阅读: 45
一、漏洞概述
近日,绿盟科技CERT监测到VMware 发布安全通告,VMware的众多产品受Apache Log4j2远程代码执行漏洞(CVE-2021-44228)的影响。由于Apache Log4j2某些功能存在递归解析功能,未经身份验证的攻击者通过发送特别构造的数据请求包,可在受影响的 VMware 产品中执行任意代码。漏洞PoC已公开,且发现在野利用,建议相关用户尽快采取措施进行排查与防护。
参考链接:https://www.vmware.com/security/advisories/VMSA-2021-0028.html
二、影响范围
受影响产品(更新中):
VMware Horizon
VMware vCenter Server
VMware HCX
VMware NSX-T Data Center
VMware Unified Access Gateway
VMware WorkspaceOne Access
VMware Identity Manager
VMware vRealize Operations
VMware vRealize Operations Cloud Proxy
VMware vRealize Log Insight
VMware vRealize Automation
VMware vRealize Lifecycle Manager
VMware Telco Cloud Automation
VMware Site Recovery Manager, vSphere Replication
VMware Carbon Black Cloud Workload Appliance
VMware Carbon Black EDR Server
VMware Tanzu GemFire
VMware Tanzu Greenplum
VMware Tanzu Operations Manager
VMware Tanzu Application Service for VMs
VMware Tanzu Kubernetes Grid Integrated Edition
VMware Tanzu Observability by Wavefront Nozzle
Healthwatch for Tanzu Application Service
Spring Cloud Services for VMware Tanzu
Spring Cloud Gateway for VMware Tanzu
Spring Cloud Gateway for Kubernetes
API Portal for VMware Tanzu
Single Sign-On for VMware Tanzu Application Service
App Metrics
VMware vCenter Cloud Gateway
VMware Tanzu SQL with MySQL for VMs
VMware vRealize Orchestrator
VMware Cloud Foundation
VMware Workspace ONE Access Connector
VMware Horizon DaaS
VMware Horizon Cloud Connector
VMware NSX Data Center for vSphere
VMware AppDefense Appliance
不受影响产品(更新中):
VMware vSphere ESXi
VMware vCloud Director
VMware vCloud Availability
VMware NSX Advanced Load Balancer (Avi)
VMware Software-Defined WAN (SD-WAN)
VMware Workspace ONE Assist
VMware RemoteHelp
VMware vCloud Usage Meter
VMware Tanzu Scheduler
VMware Tanzu Kubernetes Grid
SaltStack
参考链接:https://kb.vmware.com/s/article/87068
三、漏洞防护
3.1 官方升级
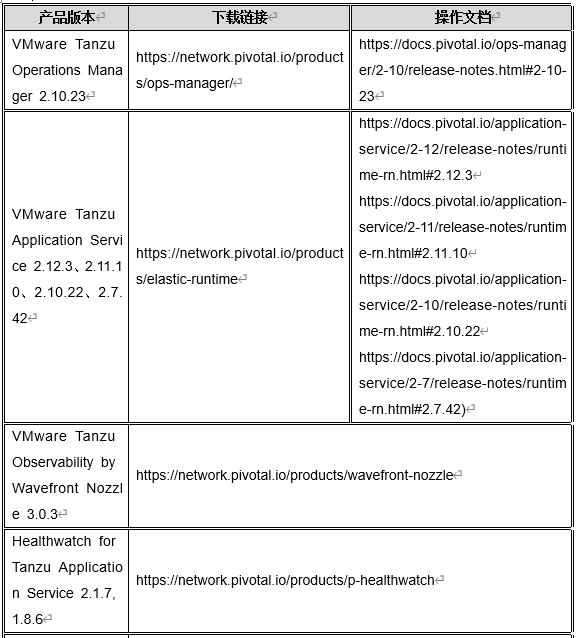
目前官方已针对以下产品发布了新版本修复该漏洞,请受影响的用户尽快升级版本进行防护,对应产品版本的下载链接及文档如下:


3.2 临时防护措施
1.若业务环境允许,可使用白名单限制web端口访问方式来降低风险
2.客户可根据自身产品结合下列参考链接采取临时防护。
| 产品版本 | 参考链接 |
| VMware Horizon 8.x, 7.x | https://kb.vmware.com/s/article/87073 |
| VMware vCenter Server 7.x, 6.x | https://kb.vmware.com/s/article/87081?lang=en_US |
| VMware HCX 4.x, 3.x | https://kb.vmware.com/s/article/86169 |
| VMware NSX-T Data Center 3.x, 2.x | https://kb.vmware.com/s/article/87086 |
| VMware Unified Access Gateway 21.x, 20.x, 3.x | https://kb.vmware.com/s/article/87092 |
| VMware Workspace ONE Access 21.x, 20.10.x | https://kb.vmware.com/s/article/87090 |
| VMware Identity Manager 3.3.x | https://kb.vmware.com/s/article/87093 |
| VMware vRealize Operations 8.x | https://kb.vmware.com/s/article/87076 |
| VMware vRealize Operations Cloud Proxy Any | https://kb.vmware.com/s/article/87080 |
| VMware vRealize Log Insight 8.x | https://kb.vmware.com/s/article/87089?lang=en_US |
| VMware Carbon Black Cloud Workload Appliance 1.x | https://community.carbonblack.com/t5/Threat-Research-Docs/Log4Shell-Mitigation-Steps-for-VMware-Carbon-Black-Cloud/ta-p/109167 |
| VMware Carbon Black EDR Server 7.x, 6.x | https://community.carbonblack.com/t5/Threat-Research-Docs/Log4Shell-Mitigation-Steps-for-VMware-Carbon-Black-EDR/ta-p/109168 |
| VMware Tanzu GemFire 9.x, 8.x | https://community.pivotal.io/s/article/Workaround-to-address-CVE-2021-44228-Apache-Log4j-Remote-Code-Execution-for-all-GemFire-versions?language=en_US |
| VMware Tanzu Greenplum 6.x | https://community.pivotal.io/s/article/Workaround-to-address-CVE-2021-44228-Apache-Log4j-Remote-Code-Execution-for-All-Greenplum-Versions?language=en_US |
| VMware Tanzu Operations Manager 2.x | https://community.pivotal.io/s/article/5004y00001mPn2N1639255611105?language=en_US |
| VMware Tanzu Application Service for VMs 2.x | https://community.pivotal.io/s/article/Workaround-instructions-to-address-CVE-2021-44228-in-Tanzu-Application-Service-2-7-through-2-12?language=en_US |
| VMware Tanzu Kubernetes Grid Integrated Edition 1.x | https://community.pivotal.io/s/article/Workaround-instructions-to-address-CVE-2021-44228-in-Tanzu-Kubernetes-Grid-Integrated?language=en_US |
| VMware Cloud Foundation4.x, 3.x | https://kb.vmware.com/s/article/87095 |
| VMware Workspace ONE Access Connector (VMware Identity Manager Connector) 21.x, 20.10.x, 19.03.0.1 | https://kb.vmware.com/s/article/87091 |
| VMware Horizon DaaS 9.1.x, 9.0.x | https://kb.vmware.com/s/article/87101 |
| VMware NSX Data Center for vSphere | https://kb.vmware.com/s/article/87099 |
| VMware AppDefense Appliance | https://community.carbonblack.com/t5/Threat-Research-Docs/Log4Shell-Mitigation-Steps-for-AppDefense/ta-p/109180 |
声明
本安全公告仅用来描述可能存在的安全问题,绿盟科技不为此安全公告提供任何保证或承诺。由于传播、利用此安全公告所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,绿盟科技以及安全公告作者不为此承担任何责任。
绿盟科技拥有对此安全公告的修改和解释权。如欲转载或传播此安全公告,必须保证此安全公告的完整性,包括版权声明等全部内容。未经绿盟科技允许,不得任意修改或者增减此安全公告内容,不得以任何方式将其用于商业目的。