focused on spelling, syntax, and grammar. The level of subtlety varies, much like the scam's sophistication. (Source) This scammy email is subtle enough, and a user would fall for it with a quick look. However, the sender's address is one of the giveaways. The same goes for the salutation. In the era of personalization and sophisticated lead nurturing, the "Hello user" salutation is quite unusual. And while this email doesn't ask the user to give up an important password, it asks the user to follow a suspicious link. Emails that are unsolicited and feature strange-looking links and attachments should always be considered suspicious, provided the recipient doesn't recognize the sender's address — or, in some cases, even if they do. Sometimes, email scams are just the cherry on top of a well-crafted holistic scam. This is why users need to keep up-to-date with various online attacks. More often than not, users think that HTTPS websites and links are safe and legitimate. However, this is no longer the case, as scammers use this protocol in the links of phishing emails to make them seem legitimate and trustworthy. Ensure the link you're about to click isn't shortened but is the original link of the website you are asked to access. Also, notice if there's hypertext, as the "innocent" URL inside the email could very well be plain text linked to a scammy website. SMS phishing (smishing) attempts to lure a person into giving up sensitive data like credit card details installing malware to their machine through text messaging. The texts appear to be sent by a well-known brand or a person, usually containing a link that leads to a page asking the user to give up personal information. Social media phishing is another way scammers obtain sensitive information that could potentially be used in other scams aimed at users. Sometimes scammers use social engineering techniques, such as false claims at collaborations with Instagram influencers that increase social proof and make it easier for users to trust them. Vishing is used to obtain data over the phone. Usually, scammers aim for the victim's credit card details, but identity theft could also be the goal in some cases. More often than not, a dialer will generate a random number, and scammers will "bait" the caller by claiming there's an issue with the potential victim's credit card or even a problem with another family member. That way, the victim feels like they need to take immediate action. Users often find themselves in a difficult position, not knowing whether to trust an email address asking them to take urgent action or not. In the day and age of sophisticated digital campaigns, it’s important to remember that not everything is what it seems and that emails that don’t stem from a specific user behavior but ask for a particular type of action that requires data could very well be a scam. This can threaten the well-being of your machine and its operating system, be it Windows or macOS, as their operating system can get viruses as well. The facts above emphasize the necessity of using email marketing, marketing automation, and updated antivirus tools that make a difference.How to recognize emails that aren’t a scam
The different types of email scams
What is email phishing?
What is spam?
What are email scams?
What is spoofing?
What is malware?
How to ensure you're protected every step of the way
Use backups and two-factor authentication
Keep your OS and antivirus updated
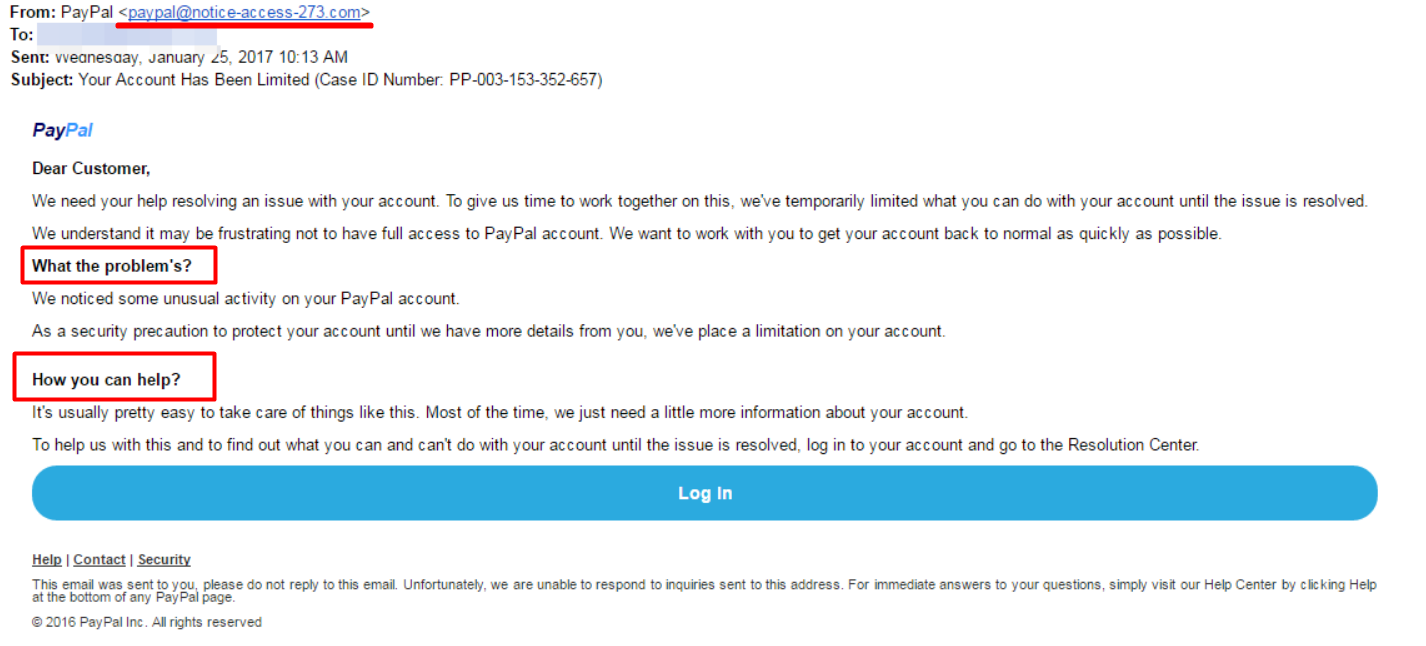
How to spot an email scam
Other types of attacks to keep an eye for
HTTPS phishing attacks
SMS and social media phishing
Vishing (voice phishing)
The takeaway
如有侵权请联系:admin#unsafe.sh