2023-11-12 01:24:27 Author: securityaffairs.com(查看原文) 阅读量:13 收藏
Police seized BulletProftLink phishing-as-a-service (PhaaS) platform
Pierluigi Paganini
November 11, 2023

The Royal Malaysian Police announced the seizure of the notorious BulletProftLink phishing-as-a-service (PhaaS) platform.
The Royal Malaysian Police announced to have dismantled the notorious BulletProftLink phishing-as-a-service (PhaaS) platform. A joint international operation conducted by the Malaysian police, the FBI, and the Australian Federal Police took down several domains employed in the cybercriminal operation.
“We seized around RM960,000 put inside an e-wallet, apart from other valuables during the simultaneous raid we conducted earlier this week.” explained Inspector General of Police Tan Sri Razarudin Husain, who also confirmed the arrest of eight people, including the mastermind. The suspects were detained in various locations, including Kuala Lumpur, Sabah, Selangor, and Perak on November 6, 2023.
“I do not think this is all they earned. He must have sold the credentials for money including on the dark web.”
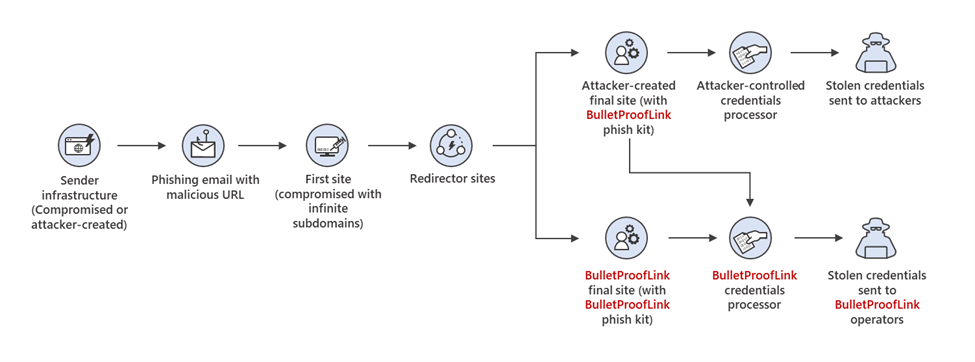
In September 2021, Microsoft researchers discovered the large-scale phishing-as-a-service (PHaaS) operation, dubbed BulletProofLink (aka Anthrax). It offers its customers phishing kits, email templates, and hosting and automated services to carry out phishing attacks. BulletProofLink service was very cheap and allowed threat actors to arrange phishing campaigns without specific technical capabilities.
Microsoft uncovered the operation during its investigation of a phishing campaign that was using a BulletProofLink phishing kit on either attacker-controlled sites or sites provided by BulletProofLink as part of their PaaS service. The operation was first documented on OSINT Fans by Gabor Szathmari in October 2020.
BulletProofLink operation provided hundreds of phishing templates that mimic popular brands and services, experts estimated that it is responsible for many of the phishing campaigns that hit enterprises today.
BulletProofLink has been active since 2015, it was used by thousands of threat actors in either one-off or monthly subscription-based business models.
BulletProofLink operated an online store to advertise their service that goes for as much as $800 a month, the group also offers a 10% welcome discount on customers’ orders if they subscribe to their newsletter.
One of the interesting aspects of this large-scale phishing campaign was called by Microsoft experts “double theft,,” it refers to a tactic where credentials stolen in phishing attacks by the customers of the service are also sent to a server controlled by PhaaS operators if they use a phishing kit in its default configuration.
The double theft tactic allows the PhaaS operators to maximize their profits, the operators also earn by selling victims’ credentials in the cybercrime underground

“With phishing kits, it is trivial for operators to include a secondary location for credentials to be sent to and hope that the purchaser of the phish kit does not alter the code to remove it. This is true for the BulletProofLink phishing kit, and in cases where the attackers using the service received credentials and logs at the end of a week instead of conducting campaigns themselves, the PhaaS operator maintained control of all credentials they resell.” reported Microsoft. “In both ransomware and phishing, the operators supplying resources to facilitate attacks maximize monetization by assuring stolen data, access, and credentials are put to use in as many ways as possible. Additionally, victims’ credentials also likely to end up in the underground economy.“
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, BulletProftLink)
如有侵权请联系:admin#unsafe.sh