2023-10-19 18:17:0 Author: securityaffairs.com(查看原文) 阅读量:19 收藏
North Korea-linked APT groups actively exploit JetBrains TeamCity flaw

North Korea-linked threat actors are actively exploiting a critical vulnerability CVE-2023-42793 in JetBrains TeamCity.
Microsoft warns that North Korea-linked threat actors are actively exploiting a critical security vulnerability, tracked as CVE-2023-42793 (CVSS score: 9.8), in JetBrains TeamCity.
CVE-2023-42793 is an authentication bypass issue affecting the on-premises version of TeamCity. An attacker can exploit the flaw to steal source code and stored service secrets and private keys of the target organization. By injecting malicious code, an attacker can also compromise the integrity of software releases and impact all downstream users.
In early October, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the JetBrains TeamCity to its Known Exploited Vulnerabilities Catalog.
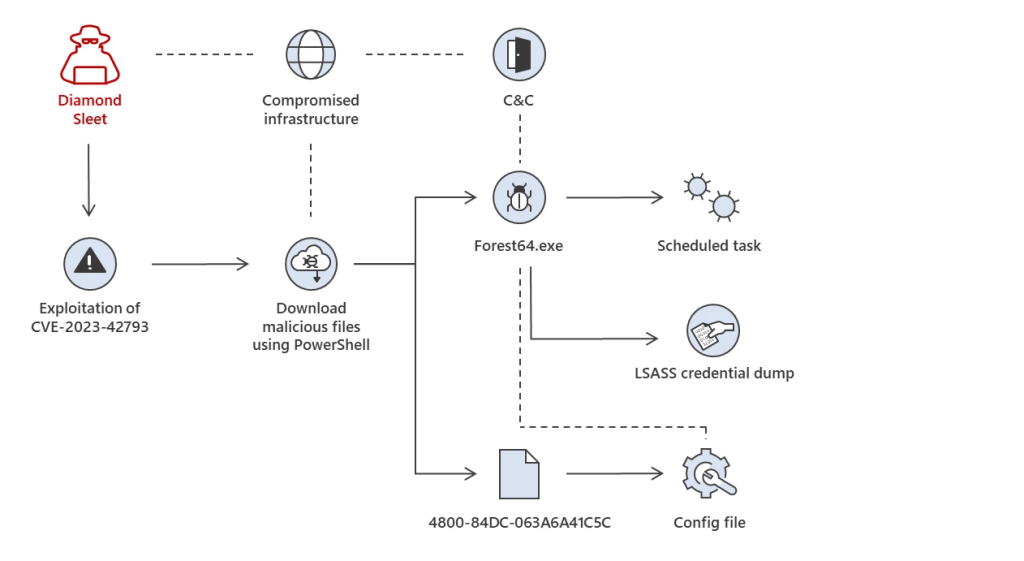
Microsoft attributes the recent attacks to two North Korean APT groups Diamond Sleet and Onyx Sleet, which operate under the Lazarus Group umbrella.
One of the attack chains detailed by Microsoft was linked to Following Diamond Sleet which compromises TeamCity servers. Then attackers used PowerShell to download two payloads from legitimate infrastructure they had previously compromised. Threat actors deployed the ForestTiger backdoor and used it to dump credentials via the LSASS memory.
In a second cluster linked to Diamond Sleet, threat actors deployed payloads for use in DLL search-order hijacking attacks.
The malicious payloads were used in DLL search-order hijacking attacks to execute a next-stage malware or a remote access trojan (RAT).
The Onyx Sleet APT used a different attack chain, threat actors exploited JetBrains TeamCity flaw to create a new user account named krtbgt that’s likely intended to impersonate the Kerberos Ticket Granting Ticket.
Then the threat actor added the account to the Local Administrators Group through net use and ran several system discovery commands on compromised systems.
The state-sponsored hackers were observed deploying a custom proxy tool dubbed HazyLoad.
In some cases, the attackers used the krtbgt account to sign into the compromised device via remote desktop protocol (RDP) and terminate the TeamCity service in a bid to prevent exploitation of the issue by other threat actors.
Threat actors were also spotted deploying tools to retrieve credentials and other data stored by browsers.
Below are the mitigation actions recommended by Microsoft:
- Apply the update or mitigations released by JetBrains to address CVE-2023-42793.
- Use the included indicators of compromise to investigate whether they exist in your environment and assess for potential intrusion.
- Block in-bound traffic from IPs specified in the IOC table.
- Use Microsoft Defender Antivirus to protect from this threat. Turn on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
- Take immediate action to address malicious activity on the impacted device. If malicious code has been launched, the attacker has likely taken complete control of the device. Immediately isolate the system and perform a reset of credentials and tokens.
- Investigate the device timeline for indications of lateral movement activities using one of the compromised accounts. Check for additional tools that attackers might have dropped to enable credential access, lateral movement, and other attack activities.
- Ensure that “Safe DLL Search Mode” is set.
- Turn on the following attack surface reduction rule:
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, JetBrains TeamCity)
如有侵权请联系:admin#unsafe.sh

