暗网成为网络犯罪分子获取情报、交易非法物品及工具、并与同伙交流的避风港。公共部门因处理大量敏感信息(如公民个人身份信息和关键基础设施运营细节)而成为高价值目标。文章探讨了暗网中针对公共部门数据的交易情况及威胁行为者的需求,并提供了安全建议以应对这些风险。 2025-10-15 13:34:4 Author: www.trustwave.com(查看原文) 阅读量:22 收藏
7 Minute Read
The dark web serves as a refuge for threat actors to gather intel, trade illicit goods and tools, and network with other cybercriminals. Aside from allowing threat actors to connect and learn from other individuals who share the same interests, the dark web facilitates the procurement and peddling of stolen data to make cyberattacks even more effective and nefarious. No organization’s data is safe from being shared in the dark web, and that includes public sector organizations. The public sector handles a wide range of information, from citizens’ personally identifiable information (PII) to critical infrastructure’s operational details, which, when exposed on the dark web, can lead to fraud, a plethora of cyberattacks, and disruptions to critical services. This article provides an overview of what the Trustwave SpiderLabs team has seen in the cybercriminal underground pertaining to public sector data, specifically what is being sold and what threat actors are seeking. Our research also provides actionable security recommendations to help public sector organizations keep their systems secure and protected against cyberthreats and risks. This is the final part of our series of public sector blogs that tackle cybercriminal motivations and trends, and ransomware tactics. VPN access to public administration systems is one of the items sold on dark web marketplaces, making it one of the most common forms of initial access for sale. Government entities still heavily rely on VPNs to enable remote work and inter-agency cooperation, and many of these systems grant broad network privileges once connected. All these reasons help make VPN credentials highly sought after, as they allow attackers to bypass perimeter defenses and operate inside the network with minimal resistance. Threat actors often harvest these access points through phishing, credential stealers, brute-force attacks, or insider leaks. In addition to VPNs, listings may include RDP, Citrix portals, webmail, or cloud dashboards like Microsoft 365. Some actors even sell access bundled with session tokens or screenshots as proof. Access brokers often resell this access to ransomware groups, hacktivists, or state-sponsored actors, multiplying the risks and complicating detection and response. For public administration, the consequences are serious. VPN access can be used to deploy malware, steal sensitive records, disrupt services, or serve as a launchpad for ransomware attacks. In some cases, it has enabled deeper espionage or data manipulation campaigns. Once inside, attackers can escalate privileges, move laterally, and evade detection for extended periods, sometimes months. To mitigate the threat, agencies must enforce MFA for all remote access, limit user privileges, monitor sessions for anomalies, and rotate credentials regularly. Reducing reliance on VPNs and moving toward zero-trust models is critical in the long term. Meanwhile, proactive monitoring of dark web markets can help identify and respond to compromised access before greater damage occurs. Malicious insider threats represent one of the most complex and dangerous threats to public sector organizations, particularly in sensitive domains such as law enforcement, intelligence, and within international policing bodies such as Interpol and Europol. Unlike external attackers who must bypass multiple layers of defense, insiders often begin with privileged access and intimate knowledge of internal systems. This makes them uniquely positioned to abuse trust and exfiltrate classified or restricted information without triggering immediate alarms. In recent years, the public sector has seen a worrying trend of threat actors actively attempting to recruit insiders through anonymous channels on the dark web. These recruitment posts specifically target government employees, including police officers, administrative staff, IT personnel, and even members of international agencies. The incentives vary; some individuals are lured by financial hardship or ideological alignment, while others are coerced through blackmail. Threat actors often offer generous rewards to those willing to provide access credentials, internal documents, system logs, intelligence, or any specific data requested, such as information from protected databases. The motivations of these cybercriminals range from simple data resale to defamation, as well as enabling various forms of espionage, blackmail, coercion, sabotage, or targeted disruption campaigns. Law enforcement and international investigatory bodies are especially attractive targets for insiders due to the type of data they handle. This includes active investigations, identities, cross-border intelligence cooperation, and operational plans. An insider in a police department or other agencies could leak data that allows threat actors to check specific information (such as people’s vehicle numbers) that can endanger lives, disrupt law enforcement operations, or expose police operational infrastructure. International law enforcement operations like Europol are not immune. Adversaries recognize that access to pan-European threat intelligence, criminal databases, and joint operational strategies can provide long-term benefits for criminal networks and hostile nation-states. While direct infiltration is rare, the growing digital interconnectivity of member states creates new opportunities for lower-level insiders in one country to access shared information affecting broader regions. The rise of remote work and increased digitalization of government operations have widened the potential attack surface. Insider recruitment is no longer limited to physical contact or embedded operatives; now, it can be orchestrated entirely online, with encrypted chats and cryptocurrency payments, ensuring anonymity and traceability for both parties. To address this threat, public sector organizations must not only strengthen technical controls such as access monitoring and behavioral analytics, but also invest in cultural resilience, vetting procedures, and staff awareness. Insider risk is no longer a theoretical concern — it is an active vector that cybercriminals are exploiting in increasingly organized and deliberate ways. A growing trend in the cybercrime ecosystem involves the sale and rental of active email accounts associated with public administration domains. These are not just leaked credentials; in many cases, the accounts remain fully functional, allowing threat actors to send and receive emails as if they were legitimate government employees. Criminals obtain these accounts through phishing, credential-stealing malware, or insider access, and then sell or lease them on dark web forums or private Telegram groups. For threat actors, the value of such access is immense. Government email addresses carry a high level of inherent trust, especially when interacting with external organizations, vendors, or citizens. Hackers can use these accounts to launch highly effective spear-phishing campaigns, impersonate officials, distribute malicious documents, or escalate their access by requesting additional credentials or system privileges from internal contacts. In some cases, attackers have used legitimate email access to manipulate procurement processes, authorize fraudulent payments, or quietly gather intelligence by observing internal communications. From the perspective of public administration facilities, the consequences can be severe. Compromised emails can lead to data breaches, financial loss, reputational damage, and erosion of public trust. Even after the account is secured, the damage may already be done, information could have been exfiltrated, malware deployed, or further access brokered to other cybercriminal groups. Moreover, the facility may have to conduct costly investigations, notify affected individuals, and implement long-term remediation. To defend against such abuse, public agencies must enforce strict access controls, implement MFA, and monitor email usage for anomalies, such as login attempts from unusual locations or suspicious message activity. Employee awareness training is also crucial, especially around phishing and social engineering tactics. Remediation for public sector cyber threats is a multi-layered endeavor. It involves deploying technology, fostering skilled personnel and awareness, establishing robust processes, and enacting smart policies. Public administrations should strive to be “secure by design”, integrating cybersecurity into every project, rather than as an afterthought. This means when new government or public administration digital services are launched, security architecture and privacy considerations should be built in from the start. It also means embracing innovation in defense: just as attackers use AI, defenders in government should leverage AI for threat hunting and anomaly detection (noting that those who used AI-based security reportedly detected breaches much faster and saved costs in 2024). Ultimately, protecting public administration from cyberattacks is essential to ensuring that governments can fulfill their duties and that citizens can trust and safely use digital public services. The past five years have been a wake-up call, illustrating worst-case scenarios, but they have also catalyzed improvements. If lessons from breaches are learned and the above practices implemented, public sector organizations will be much harder targets, and the tendencies of cyberattacks over the next five years might shift from rampant successes to more thwarted attempts. Continual vigilance, investment, and adaptation will be required, as the threat landscape never stands still. The goal, however, is clear: to preserve the continuity, security, and integrity of the digital systems that underpin modern governance and public life. The following are recommended remediations and best practices for public administration facilities to mitigate the threats outlined: Adopt recognized cybersecurity frameworks such as NIST, CIS Controls, or ISO 27001 to establish baseline protections across all systems. Transition to a zero-trust architecture by requiring continuous verification of all users and devices. Enforce MFA, strict identity and access controls, and network segmentation. Maintain accurate asset and software inventories. Incorporate supply chain risk management by vetting vendors, monitoring for compromises, and verifying software integrity through trusted sources. Establish a formal patch management process to prioritize and rapidly apply security updates, especially for known exploited vulnerabilities. Automate patch deployment when possible and ensure legacy systems are updated or replaced. Disable unused services, enforce secure configurations, and routinely audit system settings. Implement and protect offline backups with strong access controls and regular testing to ensure reliable recovery from ransomware or system failure. Deploy 24/7 security monitoring tools, including endpoint detection, threat intelligence, and anomaly detection systems. Establish and rehearse incident response plans that define roles, decision protocols, and recovery procedures. Integrate these plans with business continuity strategies to sustain operations during cyber incidents. Participate in information-sharing networks and adopt MDR services where in-house capabilities are limited. Emphasize early threat detection and rapid response to reduce operational and data loss. Implement continuous cybersecurity training tailored to phishing, social engineering, and incident reporting. Require MFA across all access points and apply privileged access management to restrict high-level controls. Regularly review and adjust user permissions. Monitor for abnormal account activity and quickly apply strict internal access verification to detect and contain compromised accounts. Develop and routinely test business continuity and disaster recovery plans that ensure critical services can function without IT systems. Segment networks to limit lateral movement in the event of compromise. Use automated endpoint isolation to contain threats immediately. Secure cyber insurance to mitigate financial losses but ensure coverage is backed by strong preventive measures. Conduct post-incident reviews to identify and correct root causes. Coordinate with other government bodies and international partners to share threat data and reinforce collective resilience. Enforce policies that discourage or prohibit public entities from making ransom payments to reduce financial incentives for attackers. Support prosecution and sanctions against cybercriminals and their facilitators. Mandate timely breach reporting to national authorities to enable coordinated responses. Publicly attribute state-sponsored attacks where appropriate and respond through legal or diplomatic channels. Promote international collaboration to build unified, long-term deterrence. The last five years have demonstrated that cyberattacks on public administration are not only persistent but also increasingly sophisticated and impactful. The trend lines show that threat actors, whether financially motivated gangs or nation-state units, have zeroed in on government entities as high-value targets. Public sector organizations must assume that attacks will continue and, indeed, become “the new reality” of daily operations and thus prioritize cybersecurity as fundamental to their mission. The analysis of recent incidents reveals key areas that need bolstering: ransomware preparedness, rapid patch management, supply-chain risk oversight, and data protection. It’s encouraging to see that effective defense is achievable. For instance, many large US municipalities are successfully avoiding major disruptions by proactively investing in modern security measures. With the right strategy and commitment, public administrations can build strong, resilient defenses.Public Administration on the Dark Web: VPN Access

Figure 1. A dark web advertisement introduces an attempt to sell VPN and domain user access to a Mexico-based government facility.%20access%20to%20a%20government%20facility%20for%20$1%2c500.jpg?width=1903&height=563&name=Figure%202.%20A%20threat%20actor%20selling%20Remote%20Desktop%20Protocol%20(RDP)%20access%20to%20a%20government%20facility%20for%20$1%2c500.jpg)
Figure 2. A threat actor selling Remote Desktop Protocol (RDP) access to a government facility for $1,500.
Figure 3. A threat actor offers VPN access to an Algerian-based government facility for $500.Malicious Insiders in the Public Sector

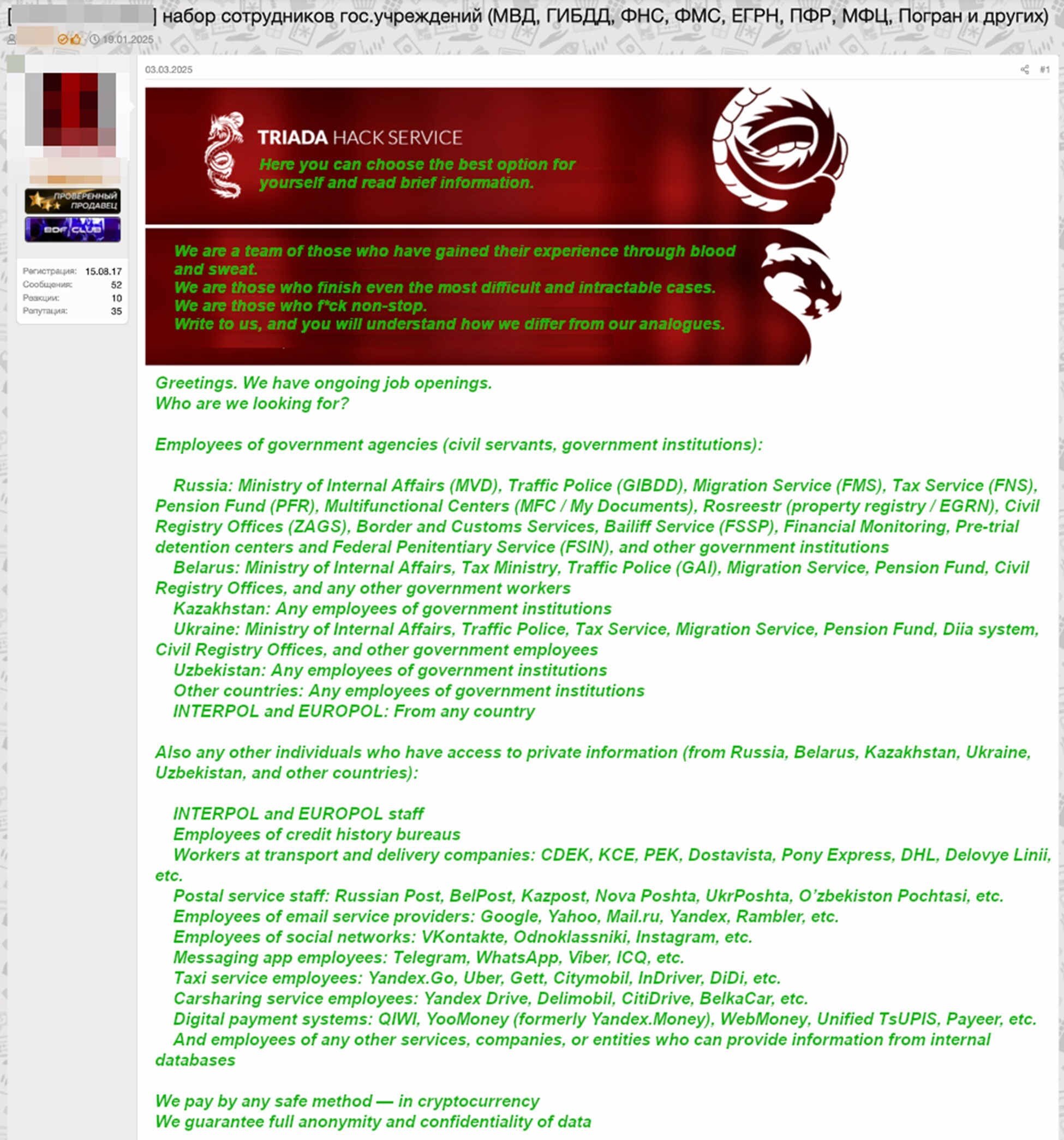
Figure 4. An advertisement on a Russian-speaking dark web forum offering a good reward to government agency insiders.
Figure 5. Indian law enforcement data shared to a dark web community.Public Administration Emails for Sale

Figure 6. A dark web advertisement offers access to government email accounts from various countries.Remediation Strategies for the Public Sector
Conclusion
如有侵权请联系:admin#unsafe.sh