2023-10-16 16:15:13 Author: securityaffairs.com(查看原文) 阅读量:20 收藏
Microsoft Defender thwarted Akira ransomware attack on an industrial engineering firm

Microsoft thwarted a large-scale hacking campaign carried out by Akira ransomware operators targeting an unknown industrial organization.
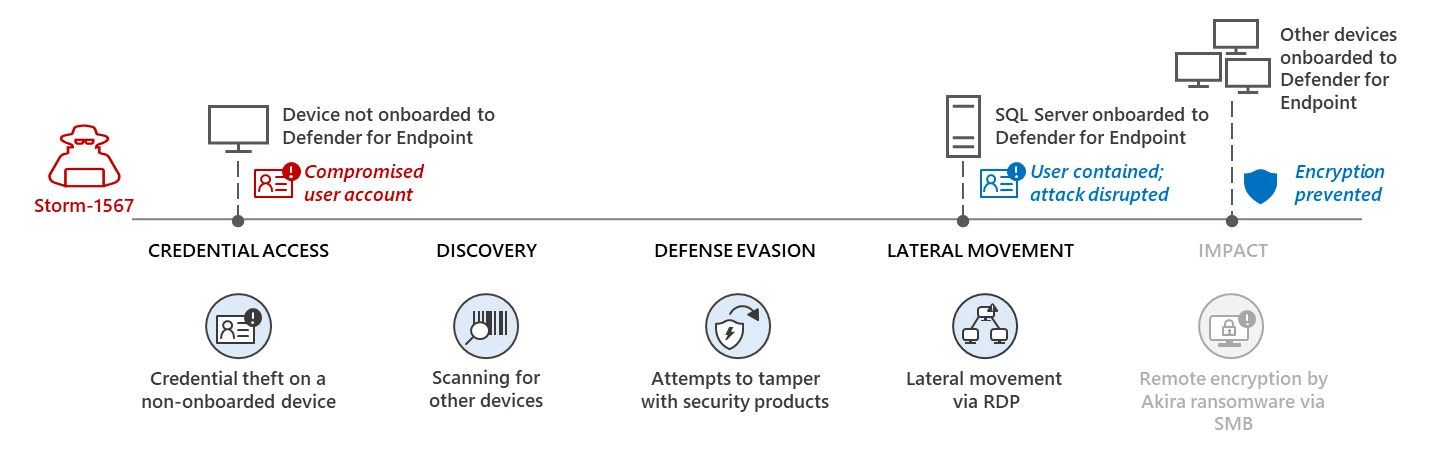
Microsoft announced that its Microsoft Defender for Endpoint helped to block a large-scale hacking campaign carried out by Akira ransomware operators (tracked by Microsoft as Storm-1567)
The attack took place in early June 2023 and aimed at an industrial engineering organization.
According to the IT giant, its cyber defense solution is able to automatically disrupt human-operated attacks like ransomware without needing to deploy any other capabilities.
The Akira ransomware has been active since March 2023, the threat actors behind the malware claim to have already hacked multiple organizations in multiple industries, including education, finance, and real estate. Like other ransomware gangs, the group has developed a Linux encryptor to target VMware ESXi servers.
“In this attack, the threat actor leveraged devices that were not onboarded to Microsoft Defender for Endpoint for most of the attack stages, a defense evasion tactic we’ve seen in other attacks.” reads the analysis published by Microsoft. “While visibility by our endpoint solution could have blocked the attack earlier in the attack chain and helped to protect the organization’s devices much sooner, Defender for Endpoint nonetheless successfully prevented the ransomware stage, protecting all onboarded devices in the organization from getting encrypted.”
Threat actors leveraged devices that were not onboarded to Microsoft Defender for Endpoint to evade detection while conducting reconnaissance and lateral movement activities.

Microsoft Defender capabilities prevented breached accounts were being used to access endpoints and other resources in the network.
The defense in place limited attackers’ ability to perform lateral movements regardless of the account’s Active Directory state or privilege level.
“Identifying and containing these compromised user accounts, therefore, prevents attacks from progressing, even if attackers gain initial access.” concludes the report. “This is why, as announced today, we added user containment to the automatic attack disruption capability in Microsoft Defender for Endpoint, a unique and innovative defense mechanism that stops human-operated attacks in their tracks”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ransomware)
如有侵权请联系:admin#unsafe.sh