2021-03-06 19:38:56 Author: medium.com(查看原文) 阅读量:292 收藏
Cyber Security, Ethical Hacking, Application Security, Penetration Testing, Bug Bounties, etc., these career options are blooming and becoming popular among teenagers, scholars, experienced professionals, etc. globally. The reason for this popularity is surely the growing community, increased attacks, and need for skilled professionals.
However, this domain is at a time confusing for a beginner and it may look like an ocean when it comes to Where should I start from? What should I learn first? Damn, there’s a lot to learn and it will take years for me to get into the game, is there any shortcut or shall I leave this domain!! These are not just some questions I frame for this blog but these are the most commonly asked questions to me over Twitter, Instagram, LinkedIn, Emails, etc.
Sometimes, it really hard to provide an exact answer to a curious mind when they come and ask me, Hey Harsh, I am new to Cyber Security and I really want to get started, can you please help me out? Keeping this thing in mind, I am writing this blog to answer all these questions and in a nutshell provide you all with a learning path from my perspective on How to Get Started in Cyber Security?
Cyber Security is a huge domain and when you refer to Cyber Security, you are actually not clear what domain you are actually trying to ask! When you say Cyber Security it can be — you want to be a bug bounty hunter or maybe a blue teamer or a cyber forensics guy or maybe you are not sure either. So let’s just first break down some general career options in Cyber Security which will help you to know where you want to go exactly.
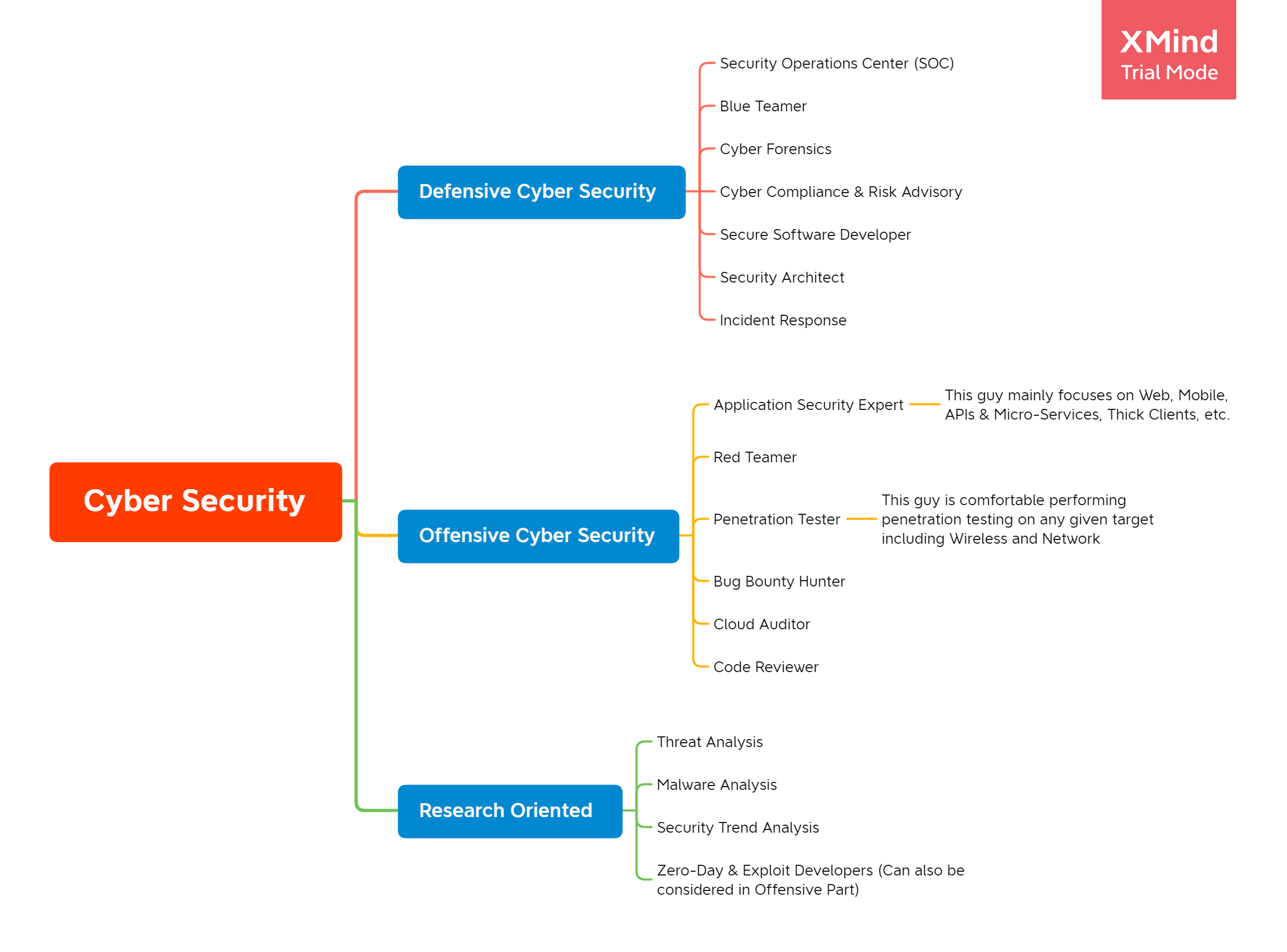
The above mindmap breaks down Cyber Security career options in three major domains Offensive, Defensive & Research. (Please note that Offensive Cyber Security is not an illegal term). Since, there’s a lot to explain, however, as I work into Offensive Cyber Security and if your end goals are to move into the Offensive Cyber Security side, keep on reading as in the next few paragraphs, I am going to give you a more close view of this domain, some requirements & how one should start learning & build a good career in it.
When we talk about getting started into Offensive Cyber Security, there are many domains such as Application Security, Red Teaming, Penetration Testing, Code Reviews, Cloud Audits, etc. However, there are always some initial requirements and at the end of the day, everything is linked somehow.
Pre-requisite:
- Good understanding of how Computer System Works
- Good understanding of how the Internet works and how to use it
- Mindset & Rythm — You must enjoy what you are doing!!!
Since I am into Offensive Security & Application Security I can guide better in how to get a start into this domain and below is the breakdown of various essential setups one should take to get a good grasp from basic to advance concepts. So let’s have a look into it:
Learning about Operating Systems
There are multiple Operating Systems available in the market, however, the most common are Windows, Mac & Linux-based Operating Systems. On the other hand, Android & iOS are the majority players in the Mobile Operating Systems.
There are many scenarios when you will require to know how a particular operating system works and what are various security features provided by them, what are the limitations each of them has and how an attacker can abuse them.
For Example: As a pentester, you have gained access to a Linux Machine as a restricted user. Now, in order to escape the restriction, you will need to know how you can abuse the available features and gain privileged access. This becomes really simple when you know what are various features present and you will have a good hold of what to exploit and gain privileged access.
Resources to learn about Operating Systems:
- Linux Basics: https://linuxjourney.com/
- Android Basics: https://www.educba.com/android-operating-system/
- Windows Basics: https://www.educba.com/introduction-to-windows/
- Operating System Basics: https://www.tutorialspoint.com/operating_system/index.htm
If you wish to dive deeper into these operating systems, you can look out for Windows Internals or Linux Internals which is a more comprehensive study about these operating systems. However, I would recommend getting a basic knowledge at least.
Learning about Computer Networks
Computer Networks are a really important aspect for any IT professional not just for the IT security people. Most of the time when you will encounter any engagement as an offensive security guy, you will be dealing with either a Web Application, Mobile Application, Cloud Infrastructure, Internal Network, Routers, Firewalls, IoT Devices, etc. and if you notice, most of these architectures communicate using internet directly or indirectly.
As a security professional, you must know basic concepts of networking which include knowing how Routing, Firewalling, SSL, TLS, Ports, Protocols, IP, TCP, UDP, MAC, and other important network security features work. Why this knowledge is required doesn’t need any explanation itself, it’s essential, that’s all.
Resources to learn Computer Networks
- https://www.tutorialspoint.com/data_communication_computer_network/index.htm
- https://www.tutorialspoint.com/network_security/index.htm
- Cryptography & Network Security (McGraw-Hill Forouzan Networking)
Learning about Web Applications
The web application is one of the widely encountered things during my journey as an application security engineer and offensive security guy. Most of the externally faced resources of any organization are web applications.
Before diving deeper into how to test for Web Application Security, it is essential to know various concepts about Web Application, their communication, and components. This includes understanding how an HTTP Request is formed, how HTTP Response works, what are the various security headers, browser security features, what is CSP and CORS, etc. This is a basic concept and will eventually help you throughout your journey as Application Security Guy!
Resources to learn Basic Concepts
- About HTTP: https://developer.mozilla.org/en-US/docs/Web/HTTP
- HTTP Headers: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers
- HTTP Security: https://developer.mozilla.org/en-US/docs/Web/Security
- Content-Security Policy: https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP
- HTTP Cookies: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies#Secure_and_HttpOnly_cookies
- Web Security Cheatsheet: https://infosec.mozilla.org/guidelines/web_security
- Cross-Origin Resource Sharing: https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS
Understanding Common Security Frameworks
Once you have gained enough understanding about the basic concepts of Web Application, Operating Systems & Computer Networks, the next part before exploring the Security perspective is to understand some of the common security frameworks which are followed at the industry standard. This is going to help you in proper referencing and understanding which category your security vulnerability lies in. How you can rate the severity of an identified security issue and how to approach for remediation.
OWASP: The Open Web Application Security Project is an online community that produces freely-available articles, methodologies, documentation, tools, and technologies in the field of web application security.
- OWASP Web Top 10: https://owasp.org/www-project-top-ten/
- OWASP API Top 10: https://owasp.org/www-project-api-security/
- OWASP Mobile Top 10: https://owasp.org/www-project-mobile-top-10/
- OWASP ASVS: https://owasp.org/www-project-application-security-verification-standard/
- OWASP Vulnerability Management Guide: https://owasp.org/www-project-vulnerability-management-guide/OWASP-Vuln-Mgm-Guide-Jul23-2020.pdf
- OWASP Risk Rating Methodology: https://owasp.org/www-community/OWASP_Risk_Rating_Methodology
STRIDE: The STRIDE model was developed by Microsoft in order to help security engineers understand and classify all possible threats on a server. The name of this model is an acronym for the six main types of threats.
CVSS: The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
- Read More: https://www.first.org/cvss/
Getting Started with Web Application Security
At this point, we will talk about how to get started in Web Application Security. There are tons of resources out there in the wild and it is not possible to learn/read all of them, however, choosing the best ones is also a difficult task. I am sharing some of the good resources to follow in order to get a good hold:
- OWASP Testing Guide explaining a wide range of security issues and how to test for them. This should be the initial reference guide to know and explore various security vulnerabilities.
- PortSwigger Web Security Academy is the practical version of Web Application Hacker’s Handbook. You will get good learning resources (short and crisp) followed by Labs to master the things you are learning.
- Bugcrowd Vulnerability Rating Taxonomy talks about multiple security issues and an associated severity with them. This is also a helpful resource to know multiple security issues.
- OWASP Juice Shop is a real-life application and gives you a flavor to test multiple security vulnerabilities ranging from Injection, Access Control to XXE.
- Cobalt.io Vulnerability Wiki is yet another great resource that includes a brief explanation, proof of concept, and risk ratings for various security issues based on OWASP ASVS.
- PayloadAllTheThings is an open-resource GitHub Repository that contains a huge list of payloads for all security issues and this is a good resource to know some of the new security issues as well.
- Learn365 is my own GitHub Repo which contains all the learning resources I am following in my #Learn365 challenge, these include various attack vectors including Web, Mobile, Network, Cloud, etc.
- HackTricks GitBook is a great collection of resources about various Network, Mobile & Web Attack vectors.
- InfoSec Writeups, PentesterLand & HackerOne Disclosures are great resources for looking at the Bug Bounty Writeups and learn how various hackers approach different bugs and different applications.
If you can purchase paid subscriptions I would suggest these two paid labs and they have nice content:
- PentesterLab: https://pentesterlab.com/
- PentesterAcademy — AttackDefense Labs: https://attackdefense.com/
Please note that I am not associated with these vendors in any sort of paid promotions.
Note: Do not spend much time on the labs and start exploring the things in the real-life application through bug bounty and responsible disclosure programs. Investing more time in labs may make you uncomfortable testing real-world applications. When you feel you need to learn any attack say cross-site scripting, simply google about the available labs and solve them, start hitting the real application and follow the process again.
Getting started with Web Application security is really simple if your basics are strong and you follow a proper approach, I strongly recommend not waste much time only looking for resources rather invest your time into facing real-life applications and various scenarios.
Getting Started with Network Security
For Network Security, there is no limit of resources but having a good understanding of computer networking from a security point is much required. There are multiple ways to practice for network security, however, the best way is to invest time in solving labs using HackTheBox and understanding new concepts. some of the good resources are:
- HackTheBox: An online platform to test and advance your skills in penetration testing and cybersecurity.
- VulnHub: To provide materials that allow anyone to gain practical ‘hands-on’ experience in digital security, computer software & network administration.
- OffensiveSecurity ProvingGrounds: Practice your Pentesting skills in a standalone, private lab environment with the additions of PG Play and PG Practice to Offensive Security’s Proving Grounds training labs.
- TryHackMe: TryHackMe is an online platform that teaches Cyber Security through short, gamified real-world labs. We have content for both complete beginners and seasoned hackers, incorporating guides and challenges to cater to different learning styles.
- HackTricks GitBook is a great collection of resources about various Network, Mobile & Web Attack vectors.
Getting Started with Mobile Application Security
The next big thing we often encounter as an Application Security engineer is Mobile Applications. However, this is a really interesting area as you have access to the source code by simply reverse-engineering the application and you can perform both Static as well as Dynamic Analysis.
I am also a learner when it comes to Mobile Application Security and currently, I have limited resources to suggest (I’ll add more in the coming days in this blog itself) which one can follow to pick up the pace with Mobile Application Security:
- OWASP Mobile Security Top 10: https://owasp.org/www-project-mobile-top-10/
- The Mobile Application Hacker’s Handbook:
- HackTricks GitBook is a great collection of resources about various Network, Mobile & Web Attack vectors.
- OWASP iGoat: https://github.com/OWASP/igoat
- Insecure Bank: https://github.com/dineshshetty/Android-InsecureBankv2
Closing Remarks
It took me a lot of time to put all the pieces together to write this blog but the purpose of drafting this blog is to answer all the questions that are generally asked to me around “How to get started”, “What is the right path” and others. Often, it is not possible to answer everyone but I hope this blog will help everyone who is seeking answers on this topic and all the newcomers. I will try to keep this blog updated at regular time intervals. In the future, I plan to add resources to get started into Cloud Security, Thick Clients, and other areas in this blog as well. I hope you enjoy reading this and get enough resources to get started in Cyber Security (Application Security/Offensive Security)
- Never ignore learning the basics. Invest as much time as you can to understand how things work. This will help you a lot.
- Do not get too much comfortable with solving the labs as you may get into Lab mentality. This may make you feel giving up if you don’t find anything in real-life applications.
- Once you learn about few security vulnerabilities through reading and labs, go and practice them through responsible disclosure and bug bounty programs, it may also give you some rewards but at the end of the day, you will learn.
- Follow the right set of people on Twitter and another social platform where you can stay updated about what’s going on in the market.
- Don’t give up easily and start seeking help to solve your problems. Dig deeper and exhaust all the possible resources and still if you stuck, reach out to others.
- Whenever you reach out to someone, make sure you explain the complete scenario and ready to provide the URLs/Affected Endpoints where you are suspecting a vulnerability. If you are restrictive to provide details, people won’t be able to help you.
- If you don’t get some bounties or a job, keep on trying harder and things will fall in place for sure. It’s easy to say someone’s hard work is luck but always focus on how you can improve yourself and your learning process.
- Certifications are good to have a thing and if you get it sponsored or you can afford them, surely, go ahead and enroll yourself.
This blog itself is a whole bunch of takeaways. This is specially written to direct people whenever they seek guidance to get started in the Cyber Security domain. This is totally my learning path and perspective about how one should get started and I am not saying to blindly follow this but if this looks good to you, follow it and I will try to keep it updated.
If you have any good resources that you know should be included in this blog, please leave a PRIVATE NOTE and I will add the relevant ones to the blog.
如有侵权请联系:admin#unsafe.sh