2024-7-27 00:12:9 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Imperva customers who properly utilize the managed certificate feature can experience a robust, interruptions-free, and fully automated certificate management process that requires no effort for domain validations and renewals.
In today’s digital landscape, security is of paramount importance. One critical aspect of online security is ensuring that communication between a user’s browser and a website is encrypted and secure. This is where SSL (Secure Sockets Layer) certificates come into play. SSL certificates encrypt data and verify the identity of a website, providing users with confidence that their information is safe from malicious eyes. However, managing SSL certificates can be a daunting task, especially when it comes to domain ownership validation.
Traditionally, SSL certificate management has been a manual process, requiring significant time and effort. This manual management involves submitting certificate signing requests (CSRs), verifying domain ownership, and ensuring compliance with industry standards. Not only is this process time-consuming, but it also introduces the possibility of human error, potentially leaving websites vulnerable to security breaches.
In recent years, internet security has undergone significant transformations. One notable shift across industries is the adoption of SSL certificates with shorter expiration dates to reduce exposure risk and improve trust and reputation. Ten years ago certificates could be issued for 39 months, five years later they could be issued for 27 months, today validity for more than 13 months is not allowed. In March 2023 Google announced its intention to reduce maximum certificate validity to just 90 days. If the CA and Browsers (CA/B) forum adopts Chrome’s vision, manual management of certificates will soon be impossible.
Domain ownership validation
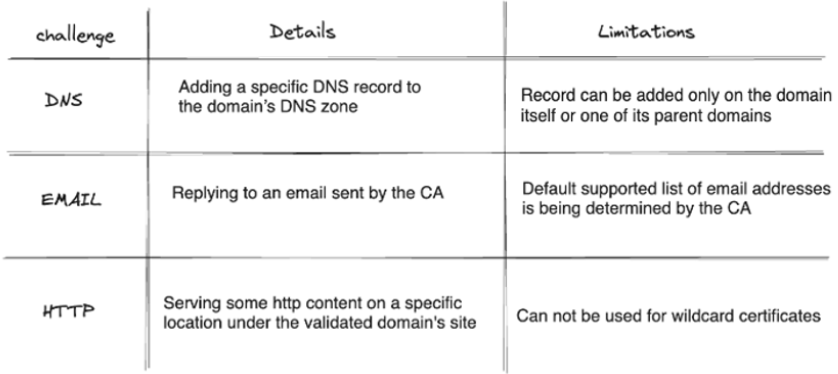
To prove domain ownership, the owner should answer a challenge generated by the certificate authority (CA). Several challenge types are supported, the most commonly used described in the following table:
Domain ownership validation is not permanent. It has an expiration date of 12 months, which means that revalidation of domains should be carried out regularly.
For Imperva’s customers the managed certificate feature reduces most of the effort that was described above, Imperva handles the certificate issuance and renewals and makes sure that the provided certificates will be completely compliant with industry standards.
However, the responsibility of ownership validation still falls on the customer.
Despite being a significant improvement, this step can be tedious and prone to human error.
For instance, in some organizations, the team responsible for domain validations may lack the necessary permissions to access the domain’s DNS management platform or the related administrator mailbox. In other cases, each domain may be managed by a different team, adding to the complexity. Organizations with hundreds of domains often employ dedicated staff to ensure revalidations are completed on time, preventing website outages.
Reseller customers often find it hard to reach their customers when revalidation is required, which increases the risk of outages for their websites.
Fortunately, there’s exciting news: revalidations (and even initial validations) can now be automated! This game-changing advancement not only streamlines the process even further but also dramatically reduces the risk of human error and service interruptions.
CNAME validation for domain ownership
When requesting a DNS challenge from a Certificate Authority (CA), applicants have the flexibility to choose the domain to be challenged. It is crucial that the selected domain can be used to validate ownership of the original domain.
For Example:
– Both test.com and www.test.com can be used to prove ownership on www.test.com
– However, challenging www.test.com cannot be used to prove ownership of test.com
CNAME validation is a flavor of DNS challenge that allows the owner to use a subdomain of the validated domain as a target for the challenge.
A common use case is a validation of a domain that already has a CNAME record on it. The DNS specification doesn’t allow for such a domain to have other kinds of records. In such cases, the owner can ask the CA to prove ownership of a subdomain of the original domain, as long as this subdomain is invalid.
For example, if public.test.com cannot be challenged directly, the owner can ask to validate on _validation.public.test.com instead.
The preceding underscore in _validation.public.test.com makes it invalid and therefore allowed by the CA for the validation of the more generic domain public.test.com
The real power of the CNAME validation method is revealed when it is being used to define delegation of the ownership validation to another domain.
The owner can put a CNAME record on an invalid subdomain that points to a completely different domain, directing the CA to challenge a domain that is more convenient for this action. As the subdomain is not a real domain, adding the CNAME record on it will not affect any real traffic.
The Imperva solution
Imperva integrated the CNAME validation solution in its site onboarding process and now allows customers to define ownership delegation to Imperva both at the site and account levels.
When onboarding a new site with a managed certificate to Imperva, the customer can choose to use CNAME validation as the validation method.
Imperva will provide instructions to put a CNAME on an invalid subdomain, under the site’s domain, that will point to a domain that is being maintained by Imperva. After following the instructions, all challenges from the CA will be answered automatically by Imperva against the Imperva’s domain.
For example, the instructions for the www.test.com site will be to add a DNS record like the following:
_delegate_validation.www.test.com CNAME 7ghbz6i.ng.impervadns.net
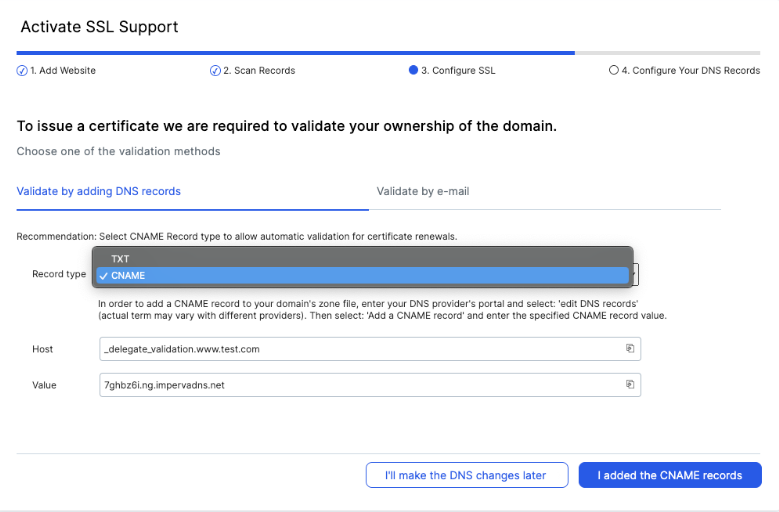
Sites that are configured with CNAME validation will enjoy the benefit of a fully automated SSL certificate life cycle as long as the CNAME record is in place.
How does it work?

Site-level CNAME validation simplicity
Using CNAME validation at the site level is great for customers who have a small number of sites under the same domain. The setup is simple and the CNAME value is the same as the value provided for pointing the site traffic to Imperva, making it very easy to understand the correlation between those records.
In the example above, when instructed, the customer will point the traffic of the site
www.test.com to Imperva by adding a record like the following:
www.test.com CNAME 7ghbz6i.ng.impervadns.net
CNAME validation – account level
Account-level CNAME validation takes the automation a step further by automating the initial validation as well.
With account level CNAME validation the customer can delegate to Imperva the ability to validate ownership of a domain and all its subdomains (currently restricted to up to 5 levels).
Adding the delegation in the account level provides:
- Automatic validation for existing sites that are pending validation
- Automatic revalidation for existing sites when the validation has expired
- Automatic validation (and revalidation) for all future onboarded sites under the
delegated domains (with no initial setup required).
For example, after adding the domain test.com to the account level delegation, the customer will be instructed to add a DNS record like the following:
_delegate_validation.test.com CNAME _5f50a5f02089.cjgiachmlhvgef.validation.imperva.com
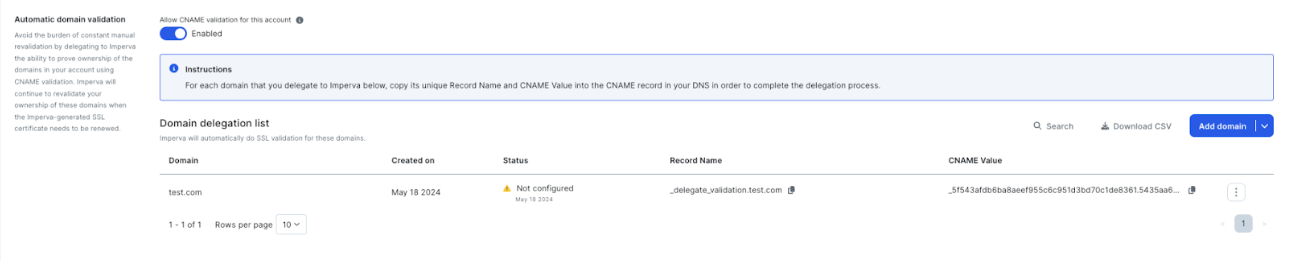
After Imperva identifies the record in place, the following features will be supported:
- Automatic revalidation of a domain – The domain www.test.com that is pending validation will be set to use CNAME validation and will be validated automatically.
- Automatic revalidation on certificate renewal – On the next renewal of the site public.eu.test.com, which already has SSL coverage, it will be set to use CNAME validation and will be revalidated automatically.
- Onboarding a new site – When the site sales.local.test.com is onboarded to the service, it will be automatically set to use CNAME validation and will be validated with no action required from the customer.
Recommendation
For customers with many sites under the same domain, we highly recommend using account-level CNAME validation, enabling you to enjoy a new experience of an effortless certificate management process.
Despite its simplicity, site-level CNAME validation is not recommended for customers who requested a wildcard SAN on the managed certificate, when the wildcard covers more than one site. Such configuration can cause a loss of the automatic validation for the wildcard SAN if the site that the CNAME validation was configured for is subsequently deleted from the system. In this case, CNAME validation at the account level is more suitable.
On the other hand, reseller customers who have only one site per domain probably want the configuration to be as simple for their customers and will get a more suitable experience with site-level CNAME validation.
Conclusions: SSL certificate management, when done manually, requires more and more attention, effort, and resources while the digital world evolves. Imperva-managed certificates with CNAME validation provide a full automatic certificate management process that makes sure that our customer’s websites are always protected and have SSL coverage in place.
For more details on automatic domain validation, see our documentation: https://docs.imperva.com/bundle/cloud-application-security/page/cname-account.htm
The post Effortless certificate management with automated CNAME validation appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Eilon Shai. Read the original post at: https://www.imperva.com/blog/how-to-do-dffortless-certificate-management-with-automated-cname-validation/
如有侵权请联系:admin#unsafe.sh