The consequences of a hacked site have wide-ranging financial repercussions that extend beyond the cost of cleaning the site. Drop-offs can be anticipated for new sales from prospects spooked by “not secure” url warning labels. The same downward turn can be expected for customer retention once the news of a hack shakes consumer confidence in a company’s security. There are also the legal implications of stolen data and the costs to regain compliance certifications – all which can put a hacked business deep into the red.
According to cybercrime magazine, 60% of small businesses close within 6 months of being hacked. Not only are the consequences difficult to recover from, but the hacks often go unnoticed for months. A 2020 report by IBM found that it takes an average of 280 days before a breach is discovered.
Today, we’re looking at 4 quick gut check tests you can do to get the answer to the question, “is my site hacked?”
1 – Give your site a visual once over
You know your site like the back of your hand, so put your detective hat on and begin scrolling. Visual indicators of a hack will be new content containing spam links to pharmaceuticals or knock-off designer products, broken links and new pages. You may also notice broken code on the page in the form of PHP errors along the top of your webpage. This is a strong indicator of clumsy hacking.
Sometimes the tip-off of a hack is obvious if the hacker decides to deface your site. Although less common, they could leave a“signature” or explanation for the hack.
Here is an example of a defacement left by the hacker group called “The Impact Team”. They hacked a website based on a “hacktivist” moral agenda that opposed extramarital affairs.

Source: Krebs Security
The reasons for defacement can range from bragging rights to convenience. A defacement is a very direct way to deliver a ransom message. It could also be the point of the attack itself. While a defacement can be an ego boost to the hacker, it is a dead giveaway of the hack and means their window of time for play and profit will be coming to a close.
2 – Google search your site
Website owners and admins normally get to the site through URL and not through search, but the search results can reveal key indicators of a hacked site.
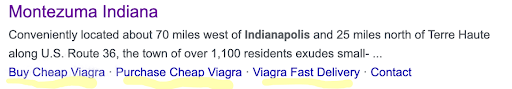
Look for unusual keywords and subdomains. Here is a search I did for Montezuma, Indiana. The keywords point to pharmaceuticals instead of town programs. This is evidence that their town website has been injected with spam.
Look for a hack notice. If google believes your site has been hacked they will add a notice below the search result url that states “This site may be hacked.”

Source: https://support.google.com/websearch/answer/190597?hl=en
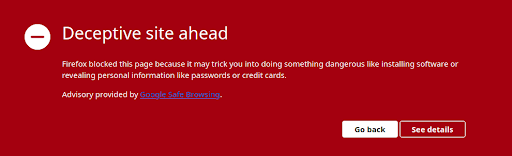
Click on your site from the search results page. Look for a red warning message. This means your website has been compromised and blocklisted.
3 – Keep your ears open
Not only will web hosting providers send you an email if they suspect you’ve been hacked, your site visitors may report strange behavior directly to you or file complaints if they believe their personal data has been compromised.
Keep a look out for subject lines indicating strange site behavior, reports in community forum chats, or even poor reviews. Take your site offline while you work to isolate and fix the issue. Meanwhile, make it a habit to visit your site daily while the situation stabilizes.
4 – Enter your site url into the reputable free tools
See if Google blocklisted youCheck if Google has officially flagged your site as dangerous by entering your url into Google Safe Browsing
Source: https://transparencyreport.google.com/safe-browsing/search
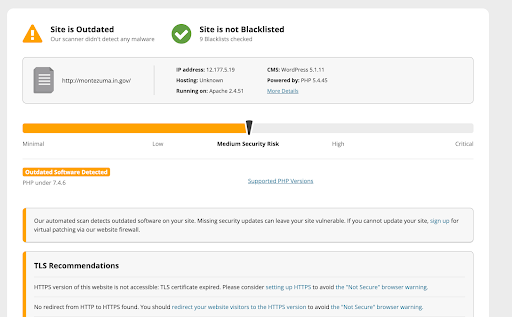
Enter your url into Sucuri’s free site check and see what steps they recommend to improve your website’s security.
Enter your site domain, or the email you associate with your website login to https://haveibeenpwned.com/ to see if your site or authentication credentials could be compromised. It will find if the information you provided shows up in their database of all breaches.

Bonus Gut check! Check the logs
If your site is running slowly and you notice spikes in traffic, this could be an indicator of a hack. Hackers may be tapping into your server’s resources or site visitor’s PC’s to run unauthorized processes, like cryptojacking. Look for unusual IPs, unusual usage, and IPs hitting the same page over and over again.
Web server error logs can help you determine the time frame of when the error occurred and the IP address it came from.
You can also check all of your logs by logging into your web server via SSH and running the following command:
[server]$ gunzip -c ~/logs/example.com/http/access.log.* | gawk '{a[$7]++}END{for (i in a) {print a[i]"\t"i}}' | sort -n | more
This will give you a complete list of requests to your site in order of least to most frequent. Exploits are more likely to be found towards the top of the report.
In Conclusion
The Verdict is in…
Not Hacked! If you are not hacked, good on you! Let’s stay that way – skip down to our hacker prevention checklist.
Hacked! If you are hacked, you need to focus on finding and removing the malware.
If you are up for the challenge of manually removing a malware infection, you can follow Sucuri’s step by step guide on how to clean a hacked site. Next, follow the process to get your site off of Google’s blocklist. Also take the time to familiarize yourself with website reinfection vectors to avoid repeating your efforts.
If you are not comfortable with the careful and time consuming process of scanning each file, finding and restoring the infected files to their original state, consider using professional hack remediation services. Look for a provider with SLAs, strong reviews and 24/7 availability.
Hacker prevention checklist
Check off these 7 boxes to give your website a brighter, malware-free future!
- Use strong passwords and change them quarterly
- Use a free change detection service like visual ping to monitor your website pages for changes
- Implement the principle of least privilege
- Keep all plugins, themes and applications running on the versions
- Activate a website application firewall and security monitoring services
- Routinely scan your site for weaknesses
- Stay informed on the latest cybersecurity threats by following Sucuri’s security updates.