2023-11-19 17:13:35 Author: securityaffairs.com(查看原文) 阅读量:17 收藏
8Base ransomware operators use a new variant of the Phobos ransomware
Pierluigi Paganini
November 19, 2023

8Base ransomware operators were observed using a variant of the Phobos ransomware in a recent wave of attacks.
Cisco Talos researchers observed 8Base ransomware operators using a variant of the Phobos ransomware in recent attacks.
Phobos variants are usually distributed by the SmokeLoader, but in 8Base campaigns, it has the ransomware component embedded in its encrypted payloads. The ransomware component is then decrypted and loaded into the SmokeLoader process’ memory.
In June, VMware Carbon Black researchers observed an intensification of the activity associated with a stealthy ransomware group named 8Base. The experts observed a massive spike in activity associated with this threat actor between May and June 2023.
The group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT.
Security experts attributed 67 attacks to the group in May 2023, most of the victims are in the U.S. and Brazil.
VMware researchers first noticed that Phobos ransomware uses the “.8base” file extension for encrypted documents, a circumstance that suggested a possible link to the 8Base group or the use of the same code-base for their ransomware.
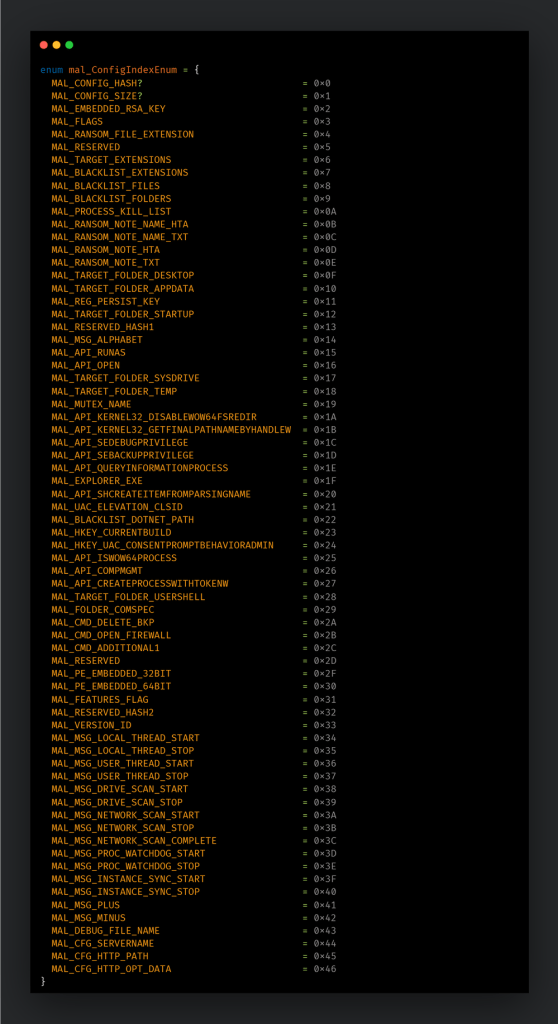
The Talos researchers discovered a number of features implemented by Phobos allowing operators to establish persistence in a targeted system, perform speedy encryption, and remove backups.
The malware supports the following features:
- Full encryption of files below 1.5MB and partial encryption of files above this threshold to improve the speed of encryption. Larger files will have smaller blocks of data encrypted throughout the file and a list of these blocks is saved in the metadata along with the key at the end of the file.
- Capability to scan for network shares in the local network.
- Persistence achieved via Startup folder and Run Registry key.
- Generation of target list of extensions and folders to encrypt.
- Process watchdog thread to kill processes that may hold target files open. This is done to improve the chances the important files will be encrypted.
- Disable system recovery, backup and shadow copies and the Windows firewall.
- Embedded configuration with more than 70 options available. This configuration is encrypted with the same AES function used to encrypt files, but using a hardcoded key.
The analysis of the configuration data revealed additional features in the malware binary, including bypassing the User Account Control (UAC) and reporting of a victim infection to an external URL.

“We also examined the encryption methodology used by Phobos. Versions of Phobos released after 2019 use a custom implementation of AES-256 encryption, with a different random symmetric key used for each encrypted file, instead of using the Windows Crypto API like earlier variants.” reads the report published by Talos.”Once each file is encrypted, the key used in the encryption along with additional metadata is then encrypted using RSA-1024 with a hardcoded public key, and saved to the end of the file.”
As each file is encrypted using a different key, decrypting files through brute-forcing of a key, as done in the past, is impossible.
“Since 8Base group is known to operate with characteristics similar to previous Phobos campaigns, we compared the code in an 8Base sample with previous Phobos variants and determined there are no differences between the code at the binary level at all.” concludes the report that also includes Indicators of Compromise.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)
如有侵权请联系:admin#unsafe.sh