2023-12-1 20:34:39 Author: securityaffairs.com(查看原文) 阅读量:8 收藏
Black Basta Ransomware gang accumulated at least $107 million in Bitcoin ransom payments since early 2022
Pierluigi Paganini
December 01, 2023

The Black Basta ransomware gang infected over 300 victims accumulating ransom payments exceeding $100 million since early 2022.
The Black Basta ransomware group has been active since April 2022, like other ransomware operations, it implements a double-extortion attack model.
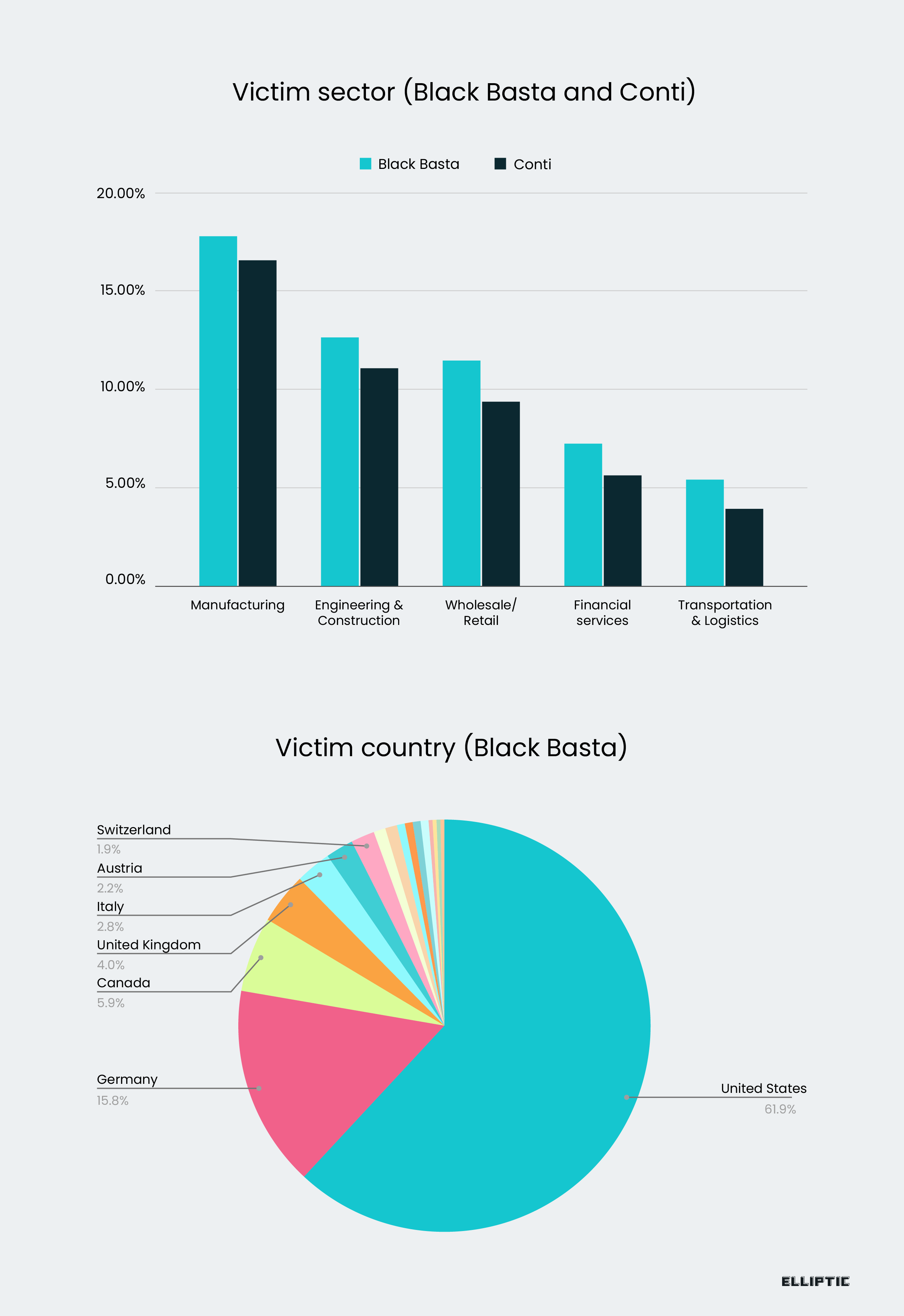
A joint research by Elliptic and Corvus Insurance revealed that the group accumulated at least $107 million in Bitcoin ransom payments since early 2022. According to the experts, the ransomware gang has infected over 329 victims, including ABB, Capita, Dish Network, and Rheinmetall.
The researchers analyzed blockchain transactions, they discovered a clear link between Black Basta and the Conti Group.
In 2022, the Conti gang discontinued its operations, coinciding with the emergence of the Black Basta group in the threat landscape.
The group mainly laundered the illicit funds through the Russian crypto exchange Garantex.
“Black Basta is a Russia-linked ransomware that emerged in early 2022. It has been used to attack more than 329 organizations globally and has grown to become the fourth-most active strain of ransomware by number of victims in 2022-2023.” reads the Elliptic’s report. “Our analysis suggests that Black Basta has received at least $107 million in ransom payments since early 2022, across more than 90 victims. The largest received ransom payment was $9 million, and at least 18 of the ransoms exceeded $1 million. The average ransom payment was $1.2 million.”
Most of the victims are in the manufacturing, engineering and construction, and retail sectors. 61,9% of the victims are in the US, 15.8% in Germany, and 5.9% in Canada.
Some of the victims’ ransom payments were sent by both Conti and Black Basta groups to gang behind the Qakbot malware.
In August, the FBI announced that the Qakbot botnet was dismantled as a result of an international law enforcement operation named Operation ‘Duck Hunt.’
Qakbot, also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. The malware spreads via malspam campaigns, it inserts replies in active email threads.
Despite the law enforcement operation, the threat actors behind QakBot are still active, Cisco Talos warns.
According to the researchers, the threat actors behind the Qakbot bot have been conducting a campaign since early August 2023. The attacks aimed at distributing Ransom Knight ransomware and the Remcos RAT.
Approximately 10% of the Black Basta ransom amount was forwarded on to Qakbot, whike the group maintained 14% of ransom payments.
“These transactions indicate that approximately 10% of the ransom amount was forwarded on to Qakbot, in cases where they were involved in providing access to the victim.” concludes the victims.
“The Black Basta operator appears to take an average of 14% of ransom payments. This is a typical split seen in ransomware-as-a-service operations,” Elliptic says.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)
如有侵权请联系:admin#unsafe.sh
