2023-10-23 14:50:23 Author: securityaffairs.com(查看原文) 阅读量:9 收藏
Vietnamese threat actors linked to DarkGate malware campaign

Researchers linked Vietnamese threat actors to the string of DarkGate malware attacks on entities in the U.K., the U.S., and India.
WithSecure researchers linked the recent attacks using the DarkGate malware to a Vietnamese cybercrime group previously known for the usage of Ducktail stealer.
DarkGate is a commodity malware that is offered with a model of Malware as a Service (MaaS), it was employed in attacks aimed at entities in the U.K., the U.S., and India.
Vietnamese cybercrime groups are using multiple Malware as a Service (MaaS), their targeting and methods heavily overlap. WithSecure speculates that these groups are a closely related cluster of operators/groups.
“The overlap of tools and campaigns is very likely due to the effects of a cybercrime marketplace and ecosystem described in the WithSecure Professionalization of Cybercrime report. Threat actors are able to acquire and use multiple different tools for the same purpose, and all they have to do is come up with targets, campaigns, and lures.” reads the report published by WithSecure.
“There have been multiple reports in Q3 2023 about DarkGate, the closely related Ducktail campaigns, and the Vietnamese threat actor cluster responsible for these campaigns.”
A Vietnamese group observed by the researchers used very similar lures and delivery methods in different attacks attempting to deliver:
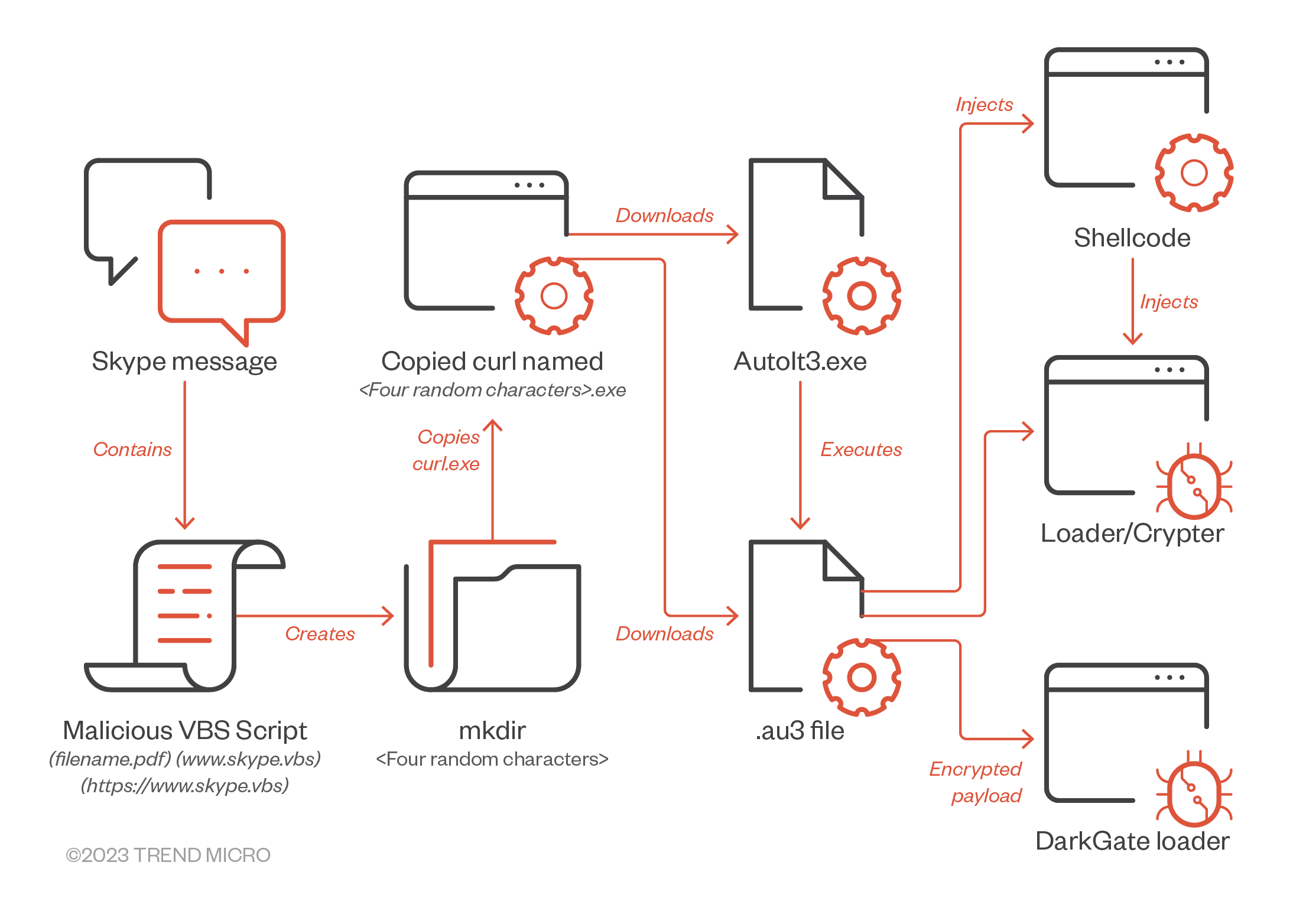
The attack chain began with the download of a file named “Salary and new products.8.4.zip” and the execution of the content. The archive contained a VBS script which copied the legitimate windows binary curl.exe to a new location. The Curl.exe was renamed to a random name and used to connect to an external destination and download two files, autoit3.exe and a compiled Autoit3 script. The script was executed using autoit3.exe, it de-obfuscated and constructed the DarkGate RAT from strings embedded in the script.
The analysis of the browser history of a victim device revealed that attackers used LinkedIn as the initial vector. Then the LinkedIn message redirected the victim to a file hosted on Google Drive.
According to WithSecure, the campaign themes and lures used to distribute Ducktail and DarkGate are very similar, although there are significant differences in the functionality of the final stage.
While Ducktail is a stealer, DarkGate is a remote access trojan (RAT) that is also used to maintain covert persistence on the infected systems.
“It very much appears that DarkGate has a much more diverse user base than Ducktail, with much more varied goals. As such however, while DarkGate is a tool which is used by and useful to multiple unrelated actors, the DarkGate behavior which most closely resembles and overlaps with the Ducktail campaigns is likely to be the same Vietnamese threat actor cluster.” concludes the report that includes Indicators of Compromise (IoCs).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DarkGate malware)
如有侵权请联系:admin#unsafe.sh